In today's complex and continuously evolving threat environment, it is imperative for organizations to conduct a digital forensic investigation to find out the root cause of security incidents. A root cause analysis armors security teams with the who, when, where, and how of breaches.
Log forensics is a technique that security teams can use to drill down deep into security breaches.
Log forensics allows organizations to:
However, security teams often feel overwhelmed when performing log forensics. This is because of the massive amount of log data collected across the network from various sources like network devices, databases, workstations, Active Directory, file servers, firewalls, and third-party applications.
The key to making it easier is for teams to identify and filter the logs as per their requirements and then gradually drill down further to arrive at the root cause of a problem.
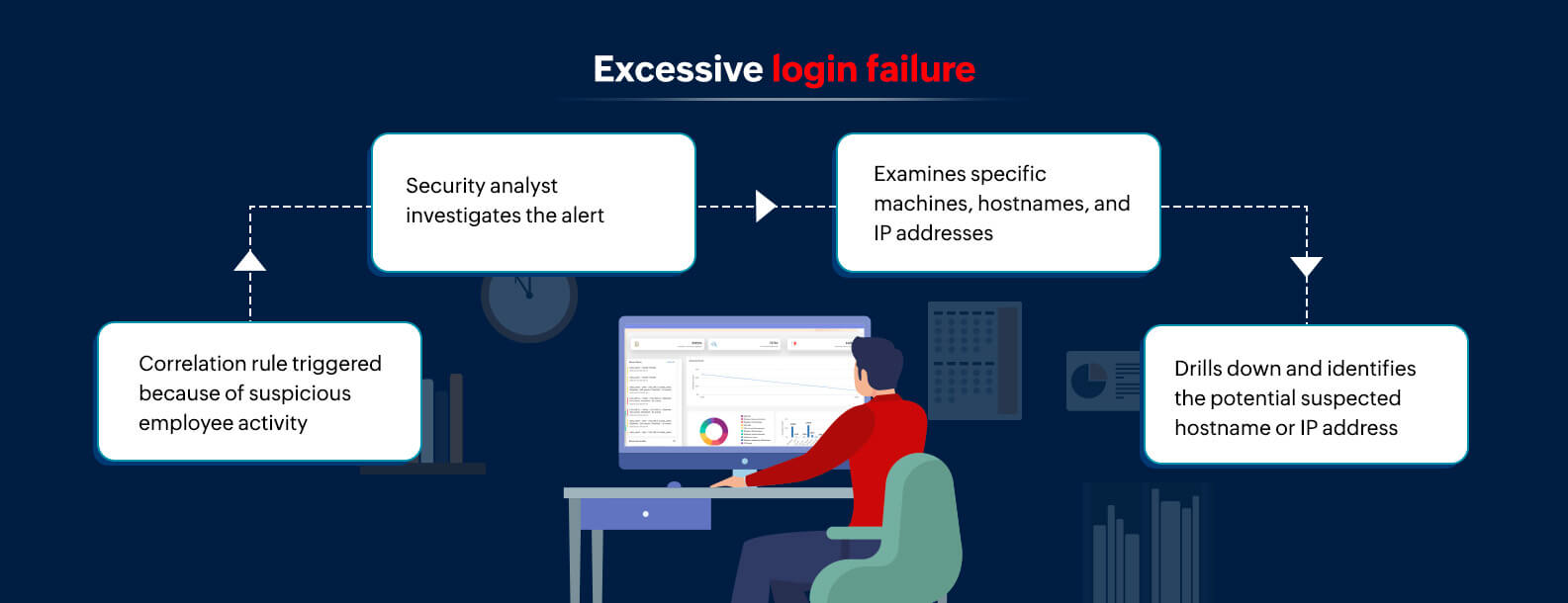
Let's consider the following example to understand how a SIEM solution can play an important role in conducting log forensics.
If an employee has multiple unsuccessful login attempts within an hour, a correlation rule in the SIEM solution gets triggered, resulting in a real-time alert.
On receiving the alert, the security analyst can drill down to investigate all the events that are related to excessive login failures within a particular time period for that user account.
The security analyst can further examine the specific machines, IP addresses, and domains where this user account was active. They can also view all the user accounts that are associated with the suspected IP addresses or hostnames.
They can identify the hostnames or IP addresses with a high number of suspected malicious login failures.
A SIEM solution like Log360 empowers security teams to efficiently search through the enormous amount of log data collected across the network from various sources. It aggregates logs, performs log normalization, and analyzes logs while generating neat and insightful reports and graphs.
Log360's log forensics engine is powered by Elasticsearch, which helps in the fast and efficient retrieval of log results from across network devices to simplify the forensic investigation process for security teams.
Try a free, 30-day trial of Log360 today to test the solution's log forensic capabilities for yourself!
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.