Every firm has to deal with the exhausting process of detecting, managing, and resolving security incidents. Failing to have an incident response plan can have a devastating impact on any organization, both in terms of financial losses and reputational damage. This blog explores the importance of incident response, the key elements of detecting and managing incidents, and the best practices to help organizations handle security incidents.
Here are some intriguing numbers from Ponemon Institute and IBM's Cost of a Data Breach Report 2021 that prove the significance of incident response management:
The security incident management life cycle is an ongoing process that requires constant monitoring and review to ensure that an organization is prepared to detect, respond to, and resolve security incidents in a timely, effective manner. It begins with preparation (having an incident response team and the right tools) and includes detection, analysis, response, containment, and post-incident recovery. Figure 1 depicts the incident management life cycle.
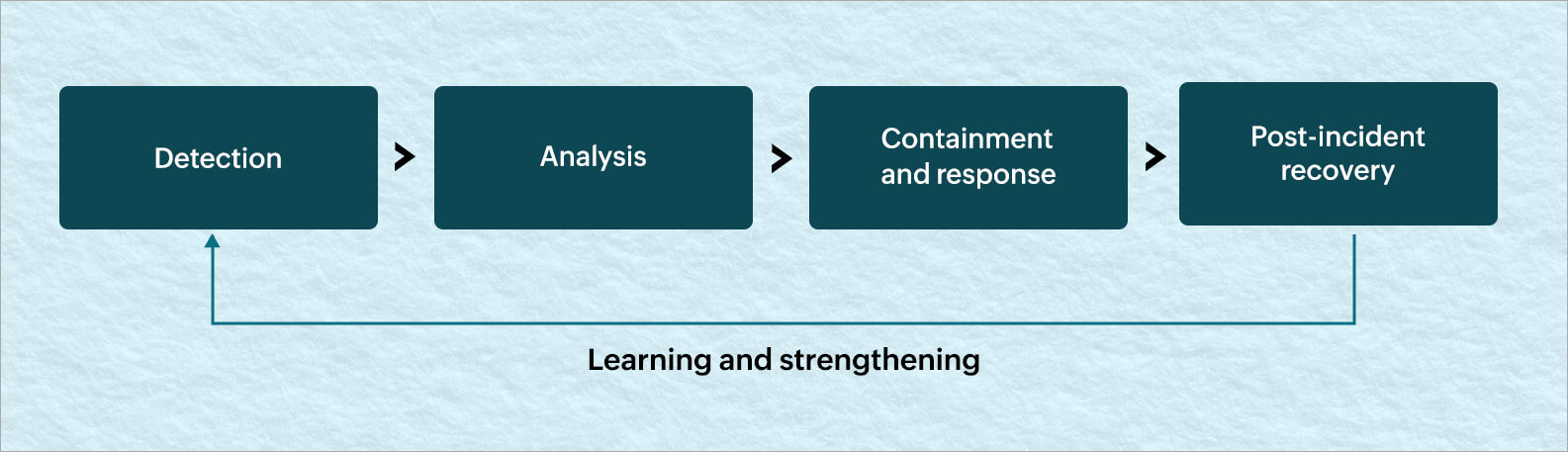 Figure 1. The security incident management life cycle.
Figure 1. The security incident management life cycle.
A SIEM tool with incident response capabilities can support you throughout your incident response process by correlating threats across sources, automating response actions and incident creation, performing log forensics, and managing incidents centrally. Here are a few best practices to follow to make incident response management easier:
Correlation rules can pick up on suspicious sequences of events and generate alerts in real time. Configure alerts to notify admins and execute a response workflow immediately.
You can use incident rules to create incidents in the SIEM tool automatically and assign them to specific technicians. The details and status of an incident can be managed centrally via the SIEM tool's console. If required, forward alerts to a third-party ticketing tool that your organization is more proficient at using.
Response workflows can be used to disable a user, block a USB, turn off a device, set firewall rules, and validate an IP using threat intelligence sources. An effective SIEM tool should offer numerous predefined workflows out of the box as well as let users create custom workflows.
Forensic analysis involves delving deeper into the attack for thorough assessment and eradication. The search function of your SIEM tool can be used to sift through the raw logs and discover an attack's origin as well as other pertinent pieces of evidence to add to the incident report.
Analysts should be able to collaborate on an incident by adding insights and notes from their findings to the SIEM tool. Collaboration helps analysts from different tiers add their comments to the incident report so they are not required to start from scratch when investigating and reviewing the incident's status. Additionally, analysts should be able to manually add relevant alerts, event logs, and events from device reports to an existing incident report.
Make sure to include all the critical facts, such as the incident timeline, users, devices, and all the associated alerts and event logs, in your incident report. This will be of great help during security auditing. You should be able to generate a report on the incident from your SIEM tool's incident management console.
The incident response process in ManageEngine Log360, a comprehensive SIEM solution, is comprised of four major stages:
A sequence of network events triggers a correlation alert through predefined or custom rules.
Log360 then:
The analysts can investigate further, adding relevant events and alerts from various sources as well as comments to enrich the incident report.
Analysts can execute a workflow manually, track the resolution status, and close the incident.
Figure 2 explains the incident response process in Log360.
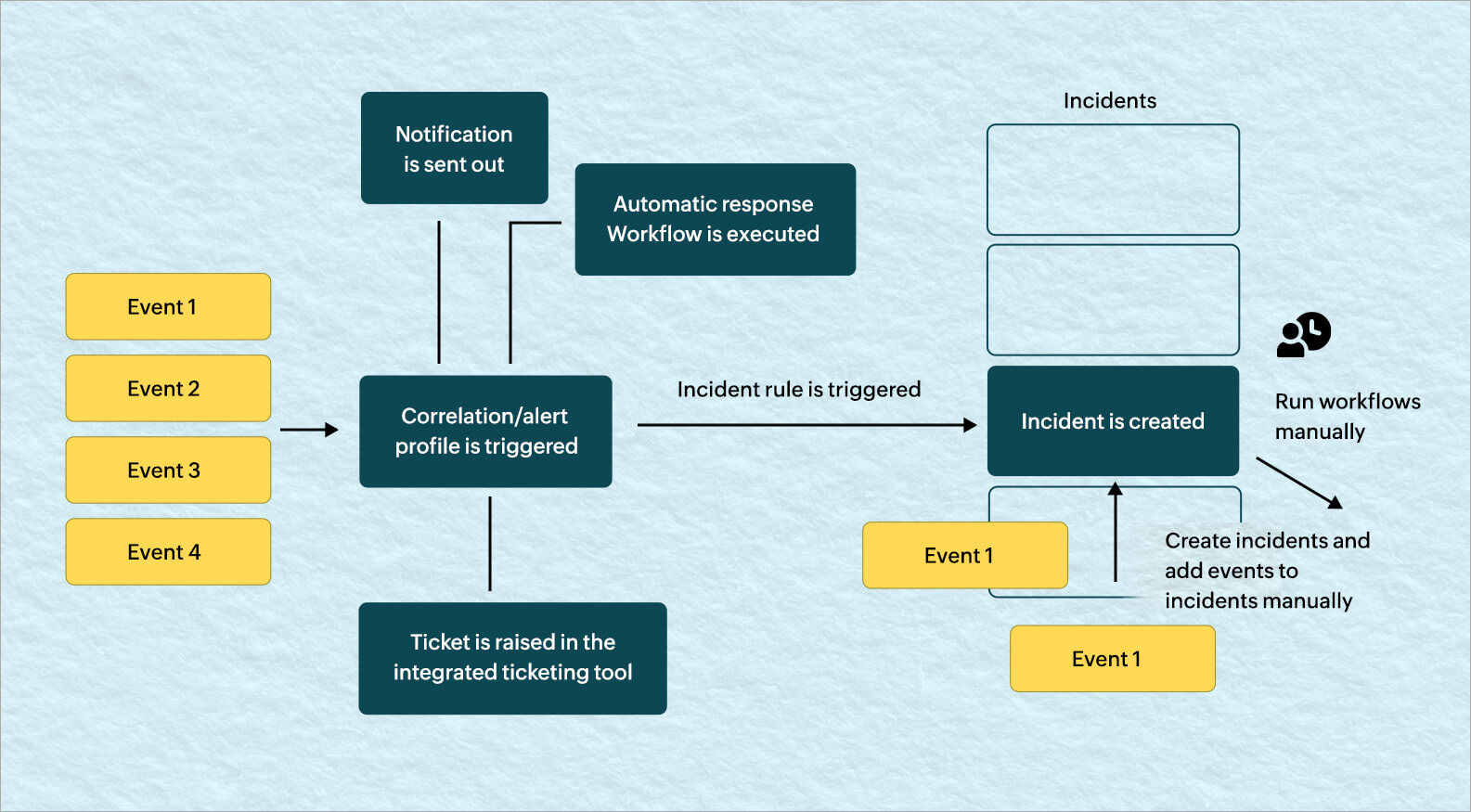 Figure 2. The incident response management process in Log360.
Figure 2. The incident response management process in Log360.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.