User and entity behavior analytics (UEBA), the anomaly detection engine of SIEM solutions, employs machine learning (ML) algorithms to establish a baseline of normal behavior for every user and entity. To establish this baseline, it uses models such as robust principal component analysis and Markov chains.
UEBA checks every current action the user or entity makes against their baseline and determines whether it is an anomaly. Anomalies can be of three types: time anomalies, count anomalies, or pattern anomalies. A UEBA-powered SIEM solution can also assign a suitable risk score to users and entities based on the extent of deviation from the baseline.
While choosing a SIEM solution for your organization, you must consider the effectiveness of its anomaly detection or UEBA capabilities. To do this, you need to evaluate the SIEM solution across the three fundamental pillars of UEBA as defined by Gartner®.
What are the three pillars of UEBA?
User and entity behavior analytics encompasses three fundamental pillars: use cases, data sources, and analytics.
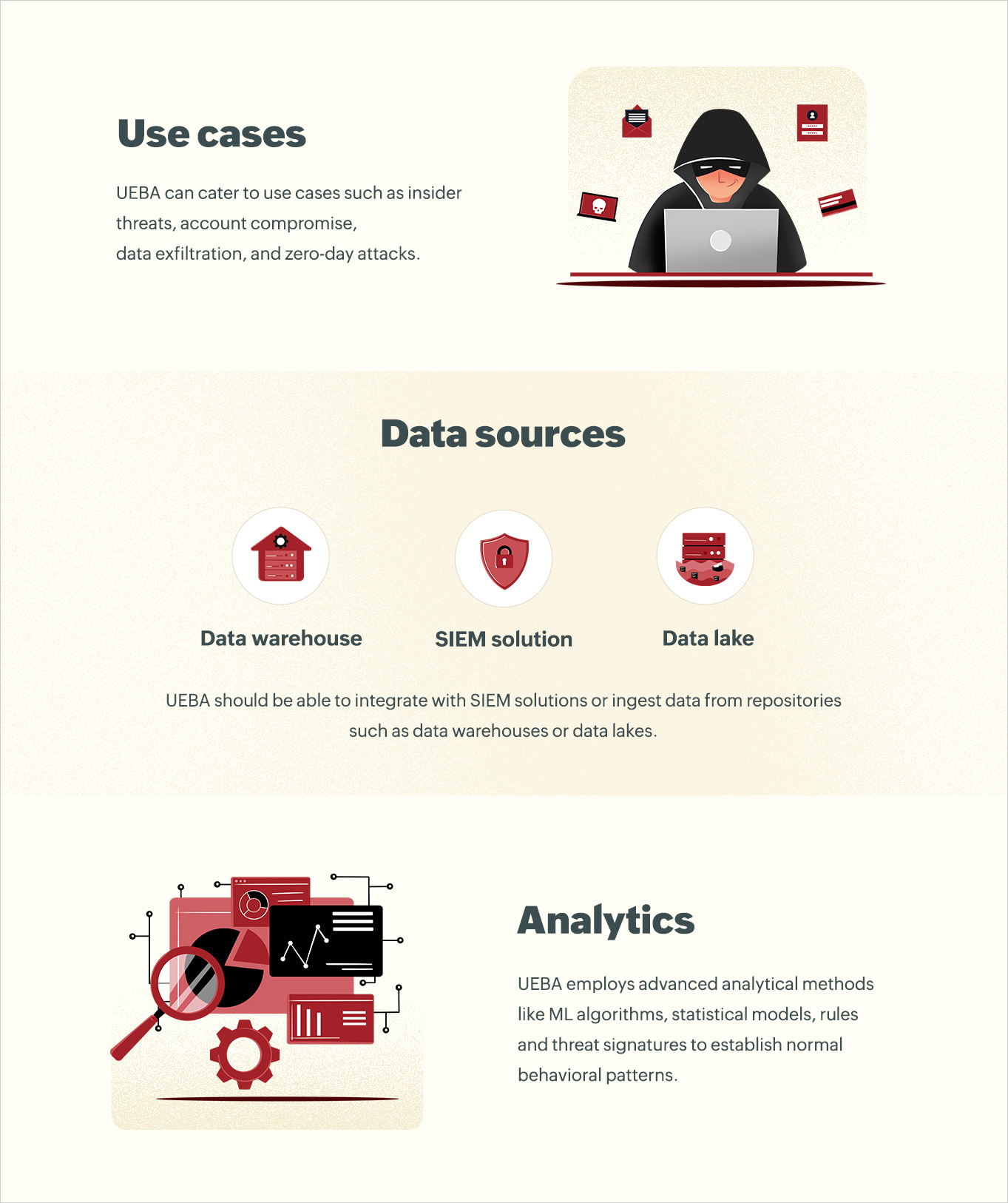
Figure 1: The three pillars of UEBA
Use cases: UEBA scrutinizes deviations from typical user and entity behavior to detect potential security threats. UEBA solutions should be versatile and capable of catering to a variety of scenarios, including insider threats, account compromise, data exfiltration, and zero-day attacks, as shown in Figure 1.
Data sources: UEBA should proficiently gather data from various sources, like event logs, network traffic, and endpoint devices. Integration with SIEM solutions or data ingestion from repositories such as data warehouses (or data lakes) is crucial and doesn't require the deployment of additional agents in IT environments.
Analytics: UEBA leverages sophisticated analytical methods, like ML algorithms, statistical models, rules, and threat signatures, to establish normal behavioral patterns. It then conducts contextual analysis within the user roles, permissions, and typical activities to accurately differentiate between normal and suspicious behavior.
Pillars and components of UEBA and ManageEngine Log360
ManageEngine's unified SIEM solution, Log360, has incorporated the three pillars of UEBA.
Use cases: Log360 caters to use cases such as insider threats, compromised accounts, data exfiltration, and logon anomalies, and also gives you the option to customize risk scores and enable contextual risk scoring, as shown in Figure 2.
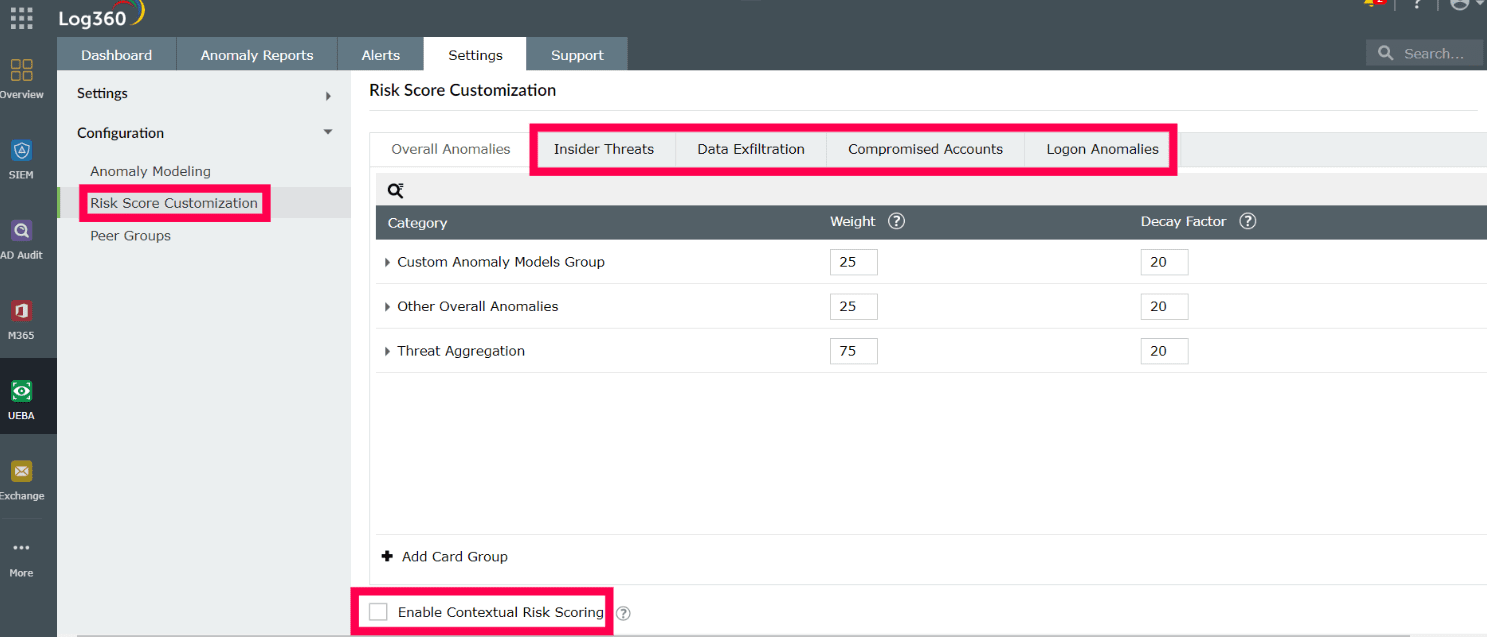
Figure 2: UEBA use cases catered to by Log360
Data sources: Being a SIEM solution, Log360 ingests data from various sources, such as network firewall logs, IDS and IPS logs, web proxy logs, server logs, Windows and Linux logs, endpoint security logs, database logs, and applications logs, thereby conforming to the second pillar of UEBA. Log360 also allows you to add devices and import logs for analysis, as shown in Figure 3.
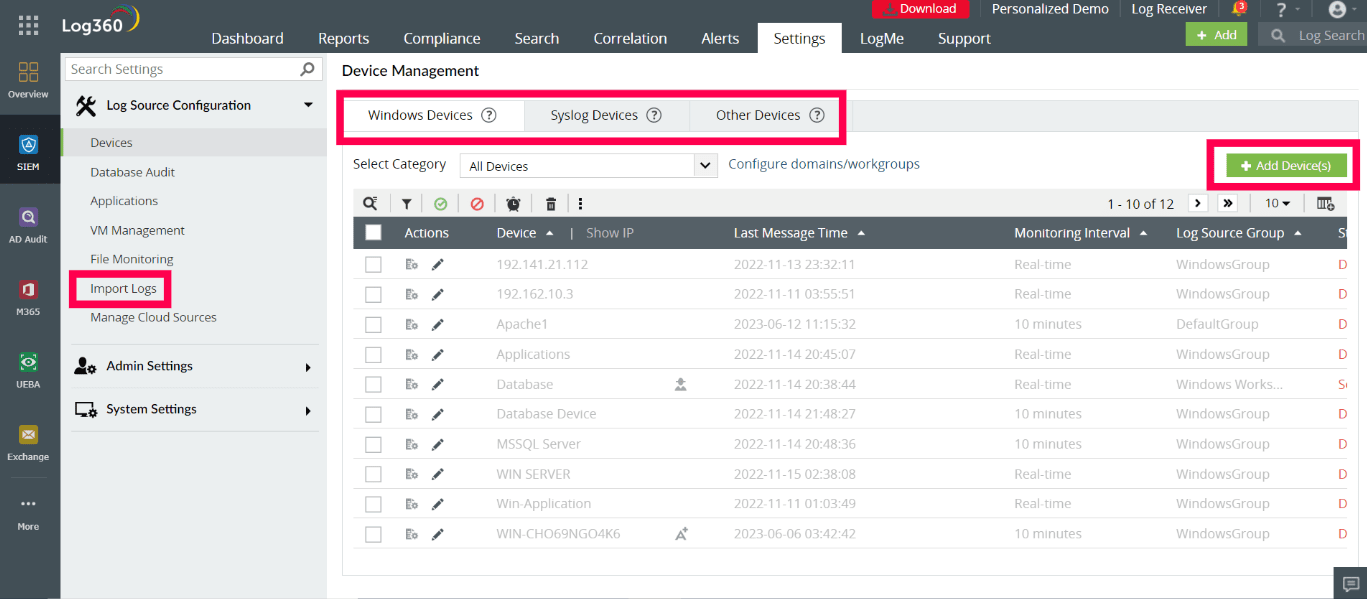
Figure 3 Data sources ingested by Log360
Analytics: In accordance to the third pillar of UEBA, Log360 employs ML algorithms and statistical models to differentiate between normal and anomalous behavior, and for arriving at a risk score, as shown in Figure 4. It also leverages techniques such as peer grouping, seasonality, and user identity mapping to improve risk scoring accuracy.
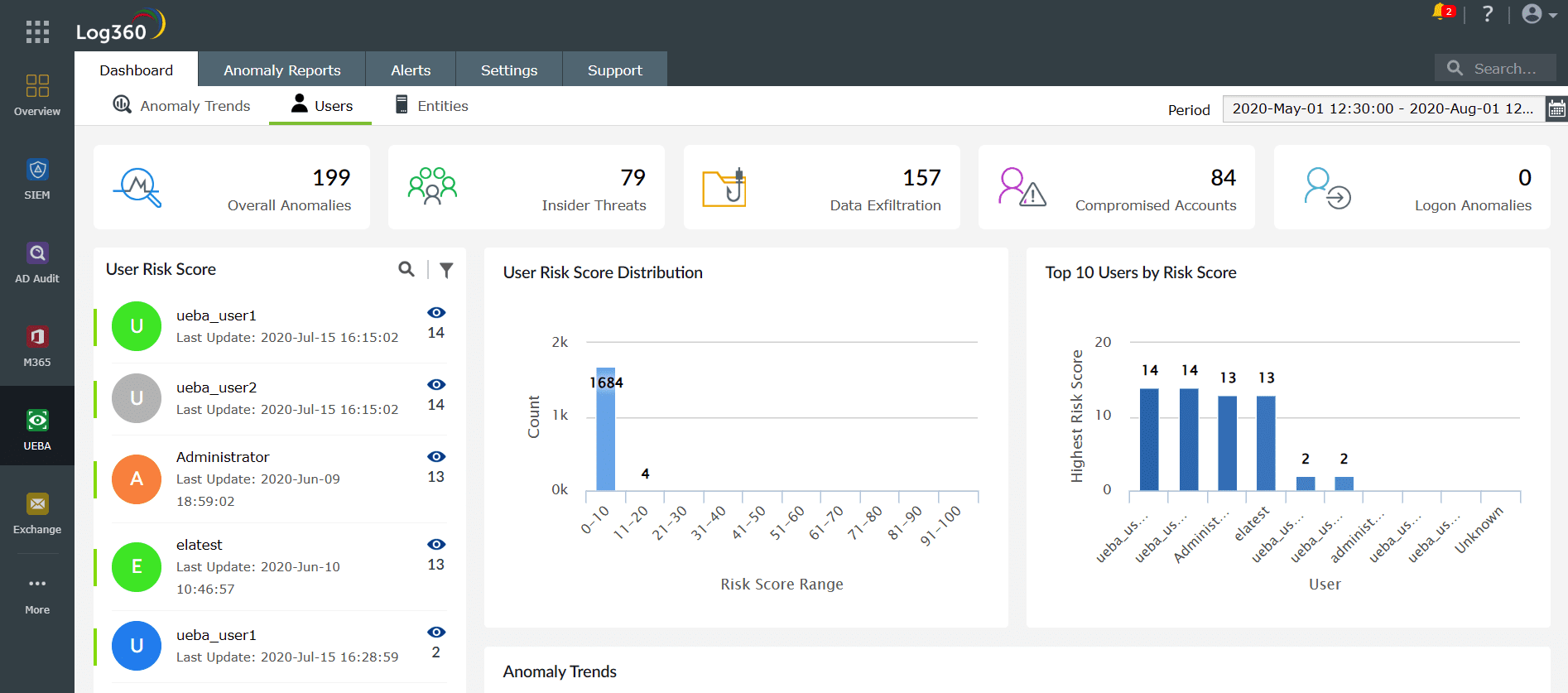
Figure 4: Log360 dashboard showing user risk score distribution and top 10 users by risk score
In addition to the pillars defined by Gartner, there's one more component you should factor in while choosing a SIEM solution with UEBA capabilities: data presentation.
Data presentation
- The presentation of data in a UEBA solution should be designed in a way that facilitates easy interpretation and informed decision-making for security analysts and stakeholders.
- Visualizations, charts, graphs, and reports should be utilized to highlight behavior patterns, anomalies, and risk scores derived from data analysis, enabling effective response to potential security threats.
Log360 presents the analyzed data in the form of easily interpretable graphs and reports, as shown in Figures 5 and 6.
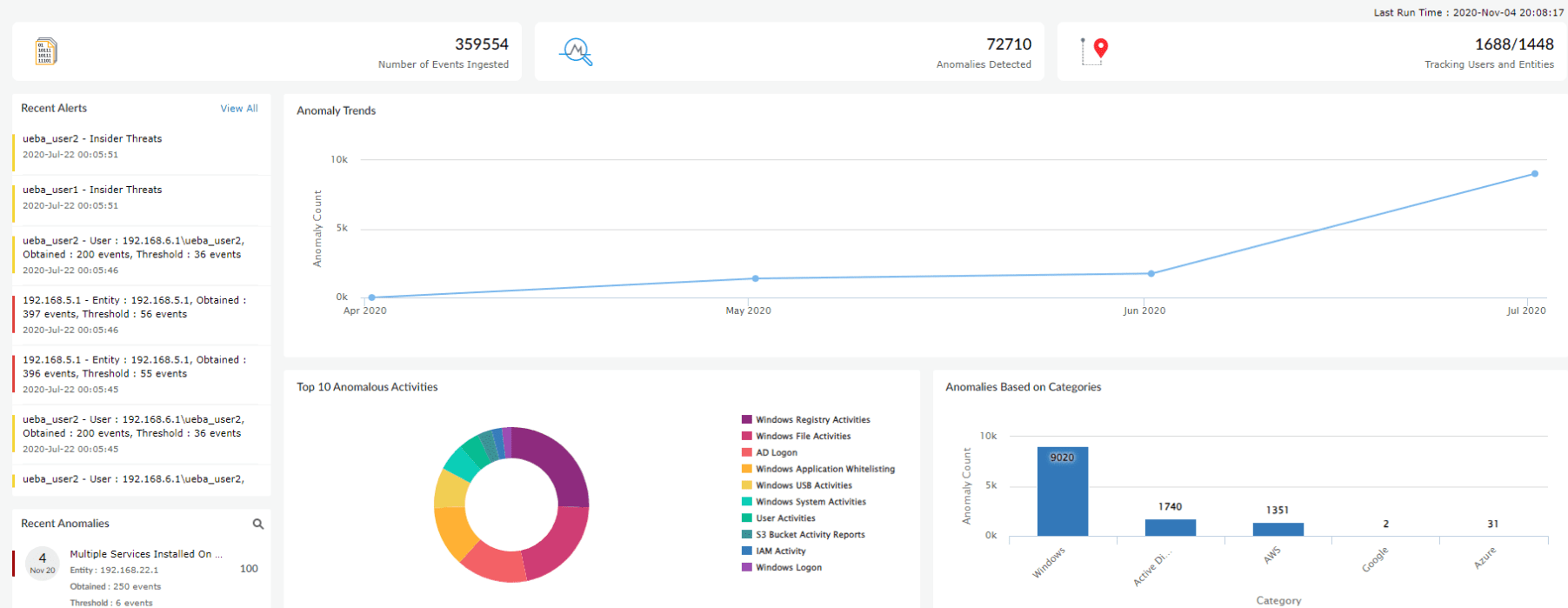
Figure 5: Log360 dashboard showing anomaly trends and top 10 anomalous activities
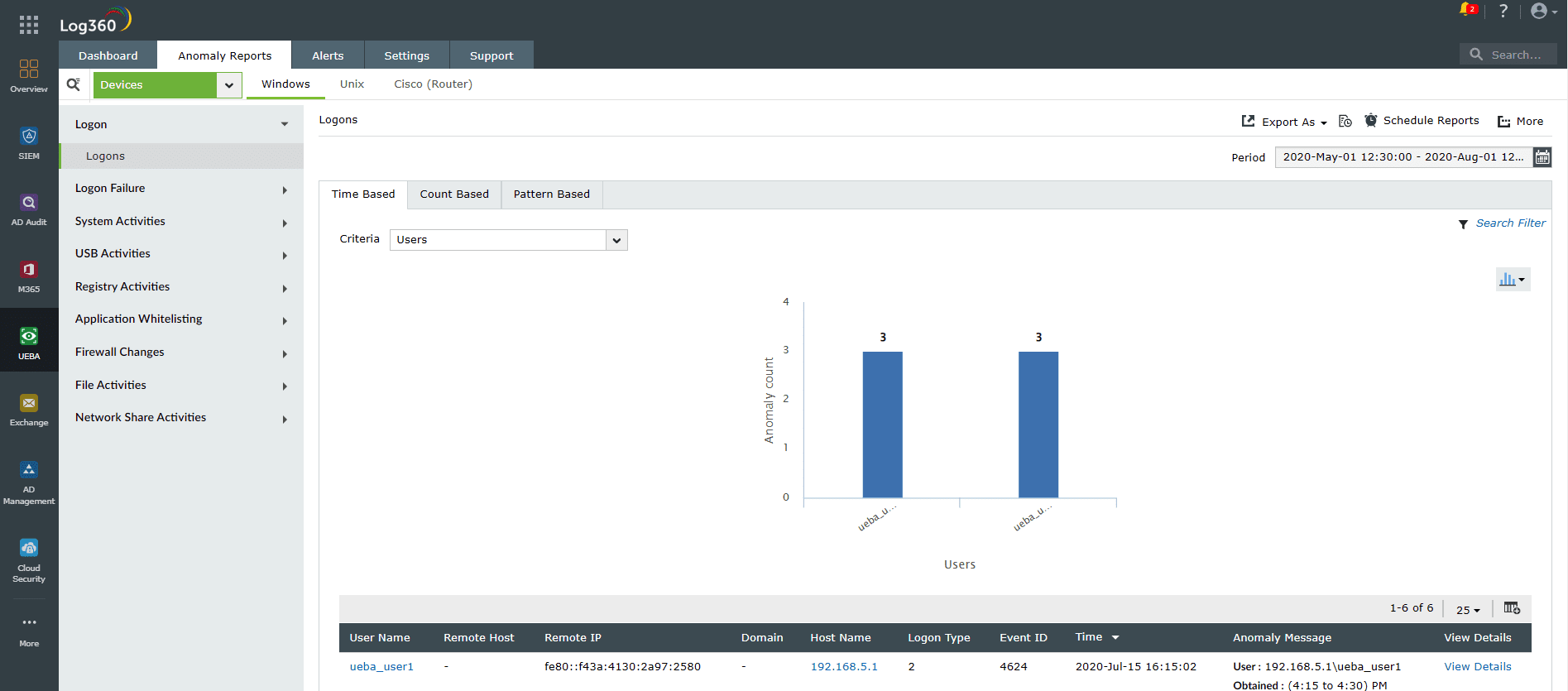
Figure 6: Anomaly reports in Log360
Why should a SOC manager know about the pillars and components of UEBA?
You should know about UEBA's pillars and components because it will give you an edge over your peers when it comes to choosing the right UEBA-powered SIEM solution for your SOC. This knowledge will confer the following advantages:
- Finding the right fit for your organization: Understanding the pillars and components of UEBA allows SOC managers to comprehend and evaluate a UEBA solution's potential in enhancing the efficiency of their security operations, and in fulfilling their organization's needs and security use cases.
- Effective implementation: Knowledge of UEBA pillars enables SOC managers to implement the technology more effectively within their organization's security infrastructure, ensuring optimal utilization of resources.
- Better threat detection and incident response: Forewarned is forearmed. By leveraging the analytics component of a UEBA solution, your team can proactively hunt for threats. Armed with this knowledge, they can also develop more targeted incident response strategies, enabling quicker remediation of security incidents.
Simply put, by understanding the pillars and components of UEBA, SOC managers can streamline their security operations, optimize resource allocation, and improve overall operational efficiency within the SOC.
About ManageEngine Log360
ManageEngine Log360 is a unified SIEM solution with integrated UEBA, SOAR, DLP, and CASB capabilities. Log360 has been recognized in Gartner's Magic Quadrant™ for SIEM six consecutive times, and it has won gold in the 2022 Cybersecurity Excellence Awards for these categories: SIEM, UEBA, hybrid cloud security, and SOAR.
Log360 provides:
- ML-based user and entity behavior analytics
- An integrated risk management system
- Identity-based threat detection
- Real-time security monitoring
- Automated incident response
Having these functionalities in your SOC will help your team prioritize and respond to threats quickly and efficiently. To learn more about how Log360 can protect your organization from various cyberattacks, including insider threats, sign up for a personalized demo.



