The average annual cost of insider threats for organizations is $7.2 million, with incidents often taking over 85 days to contain. This highlights the significant financial and operational burden insider threats impose on organizations.
In this page, we will unveil the preventative strategies to mitigate insider threat and shed light on how file integrity monitoring (FIM) plays an important role.
What is an insider threat?
A security threat that comes from within the intended organization is known as an insider threat. Usually, it involves a current or former employee or business associate who misuses their access to privileged accounts or sensitive data on an organization's network. Malicious, or even ignorant insiders, include third-party vendors, contractors, and partners. The impact of insider threats can be severe, leading to financial loss, reputational damage, legal liabilities, and compromised data security.
Depending on their motives, insider threats can be unintentional or malicious. Insider risks that aren't purposeful can come from a negligent employee falling for a phishing attack. Intentional data theft, corporate espionage, and data destruction are examples of malicious threats.
Insider threat detection is crucial for protecting sensitive data and preventing security breaches from trusted individuals within an organization. It helps mitigate risks such as data theft, sabotage, and unauthorized access. Early detection ensures timely response and reduces potential damage.
Who are insiders?
Insiders are those who have authorized access to an organization's facilities, data, and systems because of their job or involvement with the organization. They are insiders in contrast to external entities, such as hackers or cybercriminals, who attempt to breach the organization's security from outside.
Insiders constitute a vital component of an organization's security environment, irrespective of their roles and affiliations. Although the majority of insiders are dependable people who follow the rules and principles of the organization, a tiny percentage could represent an insider threat because of their malicious intent, negligence, or inadvertent actions.
Here are a few examples of insiders:
- Employees: These are individuals who are employed by the company on a full-time, part-time, or contract basis. Employees may occupy a variety of roles, such as front-line staff members, managers, administrators, and executives.
- Contractors: Organizations frequently hire outside consultants, contractors, or suppliers to handle specific tasks like project management, software development, or IT support. During their engagements, these individuals—who are not permanent employees—may have access to sensitive data and systems.
- Partners: Collaborations, affiliations, and partnerships with other organizations may entail the sharing of infrastructure, data, or resources. In the context of collaborative projects or shared initiatives, anyone connected to suppliers, partners, or stakeholders are identified as insiders
- Temporary workers: Temporary or seasonal workers are employed by organizations to cover gaps in staffing or adjust to workload fluctuations. During their time with the company, these temporary workers could have access to specific resources and systems even if they are not full-time employees.
- Interns: Individuals that participate in apprenticeship programs or supervised training within the company in order to acquire real-world experience and skills are known as interns or trainees. During their training, they are regarded as insiders even if their access to critical data may be limited.
- Former Employees: Former employees may retain insider knowledge, access credentials, or residual access to systems and data even after they leave the company. Security issues may arise if access rights are not updated or revoked when an employee leaves.
- Board Members: Members of the organization's advisory committees or board of directors may be considered insiders since they are involved in strategic decision-making and supervision responsibilities. They might have access to materials pertaining to governance and private information.
Types of insider threats in cyber security
Insider threats are security risks that can emerge from a variety of sources and originate within an organization. Being well-versed in the various types will improve insider threat management. The following are some common types of insider threats(refer to figure 1):
- Malicious insider: These insiders are individuals within the organization who intentionally misuse the access privileges to harm the organization or for personal gain.
- Negligent insider: Due to their incompetence or carelessness, these insiders unintentionally present a threat. They might accidentally expose sensitive information, fall victim to social engineering attacks, or fail to follow security protocols. Despite their broad familiarity with security and IT regulations, they choose to disregard them, creating risk for the organization.
- Compromised insider: Legitimate users whose login credentials have been stoLen by external threat actors are known as compromised insiders.Phishing attempts, spyware, or other techniques may compromise their credentials, giving attackers unauthorized access to systems and data.
- Whistle bowler: A whistleblower is a person who comes out with information about misconduct, fraud, corruption, or other unethical activity occurring within a government agency or organization.Whistleblowers may not be seen as threats in the conventional sense, but they may unintentionally cause harm to the organization by disclosing private or sensitive information to the public or regulatory authorities.
- Third party insider: These involve people or organizations outside the company that have been given access to internal systems or data. They could be partners, vendors, or contractors whose activities potentially jeopardize the security of the company.
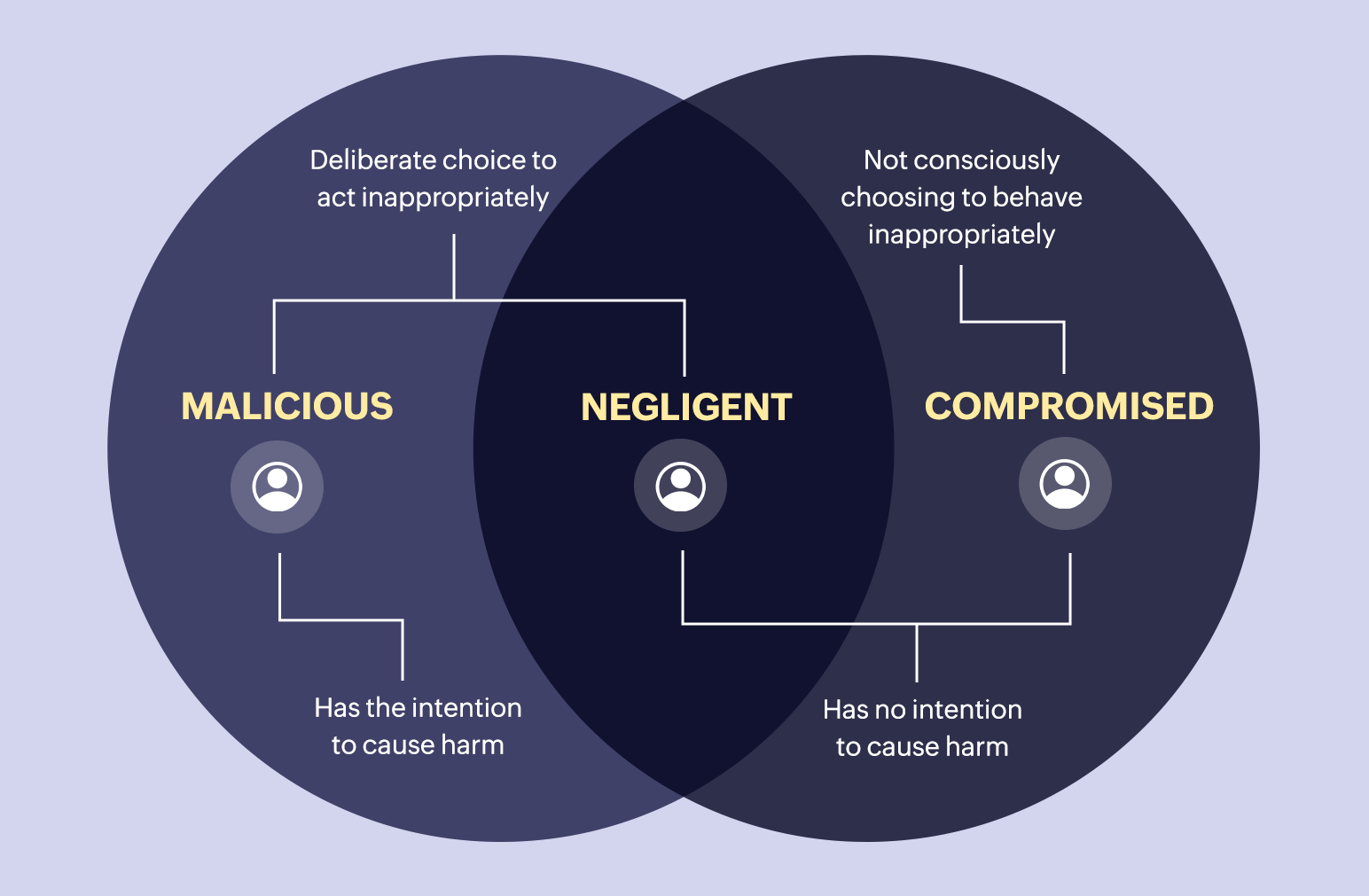
Figure 1: Types of Insider threat
What are insider threat indicators?
Here are a few potential insider threat indicators:
- Unusual access patterns: An increase in the amount of time spent accessing private data or systems after hours or on the weekends could indicate suspicious behavior. Also, usage of steel and old user accounts to access data can pose greater risk of insider threat.
- Unauthorized data exfiltration: It can be a cause for concern when large amounts of sensitive data, especially to external locations, are transferred without proper authorization
- Violations of security policies: An insider threat may be indicated by instances of password sharing,bypassing security protocols, or attempted disabling of security mechanisms.
- Multiple failed access attempts: Continuous attempts to obtain sensitive data or systems without authorization, particularly following a string of unsuccessful attempts, may indicate malicious intent.
- Unauthorized system modifications: Unauthorized modifications to software installations, system configurations, or other infrastructure elements may be signs of insider threats attempting to exploit vulnerabilities.
- Excessive privilege of access rights: Employees with unnecessary access privileges, particularly in sensitive areas of the organization's network or systems, may pose a greater risk of insider threats.
- Lack of compliance with policies and procedures: Insider threats can arise when adherence to established security policies fails, such as when required security training is not completed or when data management procedures are not followed.
How to detect insider threat?
Here are a few ways to detect insider threat:
- User activity monitoring: Implement tools and systems that monitor and assess user activity on the network, in systems, and in applications within the organization. This can involve monitoring the file access, data transfers, login/logout times, and system configuration changes.
- Anomaly detection: To spot unusual or suspicious behavior patterns that deviate from usual user activity, apply machine learning algorithms and advanced analytics. Anomalies could include unusual patterns of access, efforts at data exfiltration, or unauthorized system alterations.
- Insider threat programs: Establish specialized teams or programs to monitor, investigate and address internal threats. Clear policies, processes, and escalation paths must to be included in these programs for managing insider threat incidents.
- Security Information and Event Management (SIEM): SIEM platforms can help detect and correlate suspicious activities in real-time.Implement SIEM solutions that aggregate and analyze security event logs from various sources across the organization's IT infrastructure.
- Incident response planning: Create incident response plans and update them often. These plans should include steps for identifying, analyzing, and addressing situations involving insider threats. Make that the appropriate parties are informed, equipped, and trained to handle insider threats.
ManageEngine Log360 helps you detect; investigate; and respond to threats, while meeting compliance requirements.
How to prevent insider threat?
Here are a few best practices to be followed in order to mitigate insider threat:
- Clearly define your policies and procedures: Provide clear instructions to employees on permissible use policies, data management practices, and security protocols. Ensure that every employee is aware of their responsibilities with regards to sensitive data.
- Put role based access controls (RBAC) into practice: Restrict access to systems and sensitive data according to the roles and responsibilities of employees. Employees should only have access to the data required to carry out their duties.
- Track user activity: Use tools to keep tabs on user behavior, systems, and network of the organization.
- Implement strong authentication: Use MFA to add an extra layer of security to access private and sensitive information.
- Educate employees: Regularly train employees and conduct awareness campaigns to inform them of insider threat risks and teach them how to spot and report suspicious activity.
- Review and update security policies on a regular basis: It is imperative to periodically assess and revise security policies and processes in order to tackle emerging risks and vulnerabilities, as security threats and technology undergo constant evolution.
- Implement DLP solutions: Use DLP solutions to monitor and stop sensitive data from being sent outside of the company's network without authorization. Policies pertaining to the management of sensitive information can be enforced with the use of DLP solutions.
5 steps to utilize file integrity monitoring to detect and prevent insider threats
1. Configure the necessary resources: When setting up FIM, the network elements that need to be monitored, such as files, folders, and directory servers, need to be specified. This is especially useful for resources that store sensitive data and are more likely to be handled improperly.
2. Set up alert criteria:By ascertaining the users' regular usage behaviors, an alert criteria or threshold(such as permissions, sizes, and hash values) can be set by the users. Then, using this alert criteriaas a guide, FIM analyzes events occurring in real time. When an event crosses the set up threshold, an alert is generated and forwarded to the appropriate authority, who analyzes the issue and takes the appropriate action to rectify it. These alerts may include details such as the type of change, the affected files or directories, and the time of the event.
ManageEngine Log360 provides immediate alerts for important updates, including change in rules or access policies for database-stored files and folders. You can do this while configuring the alert criteria (see Figure 2) as per your needs. Alert criteria can also be created based on custom thresholds and user actions.
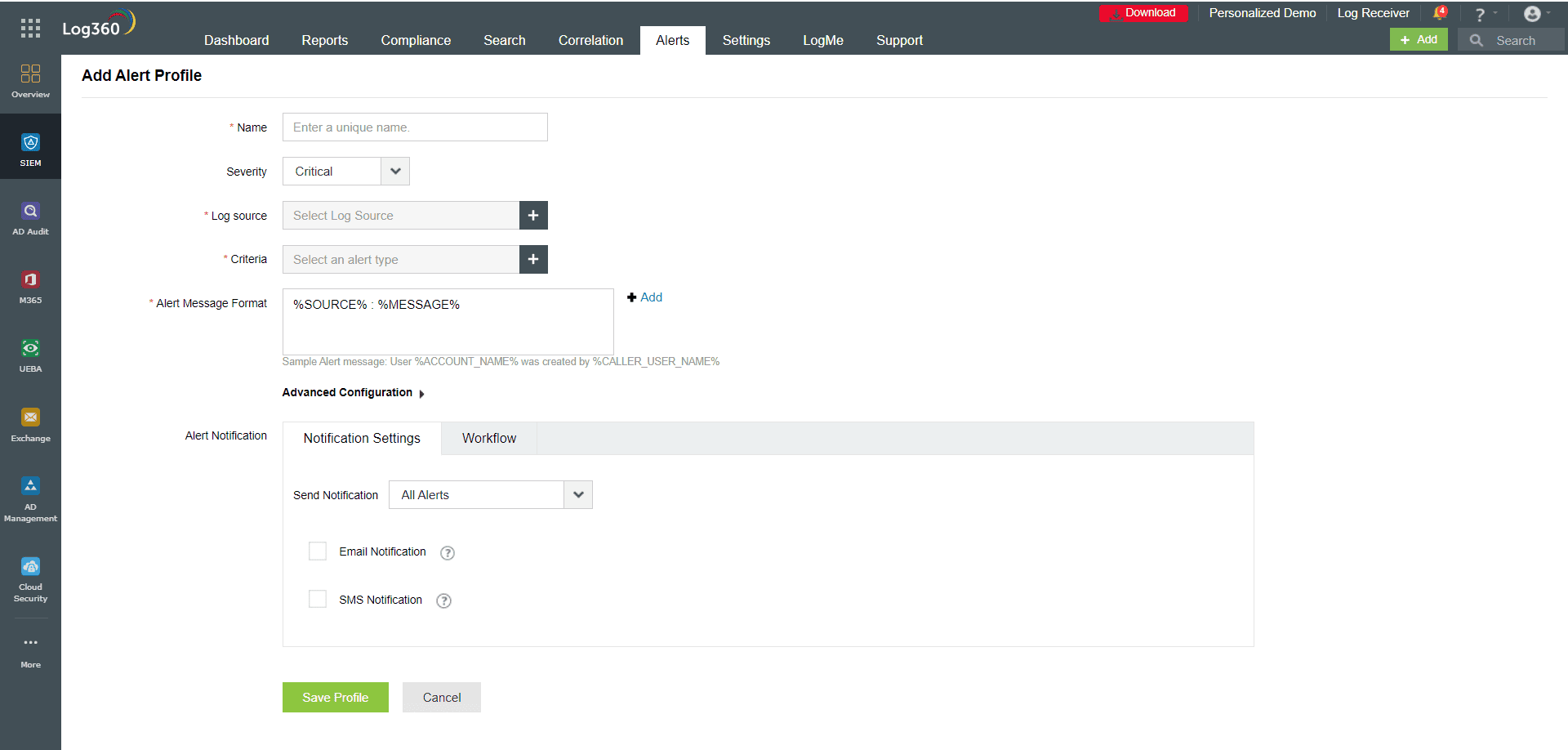
Figure 2: Creating alert profiles
3. Continuous monitoring: Following the setting up of appropriate policies and an alert criteria, the FIM module starts continuously monitoring the files and folders. Unauthorized additions, deletions, and modifications to files and directories are all tracked and continuously saved. This makes it easier to identify any unusual activity and prevents insiders from trying to transfer or exfiltrate sensitive data. The FIM system then notifies the security team in real-time if an insider tries to access or alter sensitive data without proper authorization .
ManageEngine Log360's dashboard provides in-depth graphical representation of all the activities performed on the files and folders. These are represented as separate sections as shown below (refer to figure 3). It will provide all of the details of when, where, and what changes occurred.
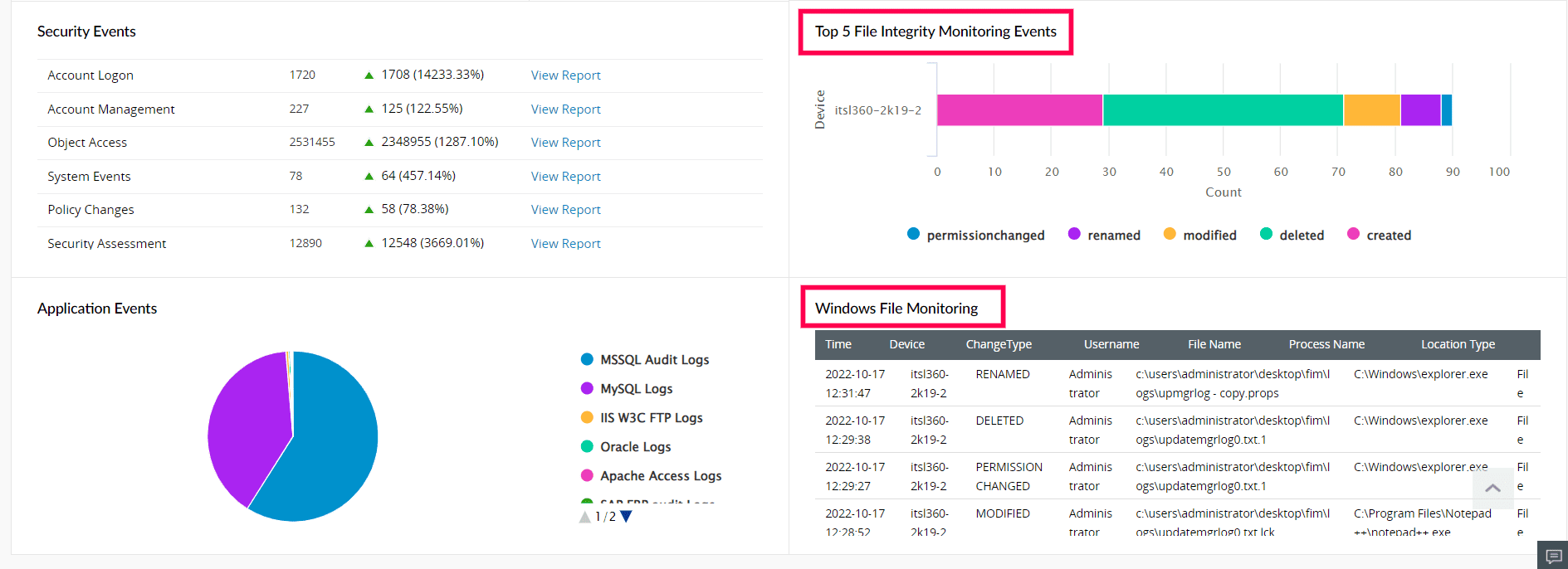
Figure 3: Changes made to the files represented in the dashboard
Also, by keeping an eye on file integrity and user behavior, organizations can reduce the chance of security incidents and data breaches. This allows for more effective detection, investigation, and response to insider threats. By monitoring how users interact with critical files and folders, FIM can spot anomalous activity and possible insider threats. This includes unauthorized access attempts, unusual file modifications, and suspicious file activity patterns.
ManageEngine Log360 generates thorough reports with accurate integrity information (file creation, deletion, modification, permission changes, operation changes) in multiple formats, including CSV and PDF. You can automatically receive the reports at regular intervals with the help of flexible report scheduling (refer to figure 4).
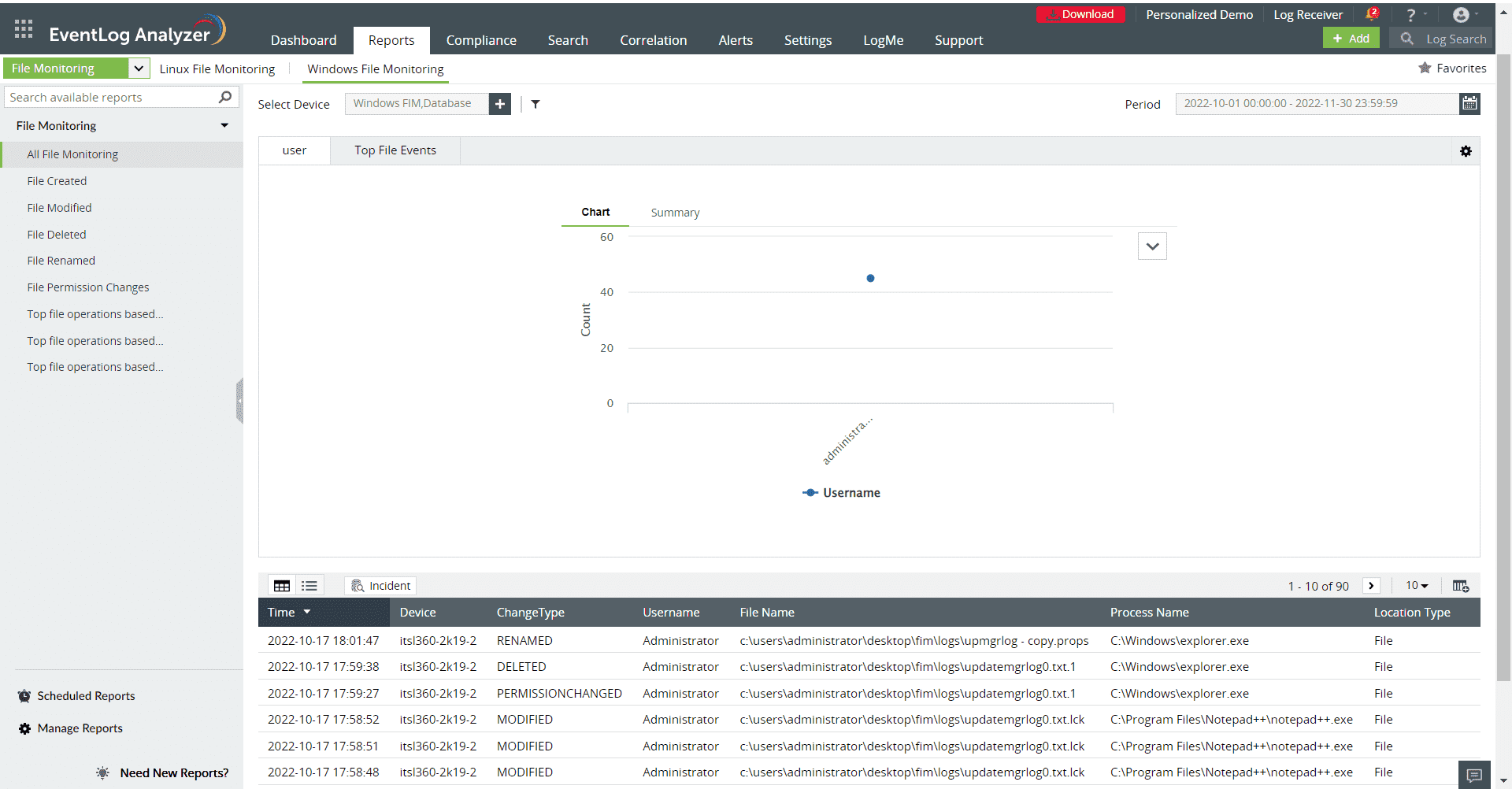
Figure 4: File integrity monitoring report
4. Generate reports: The FIM solution maintains detailed audit logs along with historical information on file modifications and access events. This makes it possible for security analysts to carry out forensic investigation and ascertain the source and extent of occurrences involving insider threats, hence enabling incident response and appropriate disciplinary measures. All of the actions performed (creation, deletion, access, modification, or renaming) are represented to the users in the form of reports for identifying the threats effectively.
A deeper understanding of the incident can be obtained by correlating the events occurring within your network, which may have been overlooked while examining the situation at the individual level. This can be viewed in the correlation reports of Log360. The correlation reports have real-time answers to the what, when, where, and how of all modifications. A thorough audit record of every modification made to files and folders is available (refer to figure 5).
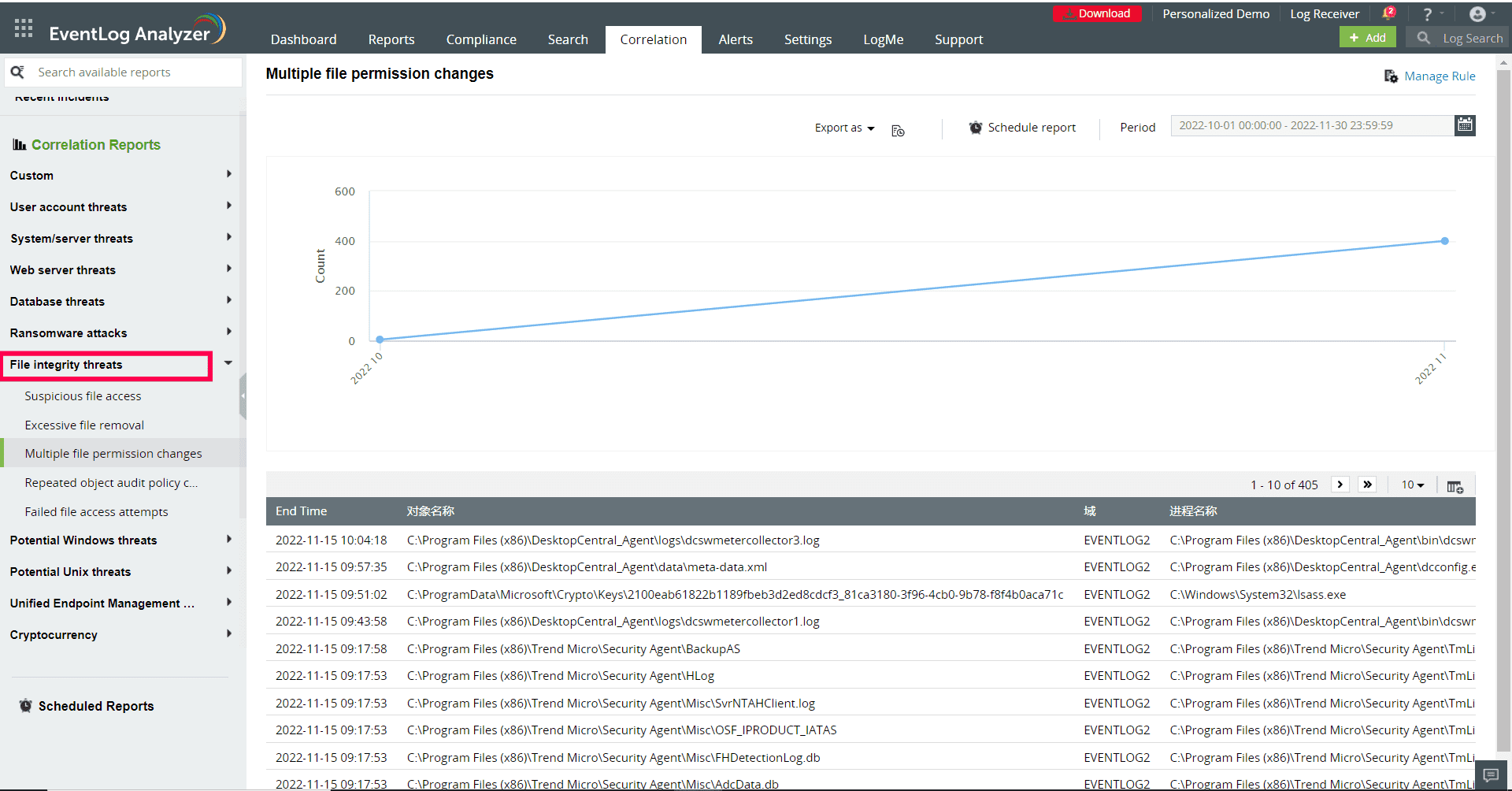
Figure 5: Correlation report of file integrity threats
Also, to provide proof of compliance with regulations like PCI DSS and HIPAA, FIM compliance reports can be generated in order to compile every relevant information for auditing purposes. ManageEngine Log360 enables organizations to fulfill the requirements of essential regulatory mandates like PCI DSS, SOX, HIPAA, and FISMA(refer to figure 6).
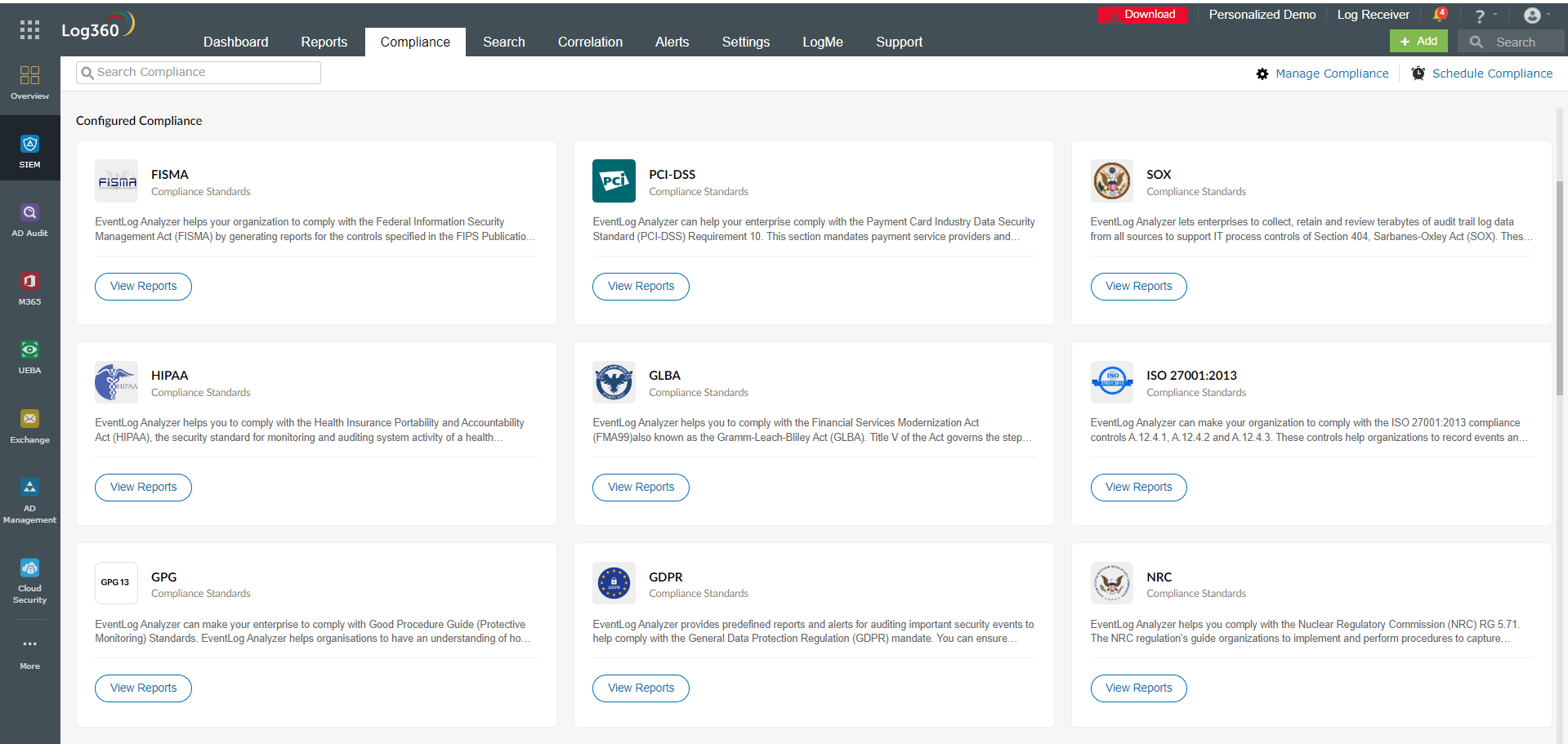
Figure 6: Compliance report in ManageEngine Log360
5. Mitigate insider threat automatically with incident management: An incident response plan will help to quickly identify the scope and impact of a security incident and take appropriate actions. As soon as we become aware of an attack within an organization, we must move quickly to counter it. This will ensure that the organization won't experience the similar threat in the future. Upon identifying the vulnerability and the specific threat's cause, create an incident workflow. In order to make sure that unwanted modifications are tracked down and stopped, it can also be helpful to set up alerts with a predefined threshold based on the vulnerability discovered.
An integrated ticketing module, part of Log360's end-to-end incident management system, assists in allocating tickets to security administrators, monitoring their progress, and ensuring accountability throughout the incident resolution process (refer to figure 7). It also includes an automatic remediation framework that can associate workflows with alert profiles. These workflows get executed automatically when a correlation alert is triggered to remediate the incident.
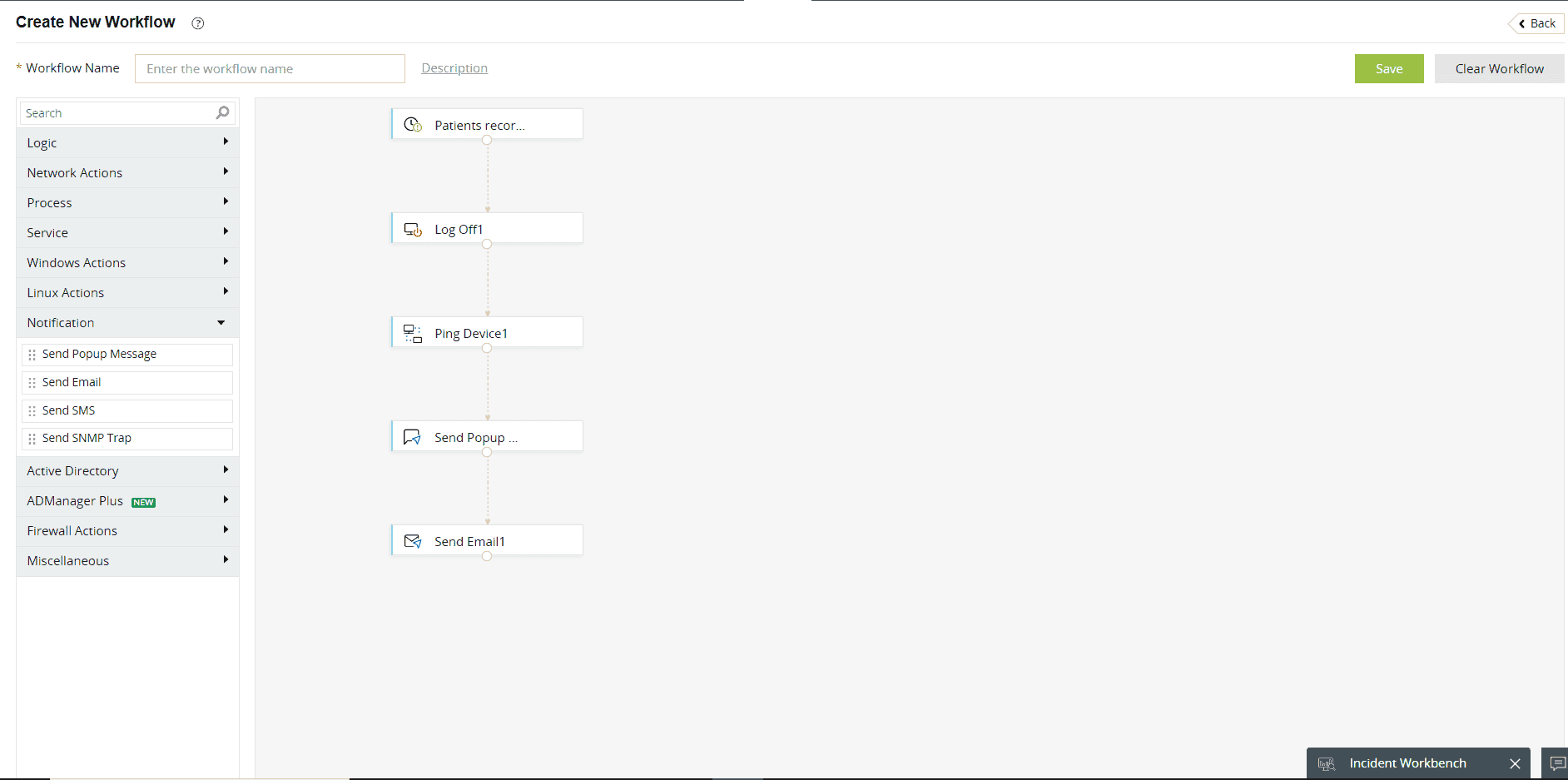
Figure 7: Incident management system of ManageEngine Log360
Figure 8 illustrates the numerous ways in which FIM assists organizations in defending against insider threats.
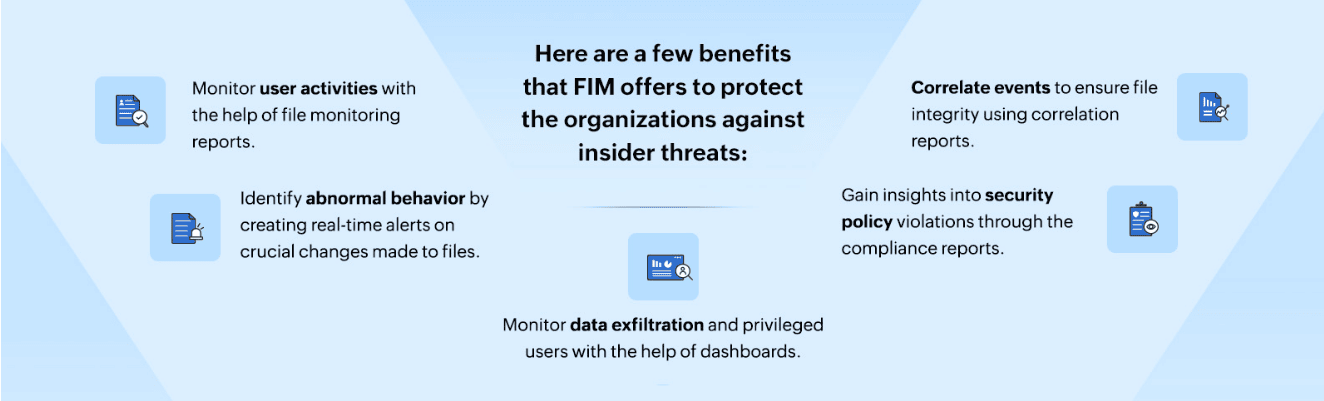
Figure 8: Implementing FIM to prevent insider threat
Organizations seeking to minimize insider threats and safeguard sensitive data and systems from illegal access, modification, and exfiltration should consider using FIM. Organizations can lessen the likelihood of insider threat by proactively monitoring file integrity and user actions. This allows for more effective detection, investigation, and response to insider threats.
Ready for the next step?
Are you looking for ways in which you can protect your organization's sensitive information from being misused? Sign up for a personalized demo of ManageEngine Log360, a comprehensive SIEM solution that can help you detect, prioritize, investigate, and respond to security threats.



