Related content
DDoS attack meaning
A distributed denial-of-service (DDoS) attack is a cyber assault aimed at overwhelming a target system, network, or service with a flood of malicious traffic. Unlike a denial-of-service (DoS) attack, which originates from a single source, a DDoS attack leverages multiple compromised devices (often forming a botnet) to amplify the attack. These devices, typically hijacked through malware infections, execute coordinated requests to exhaust bandwidth, CPU, or memory resources, rendering the target inaccessible to legitimate users.
How does a DDoS attack work?
DDoS attacks exploit the fundamental limitations of networked systems by bombarding them with excessive traffic. The attack usually follows these stages:
- Botnet formation: The attacker infects numerous devices, including computers, IoT devices, and even cloud-based systems, with malware, converting them into bots. These compromised devices are controlled via a command and control (C2) server, which allows the attacker to manage and orchestrate large-scale attack campaigns. The malware used can propagate through phishing emails, malicious downloads, or exploiting software vulnerabilities.
- Attack initiation: Once the botnet is established, the attacker issues commands to the compromised devices, instructing them to send massive amounts of traffic to the target. The attack can involve high-volume requests, malformed packets, or sophisticated request sequences designed to exploit weaknesses in the target’s network stack or application architecture.
- Resource exhaustion: The flood of malicious traffic overwhelms server resources, consuming bandwidth, CPU, memory, and network connection slots. This results in degraded performance, slower response times, and eventually, a complete service outage. Attackers often use adaptive attack strategies, dynamically shifting traffic patterns to bypass mitigation efforts.
- Impact and exploitation: DDoS attacks can serve multiple malicious purposes, including:
- Extortion (Ransom DDoS or RDoS): Attackers demand a ransom to stop the attack, leveraging fear and urgency.
- Distraction for cyber intrusions: Attackers use DDoS as a smokescreen while executing a more targeted attack, such as data exfiltration or malware deployment.
- Competitive sabotage: DDoS attacks are used to disrupt rivals in industries like gaming and e-commerce.
- Hacktivism and political disruption: Attackers use DDoS attacks to protest, disrupt government operations, or censor online platforms.
DDoS attack types
DDoS attacks are categorized based on their target layers within the OSI model:
- Volumetric attacks: These DDoS attacks aim to consume the target's available bandwidth by overwhelming it with a massive amount of traffic. The goal is to saturate the network link and prevent legitimate requests from reaching the system. Examples include:
- UDP flood: Overloads a server with numerous User Datagram Protocol (UDP) packets, often targeting open ports and forcing the system to handle unresponsive requests.
- ICMP flood (Ping flood): Consumes bandwidth by sending a large volume of Internet Control Message Protocol (ICMP) echo requests, exhausting network resources.
- DNS amplification: Exploits open DNS resolvers by sending small queries with a spoofed source address (victim’s IP), causing an amplified response flood to the target.
- NTP amplification: Similar to DNS amplification but exploits Network Time Protocol (NTP) servers to reflect and amplify attack traffic.
- Protocol attacks: These DDoS attacks exploit vulnerabilities in network protocol implementations to exhaust server resources. They often manipulate connection-handling processes, leading to system crashes or unresponsive services. Key examples include:
- SYN flood: Exploits the TCP three-way handshake process by sending numerous TCP/SYN requests but never completing the handshake, exhausting connection queues.
- ACK flood: Overwhelms firewalls and load balancers by sending a massive number of TCP ACK packets, forcing devices to track non-existent sessions.
- Fragmentation attacks: Sends fragmented IP packets that require excessive reassembly resources, leading to server exhaustion. Examples include teardrop attacks and overlapping fragment exploits.
- RST/FIN flood: Sends numerous TCP RST or FIN packets to force session terminations, causing disruption to active connections.
- Application layer attacks (Layer 7 attacks): These DDoS attacks specifically target vulnerabilities in web applications and services, often mimicking legitimate user behavior to evade detection. Unlike volumetric and protocol-based attacks, application layer attacks focus on exhausting server-side processing power rather than network bandwidth. The primary attack vectors include:
- HTTP flood: Bombards web servers with an excessive number of HTTP requests, consuming server resources and causing downtime.
- Slowloris attack: Opens multiple HTTP connections and keeps them open indefinitely by sending partial requests, preventing new connections.
- DNS query flood: Overwhelms DNS servers with fake domain resolution requests, leading to DNS service degradation.
- SSL/TLS exhaustion attacks: Exploits the computational overhead of SSL/TLS handshakes by initiating numerous encrypted sessions, overwhelming server resources.
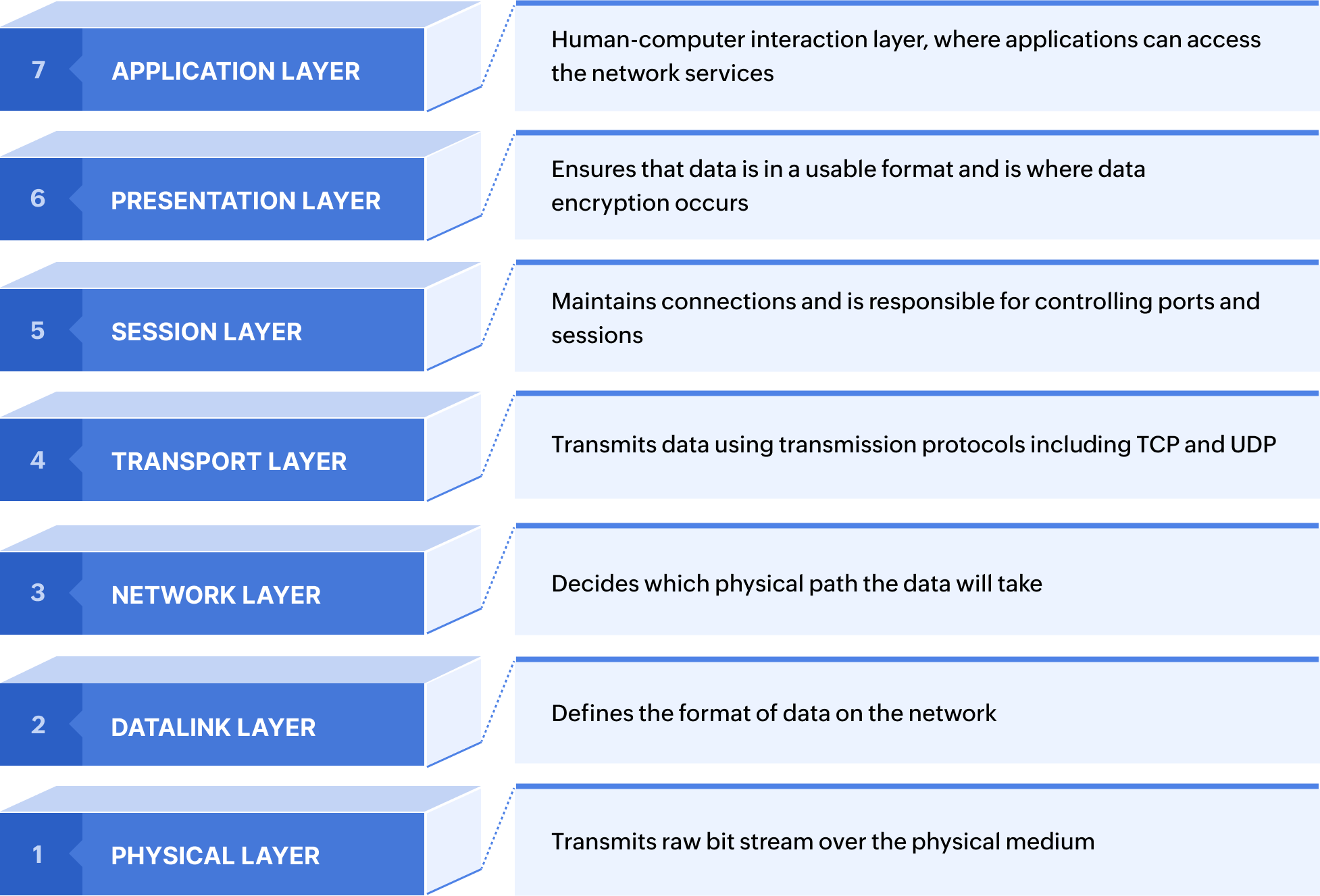
- Layer 7 (Application layer): HTTP floods and bot-based request flooding target web applications.
- Layer 6 (Presentation layer): SSL/TLS-based attacks exploit encryption overhead.
- Layer 5 (Session layer): Attacks manipulate session handling mechanisms, leading to service failures.
- Layer 4 (Transport layer): Protocol-based floods like SYN/ACK targeting TCP connections.
- Layer 3 (Network layer): ICMP and fragmented packet attacks disrupt routing operations.
- Layer 2 (Data link layer): Attacks like MAC flooding exploit network switching mechanisms.
- Layer 1 (Physical layer): Physical-layer disruptions, such as cable-cut attacks, are rare but can be highly disruptive.
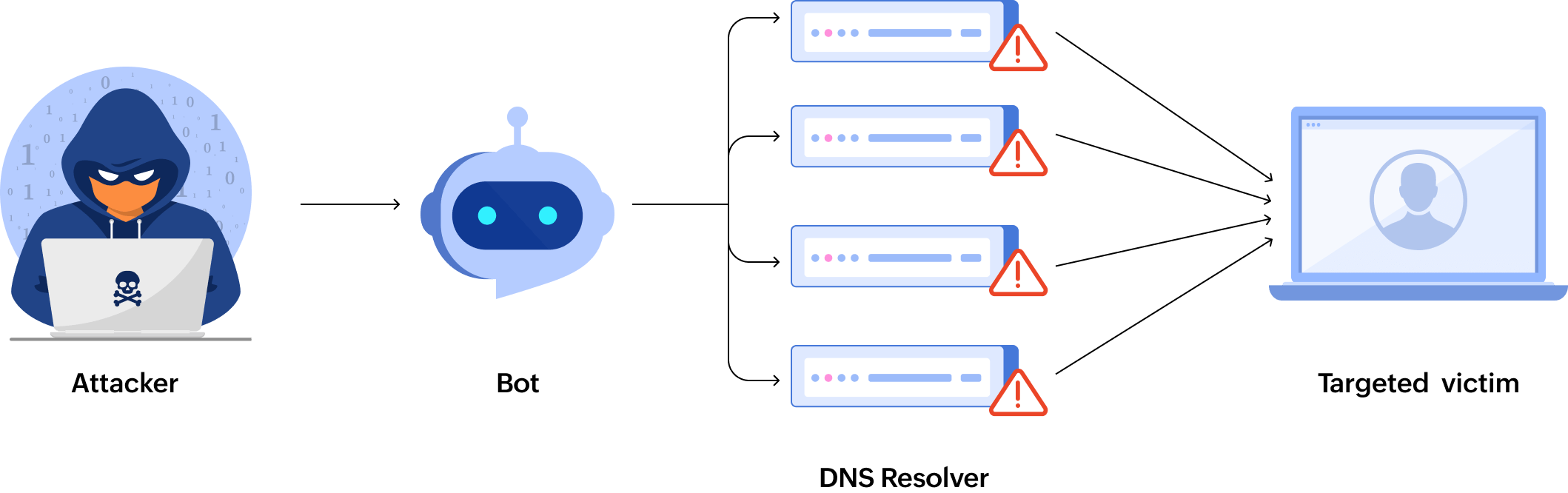
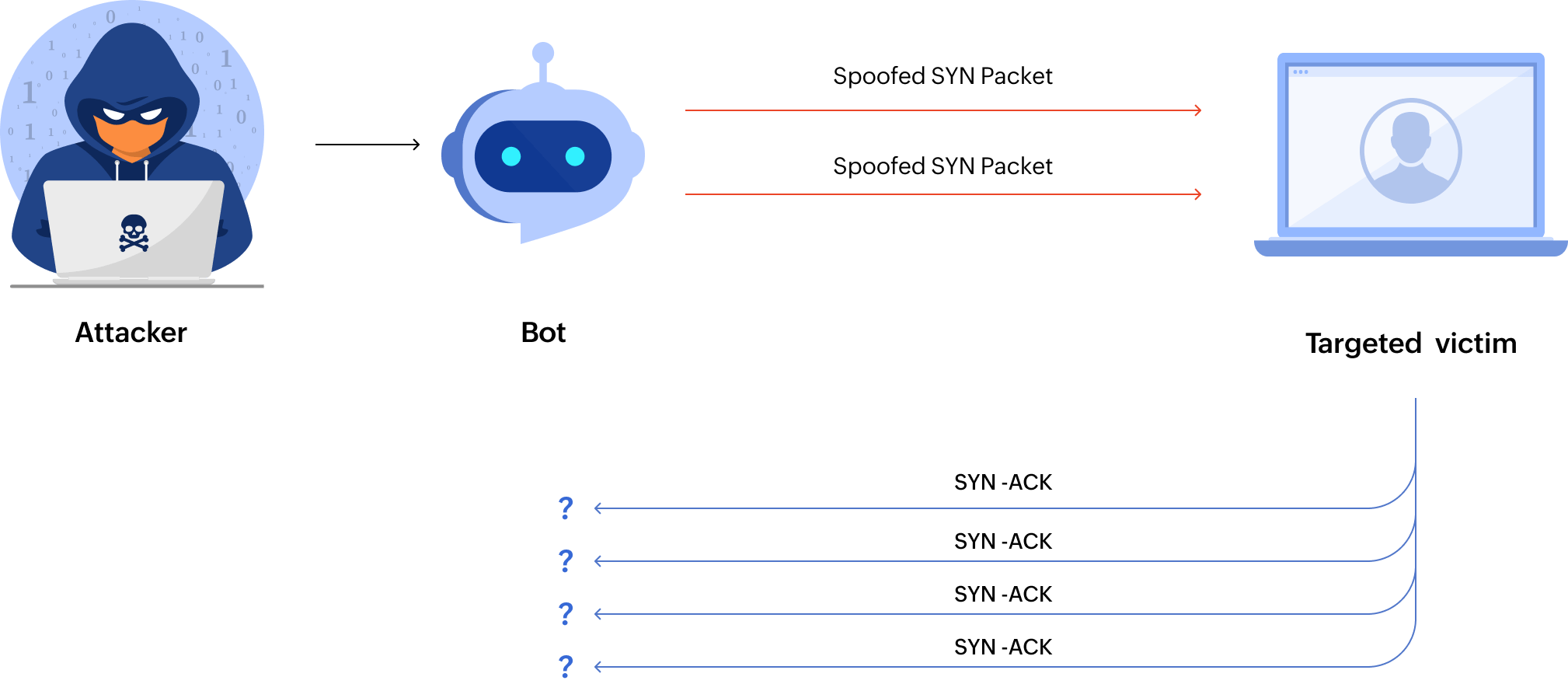
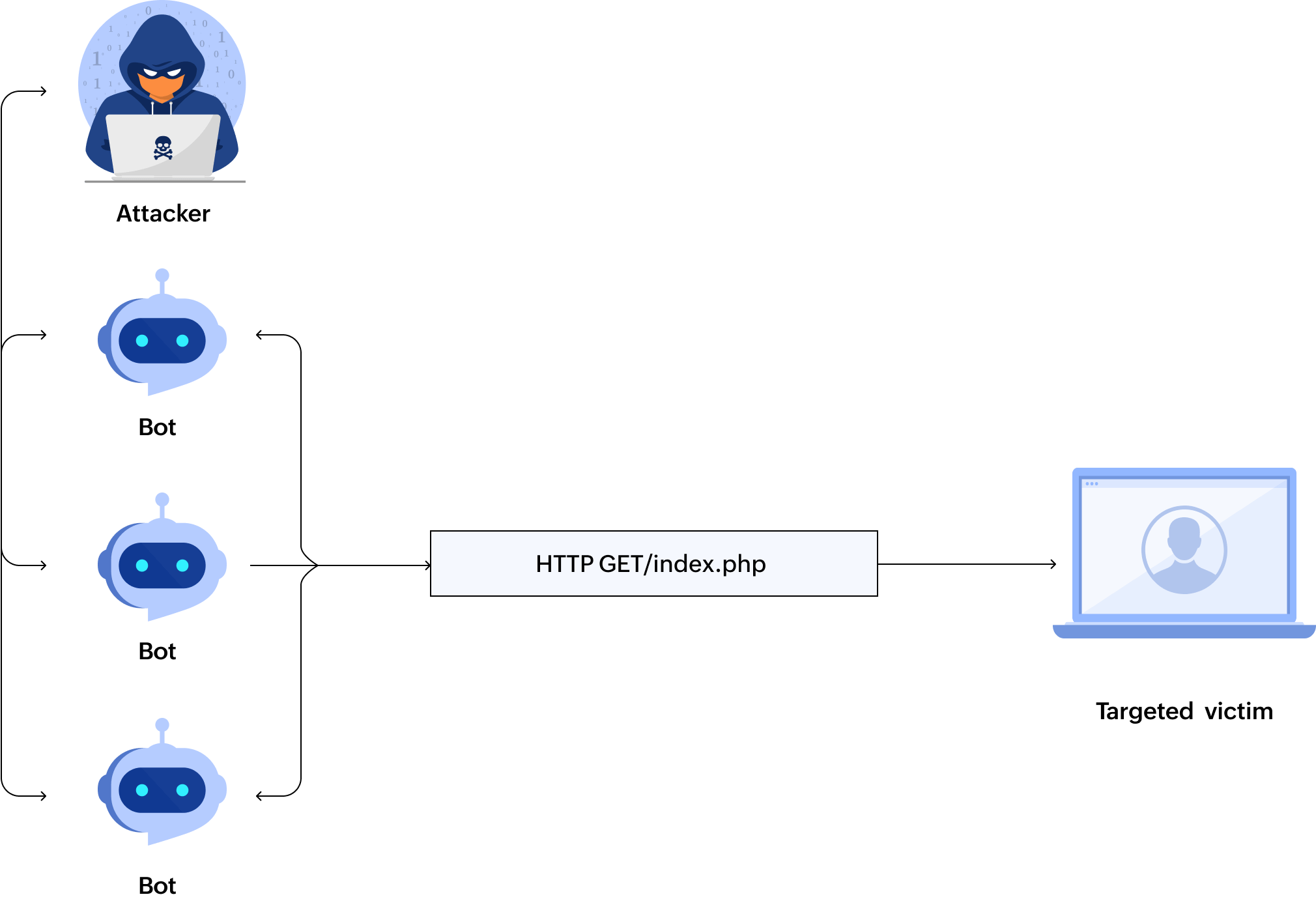
Application-layer DDoS attacks can target different layers of the OSI model:
How to identify a DDoS attack
Detecting a DDoS attack early is crucial for effective mitigation. Key indicators include:
- Unusual traffic spikes: A sudden and sustained increase in traffic, especially from unknown or geographically dispersed sources.
- Slow network performance: Websites or applications responding sluggishly or timing out unexpectedly.
- Unexplained server crashes: Frequent and unexplained downtime of critical services.
- Unusual traffic patterns: Anomalies such as excessive requests to a specific endpoint, repetitive queries, or traffic from known blocklisted IPs.
- Increased resource utilization: High CPU, memory, or bandwidth consumption without corresponding legitimate user activity.
How to stop a DDoS attack
Once a DDoS attack is detected, the following steps should be taken to mitigate its impact:
- Traffic filtering and rate limiting: Deploy traffic filtering solutions to drop illegitimate traffic and enforce rate limits on requests.
- Deploy DDoS protection services: Utilize cloud-based DDoS mitigation providers that use AI-driven traffic analysis and global scrubbing networks.
- Implement network level defenses: Configure firewalls, intrusion prevention systems (IPS), and load balancers to detect and block malicious traffic.
- Use anycast routing: Distribute traffic across multiple data centers to absorb attack traffic without overwhelming a single point of failure.
- Enable web application firewalls (WAFs): Protect against application-layer attacks like HTTP floods and bot-based exploitation.
- Engage an ISP or CDN: Work with your internet service provider (ISP) or a content delivery network (CDN) to filter attack traffic upstream before it reaches your infrastructure.
Want to protect your systems and network from DDoS attacks?
DDoS protection and mitigation
Mitigating DDoS attacks requires a multi-layered security approach, including:
- Real time monitoring: Deploy SIEM solutions to detect traffic anomalies and trigger automated countermeasures.
- Threat intelligence feeds: Utilize real-time threat intelligence to identify known malicious IPs and block them preemptively.
- Redundant infrastructure: Distribute services across multiple geographic locations to absorb traffic surges.
DoS vs. DDoS
| Feature | DoS attack | DDoS attack |
|---|---|---|
| Source | Single device | Multiple compromised devices (botnet) |
| Scale | Limited impact | Large-scale, highly disruptive |
| Detection | Easier to block | Harder to mitigate due to traffic diversity |
| Attack complexity | Simple | Complex, often multi-vector |
| Mitigation | Localized filtering | Requires advanced, multi-layered defense |
Protect against DDos attacks with ManageEngine's security platform
DDoS attacks generate massive amounts of malicious traffic, but the early warning signs often appear in log data, network patterns, and threat intelligence feeds. ManageEngine Log360 is a comprehensive security platform that helps organizations detect, mitigate, and prevent DDoS attacks by offering deep visibility into network traffic, anomalous patterns, and external threat sources.
1. Real time log monitoring and anomaly detection
DDoS attacks often start with reconnaissance or low-volume test floods before escalating into full-scale disruptions. Log360 continuously analyzes logs from firewalls, IDS/IPS, web servers, and network devices to detect early signs of abnormal spikes in requests, repeated failed connections, or unusual traffic from specific geo locations.
- Traffic pattern anomalies: Detects sudden surges in inbound traffic, abnormal connection rates, or excessive requests from a single IP range.
- Firewall and IPS logs: Identifies excessive denied connections, blocklisted IPs attempting access, and protocol-based attack signatures.
- User and entity behavior analytics (UEBA): Flags anomalies such as a sudden flood of API calls or unusual spikes in DNS queries.
2. Threat intelligence integration for proactive defense
DDoS attacks are often executed by botnets, many of which are linked to known malicious IP addresses and domains. Log360 integrates with global threat intelligence feeds to correlate inbound traffic against known bad actors, helping organizations proactively block potential threats before they escalate.
- Threat feed correlation: Automatically matches suspicious IPs with real-time global blocklists of DDoS botnets.
- Dark web monitoring: Detects if an organization’s assets are being targeted in underground forums or botnet-for-hire services.
- Geolocation tracking: Identifies DDoS attempts originating from high-risk regions or anonymized IPs.
3. Deep packet inspection and DNS traffic analysis
DDoS attackers often use amplification attacks via DNS, NTP, and other protocols to flood a target. Log360 enhances detection by analyzing DNS query logs, inspecting malformed packet structures, and identifying protocol abuse.
- DNS traffic monitoring: Identifies excessive requests, spoofed queries, and attempts at DNS amplification.
- Protocol based attack detection: Detects unusual TCP SYN flood attempts, malformed UDP packets, and other protocol anomalies.
- SSL/TLS exhaustion monitoring: Tracks an excessive number of SSL handshake attempts, indicating an SSL-based DDoS attack.
4. Alerts and incident response
Log360 generates alerts based on network anomalies, unusual traffic spikes, and threat intelligence correlations. Security teams can configure alerts for:
- Unusual traffic surges from specific IP ranges or geolocations.
- Excessive requests to critical applications, indicating a Layer 7 attack.
- Repeated connection attempts from flagged threat actors or botnets.
To enhance response actions, customizable workflows allow teams to define automated escalation steps, such as killing a process, disabling a computer or stopping a service.
What's next?
Interested to explore how ManageEngine helped enterprises across the world to tackle DDOS and other cyberattacks? Get in touch with our solution experts
- DDoS attack meaning
- How Does a DDoS Attack Work?
- DDoS Attack Types
- How to identify a DDoS attack
- How to Stop a DDoS Attack
- DDoS Protection and Mitigation
- DoS vs. DDoS
- Protect against DDos attacks with ManageEngine's security platform