Have you ever wondered at exactly what stage cyberattackers consider their attack to be successful? Is it when they gain privileged access, or is it when they evade the security defenses of the organization?
The real success of a cyberattack is when the attacker can remain undetected within the target environment and continue to establish communication with the compromised systems in the network to corrupt it in multiple malicious ways. In order to maintain this impregnable communication channel, cybercriminals use command and control (known as C&C or C2).
In this two-part blog series, we'll shed light on various facets of the command and control attack, from its definition to detection.
Let's begin by learning what C&C tactics are.
C&C is a technique used by cyberattackers to establish and maintain discrete communication with compromised devices in the target network.
The attacker employs a malicious C&C server to communicate with infected machines over the target network. This C&C server is also used for receiving the desired data or payload back from the infected systems.
The attacker usually tries to impersonate the normal, expected traffic to avoid any detection within the network. The C&C servers can be further used by the adversaries to create a network of infected machines called botnets to perform malicious activities such as data exfiltration, a distributed-denial-of service (DDoS) attack, cryptocurrency mining, or network shutdown.
There are multiple ways in which an attacker can establish command and control over the target network covertly. Here are six ways this dominance can be established:
Adversaries may discretely communicate using application layer protocols with a compromised computer to control them remotely. They can insert malicious commands and the results of those commands within the existing protocol traffic between the client and server. This helps them to avoid any suspicion or detection, making it easier for them to blend in and pivot through the target network.
Application layer protocols like web protocols, mail protocols, DNS, and FTPs may be exploited by adversaries.
Adversaries may opt for encoding data using a standard data encoding system. This makes it difficult to detect the traffic in the network. Data encoding can be achieved using ASCII, MIME, Unicode, or other binary-to-text and character encoding systems.
Adversaries may communicate using non-application layer protocols between the infected device and the C&C server within a network. Since the non-application layer protocols are not generally monitored, it makes it easier for attackers to establish covert communication.
Non-application layer protocols like Internet Control Message Protocol (ICMP), User Datagram Protocol (UDP), Serial over LAN (SOL), and Socket Secure (SOCKS) may be exploited by adversaries.
Adversaries may attempt to obfuscate infected devices and C&C traffic to make it harder to be detected. They may use tools like FlawedAmmyy to muddle the initial parts of the C&C channel, making the content almost imperceptible and difficult to identify or decipher. Other methods to avoid detection include using steganography techniques, impersonating legitimate protocols, or adding junk data to protocol traffic.
Adversaries may use legitimate remote access and desktop support tools such as Ammyy Admin, TeamViewer, AnyDesk, LogMeIn, GoToAssist, VNC, and others to establish interactive command over target devices in the network.
Adversaries may establish command and control channels on air-gapped host systems by using removable media such as USB drives to transfer commands from system to system. Here, the internet connected system is compromised first and the second system is compromised through lateral movement by relaying commands by using replication through removable media.
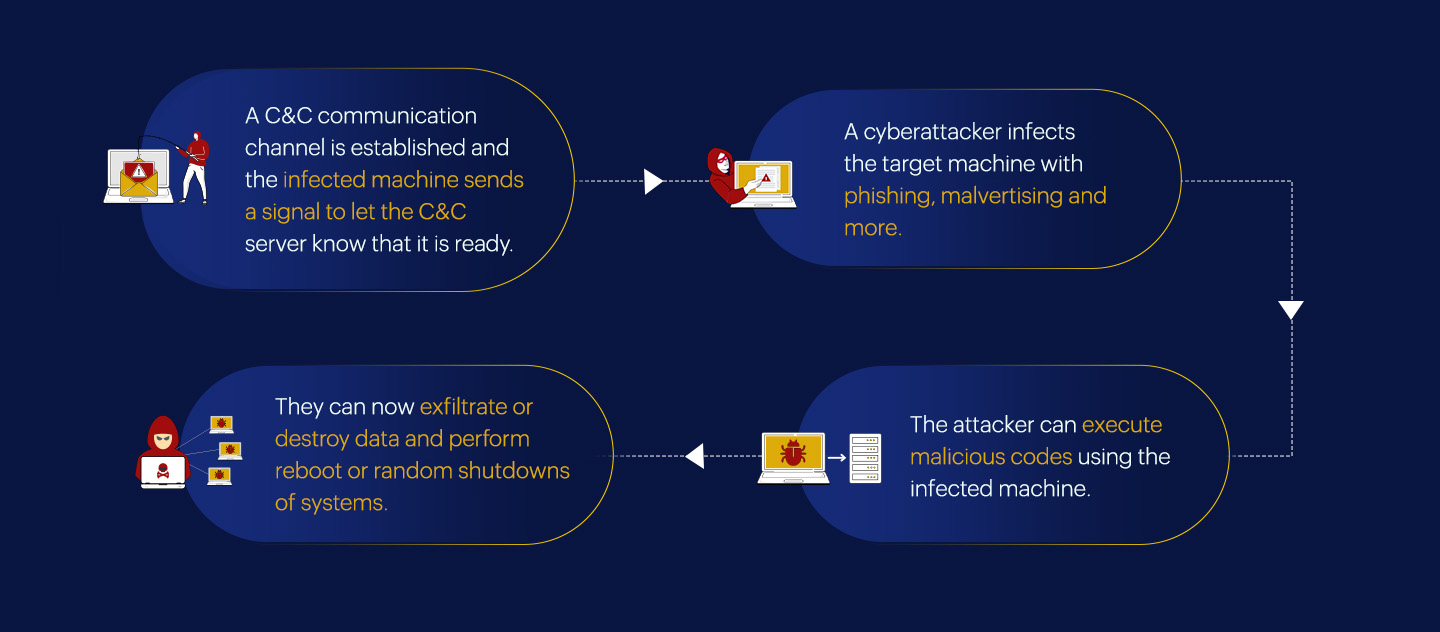
To establish a C&C communication, the attacker first needs to gain entry into the organization's network. This can be achieved using some of the following tactics:
Once initial access is achieved, the attacker establishes the command and control communication in the following steps:
The malicious code used to establish the C&C communication will advance further to other systems in the network and create a network of compromised systems called botnets. Through this, the attacker can easily have a lateral movement inside the network.
Now you should have a sound understanding of what C&C is and how adversaries use it to infiltrate a network and execute an attack.
Interested to learn more? Watch out for our second and final part of this blog series to learn about Indicator of Compromise and other detection and attack prevention techniques using a SIEM solution. Stay tuned!
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.