Hi, there! It's great to engage with you again. If you're excited to learn how to prevent and detect cryptojacking, you won't be disappointed. If you missed the first part of this blog series, or want a refresher on the topics previously covered, you can find it here. In this second and final part, you'll learn the signs of cryptojacking and effective ways to thwart them. Let's get started.
Whenever a device is used for mining cryptocurrency, with or without the user's consent, it leaves behind a trail of evidence in the form of certain signs. These signs, if recognized, can provide information about the device(s) involved, and help you classify them as safe or cryptojacked. These are some of the signs to watch for:
Except for the last item on the list, the signs pertain to the infected device. If a device exhibits the first few signs frequently, then it's likely that device has been infected with cryptojacking malware. Depending on the sophistication of the malware, it can also infect other devices on the network. Now, the question arises: Is there a way to prevent it? Or, if a device is already infected, how can we detect it? Read on to find out.
As the saying goes, "Prevention is better than a cure" and we realize how true that is today, in more ways than one. Here are a few ways to avoid falling victim to cryptojacking:
While prevention should be our primary goal, let's learn how to detect cryptojacking so we can be prepared.
Cryptojackers are smart and sophisticated enough to design malware that can remain undetected for quite a while, or persist in the device even after the user leaves the infected browser. However, while detecting cryptojacking might be difficult, it is not impossible, especially if you know what to watch for. A combination of inputs from users and security solutions can help you identify and combat cryptojacking.
ManageEngine Log360 offers built-in correlation rules to identify cryptojacking. It also allows for the customization of rules. To detect cryptojacking more effectively, you can create your own rules to integrate logs from antivirus and antimalware solutions to the built-in rules.
In Log360, the built-in correlation rule for detecting cryptojacking offers insights and alerts based on:
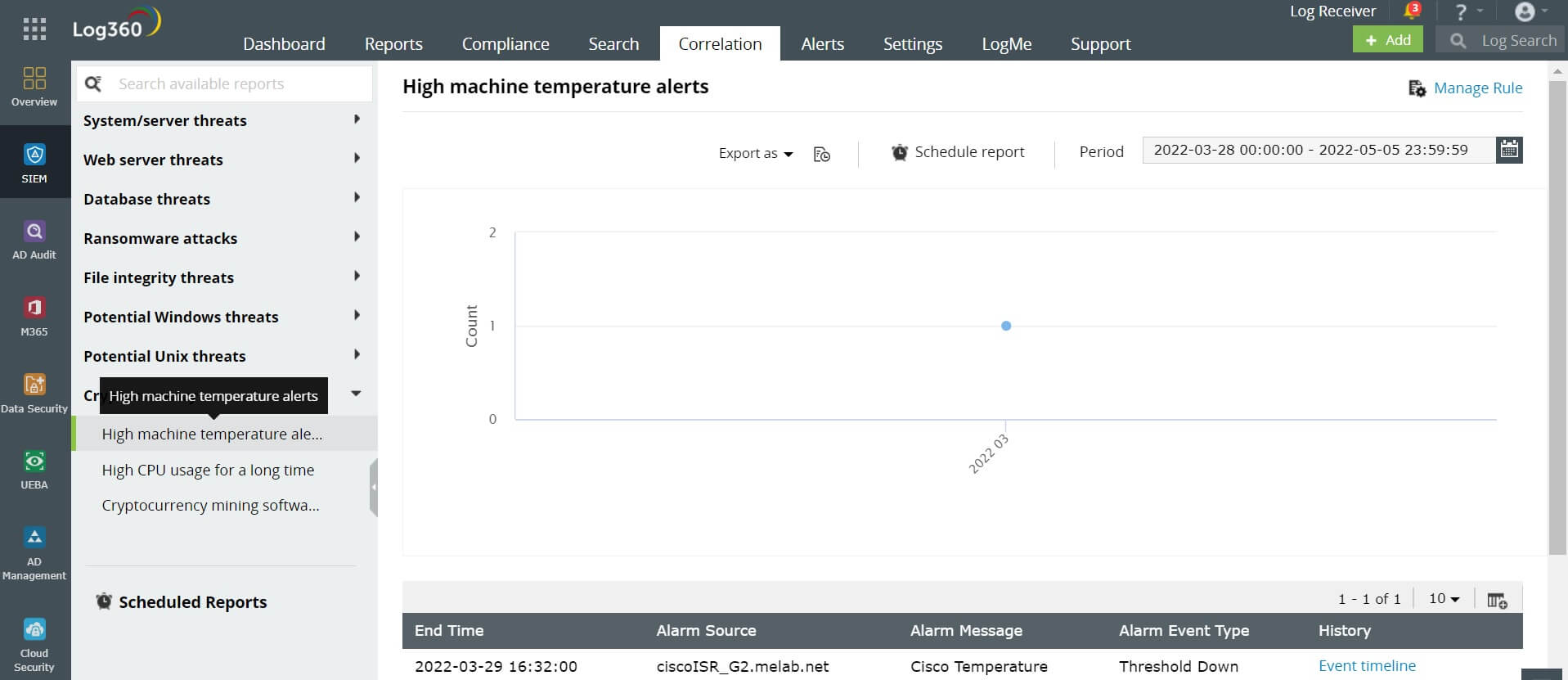
Let's now take a look at the default criteria for a cryptojacking alert in Log360.
When a device violates the threshold temperature five times in an hour, an alert will be sent to the security analyst.
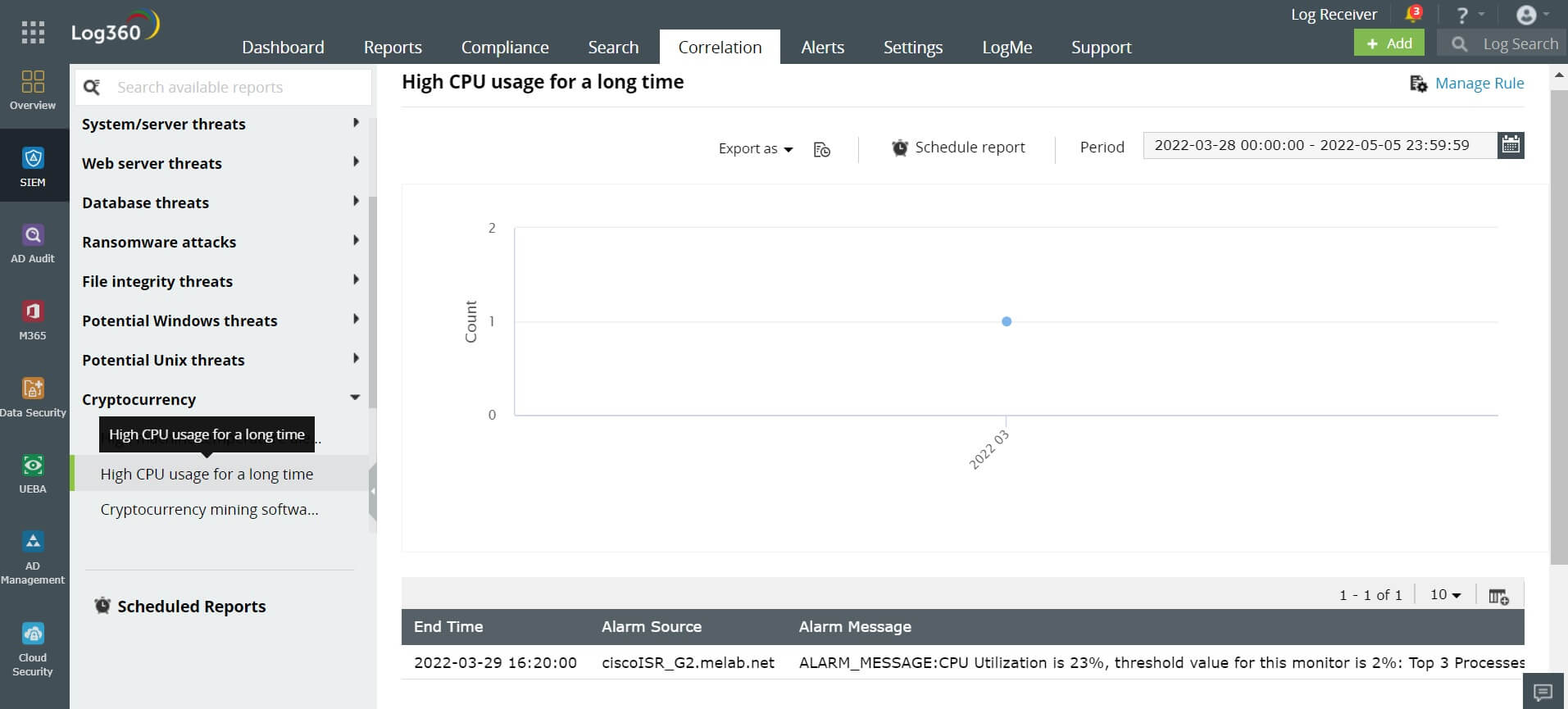
When a device utilizes the CPU beyond the threshold level three times within 30 minutes, the analyst will be alerted.
In your device, whenever a Windows process containing a name such as bitcoin-qt, cgminer, tbalance, bfgminer, coin-miner, bitmoose, and AwesomeMiner are started, the security analyst will be alerted. These processes indicate that a cryptomining code is running on your device. Organizations generally don't allow the use of their resources for mining cryptocurrencies. If this process starts on your device, it's a concern for the security analyst. This means that, without your knowledge, the malcode is using your device's resources to mine cryptocurrencies, and your organization's security analyst needs to be alerted.
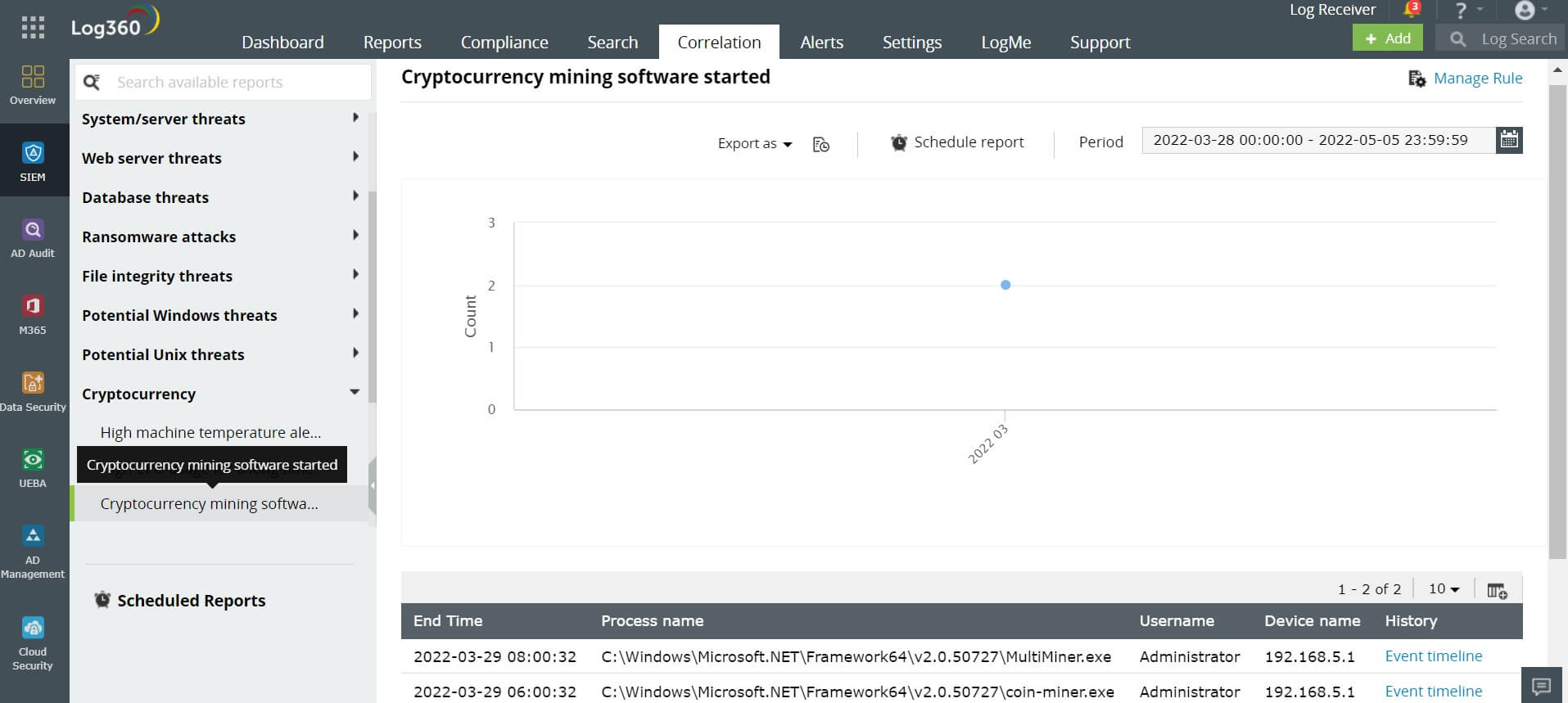
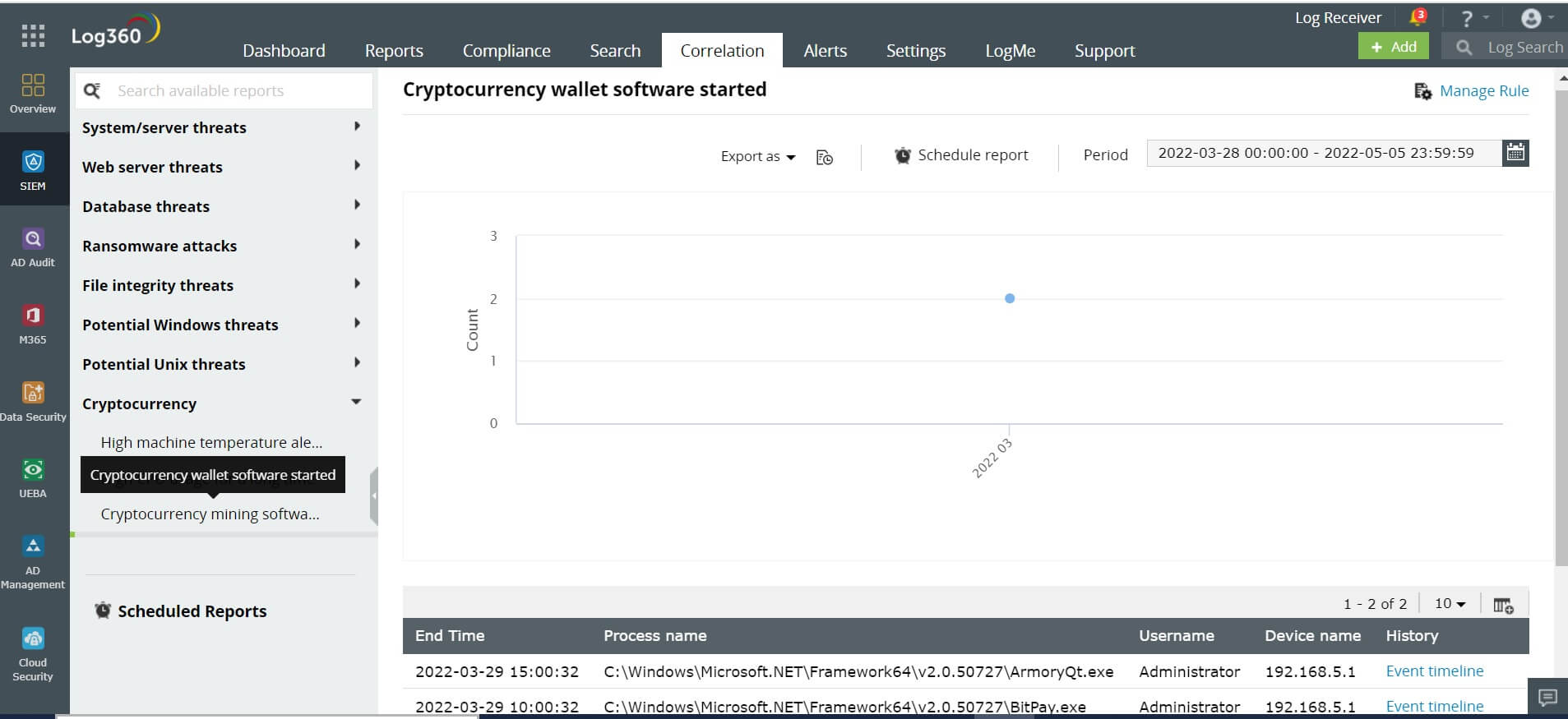
Whenever a cryptojacking software starts in your device, it will simultaneously start the wallet software to collect, send and spend the mined cryptocurrencies. In your device, if a Windows process with a name such as electrum, BitPay, Ethereum wallet, Armory-qt, and multbit-hd starts, the security analyst will be alerted.
To fully evaluate how a SIEM solution like Log360 can help defend your organization against various cyberattacks, including cryptojacking, schedule a personalized demo. Thanks for reading, folks!
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.