In System Monitor (Sysmon) version 13, Windows introduced the ability to detect advanced process tampering techniques such as process herpaderping and process hollowing.
This is a process injection technique where a malicious code is executed within the context of a legitimate process in order to evade defense setups like IDS/IPS systems, firewalls, etc. A threat actor performs this technique by hollowing out an executable thread of a trusted process and replaces this with a malicious binary of their own. The kicker here is that the tampered process still points to a legitimate executable pathway. Process hollowing is conducted to achieve the tactical goals of Privilege Escalation and Defense Evasion.
Process Herpaderping is a relatively newly identified technique that works towards the goal of evading defenses. When a new process is created, antivirus solutions register a callback in the Windows kernel. At this point, a security product will investigate the file that was used to map the executable and conclude if execution of the process can continue. Note that this kernel callback is invoked when the initial thread is inserted, not when the process object is created. This creates a window of opportunity for the threat actor to first create the process, modify the contents, and then create the initial thread.
For example a hacker might run a Rubeus program in the space of a legitimate Firefox process. If security solutions scan processes before the creation of the initial thread, they would fail to identify the modification in the process. Sysmon 13 aims to call this herpaderping to attention through the introduction of Event ID 25.
Here's a breakdown of the steps that will lead to the generation of Event ID 25. You can use the following steps to generate the event to test if it reflects in your system.
The new executable then runs in the address space of the target process and waits for the target process to terminate. This will lead to the generation of Event ID 25, the description for which reads as "Image is replaced."
If you view this in the Event Viewer, these are the fields that pop up so you can dive into the forensics of it.
| Field | Description |
|---|---|
| UtcTime | Time in UTC when the event was created |
| ProcessGuid | Process GUID of the process that was tampered with |
| ProcessId | Process ID used by the OS to identify the process that was tampered with |
| Image | File path of the process that was tampered with |
| Type | The type of tampering detected |
| User | The name of the account in which the process tampered with runs |
Stay tuned for more Sysmon Event ID updates that can help you detect more techniques hackers use to compromise your network.
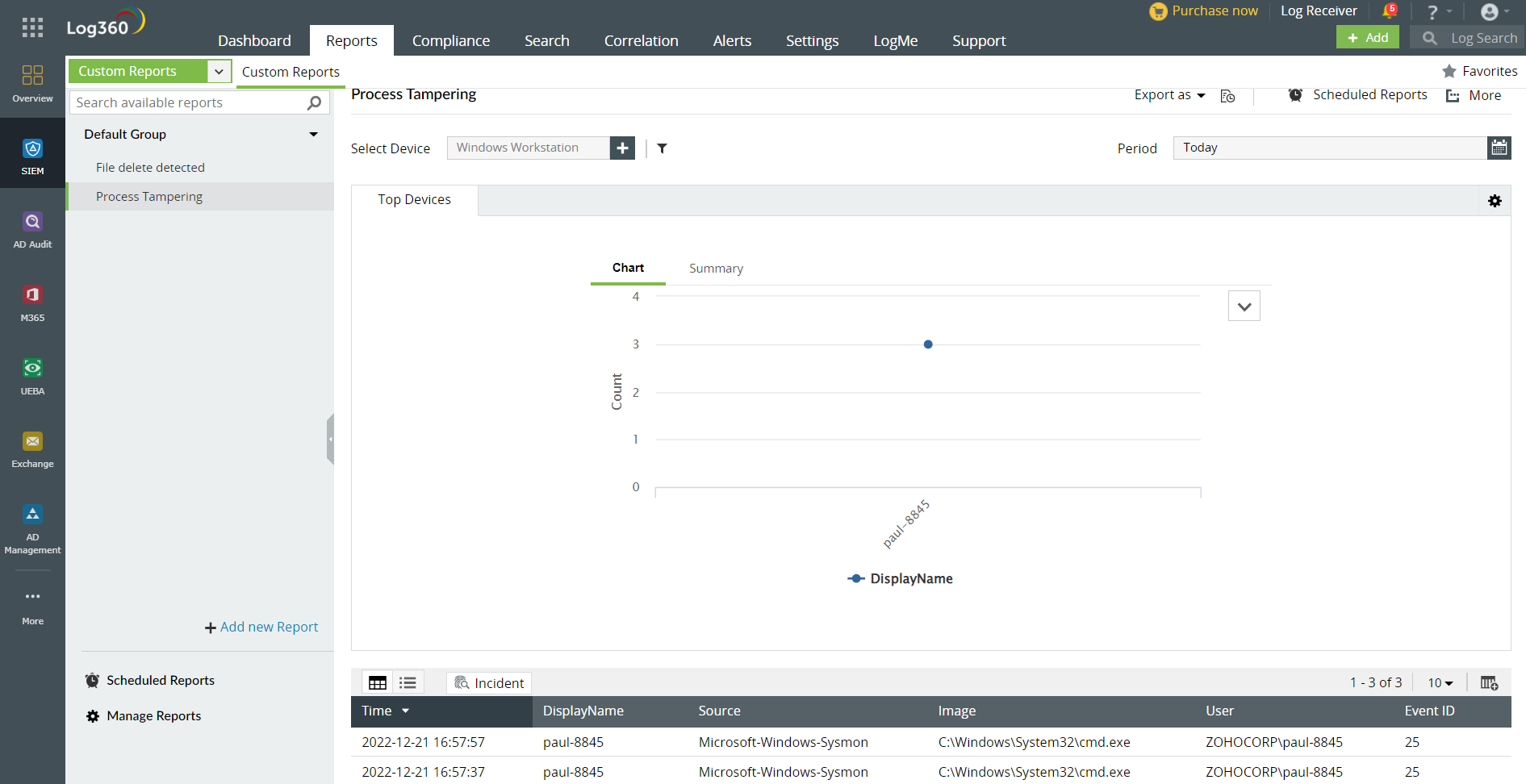
Fig 1: Log360 detection of Process Tampering with Sysmon Event ID 25
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.