A set of security standards known as the Payment Card Industry Data Security Standard (PCI DSS) is intended to ensure that any organization that handles credit card data keeps a secure environment. It applies to all organizations that process, store, or transmit cardholder data, aiming to protect against data breaches and fraud. Compliance involves adhering to specific requirements, which cover areas like secure network maintenance, data protection, access control, and regular monitoring. Non-compliance can result in large fines and penalties.
So, here's how file integrity monitoring (FIM) helps in ensuring a few requirement of the PCI DSS. Several sections of the standard specify FIM as a requirement for PCI DSS compliance, including:
1. Requirement 10: Track and monitor all access to network resources and cardholder data.
Using FIM tools to detect accesses and modifications to sensitive files and configurations is part of meeting this requirement.
A good SIEM solution accomplishes overall file and folder monitoring by assessing executable files, folders, system configuration files, content files, zipped files, zipped folders, and more. Fig. 1 shows how this is done in ManageEngine Log360.
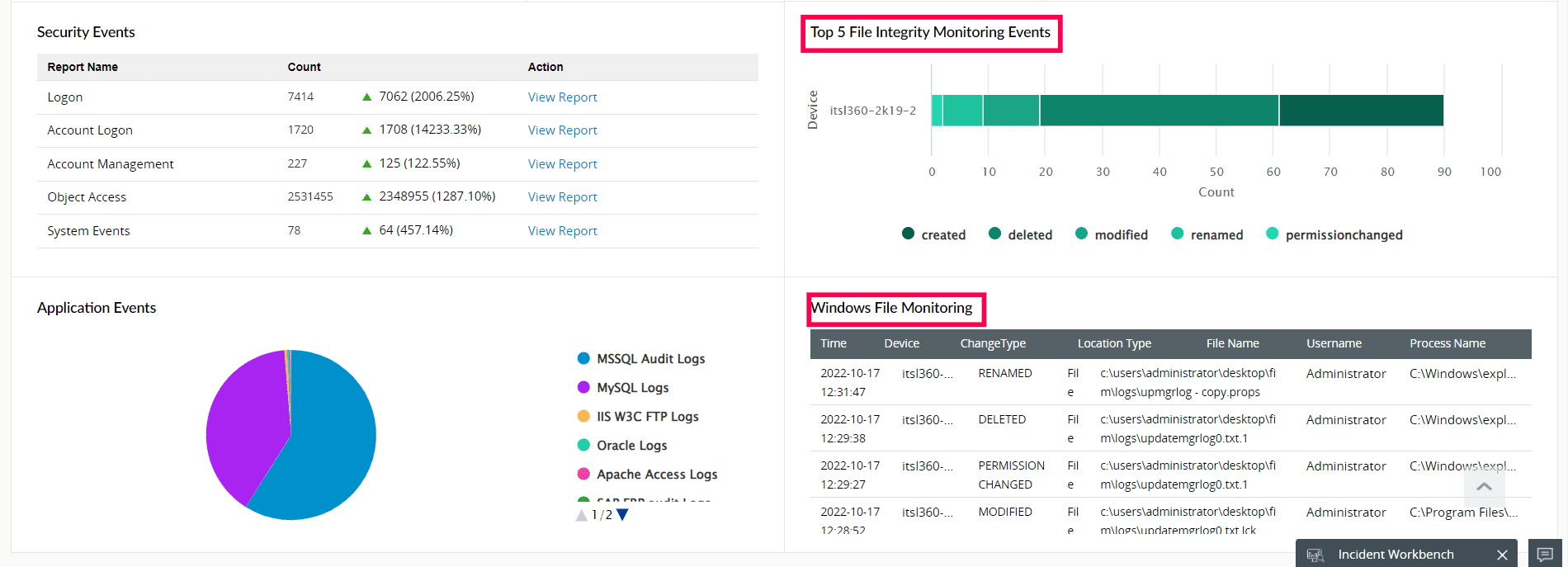
Figure 1: File Integrity Monitoring dashboard view
2. Requirement 11.5: To detect unauthorized modifications to important system, configuration or content files, use the change detection mechanism. Configure the solution to compare crucial files at least once a week.
Changes, additions, and deletions of important files are managed by change detection tools, such as FIM tools, which alert authorized individuals when such changes are detected.
Also, an integrated ticketing module, part of Log360's end-to-end incident management system, assists in assigning tickets to security administrators, monitoring their progress, and ensuring accountability throughout the incident resolution process (Fig. 2). It also includes an automatic remediation framework that can associate workflows with alert profiles. These workflows get executed automatically when a correlation alert is triggered to remediate the incident.
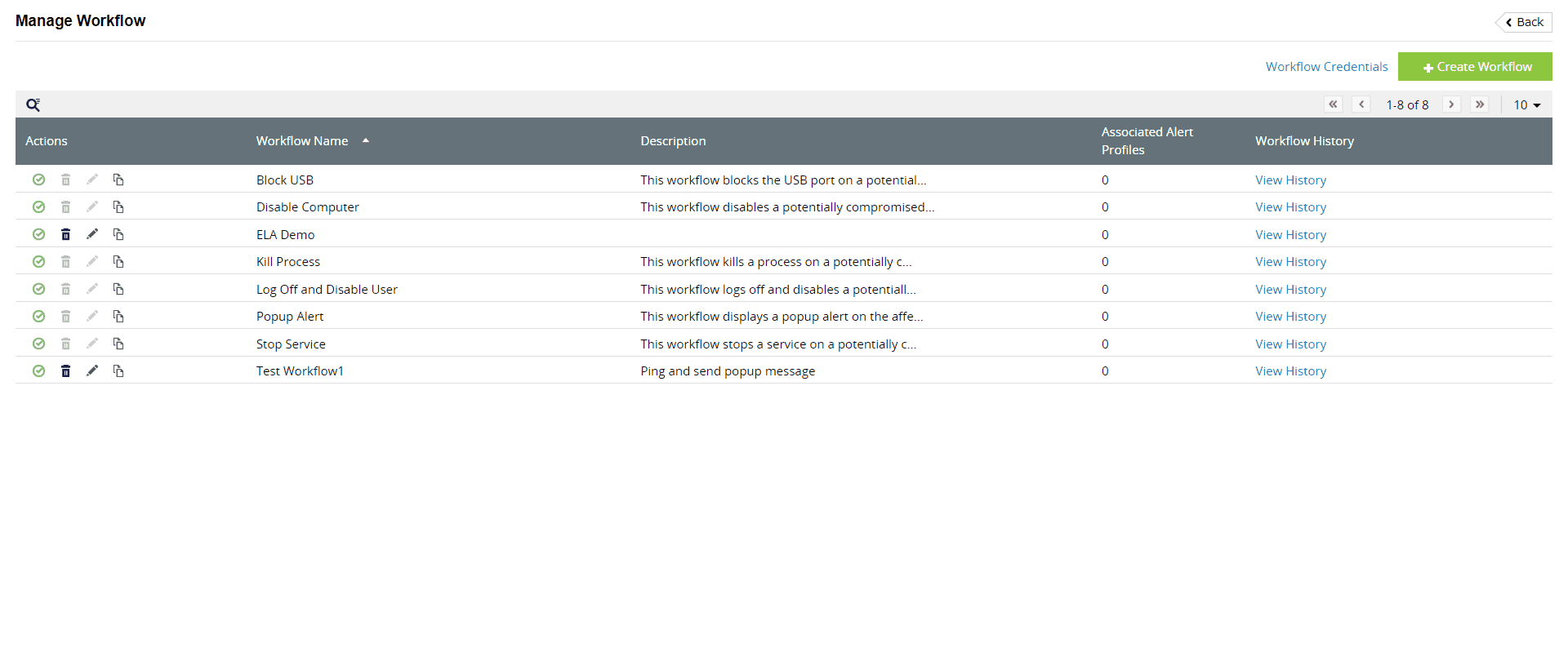
Figure 2: FIM incident remediation workflow in Log360
Also, to know how FIM helps in ensuring other common compliance mandates, check out this page.
Ready for the next step?
Are you looking for to protect your organization's sensitive information from being misused? Sign up for a personalized demo of Log360, a comprehensive SIEM solution that can help you detect, prioritize, investigate, and respond to security threats.
You can also explore the solution on your own with a free, fully functional, 30-day trial of Log360.



