Local privileged account group modification refers to any alteration made to the membership of groups possessing elevated system privileges on a local machine. These "privileged" groups—such as administrators or power users—grant members significant control, including installing software, modifying system settings, accessing sensitive data, and managing system resources.
Here are some damaging events that can occur when there are unauthorized changes to privileged groups.
1. Adding or removing users: Attackers might add their own accounts or other compromised accounts to high-privilege groups like "Administrators" or "Domain Admins." This grants them elevated permissions and access to sensitive system resources.
2. Altering group policies: Modifying group policies can change the permissions and access controls for users and groups, potentially allowing attackers to bypass security measures and gain unauthorized access.
3. Privilege escalation: By adding themselves to privileged groups, attackers can escalate their privileges, giving them the ability to execute commands and perform actions that would normally require higher-level permissions.
Detection of account group modification
Detection of local privileged account group modifications involves using monitoring tools and security solutions to track changes made to privileged groups. These tools analyze event logs generated by the system to identify any unauthorized or suspicious modifications.
Key event IDs
- Event ID 4732: This event ID is generated when a member is added to a security-enabled local group. Monitoring for this event can help detect unauthorized additions to privileged groups.
- Event ID 4733: This event ID is generated when a member is removed from a security-enabled local group. Monitoring for this event can help detect unauthorized removals from privileged groups.
How Log360 detects these modifications
Log360 correlation rules are designed to detect and analyze security threats by correlating various events happening across your network. These rules help identify patterns and relationships between seemingly unrelated events, providing a clearer picture of potential security incidents.
In a Windows environment, system accounts typically end with "$" and are used for services and other system-related functions. The criterion "USERNAME notendswith $" ensures that the accounts being checked are regular user accounts, not system accounts.
Triggering the rule
This rule is activated when a non-privileged user account is added to a privileged group, such as the "Administrators" group within the "Builtin" container. By monitoring for these specific conditions, Log360 can detect unauthorized additions of user accounts to privileged groups, allowing for prompt investigation and response to potential security threats.
By implementing this security information and event management (SIEM) correlation rule, Log360 enhances an organization's ability to maintain a secure environment by identifying unauthorized changes to privileged account groups, thus mitigating risks associated with privilege escalation and persistent threats.
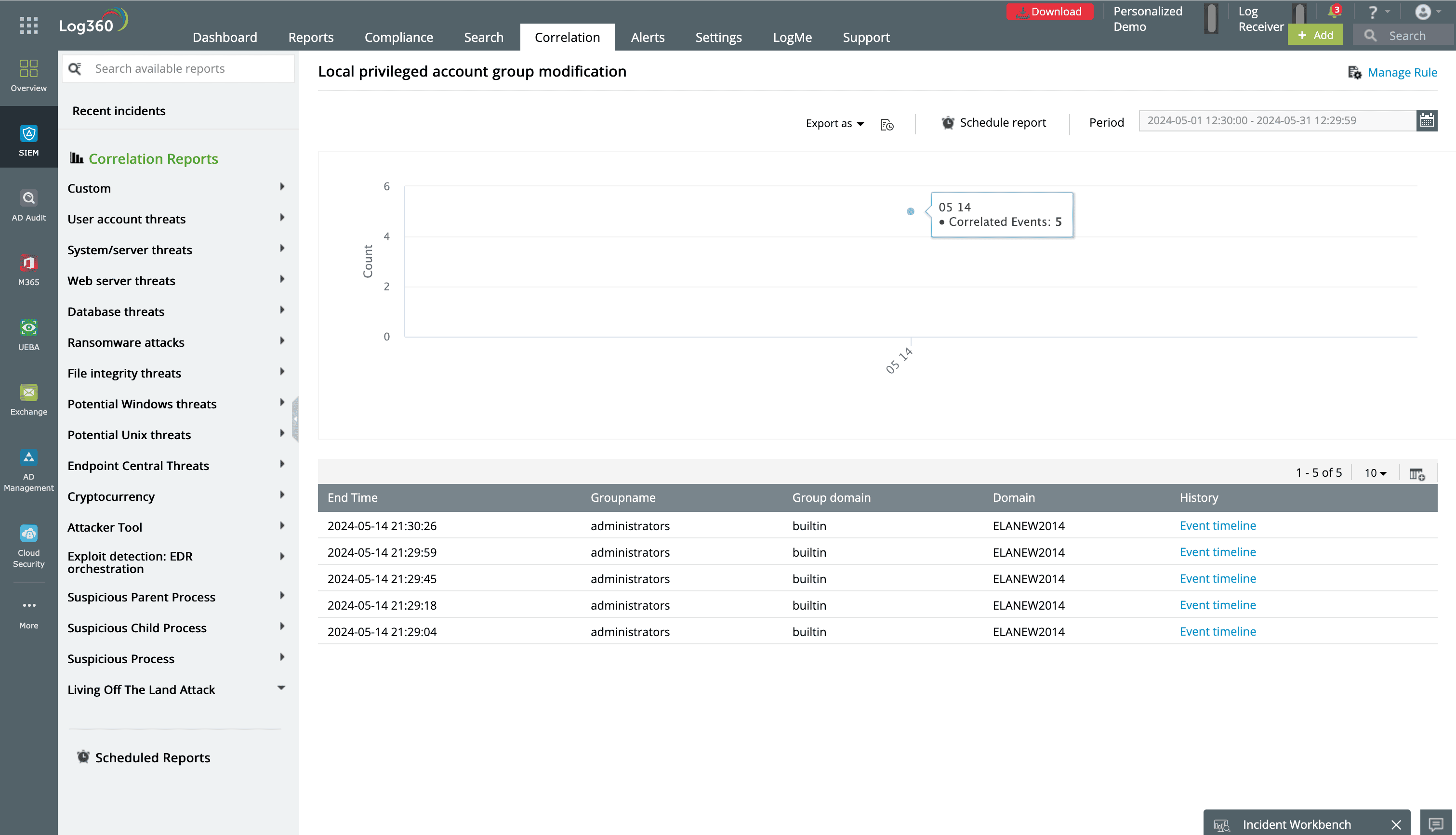
Figure 1: Predefined report in Log360 showing modifications that took place in local privileged account groups.
How to prevent attackers from modifying privileged groups
Least privilege policies: Implementing the principle of least privilege (PoLP) ensures that users and processes have the minimum level of access necessary to perform their tasks. By restricting permissions beyond this minimum access, the risk of unauthorized modifications to privileged groups is reduced.
Regular audits: Conducting regular audits of group memberships and permissions helps identify any unauthorized changes. Audits involve reviewing the current state of group memberships and comparing it to historical data to detect discrepancies. These audits can be automated or performed manually and should be conducted periodically.
Multi-factor authentication (MFA): Requiring MFA for accessing and modifying privileged accounts adds an extra layer of security. Even if an attacker gains access to a user’s credentials, they would still need the additional authentication factor (e.g., a security token or mobile app approval) to make any changes. This significantly reduces the risk of unauthorized access and modifications.
Access control mechanisms: Implementing robust access control mechanisms ensures that only authorized users can modify privileged groups. This includes setting up role-based access control (RBAC) and enforcing strict policies around who can add or remove members from privileged groups.
Audit policies and logging: Enabling detailed audit policies and logging for privileged account activities ensures that all changes are recorded and can be reviewed if suspicious activity is detected. This includes tracking who made the changes, when they were made, and what modifications were performed.



