If you're an Australian entity that is not planning to implement the Essential Eight yet, you might want to rethink your stance. According to a survey by BeyondTrust, even though it is not a mandate, nine out of ten organizations in Australia aim to align their cybersecurity strategy with the Australian Cybersecurity Center's (ACSC) Essential Eight. Like any other compliance standard, organizations are facing challenges while implementing the required security controls. Around 63% of the survey's respondents chose implementing the first mitigation strategy, application control, as their biggest challenge.
The Essential Eight Maturity Model will help organizations implement the Essential Eight. It helps organizations gauge their security maturity and classify themselves into one of four maturity levels. The goal is to graduate from one level to the next over time.
This blog series will consist of four parts and is written to help organizations better understand the steps they need to take to go from one maturity level to the next.
In the first part, we will explore:
Published in 2017, the Essential Eight is a cybersecurity framework created by the ACSC, and it cites eight security measures or mitigation strategies organizations can implement to protect against cyberthreats and address security incidents. These have been picked from those listed in the cybersecurity framework, Strategies to mitigate cybersecurity incidents, put out by the ACSC in 2010.
The Essential Eight Maturity Model (EEMM) defines four maturity levels for organizations based on their ability to address the risk caused by threat actors, and the tradecraft or techniques used by them. The four maturity levels help organizations identify their exposure to cyber risk and focus on mitigating it.
Before implementing the EEMM, organizations should first assess their current maturity level. They should then decide on a target maturity level and try to achieve it across all eight mitigation strategies before moving on to the next maturity level. Here are the four maturity levels of the EEMM:
Maturity level assessment is critical to the effective implementation of the Essential Eight. The ACSC outlines a detailed assessment procedure to be followed by assessors and system owners to check the effective implementation of the Essential Eight security strategies. The term assesor is used to refer to the assessing body or personnel, and the term system owner is used to refer to the organization being assessed.
The EEMM provides the option of implementing alternative or compensatory controls to the prescribed measures. However, organizations must have sufficient proof that these alternatives ensure equal protection to the security control they are replacing.
There are four stages for carrying out the assessment procedure:
The image below illustrates which of the stages are carried out before, during, and after the assessment.
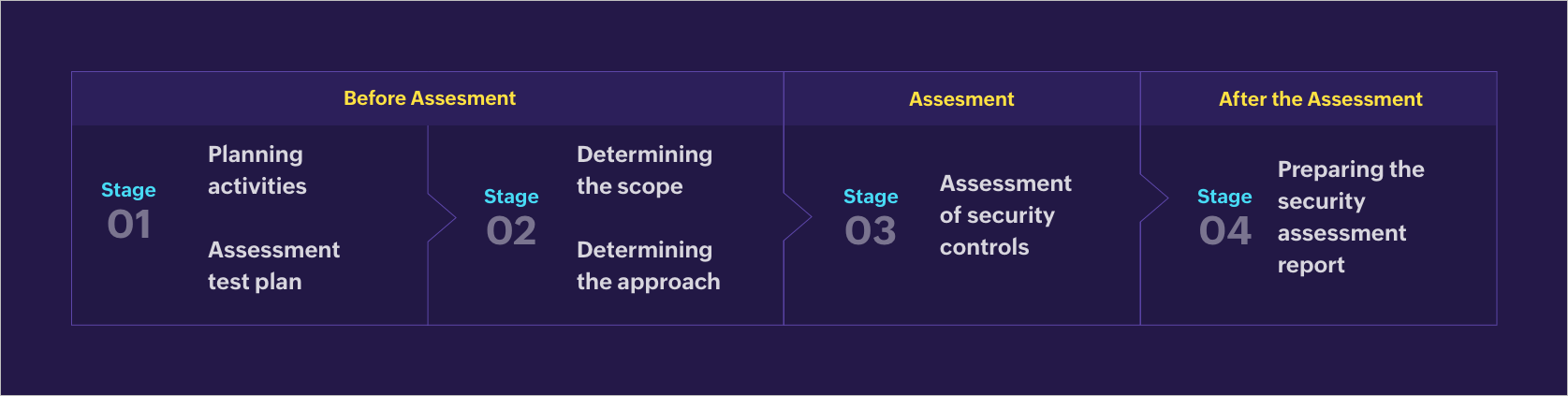 Three stages involved in the Essential Eight assessment procedure
Three stages involved in the Essential Eight assessment procedure
Let us briefly look through each one.
There are two steps to be taken at this stage:
Planning activities: The assessor must speak with the system owner and come up with suitable assessment planning activities, like identifying the permissions required to run scripts or use tools to carry out assessments, discussing system classification and the scope of the assessment, establishing the involvement of MSPs or other providers in managing certain aspects of the system and their points of contact, and more.
Creating an assessment test plan: The assessor must also develop an assessment test plan and share it with the system owner. The ACSC provides an assessment test plan template, which can be found here.
There are five steps the assessor must take to measure the assessment scope:
Identify the system owner's target maturity level.
Familiarize themselves with the security requirements of that level.
Request an approximate percentage breakdown of the operating systems used on workstations and servers.
Determine the assessment's duration and any milestones the assessor and system owner might want to record.
Document the scope and add it to the security assessment report.
The assessor must determine appropriate testing techniques, either qualitative or quantitative, and tools to carry out the assessment. Qualitative methods can include documentation reviews or interviews with the system security administrator or manager. Quantitative methods usually involve system configuration reviews and the use of scripts and tools to assess the effectiveness of the controls installed.
The ACSC recommends quantitative methods over qualitative methods since scripts or tools can better gauge how well the controls have been implemented across several workstations and servers installed in the network.
Assessors can use tools provided by the system owner if appropriate tools are not present with them. Assessment limitations, if any, should be documented and added to the security assessment report.
The Essential Eight assessment is prescribed based on the EEMM. Once the assessor has determined the scope of the assessment based on the maturity level of the organization, they must check if all eight security strategies are implemented as per the requirements of that level. The ACSC has prescribed specific guidelines and considerations for individual security controls under each maturity level.
The guidance is cumulative in nature. This means that organizations aiming for Maturity Level Two must follow the guidelines for both levels one and two. To understand this better, the table below shows how the implementation of application control (which is the hardest to implement) will be assessed across organizations of different maturity levels.
Application control is a measure used to prevent the execution of malicious code, i.e., malware in systems, identify applications that are allowed to be used, and develop controls to ensure only those are accessible. To implement this measure, organizations need to gain an overview of all applications and processes run by users in the network.
The assessor must use the Essential Eight report template provided by the ACSC to prepare the security assessment report.
Keep an eye out for the next part in this series, which will focus on the different steps an organization at Maturity Level Zero has to take to reach Maturity Level One.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.