A security operations center (SOC) analyst is critical to an organization's cybersecurity function, serving as the first line of defense against cyberthreats. Their responsibilities include monitoring networks, detecting potential security problems, and responding to attacks in real time. SOC analysts are critical to protecting sensitive data and ensuring business continuity. As cyberattacks become more frequent and sophisticated, the demand for SOC analysts has increased. The job market for SOC analysts is thriving, with businesses across industries investing extensively in cybersecurity personnel to reduce risks. This expanding need makes it one of today's fastest-growing and most important cybersecurity occupations. So, on this page, we will discuss the various roles SOC analysts play, their responsibilities, and the skills required of SOC analysts.
What are the day-to-day duties of a SOC analyst?
SOCs are classified into three tiers (Tier 1, Tier 2, and Tier 3) of analysts, and there is a variety of other positions, such as SOC managers and SOC engineers, based on their level of experience, expertise, and work difficulty. The steps required for professional advancement in the SOC analyst sector are explained in the infographic below.
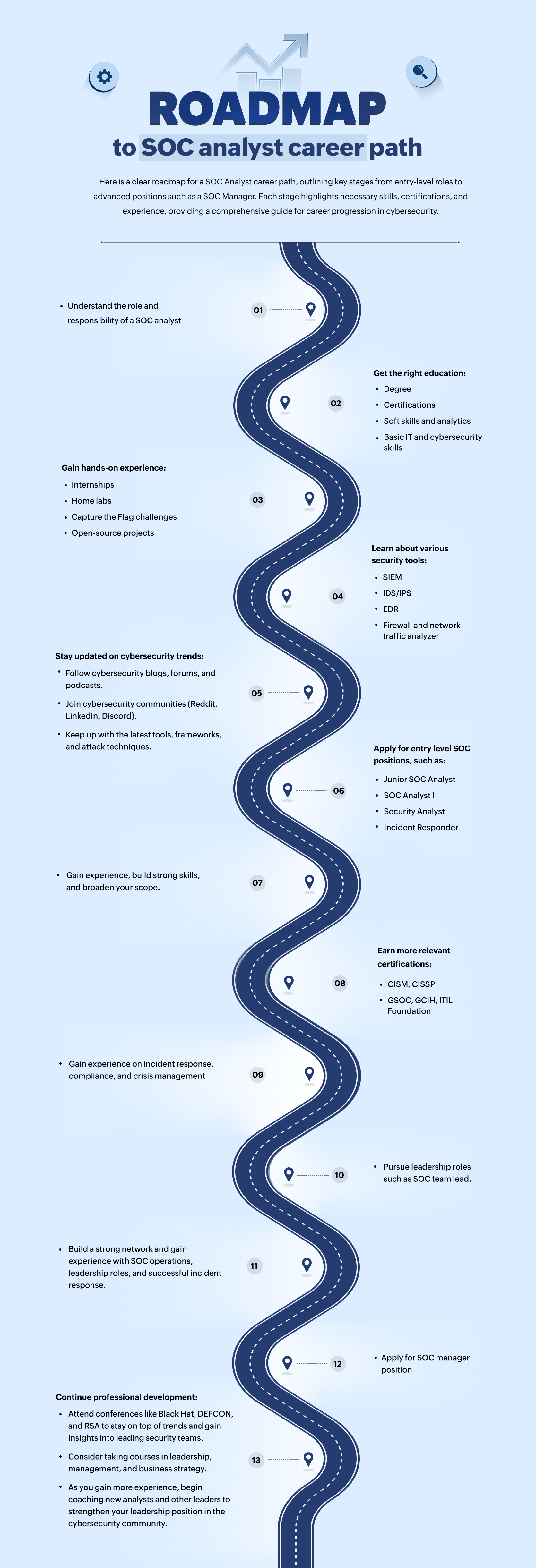
Figure 1: Roadmap to a SOC analyst career path

To learn more in depth about the technical skills, soft skills, qualifications, and certifications that are required to become a SOC analyst , refer to this page.
Different SOC analyst roles and their key responsibilities
Tier 1 SOC analyst: Junior analyst
They focus on monitoring, triaging, initial investigation, and escalation. Their responsibilities include:
- Monitoring logs gathered from firewalls, servers, endpoints, and other security devices by utilizing the security dashboards and alerts produced by security solutions, like a SIEM tool.
- Reviewing alerts to identify potential security incidents and then prioritizing them based on severity.
- Investigating the generated alerts to check if they are true incidents or false positives.
- Analyzing log data to identify indicators of compromise.
- Carrying out incident response, where low-risk incidents are first brought under control by isolating endpoints or disabling user accounts.
- Escalating incidents to higher tiers if more detailed investigation is required.
- Documenting all alerts, action taken, and findings in incident management systems and handing them over for smooth communication with the next shift.
- Helping end users or IT teams by responding to routine inquiries about security and reporting unusual activity.
Skills required to become a junior analyst:
- Ability to monitor security alerts and events using SIEM tools
- Knowledge of common attack types (phishing, malware, etc.)
- Ability to assess and prioritize security issues for escalation
- Experience using ticketing systems to log incidents
- Can report security events in a clear and simple manner
Tier 2 SOC analyst: Intermediate analyst
They handle more complex investigations, advanced response actions, and threat hunting. Their responsibilities include:
- Conducting proactive threat hunting using tools like EDR to discover hidden threats based on patterns and indicators from recent incidents or threat intelligence.
- Verifying and validating severity by carrying out detailed analysis of alerts and incidents that are escalated by Tier 1.
- Investigating complicated events, such as malware infections or lateral movement, and closely examining potential threats.
- Responding to incidents that require more advanced action, such as root cause identification and containment.
- Performing system isolation, patching, or eradication steps when necessary by coordinating with IT teams.
- Modifying SIEM rules and correlation rules and enhancing detection capabilities by collaborating with Tier 1 analysts to reduce false positives.
- Ensuring that logs are correctly ingested and that alerts are being generated by regularly performing health checks on security tools.
- Preparing detailed incident reports for management and compliance purposes.
- Communicating with other teams, such as network or system administrators, to address issues discovered during investigations.
Skills required to become an intermediate analyst:
- In-depth investigation into security events and data breaches
- Understands threat actors' tactics, techniques, and procedures (TTPs)
- Can collect and analyze digital evidence from systems and networks
- Ability to prevent, mitigate, and recover from security incidents
- Proficiency with scripting languages (Python, PowerShell) for automating tasks
Tier 3 SOC analyst: Senior analyst
They focus on taking lead on incident handling, forensics, architecture improvements, and mentorship. Their responsibilities include:
- Utilizing specific tools to perform forensic analysis and look into different types of attacks, like APTs, to determine the extent of data breaches or compromises.
- Overseeing major incident response activities and coordinating across teams to ensure effective remediation.
- Providing recommendations for security architecture and helping to create more effective detection and response mechanisms.
- Reviewing and analyzing threat intelligence to understand emerging threats and TTPs.
- Guiding and mentoring Tier 1 and Tier 2 analysts, helping them improve their technical skills and knowledge.
- Organizing training sessions and providing knowledge about incident handling and threat detection best practices.
- Performing post-incident analysis, identifying weaknesses and recommending changes to security policies and procedures.
- Working closely with red teams to evaluate and test the performance of the security measures in place.
Skills required to become a senior analyst:
- Actively seeks out advanced threats through proactive monitoring
- Expertise in reverse-engineering malware and understanding its behavior
- Can conduct red team exercises and simulate real-world cyberattacks
- Mastery in network forensics and incident response at the enterprise level
- Can advise on security policies and improving SOC methodologies
SOC team lead or manager
They supervise the SOC's activities and ensure effective incident response. Their responsibilities include:
- Mentoring and leading SOC analysts to ensure effective performance and continuous skill development.
- Leading the response to security incidents, including coordinating investigation, containment, recovery, and documentation.
- Ensuring the effective usage of security tools to monitor networks and systems for real-time detection of threats.
- Creating, updating, and enforcing incident response practices to ensure that the team adheres to standardized best practices.
- Serving as the primary point of contact for the SOC and other internal teams to facilitate clear communication during security issues.
- Organizing regular training sessions and simulations to increase the team's understanding of evolving threats and tools.
- Tracking and reporting key performance metrics to provide insights into SOC performance, threat trends, and response times to stakeholders.
Skills required to become a SOC team lead or manager:
- Leadership to guide the SOC team, establish objectives, and monitor performance
- Can create and update a roadmap for SOC development and improvement
- Understands organizational risks and can focus the SOC's efforts accordingly
- Communicates effectively with leaders, external partners, and regulators
- Can ensure SOC operations adhere to industry standards and regulations (e.g., GDPR, PCI DSS)
Here are some other advanced roles and specialization related to the SOC analyst sector:
Threat hunter
- Proactively searches for hidden threats and anomalies within an organization's network that could allow automated security systems to bypass.
- Detects complex attacks by analyzing SOC notifications and investigating any suspicious activity on a deeper level.
- Increases the effectiveness of incident response and fine-tunes detection tools by identifying patterns and vulnerabilities.
Incident responder
- Leads efforts to control an event and remove any harmful actors or data from the system.
- Analyzes incidents after they have been resolved to identify vulnerabilities and offer future prevention measures.
- Works with law enforcement to conduct legal investigations and prosecutions in the event of serious breaches.
SOC engineer
- Manages the installation, implementation, and maintenance of SOC tools, including SIEM solutions and IDSs or IPSs.
- Develops scripts and integrations to automate repetitive activities and improve SOC efficiency.
- Provides technical support and troubleshooting for the SOC team.
- Keeps SOC systems up to date and secure against vulnerabilities.
Threat intelligence engineer
- Monitors numerous external sources, such as the dark web and threat intelligence feeds, to discover emerging threats relevant to the organization.
- Shares their knowledge and insights with SOC analysts and incident responders to help improve the organization's security.
Digital forensic analyst
- Investigates compromised systems to determine how breaches occurred.
- Gathers digital evidence in a way that ensures its integrity for legal purposes.
- Analyzes system and network logs after an incident to identify attack pathways and vulnerabilities.
Empower your SOC analysts
Our cutting-edge security technology can help your SOC team reach its full potential! Are you ready to improve your threat detection and response capabilities? Sign up for a personalized demo of ManageEngine Log360, a comprehensive SIEM solution that can help you detect, prioritize, investigate, and respond to security threats.



