On February 23, 2022, just hours before the Russian invasion, several Ukrainian enterprises were hit with a ransomware note, but it turned out to be a smokescreen for more deadly, disk-wiping malware running in the background. The HermeticWiper is disk-wiping malware that targets Windows users with the sole intent of destroying the boot record and rendering the system inoperable with its data permanently lost.
HermeticWiper remains prominent among recent disk-wiping malware like CaddyWiper, IsaacWiper, and WhisperGate. This malware variant was detected and reported by ESET Research and is significant for quite a few reasons.
The malware file is initially dropped to the system as a compressed package and it decompresses to create the EaseUS driver file. It begins execution by parsing NTFS structures to enumerate all physical drives. The driver is then loaded and runs as a service. With the collected data of physical drives, the driver is used to overwrite the master boot record (MBR) and restart the system. This flowchart is a basic representation of the different stages in a HermeticWiper malware attack.
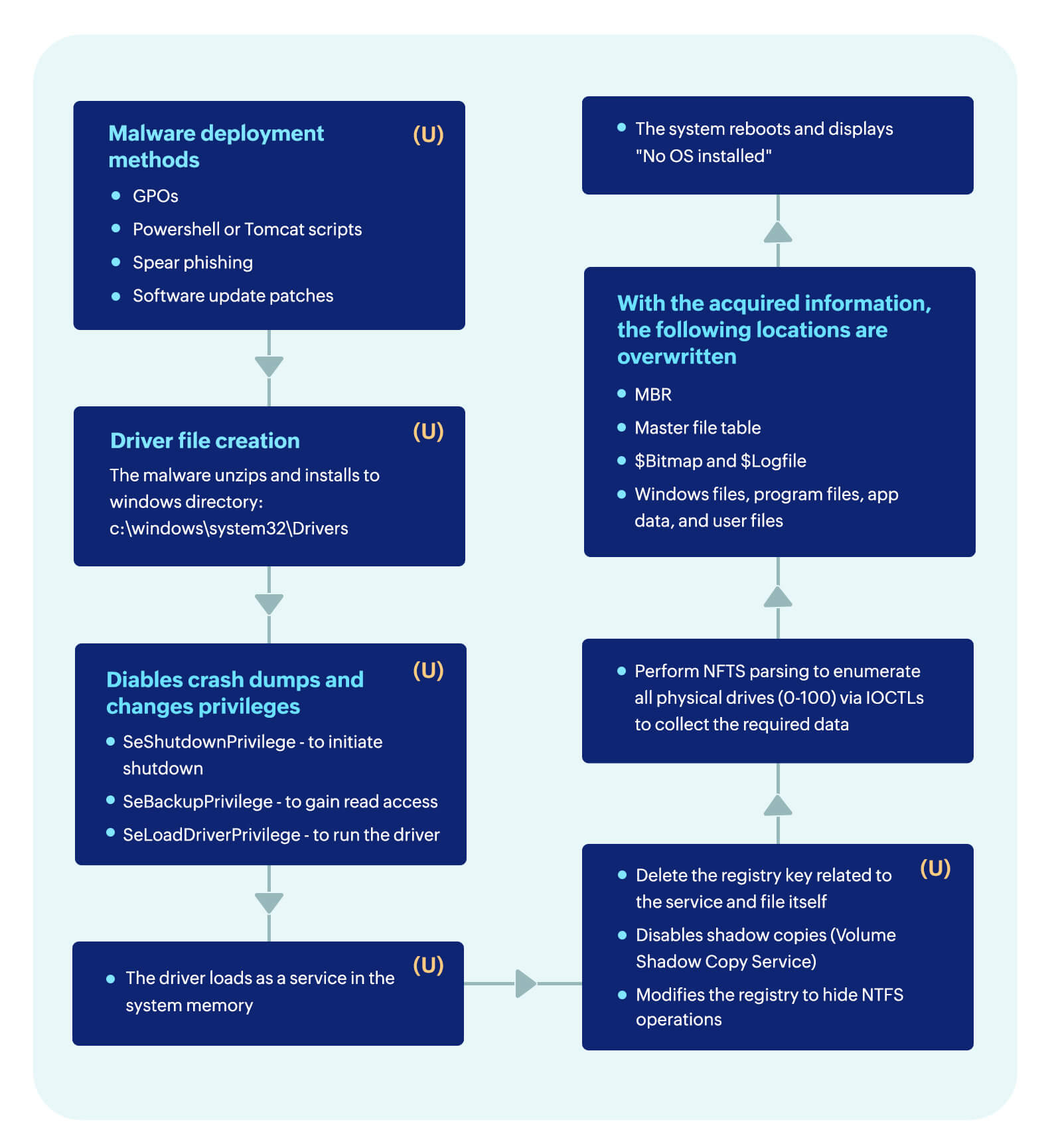
Looking closely at the flowchart above, you can see HermeticWiper performs actions to thwart forensic analysis by wiping logs and registries. This is why it's vital to detect and report on the attack quickly and take appropriate action. The stages marked with a (U) in the attack process are examples of possible use cases for detection using a monitoring solution. Let's see how ManageEngine Log360, a comprehensive SIEM solution, can help in these scenarios.
Malware deployment: Log360 can monitor suspicious activity in AD, read PowerShell scripts, detect privilege escalations and account compromises, and trigger alerts in real time.
Driver installation and creation: With file integrity monitoring, you can track unauthorized file creation, deletion, and modification; log tampering; and a variety of other things. Custom alert profiles can be set to keep an eye on sensitive Windows driver directories.
Registry changes: Sysmon auditing enables tracking of registry changes.
Process creation: The anomaly detection capability can help with detecting unauthorized processes that have been created or stopped.
HermeticWizard: Access requests and suspicious file transfer requests can be detected by tracking processes across network devices.
Moreover, incorporating IoCs to set alert profiles can help detect and tag HermeticWiper as soon as it attacks. A SIEM solution with threat intelligence feeds can automatically do this for you.
When the attack is detected, it requires immediate action from IT personnel before the attack spirals out of control. IT teams can effectively respond by blocking or logging off the user, stopping unauthorized processes, and isolating the infected host from the rest of the network. A robust incident response tool or security orchestration, automation, and response tool can support the SOC team with automated workflow-based investigation and responses as alerts are triggered.
HermeticWiper exemplifies how sophisticated the threat landscape is becoming. Ukraine has been a victim of many malware attacks in recent months as we watch the nation defend itself both on the battlefield and in digital space. With the looming threat of this cyberattack spreading to other countries, cybersecurity is more vital than ever.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.