The volume of cyberattacks and ransom demands on the healthcare industry is increasing at a very fast rate. According to a 2022 study by the Ponemon Institute, 43% of healthcare organizations in the US experienced a ransomware attack and 76% of those experienced an average of three or more. Such attacks have an adverse effect on patient care, including loss of life.
The same study reported that the primary target for cyberattackers are Internet of Things (IoT) and Internet of Medical Things (IoMT) or medical Internet of Things. IoMT devices were the root cause for 21% of all ransomware attacks. Here are some of the other findings of the study:
- Fifty-six% of organizations experienced at least one cyberattack in the last two years that involved an IoT or IoMT device, and 24% reported adverse impacts resulting in increased mortality rates.
- Sixty-five% of the respondents suffered an average of five or more data breaches (since 2020) with IoT and IoMT devices being involved 88% of the time.
- While 71% of respondents rated the risk posed by IoMT devices as high or very high, only 21% of respondents reported having proactive security measures in place.
With patient care so deeply dependent on connected devices, it's clear that securing them should be the top priority for IT security professionals working in healthcare organizations. But to do that, they should first know the various categories of IoT devices in healthcare.
What are the different categories of healthcare IoT devices?
The IoT devices in a healthcare organization can be segregated into the following four categories:
-
IoT: This includes any device or asset that's connected to a network and is not recognized as a traditional IT device.
-
IoMT: This indicates IoT devices that possess medical functionality.
-
OT: Operational technology (OT) constitutes any software, hardware, or communication systems that enable the proper functioning of large-scale industrial equipment and assets.
-
Connected devices: Any simple device that's remotely connected and controlled.
The following table provides examples of the above-discussed category of devices.
| Healthcare device category |
Examples |
| Internet of Things |
IP security cameras, smart locks, VoIP phones, and gateways |
| Internet of Medical Things |
MRI machines, IV pumps, glucometers, ultrasound machines, patient monitors, medicine dispensers, PACS servers, radiography systems, DICOM workstations, and heart monitors |
| Operational technology |
Elevators, electrical grids, and HVAC systems |
| Connected devices |
Coffee machines, light switches, and printers |
Table 1: Example of different healthcare IoT devices
The top-10 bedside devices that pose the greatest security risks are:
-
Infusion pumps
-
VoIP devices
-
Ultrasound machines
-
Patient monitors
-
Medicine dispensers
-
Gateways
-
IP security cameras
-
PACS servers
-
Computerized radiography systems
-
DICOM workstations
According to another Ponemon report, infusion pumps, aka IV pumps, account for 38% of a hospital's IoT devices. The same report also suggests that 73% of IV pumps have vulnerabilities that attackers can exploit to compromise patient safety and data confidentiality. Moreover, VoIP devices that enable communication between doctors and lab technicians and access points that restrict access to rooms present additional security risks. These, if unaddressed, could be hacked or disabled by attackers during a ransomware attack, having a catastrophic impact on patient outcomes.
How does ransomware affect healthcare organizations?
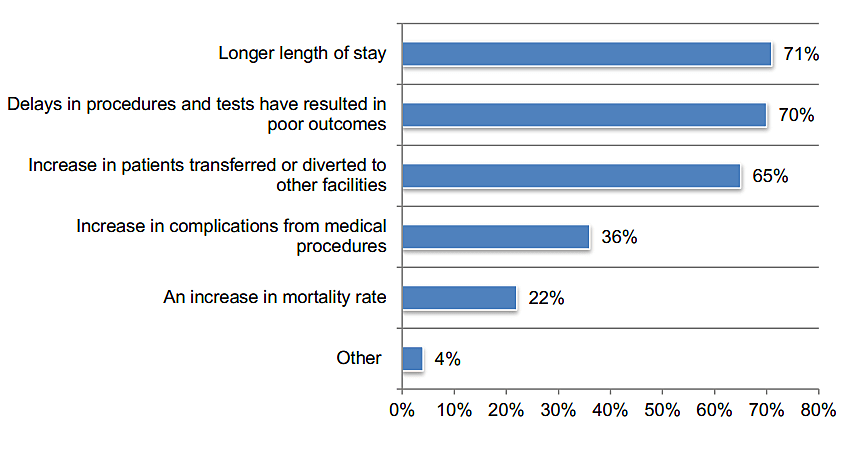
As evidenced above, cyberattacks almost always involve IoT and IoMT devices. Cyberattacks, especially ones as sinister as ransomware, have devastating consequences in the healthcare industry. According to yet another Ponemon report from 2021, ransomware impacts healthcare organizations in the following ways:
- Longer stays at the hospital for patients
- Poor patient outcomes caused by delays in tests and procedures
- Increase in patient transfers
- Increase in medical complications
- Increase in mortality rate
 Source: Ponemon
Source: Ponemon
Clearly, IoT medical devices pose a great risk to the security and privacy of patients and patient data. But why do they pose such a risk? What are the challenges that analysts face that make securing IoT devices for healthcare so hard?
Why is it so hard to secure healthcare IoT devices?
The complexity of securing devices in healthcare can be attributed to the following reasons:
- Unpatched IoT devices: IoT healthcare devices are often built with functionality in mind, not security. Healthcare personnel are not trained in device security and wouldn't know if the IoT device needs to be patched. Moreover, with IoT devices being expensive, employees might not make any updates or changes in fear of causing adverse impacts on the device or patient care.
- Expanding volume of connected devices: With IoT, IoMT, OT, and connected devices coexisting, the attack surface expands phenomenally. Securing these becomes hard for any security team.
- Dealing with multiple vendors: Tracking devices, categorizing them, and managing their vulnerabilities is hard because healthcare organizations tend to use multiple vendors, each with their own operating system.
- The added complexity of portable devices: It's easy to lose track of an asset when it's being moved between rooms. For example, the movement of IV pumps and ultrasound machines makes gaining full visibility a challenge.
- The conundrum of frequent device use and downtime: Healthcare IoT devices are used frequently. This means that they aren't afforded a lot of downtime to give security teams time to analyze them and apply the required patches.
- The drawback of durability: IoMT devices are also designed to be longstanding. Their durability can be a drawback because even after the vendor has stopped manufacturing or updating patches to these devices, hospitals might still be using these legacy technologies, leaving them open for attackers to exploit.
- Software incompatibility impacts security: IoMT devices don't usually accommodate external software, so updating patches or securing them through traditional endpoint agents presents quite a challenge.
- Lack of context: Security solutions don't automatically understand the context or behavior of medical IoT devices.
- Unpredictability of device scanning: How a medical device responds to the protocols of the vulnerability scanner depends on how the vendor designed its operating system. There's a chance that the device might crash due to an unexpected communication.
- Lack of ownership: Security researchers are suggesting that the lack of clear ownership and accountability affects the security of healthcare IoT devices.
- Lack of network segmentation: Lastly, but most importantly, a lack of proper network segmentation makes it hard to secure the various IoT devices in a healthcare organization.
How to secure IoT healthcare devices
While it's the vendor's responsibility to design the medical IoT devices using DevSecOps, maintaining the security of the device once it's deployed falls onto that organization's security teams. The following measures can help IT security professionals working in healthcare organizations secure IoT devices.
- Perform complete asset inventory to identify all managed and unmanaged devices.
- Ensure that the devices are properly authenticated and are communicating only via ports and protocols that have been deemed acceptable by the organization.
- Establish network access control, and restrict unauthorized accesses and privileges to the devices and network. Implement the principles of least privilege to prevent cyberattacks.
- Segment networks based on users, devices, and criticality of resources. Networks can be segmented based on patients, doctors, guests, admin staff, or hospital technicians.
- Deploy a SIEM solution that provides real-time security monitoring, advanced threat intelligence, user and entity behavior analytics, and automated incident response capabilities.
- Configure the SIEM solution to discover devices automatically and understand context, so it can alert you if the connection to a device goes down or if it stops sending logs suddenly. The machine learning algorithms in a SIEM solution can, with time, learn the expected behavior of devices. But to get started, they need at least two weeks of historical data.
- Apply patches across devices as soon as they've been released by the IoT device vendors. To prevent attacks before the availability of a permanent solution, consider implementing a virtual patch. Virtual patches add an additional layer of security by analyzing and intercepting the traffic from bad actors before the request reaches the application or the attacker exploits the vulnerability.
- Adopt a Zero Trust policy and implement it in a phased manner to protect against various cyberattacks.
While it's good to learn about proactive measures, security teams should also have a plan in place to deal with an attack if it were to happen. To understand the intricacies of healthcare-related ransomware attacks, the different stages of infection, and the steps to detect and combat it, download this free e-book. Alternatively, you can schedule a call with our product experts and have an in-depth conversation with them. Thanks for reading, folks!
 Source: Ponemon
Source: Ponemon