Related content
What is the dark web?
The internet is often described in layers. The dark web hides beneath the surface web and the deep web. Unlike the surface web, the dark web isn’t easily accessible to the average user and often involves tools like the Tor browser to conceal identities. These browsers use encryption to hide users' identities and locations. This anonymity makes the dark web a place where illegal activities can take place.
This article dives deeper into the dark web types, potential cybersecurity risks on the dark web and how ManageEngine Log360, a unified SIEM solution, Log360, can help with dark web monitoring.
The dark web iceberg
The internet is classified into three categories—the surface web, the deep web, and the dark web. The surface web includes everything easily accessible through traditional search engines like Google or Bing. Websites like Wikipedia, news sites, e-commerce sites, enterprise websites, and social media are also examples.
Beyond this, we have the deep web—the sites and pages that are not indexed or searchable using the standard search engines. This includes private and enterprise sites that are either gated or pay-walled for data access. Although search engines don’t display deep web content results directly, they often guide users to access points for the deep web. These access points are pages that require users to provide their information or login pages for platforms like e-commerce sites or online banking.
The final layer—the dark web—exists within the deep web but is differentiated by its unique need for special tools, like the Tor browser, to access it. Here, websites often have “.onion” domains, providing anonymity for both users and site operators.
The dark web iceberg is a metaphorical representation that describes different layers of internet accessibility, with the surface web at the top and the most hidden dark web content at the base. This iceberg analogy helps visualize the way content becomes more hidden and sometimes more controversial as you dive deeper. Here’s a common way to break it down:
Surface web (top layer): The visible layer where general content resides. Search engines index this layer.
Shallow deep web (mid-level): Includes databases, academic journals, and password-protected sites.
Dark web (bottom of the iceberg): Anonymous forums, marketplaces that sell attack kits like malware and phishing kits, and other areas that require specialized access like Tor. This part is the most concealed, where one may find controversial, illegal, or highly secure content that is unauthorized. It’s difficult to access, even with advanced tools, as some parts require invitations or special networks.
Suggested reading: Explore the intricate differences between the deep and dark web and how it affects your business. .
Threats and risks of the dark web
The dark web is known for its privacy features due to its encrypted nature, but users should be aware of the risks involved, especially as some parts harbor illegal activities and are a breeding ground for cybercrime. By 2020, researchers found that illegal content, including violent materials, extremist propaganda, illicit marketplaces, drugs, and cybercrime discussions, was being hosted on about 57% of the dark web. By 2023, highly profitable illegal digital goods on the dark web included cryptocurrency accounts, online banking credentials, and e-wallets. Here are some primary concerns:
Illegal activities: There are numerous illegal sites on the dark web that are a hotbed for criminal activities. This includes marketplaces that sell drugs, weapons, illegal documents, and other illegal goods. Law enforcement agencies and governments may monitor many of these illegal sites, and even unknowingly browsing or accessing certain areas could lead to legal consequences.
Scams and fraud: One of the most common dangers on the dark web is the prevalence of scams. Marketplaces present on the dark web can be fraudulent in nature, where users may pay for goods or services and never receive them. Scammers often target those seeking to buy illegal or hard-to-find items, so it’s crucial to be cautious and skeptical of offers that seem too good to be true.
Uncertain anonymity: While the dark web provides anonymity through tools like Tor, it is not entirely foolproof. Governments, law enforcement, and cybercriminals monitor dark web traffic, and may utilize techniques to track users or uncover identities in necessary cases.
Malware: The dark web contains many websites that may infect your device with malware, viruses, tracking software, or ransomware. They can steal personal data or compromise security. Users should take precautions, such as using a SIEM solution to gain protection from malware threats and avoiding suspicious downloads or links.
Ransomware: Ransomware-as-a-Service (RaaS) is one of the most prominent models on the dark web. Major cybercriminal groups like LockBit and BlackCat use this model, where they develop the ransomware strains and the affiliates execute the attacks. Affiliates often gain initial access via brokers who sell compromised credentials.
Botnet: These networks of compromised devices can be used for DDoS attacks, spamming, and cryptocurrency mining. Popular botnets like Mirai and Qakbot exploit vulnerabilities in IoT devices or systems with weak credentials. The dark web also offers botnet creation tools and services, including renting preconfigured botnets for malicious campaigns, making it accessible even for less sophisticated attackers.
Other common threats and risks include backdoors, Trojan horses, keyloggers, Bitcoin-related scams and more.
How to stay safe on the dark web
If you decide to explore the dark web, taking the proper precautions is essential. Secure software like Tor enables anonymous browsing by routing traffic through encrypted relays. Combining this with a reliable VPN adds an extra layer of privacy by encrypting your internet connection and masking your IP address. Onion routing, a core feature of Tor, enhances privacy further by encrypting data in multiple layers and transmitting it through random servers.
It's important to avoid engaging with unknown sources and never downloading files from untrusted sites. Lastly, always be mindful of the legal and ethical implications of dark web activities, as even innocent browsing can inadvertently expose you to harmful content, including darknet markets.
Why dark web monitoring is essential for enterprises?
Cybercriminals use the dark web to carry out different advanced techniques to perform security breaches and compromise data. This includes attacks like social engineering, phishing, DDoS, credential-based attacks and financial cybercrime. As of April 2023, cybercriminals could purchase the details of a credit card with a $5,000 balance for just $110. This shows the ease of usage of the dark web and the extent of cybercrime that can be committed.
Dark web monitoring entails actively observing hidden online networks to identify and address threats such as stolen data, PII, credentials, credit card information, and illegal activities. It enables early identification of compromised information, allowing organizations to quickly respond to potential cybersecurity risks before they grow more severe.
How you can use ManageEngine Log360 to stay ahead of dark web threats
ManageEngine Log360 is a unified SIEM solution that includes robust dark web monitoring features to detect activities targeting your organization. Through its integration with Constella Intelligence, a digital risk intelligence provider, Log360 offers continuous monitoring of the dark web for potential data leaks. This integration ensures that any exposure of PII such as name, email, credentials, and credit card information on the dark web is immediately flagged. Many compliance regulations such as GDPR, CPRA/CCPA, DORA, NIS 2 and more mandate that organizations implement proactive security measures to protect sensitive data and mitigate risks. These dark web insights from Log360 help security teams to act swiftly, preventing further exploitation and potential attacks. By adopting this approach, organizations take a more proactive stance in threat detection and mitigation.
Log360's dark web monitoring capability allows you to track the dark web for the exposure of sensitive data, including credit card numbers, compromised passwords, usernames, email addresses, domain names, and other illicitly traded information by cybercriminals. You can also gain insights into your personal data exposure associated with third-party websites and applications, ensuring proactive security beyond your organization.
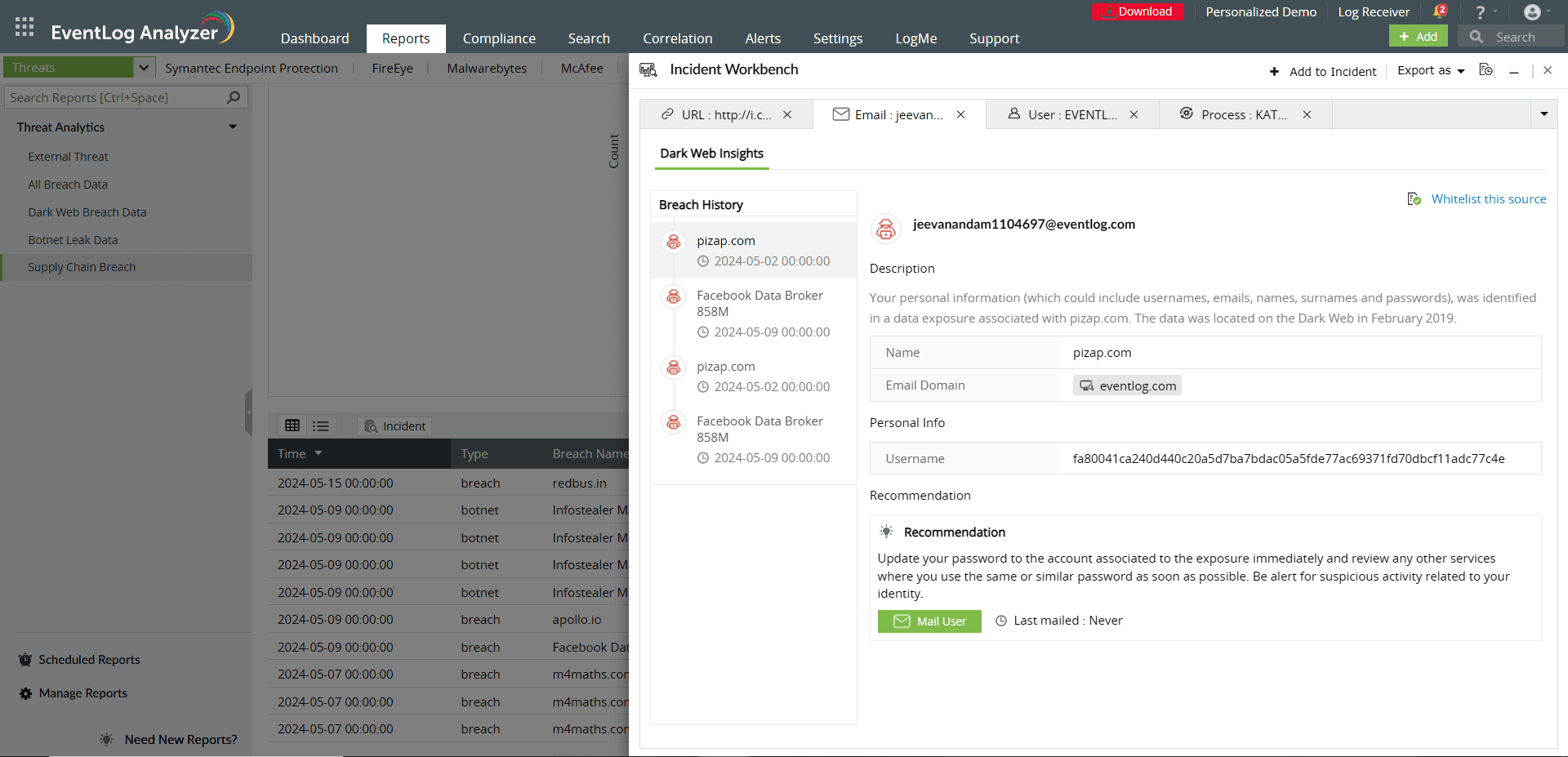
In addition, Log360 provides real-time alerts for threats such as phishing, social engineering attacks, and account takeovers, enabling users to take proactive measures and strengthen their security defenses.
FAQs
- How do you access the dark web?
-
To access the dark web, download the Tor browser from the official Tor Project website. Tor provides anonymity by encrypting your connection and routing it through multiple servers. Using a VPN with Tor is recommended for extra privacy. Once in Tor, you can visit “.onion” websites, but you’ll need directories like "The Hidden Wiki" to find legitimate links, as regular search engines won’t work. Always avoid sharing personal information, clicking unknown links, or downloading files, as some sites may be unsafe.
- What is Tor and is it safe?
-
Tor is a browser that provides access to the dark web, and while it offers anonymity, it is not entirely foolproof. Security and privacy measures should still be practiced.
- Can I be tracked on the dark web?
-
Although Tor masks user IP addresses, government agencies can still track you, so avoid engaging in risky activities.
- What are legitimate uses of the dark web?
-
Legitimate uses can include secure communication for individuals who wish to express their views freely while having their privacy protected and using privacy tools.
- How big is the dark web?
-
The dark web is a relatively small part of the internet but is difficult to measure precisely due to its hidden and dynamic nature. While estimates vary, the dark web makes up only about 4% of the internet. Most internet data lies in the deep web—content not indexed by search engines, such as academic databases, private files, and subscription sites. The dark web itself is just a fraction of this deep web, hosting hidden sites and forums that require special software like the Tor browser for access.
What should I do now?
You can continue your journey of staying safe on the dark web through the following ways:
- Schedule a product tour with us to see Log360's powerful dark web monitoring capability in action.
- Download a free trial of Log360 to try out the solution in your environment.
- Explore use cases on the type of dark web threats that can be detected.
- What is the dark web?
- The dark web iceberg
- Is the dark web dangerous?
- Why dark web monitoring?
- How you can use ManageEngine Log360 to stay ahead of dark web threats