Key takeaways
- What is MITRE ATT&CK®? The MITRE ATT&CK® framework is a globally recognized, comprehensive matrix used by cybersecurity professionals to categorize and understand adversary tactics, techniques, and procedures (TTPs). It helps organizations detect and mitigate cyberattacks by modeling real-world adversarial behaviors.
- Core Components: Tactics, Techniques, and Procedures: The framework is built around tactics, techniques, and procedures (TTPs) which outline how adversaries approach and execute their attacks. These components guide security teams in defending against threats by mapping the entire life cycle of a cyberattack.
- Real-world applications of ATT&CK: By leveraging MITRE ATT&CK, organizations gain insights into real-world cyberthreats, improving detection, threat intelligence, and response strategies. It helps security professionals anticipate potential attack vectors and take proactive measures to strengthen their defenses.
- Enhanced threat detection: The ATT&CK framework is integrated into SIEM tools, enabling organizations to automate threat detection through predefined correlation rules, improve incident investigation, and align cybersecurity strategies with compliance standards.
The MITRE ATT&CK framework is a globally recognized knowledge base of adversary TTPs used in real-world cyberattacks. Designed to provide security professionals with detailed insights into adversarial behavior, it empowers organizations to enhance their defenses against sophisticated cyberthreats by categorizing the attack life cycle into actionable steps.
The ATT&CK framework aids in understanding how adversaries operate by modeling their behaviors in a structured way. It is continuously updated based on real-world data, making it a valuable tool for threat detection, response, and cybersecurity strategies. According to recent industry research, organizations implementing the MITRE ATT&CK framework reported a 62% improvement in threat detection capabilities and reduced incident response time by an average of 45%.
Expert Insights on MITRE ATT&CK
The MITRE ATT&CK framework fundamentally transforms security operations when implemented thoughtfully. Rather than trying to address the entire matrix at once, begin with a focused approach—map your existing controls against the techniques most commonly used against your industry, then prioritize addressing the gaps that align with your highest business risks. This practical mapping often reveals unexpected defensive blind spots even in mature environments. For maximum impact, integrate ATT&CK into your existing workflow rather than treating it as a separate initiative: use it to enhance threat hunting, improve security architecture reviews, and create more realistic adversary emulations during testing. The most successful implementations I've seen treat ATT&CK as a continuous journey of improvement, where teams iteratively expand coverage while measuring the reduced dwell time of threats targeting their specific environment.
- Subhalakshmi Ganapathy, Cybersecurity expert
Understanding MITRE ATT&CK: Tactics, techniques, and procedures (TTPs)
The MITRE ATT&CK framework categorizes adversary behavior into three core components, often referred to as TTPs: Tactics, Techniques, and Procedures.
- Tactics represent the adversary's high-level objectives during an attack, such as gaining access to a system or maintaining persistence. They provide insight into the why of an adversary's actions.
- Techniques are the methods adversaries use to accomplish their goals. For example, an adversary may use a brute force technique to gain access to credentials.
- Procedures are the detailed steps attackers follow to implement a technique. These steps are often highly specific, adapting to the attacker’s goals and the environment they are operating in.
These components help security teams anticipate adversary actions and build defenses tailored to real-world attack strategies. For example, in an attack focused on credential access, an adversary may use the brute force technique and follow a password spraying procedure, where they try common passwords across multiple accounts.
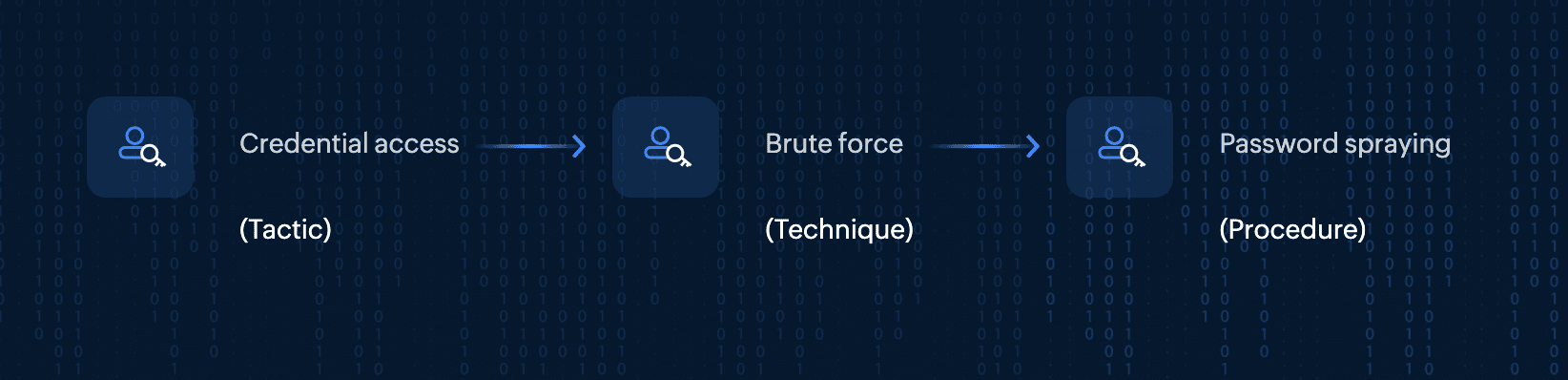
This structured classification enables security teams to better defend against threats by understanding the entire attack life cycle, from the adversary’s goals (tactics) to their specific execution steps (procedures).
The 14 tactics in the MITRE ATT&CK matrix
The MITRE ATT&CK matrix visually represents adversary behavior by breaking down attacks into 14 core tactics. These tactics represent each stage of an adversary's attack, from the initial reconnaissance phase to the final impact on systems.
Video 1: The MITRE framework explained with an example
1. Reconnaissance (TA0043):
The adversary conducts reconnaissance to gather information that will support their future operations. To achieve this, the adversaries often employ passive methods to avoid detection, such as researching public resources for information on targets.
2. Resource development (TA0042):
This tactic involves adversaries creating or obtaining resources, like establishing command and control infrastructure or acquiring tools, that support their operations. These resources aid in launching attacks and maintaining a presence within a target's environment.
3. Initial access (TA0001):
The adversary seeks to enter your network. Techniques for initial access include tactics like spear phishing, exploiting public-facing applications, or using stolen credentials to masquerade as legitimate users.
4. Execution (TA0002):
The adversary will try to execute malicious code on a local or remote system. This could be achieved through various means, such as user execution of a malicious file or automated execution via a vulnerability exploit.
5. Persistence (TA0003):
The adversary will try to maintain their foothold in the network. Adversaries may create accounts, manipulate existing ones, or use legitimate credentials to ensure continued access to compromised systems. This includes during disruptions like system restarts or credential changes.
6. Privilege escalation (TA0004):
The adversary will try to gain higher-level permissions in a system or network. To achieve this, adversaries might utilize software vulnerabilities to elevate privileges. Exploiting such vulnerabilities involves taking advantage of programming errors within programs, services, or the operating system software itself. This allows adversaries to execute their own code, exerting control over the compromised system.
7. Defense evasion (TA0005):
The adversary uses defense evasion to avoid being detected. They may disguise their actions, modify system processes, or use obfuscation to hide their activities. This allowing them to remain undetected while conducting their operations.
8. Credential access (TA0006):
The adversary aims to steal credentials like passwords or tokens to gain access to systems, services, and network resources. To achieve this, adversaries might employ brute-force techniques to gain unauthorized access to accounts when passwords are either unknown or when they have obtained password hashes.
9. Discovery (TA0007):
The adversary will try to figure out your systems and environment. To achieve this, adversaries might turn to network sniffing to gather information about a targeted environment. This involves intercepting sensitive login credentials and other network traffic.
10. Lateral movement (TA0008):
The adversary will try to move through your environment to gain control of additional systems. Techniques include using stolen credentials to access networked devices, or employing methods like pass-the-ticket or remote services to extend their reach within the network.
11. Collection (TA0009):
The adversary will try to gather data of interest to their goal. To achieve this, adversaries might attempt to collect data from sensitive documents, key operational data, or proprietary technology within compromised environments, often before exfiltration.
12. Command & control (TA011):
The adversary will try to communicate with compromised systems to control them. To achieve this, adversaries might employ a connection proxy, which acts as an intermediary for network traffic between systems. By doing so, they can redirect network traffic through the proxy, avoiding direct links to their own infrastructure or command and control servers.
13. Exfiltration (TA0010):
The adversary will try to steal data from their targets. To achieve this, adversaries might illicitly move data, including backups of cloud environments, from one cloud account to another that they control within the same service. This is done to avoid standard detection systems that might trigger alerts based on file transfers, downloads, or network-based exfiltration.
14. Impact (TA0040):
The adversary will try to manipulate, interrupt, or destroy your systems and data. To achieve this, adversaries might disrupt the availability of systems, services, and network resources by deliberately deleting data and files on targeted systems or across an entire network.
Additional resource: Play the role of the cybercriminal and understand the tactics behind a real-world cyberattack and learn how to defend against them.
How the MITRE ATT&CK framework works
The MITRE ATT&CK framework is organized into a matrix that categorizes the behaviors of adversaries across different attack stages. The framework covers a variety of environments, including enterprise systems, mobile devices, and industrial control systems (ICS). This allows organizations across various sectors to adopt it and improve their cyberdefense strategies.
The structure of the MITRE ATT&CK matrix
The ATT&CK matrix is divided into rows representing adversary tactics and columns representing techniques used to achieve these tactics. Each tactic, such as initial access or lateral movement, is accompanied by a list of specific techniques adversaries might use. For example, under the credential access tactic, techniques like password spraying or keylogging are listed.
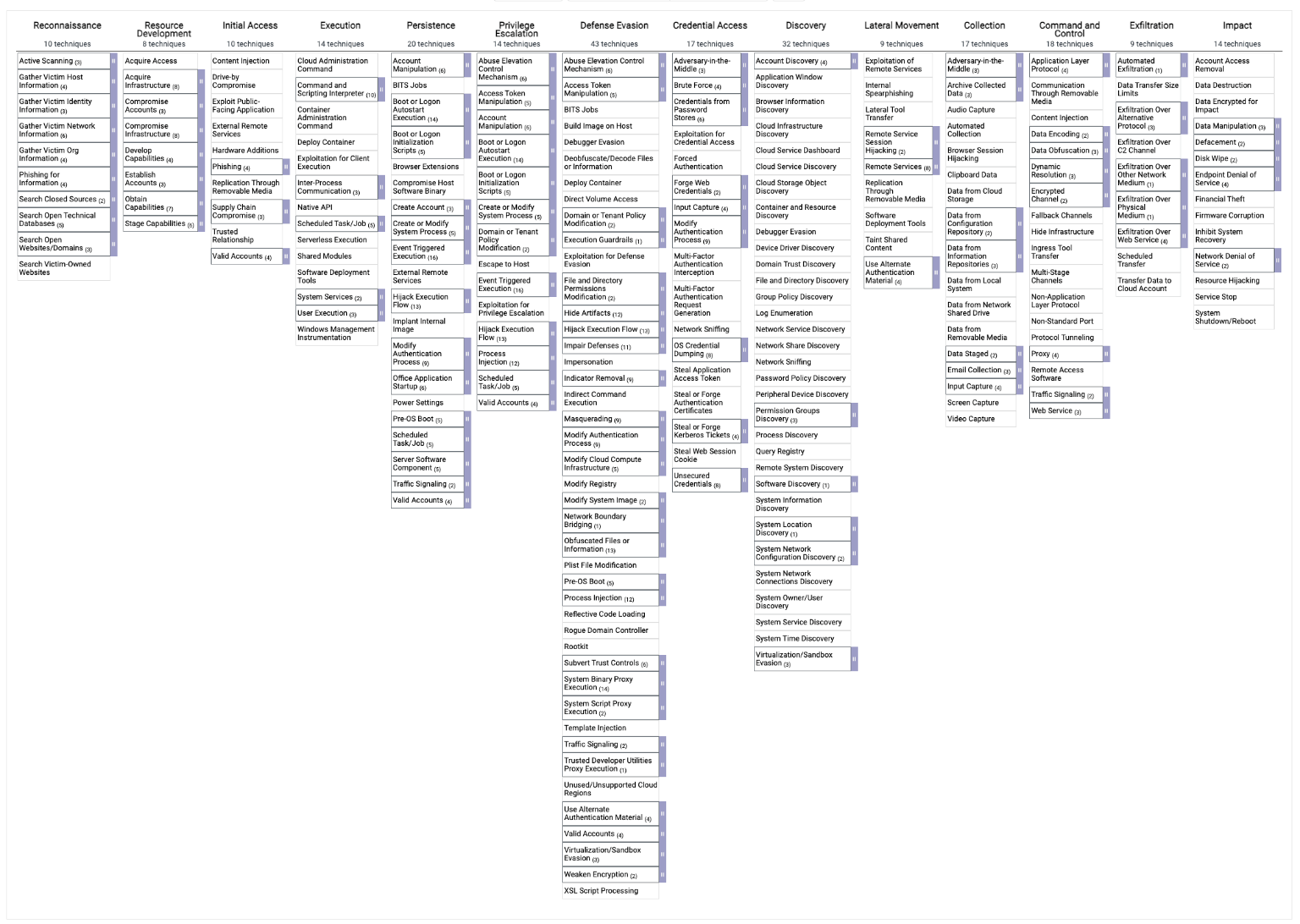
Each technique may also be broken down further into sub-techniques, which provide even more detail on how adversaries might execute an attack. This structure allows organizations to map out the entire attack life cycle, from the initial reconnaissance to the final impact on the target systems.
Multi-platform coverage
The MITRE ATT&CK framework covers three major domains:
- Enterprise ATT&CK: Focuses on tactics and techniques targeting traditional enterprise environments, such as Windows, Linux, and macOS systems. This domain includes a broad range of attack vectors, including network exploits, credential theft, and malware delivery.
- Mobile ATT&CK: Focuses on tactics and techniques used in attacks on mobile devices, covering both iOS and Android platforms. This domain includes techniques like data extraction, location tracking, and device compromise through malicious apps.
- ICS ATT&CK: Focuses on tactics and techniques that adversaries use to target industrial control systems, which are critical for sectors like energy, manufacturing, and transportation. These attacks often aim to disrupt physical processes, causing damage or downtime.
How the matrix enhances cyberdefense
By leveraging the MITRE ATT&CK matrix, security teams can:
- Visualize the attack life cycle: The matrix provides a clear representation of each phase of an attack, from reconnaissance to impact. This helps security teams understand how adversaries progress through their attacks, allowing them to anticipate the next steps.
- Detect early indicators of compromise (IoCs): The framework helps organizations identify IoCs related to each technique. For example, if a technique like lateral movement is detected, teams can look for indicators such as unauthorized remote access or unusual credential usage. This enables faster detection of active threats.
- Correlate threat intelligence: Security teams can map threat intelligence and real-world incidents to specific techniques in the matrix. This helps build a comprehensive picture of how adversaries are behaving in real-time and allows organizations to adjust defenses accordingly.
- Prioritize security efforts: By using the matrix, teams can prioritize high-risk techniques and tactics that are most relevant to their environment. For instance, a company operating in a cloud-heavy environment might focus on techniques related to cloud account compromise, while an ICS-heavy organization may focus on techniques targeting industrial control systems.
Additional resources:
From understanding to defending: Explore how to leverage MITRE ATT&CK to proactively identify and mitigate potential threats.
- USING MITRE ATT&CK® to understand the techniques behind breaches
-Threat hunting 101: Extend your threat detection and investigation with the MITRE ATT&CK framework
Use cases of MITRE ATT&CK
The MITRE ATT&CK framework is widely used by both private and public organizations to improve their cybersecurity posture. Here are the primary use cases:
- Threat intelligence analysis: MITRE ATT&CK offers a common language for categorizing and sharing adversary behaviors, fostering a collective defense against cyberthreats. Analysts can map observed behavior to specific TTPs in the framework, helping organizations track and analyze cyberthreats more effectively.
- Red and blue team exercises: The framework is a critical resource for red teams when emulating real-world adversaries. By simulating attack scenarios, they can identify system vulnerabilities. Blue teams, on the other hand, use the framework to develop detection rules and improve their response strategies.
- Incident response: ATT&CK is used to map incidents back to adversary techniques, enabling faster and more effective response. By pinpointing specific tactics, security teams can correlate these behaviors to alerts, allowing for quicker containment of ongoing attacks.
- Compliance alignment: Organizations can align their security initiatives with compliance standards such as PCI DSS, HIPAA, and GDPR by mapping specific ATT&CK tactics and techniques to regulatory requirements. This helps demonstrate a proactive approach to threat detection and response.
- Automated threat detection: The ATT&CK framework helps automate the identification of adversary behaviors, reducing false positives. By correlating log data and detecting patterns that align with ATT&CK techniques, security teams can improve operational efficiency and focus on higher-priority threats.
Interested in exploring how Log360 leverages SIEM to enhance threat detection? Discover how Log360 uses MITRE ATT&CK to track and mitigate cyberthreats effectively.
Five-step guide to implementing MITRE ATT&CK
Step 1: Assess your current security posture
Document your existing security tools, controls, and processes. Identify your most critical assets and the threats most likely to target your organization.
Step 2: Prioritize relevant tactics and techniques
Based on your industry, analyze which MITRE tactics and techniques are most relevant. Focus on techniques commonly used against organizations like yours.
Step 3: Map Detection Capabilities
Evaluate how well your existing security tools can detect the prioritized techniques. Identify gaps in your detection capabilities.
Step 4: Enhance Detection and Response
Implement new detection rules, controls, or processes to address the identified gaps. Configure your SIEM solution to map alerts to MITRE techniques.
Step 5: Test and Refine
Conduct red team exercises or tabletop scenarios to test your enhanced capabilities. Continuously refine your implementation based on test results and new threat intelligence.
Ready to implement MITRE ATT&CK in your security operations?
Schedule a personalized security assessment to identify how Log360 can help you leverage the MITRE ATT&CK framework in your organization.
How Log360 leverages MITRE ATT&CK for threat detection
By integrating MITRE ATT&CK into Log360, organizations can boost their cybersecurity capabilities. Log360 enhances threat detection and response by:
- Providing ATT&CK-aligned security dashboards and incident reports: These reports give a detailed view of adversary activities mapped to the framework, enabling better situational awareness and quick response times.
- Predefined correlation rules for ATT&CK techniques: Log360 includes predefined correlation rules for detecting ATT&CK techniques, allowing security admins to track and monitor adversary behavior in real-time.
- Actionable mitigation strategies: Log360 offers recommended mitigation strategies for each stage of the attack life cycle, helping teams implement effective countermeasures.
- Comprehensive incident investigation: With in-depth visibility into all 14 tactics and associated techniques, Log360 facilitates thorough investigation of security incidents, ensuring that no threat goes unnoticed.
What our customers are saying
"The alerts that warn of critical security events once detected have been instrumental in our threat detection efforts."
-Mireille Kasikila, system administrator at Zaxby's
Improving threat detection and compliance with MITRE ATT&CK
The MITRE ATT&CK framework offers a comprehensive approach to improving an organization’s cybersecurity posture. With Log360's integration of ATT&CK, organizations can:
- Gain real-time visibility into adversary tactics and techniques.
- Automate threat detection with predefined correlation rules.
- Enhance incident investigations by mapping adversary behaviors to the 14 ATT&CK tactics.
- Strengthen compliance efforts by aligning security strategies with regulatory standards.
Continue reading about critical cyber security practices:
- What is SIEM, a complete guide
- Top five SIEM tools to consider
- 2024 Gartner Magic Quadrant for SIEM report
- Logging guide, a sysadmin's guide for effective log management
- Popular attacks and how to mitigate them
- TDIR, explained
What's next?
Learn how MITRE ATT&CK implementation can improve your SIEM.
Frequently Asked Questions About MITRE ATT&CK
- How do I start implementing MITRE ATT&CK in my organization?
-
Begin by identifying your most critical assets and the threats most likely to target them. Then map your existing security controls to relevant MITRE tactics and techniques to identify coverage gaps. Start small with a few key techniques rather than attempting to cover the entire framework at once.
- How often is the MITRE ATT&CK framework updated?
-
MITRE typically updates the ATT&CK framework biannually, with major releases introducing new techniques, tactics, and refinements based on observed threat actor behaviors.
- What's the difference between tactics, techniques, and procedures?
-
Tactics are the adversary's high-level goals (the "why"), techniques are the methods used to achieve those goals (the "how"), and procedures are the specific implementations of techniques (the "exact steps").
- Is MITRE ATT&CK suitable for small organizations?
-
Yes, organizations of all sizes can benefit from the MITRE ATT&CK framework. Smaller organizations may want to focus on the most common techniques used against their industry rather than trying to address the entire framework at once.
- How does MITRE ATT&CK relate to other frameworks like NIST or ISO?
-
While frameworks like NIST and ISO focus on security controls and best practices, MITRE ATT&CK focuses on adversary behaviors. They complement each other—NIST and ISO help you build a strong security foundation, while MITRE ATT&CK helps you understand and defend against specific attack methods.
- Key takeaways
- Understanding MITRE ATT&CK: Tactics, techniques, and procedures (TTPs)
- The 14 tactics in the MITRE ATT&CK matrix
- How the MITRE ATT&CK framework works
- Multi-platform coverage
- How the matrix enhances cyberdefense
- Use cases of MITRE ATT&CK
- Five-step guide to implementing MITRE ATT&CK
- How Log360 leverages MITRE ATT&CK for threat detection
- Improving threat detection and compliance with MITRE ATT&CK
- Continue reading about critical cyber security practices
- Frequently Asked Questions About MITRE ATT&CK