Picture this: Your organization's network is a bustling city, full of files scurrying around like caffeinated squirrels on a mission. Now, imagine you had a superhero sidekick that not only watched over these files but also wore a cape made of compliance standards and a utility belt loaded with customizable templates. Enter file integrity monitoring (FIM), the unsung hero of the cybersecurity realm, here to bring order to the chaos of data security.
In a world where files have secret lives of their own—reading, writing, changing owners like they're in a game of digital hot potato—FIM is the all-seeing eye that keeps tabs on their every move.
Buckle up, because this guide is your backstage pass to explore how FIM can benefit your organization, reduce costs, and mitigate breach risks, while also delving into various FIM use cases that showcase its indispensability.
What are the critical files that FIM can help monitor?
Before diving into what FIM can accomplish, let's understand why it's important by understanding some examples of sensitive data that your files could hold. Here are a few.
- Personally identifiable information (PII): Information that can be directly tagged to any customer or employee can be categorized as PII and is extremely sensitive. Credit card information, patient data, social security numbers, certificates, customer details, and more can all be critical. Any leakage of this data can result in major compliance breaches.
- Intellectual property (IP): Protecting files related to IP is important, as the development of IP can require years of research and hard work. Loss of such data can compromise your organization's competitive advantage.
- Log files and historical events: Log data provides analysts with detailed insights during root cause analysis and forensic analysis. Any tampering of these files can result in the team overlooking the foothold that attackers possess within your network.
- System files: System files are critical. If attackers gain access to these files, it can lead to instability of your system, application failures, and potentially catastrophic data loss.
- Financial data: If any financial data of your organization is unofficially revealed—such as ledgers, investments, and private assets—it could lead to potential stock fluctuations and stakeholder disapproval.
Reducing costs with proactive threat detection
Cost is one major factor of concern to every security manager. Let's see the capabilities of FIM tools that can aid your team to reduce cost.
1. Early threat detection:
FIM enables your security analysts to monitor a plethora of file activities, including reads, modifications, creations, movements, copy-and-pastes, deletions, permission changes, and owner changes. By staying vigilant on these activities, your team can detect potential data threats at an early stage, preventing the escalation of security incidents.
2. Streamlining investigations:
FIM provides insights of the top file activities based on users and also identifies top users with failed accesses. This information proves invaluable during investigations, allowing your team to identify quickly and respond to suspicious user behavior. This proactive approach not only saves time but also reduces the costs associated with incident response.
Mitigating breach risks with comprehensive monitoring
Cyber breaches are literal nightmares for SOCs worldwide. How can FIM tools reduce such breach risks?
1. Customizable templates:
FIM allows you to create custom templates based on compliance standards, operating systems, and file extensions. This feature significantly reduces redundancy in configuration across multiple devices, ensuring a standardized and efficient monitoring system. Compliance is a critical aspect of data security, and FIM ensures that organizations stay ahead of regulatory requirements.
2. Real-time visibility:
A comprehensive dashboard consolidates all FIM data into a single space, presenting information through visual charts and graphs. You gain real-time visibility into file activities, enabling you to make informed decisions promptly. This level of transparency is instrumental in identifying and mitigating breach risks before they can inflict severe damage. The below image shows the detailed dashboard available in Log360 Cloud that provides comprehensive visualization of the network.
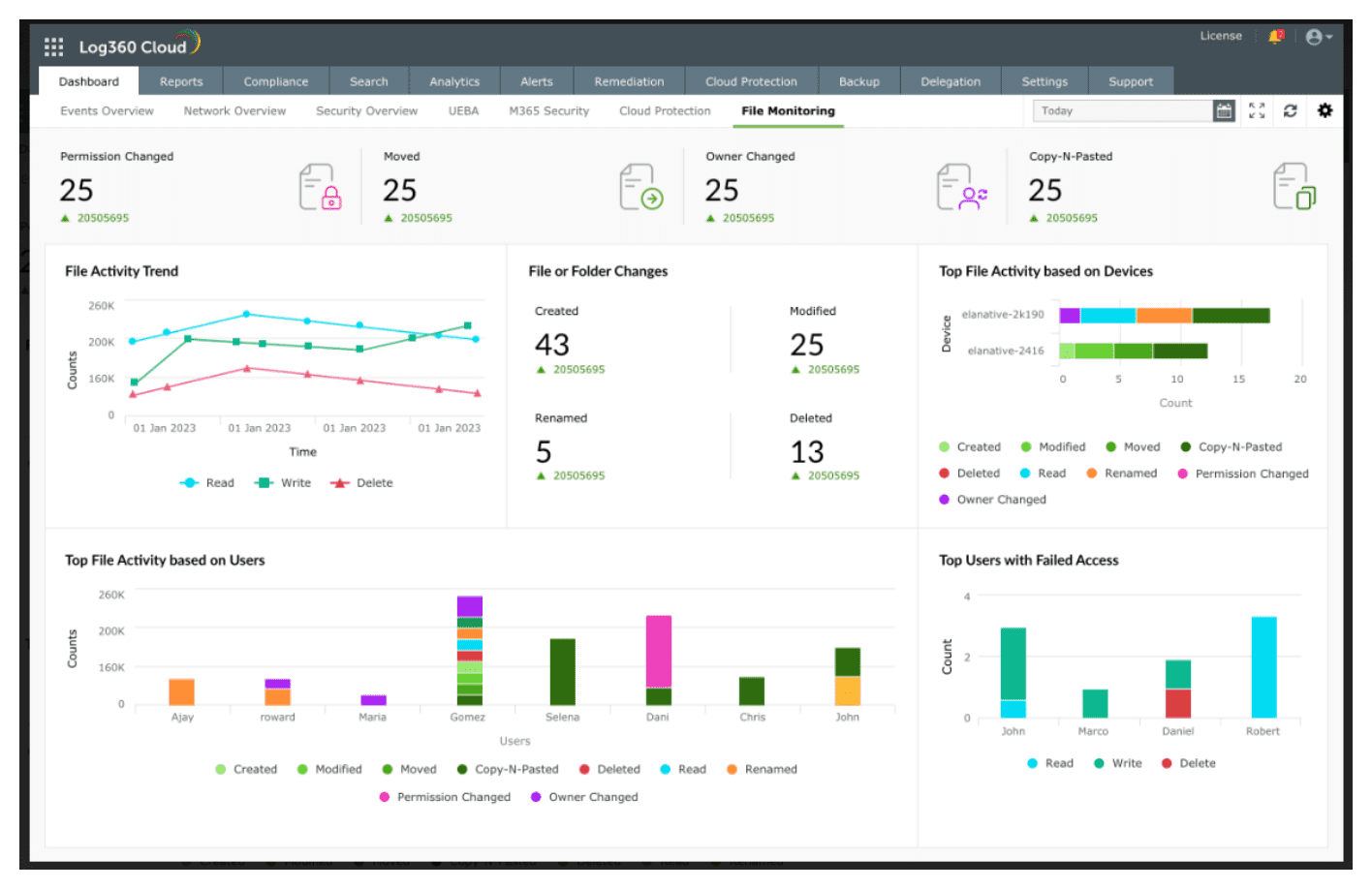
FIM use cases: Unveiling the versatility of FIM
We've explored the ways in which FIM can aid the team in reducing cost and risk. Now let's explore some use cases for FIM tools.
1. Insider threat detection:
FIM plays a pivotal role in identifying insider threats by monitoring unauthorized or unusual file activities by employees. SOC teams can swiftly respond to potential data exfiltration attempts or malicious activities from within the organization. For instance, System32 files are critical because they contain essential system files and libraries necessary for the Windows operating system to function properly, including vital components such as device drivers, system configurations, and dynamic link libraries (DLLs). Deleting or corrupting System32 files can render the operating system inoperable, leading to system instability, application failures, and potentially catastrophic data loss. FIM tools can be used to track, detect, and alert for such modifications.
2. Ransomware protection:
By tracking file modifications and creations, FIM tools act as a robust defense against ransomware attacks. Any abnormal spike in file changes will trigger immediate alerts, allowing SOC analysts to intervene and prevent the encryption of critical files. ManageEngine Log360 provides File Monitoring reports that give detailed insights into file activity—such as File Modified, File Deleted, File Renamed, and more—which can help detect ransomware activity.
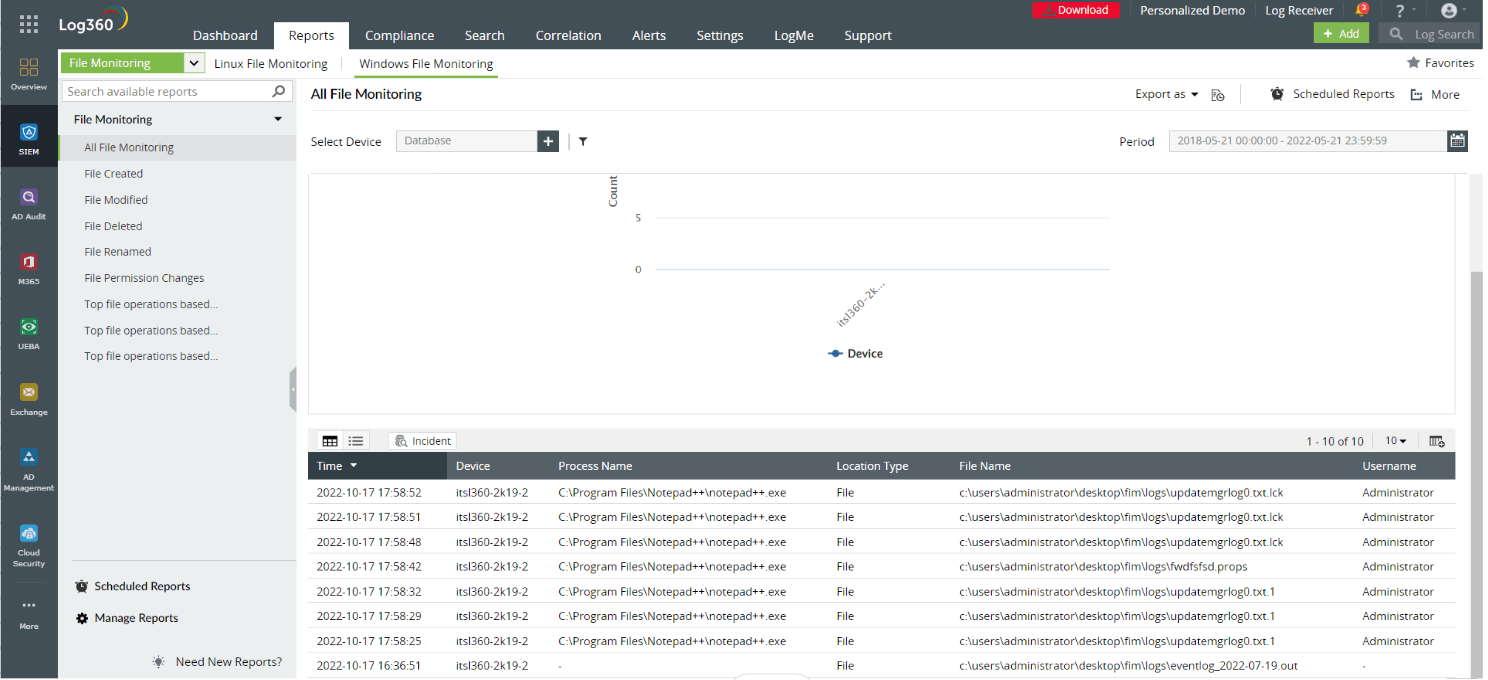
Log360's All File Monitoring reports found under File Monitoring activity reports.
3. Compliance assurance:
A FIM tool's customizable templates ensure that organizations adhere to regulatory compliance requirements. This is crucial for sectors such as finance, healthcare, and government, where stringent regulations demand continuous monitoring. This is where file integrity monitoring is leveraged; ManageEngine Log360 provides comprehensive File Audit reports for all the major compliance mandates.
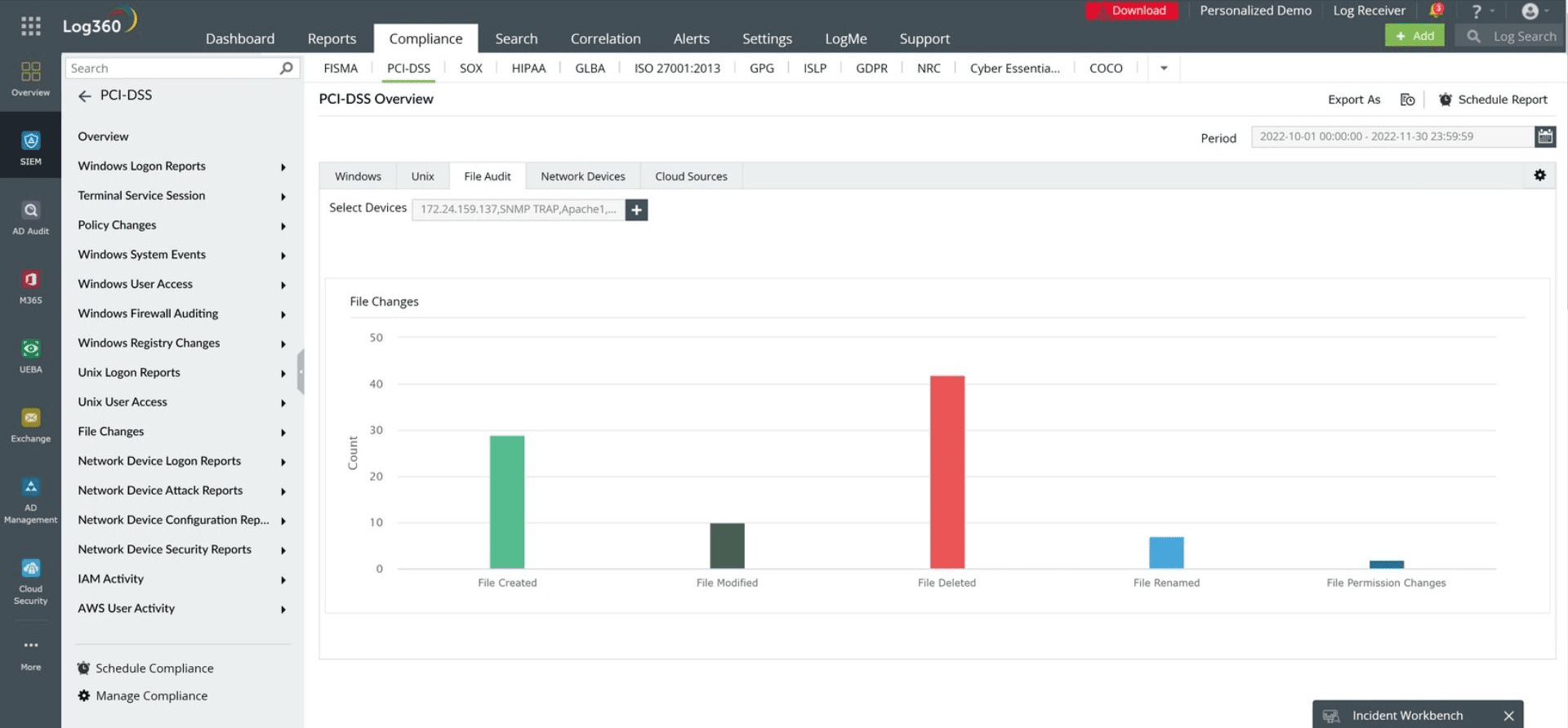
Log360's File Audit report for PCI DSS compliance.
Your next step
File integrity monitoring (FIM) has emerged as an indispensable strategy for SOC managers seeking to enhance data security, streamline operations, and reduce costs. Its ability to provide real-time visibility, early threat detection, and customizable templates makes it a cornerstone in the defense against cyber threats. By leveraging a FIM tool, SOC managers can fortify their organization's data security posture, ensuring a robust defense against the ever-evolving threat landscape.
The file integrity monitoring feature available on Log360 Cloud gives you a microscope by enabling granular file visibility across your network. The latest comprehensive dashboard allows you and your team to visualize trends based on both file and user activity. Always be a step ahead: Download or sign up now.



