The menace of ransomware has been significantly rising over the past decade, both in terms of quantity and complexity. Cybercriminals and malware authors are increasingly innovative with their malware codes, customizing them to create maximum damage. Ransomware is known to encrypt files on a victim’s computer and demand a ransom in return for the decryption key. As if that isn’t scary enough, certain ransomware have the additional capability to not just encrypt, but also infect files, turning them into polymorphic file infectors. VirLocker is one such ransomware, and its effects can be disastrous.
The VirLocker ransomware strain, also known as VirLock or VirRansom, first appeared in 2014. By 2016 it became prominent, as security researchers found that variants of this strain were capable of spreading through cloud storage and collaboration apps. VirLocker is believed to be the world’s first self-replicating polymorphic ransomware. Most ransomware either lock screens or encrypt files. Some take a hybrid approach and do both. VirLocker goes one step further, and not only locks screens and encrypts files, but also infects them and turns each of these encrypted files into a polymorphic file infector. An infected VirLocker file contains embedded clean code sandwiched between the polymorphic code and malware code.
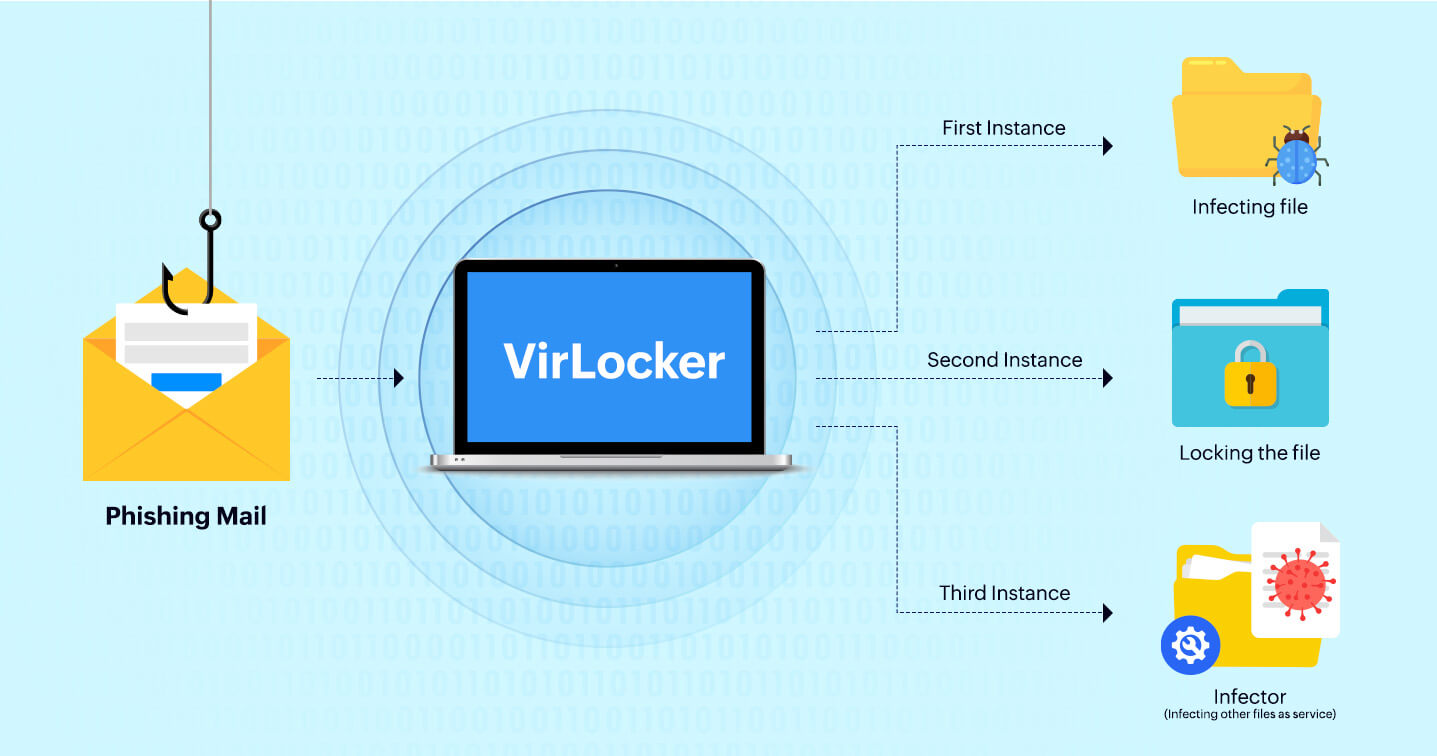
Ransomware is most commonly known to get initial access through phishing mail, exploit kits, removable drives, etc. The latest variants of VirLocker are believed to spread through external drives or USB sticks. Once executed, VirLocker drops three instances of itself–one carries out the file infection, another locks the machine, and the third registers itself as a service. Each of these three instances is unique, and the body of the code is different not only for each infected host but also each time it is executed. The three instances appear as randomly named executables with different hashes in randomly named folders. It is also known to create and modify registry entries in order to avoid detection. It creates run entries in HKEY_CURRENT_USER and HKEY_LOCAL_MACHINE so that persistence is gained and it is launched each time the operating system boots up. VirLocker then disables explorer.exe and taskmgr.exe, preventing victims from identifying and removing the malicious processes and entries. It also changes registry settings not to show any hidden files, hides file extensions, and disables user access control. The following is a sample set of commands used to alter registry entries:
The files most commonly targeted by VirLocker include executable files, document files, archive files, audio/video files, and image files (EXE, DOC, XLS, PDF, PPT, ZIP, RAR, MP3, MPG, WMA, PNG, GIF, BMP, JPG, JPEG, etc.). For the files that are not EXE files, VirLocker attaches ‘.exe’ to the original filename. For example, a file named ‘CentreABC.pdf’, would be modified as ‘CentreABC.pdf.exe’. As the file extensions are hidden by VirLocker, these changes are not visible to the user.
Since variants of VirLocker are capable of spreading through cloud storage and collaboration apps, every infected file on the first victim’s system is essentially a weapon that is capable of spreading and infecting other systems on the network. Consider a scenario where one user gets infected with VirLocker. VirLocker will encrypt all the files on this user's system and turn each into VirLocker infector files. Now, if this user has any shared files and folders, they will also get infected. When another user clicks on any of these shared files, VirLocker is executed on their system, and all other files on that system are also encrypted and converted into a VirLocker file infector. This scenario will extend to all the users who are collaborating with one another through cloud storage apps, infecting the entire organization in no time.
Once VirLocker is executed and the user system is infected, the following ransom note is displayed on the screen.
Interestingly, VirLocker disguises itself as an anti-piracy warning from the FBI. It claims that some pirated software has been detected on the victim’s computer, and threatens them with legal consequences if they don’t pay up the so-called ‘first-time offender’ fine, which essentially is the ransom. VirLocker is also known to check the geo-location of the device by searching the registry and display a message suitable to the victim’s location.
As with any other ransomware attack, paying the ransom can never really guarantee that a victim will get all their files back. However, with VirLocker the situation becomes so much worse, because the files are not only encrypted, they are infected as well. Victims are increasingly being advised by security experts not to pay the ransom, because even if they can get back their files, it is likely that a sneaky infected file could be lying somewhere undetected in the system. And if a user happens to click this file unknowingly, it will start the whole nightmare again.
Several standalone cleaners and removal tools are available for VirLocker, but the problem of leaving behind a few infected files always remains. An effective security solution should be able to track an attack quickly, investigate the root cause, and take remedial actions. Our SIEM solution, ManageEngine Log360, helps prevent attacks by alerting if any unusual events or activities are detected, and initiating an automatic remediation processes. To fully evaluate how Log360 can help your organization defend against VirLocker and other cyberattacks, sign up for a personalized demo.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.