Protecting your organization's data is crucial in order to avoid monetary loss, reputation damage, loss of confidentiality, non-compliance with government regulations, and more. Securing your database can defend your enterprise from a myriad of security threats including privilege abuse, data exfiltration, data leaks, database injection, and other cyberattacks. Log360, a comprehensive security information and event management (SIEM) solution, provides various feature such as advanced threat analytics, threat hunting, user and entity behavior analytics (UEBA), and more to help your business combat cyberattacks at ease.
Log360 is a one-stop SIEM solution that can help enterprises secure databases and ensure data integrity with its capabilities to:
Spot and mitigate privilege abuse through Log360's privileged user activity monitoring module.
Monitor privileged user activity and identify any anomalous behaviour using the built-in UEBA module powered by machine learning (ML). UEBA works by creating a baseline of user activity and behavior and deems any activity that deviates from the baseline as anomalous. ML-based user activity monitoring helps detect privilege abuse such as database creations, deletions, or modifications.
Assign a risk score based on the activity a user performs, using the solution's dynamic risk management module. Further, Log360 allows you to dynamically change the severity of anomalous events based your organization's requirements.
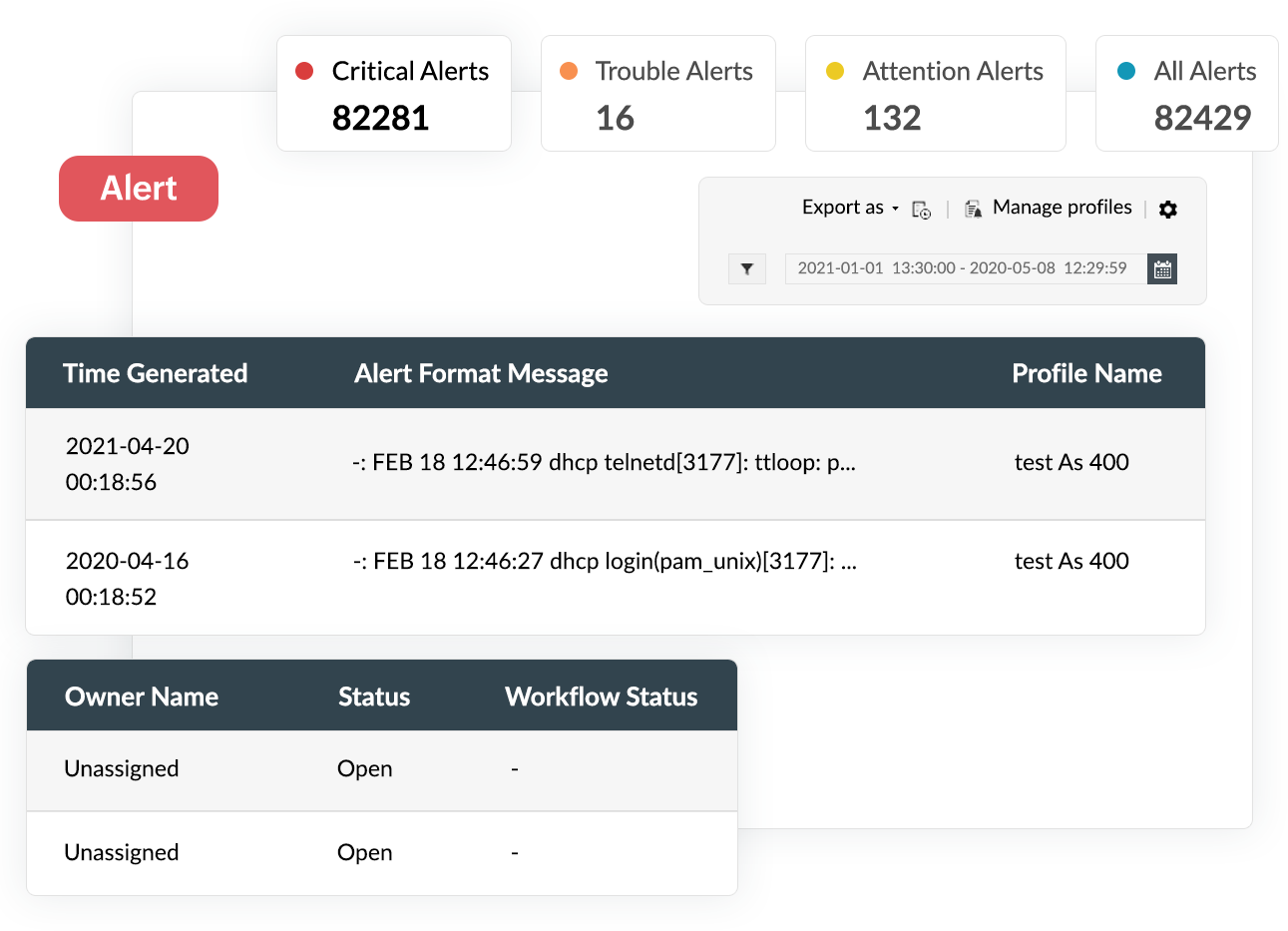
The security and continuous running of business-critical applications such as databases and
web servers are crucial to organizations.
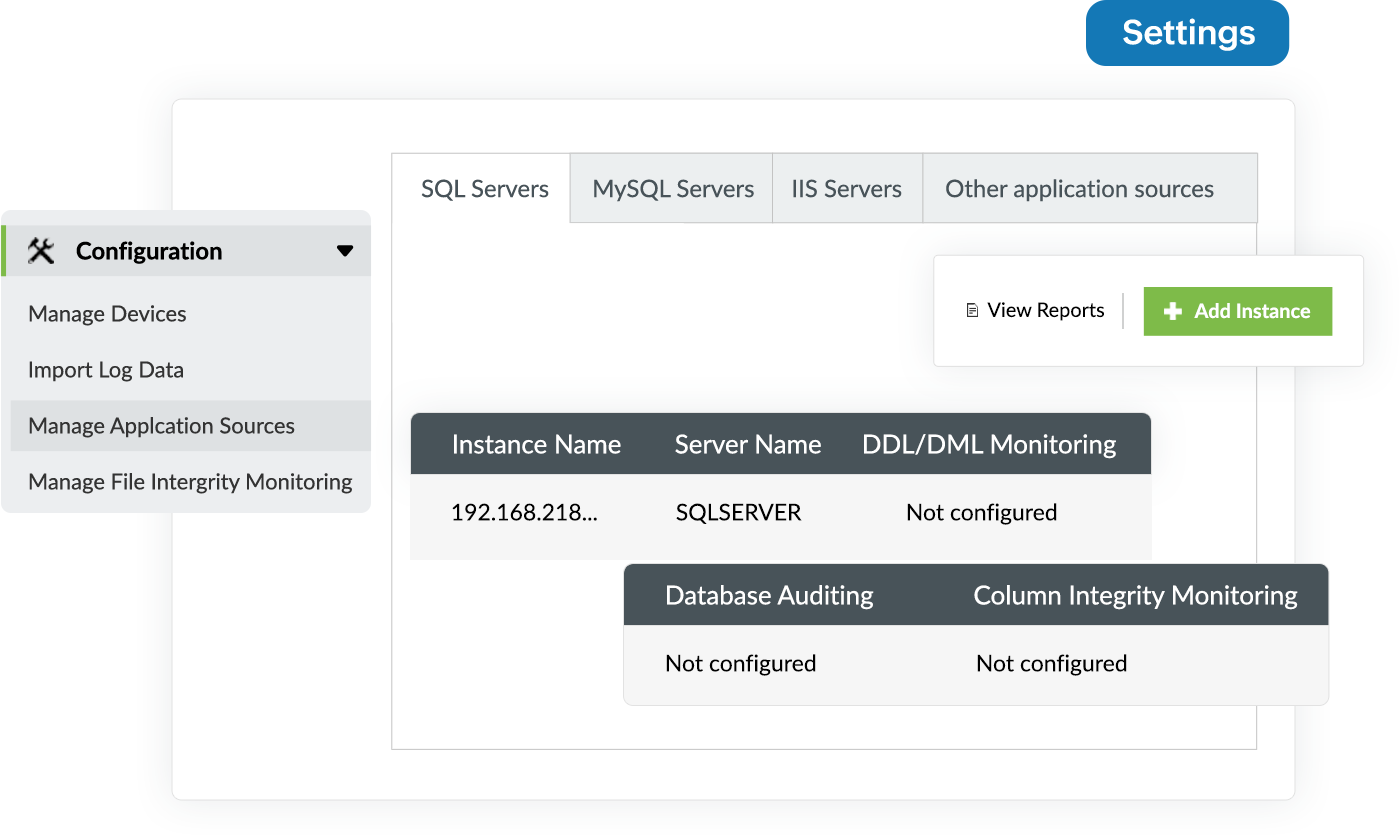
Log360 spots changes made to your SQL and Oracle databases and alerts security personnel by continuously monitoring and auditing DML and DDL activity. You can also track database server account changes using Log360.
Spot and track all changes made to critical database columns using Log360's integrity monitoring feature, which allows you to look for critical database columns and track all changes made to them, including old and new values. This helps you preserve column integrity and restore your database to a stable state in the event of unauthorized changes.
Detect anomalous activity and security attacks that target databases including SQL injection attacks, cross-site-scripting attacks, and more by monitoring database activity and alert your security operations center (SOC).
Data exfiltration is a form of data theft that is challenging to detect and can be detrimental
to your enterprise.
Spot various indicators of compromise and indicators of attack such as bulk copying of data from the database and alert your SOC before a breach actually takes place. Log30 exposes major threats including data exfiltration and compromised accounts with continuous monitoring.
Monitor outbound traffic continuously and send real-time alerts to concerned security personnel when communication takes place with malicious or blocklisted IP's using Log360's threat intelligent module.
Monitor file and folder creation, deletion, modification, and permission changes in databases and more with Log360. This, coupled with the solution's incident management module, makes it effortless for enterprises to spot and mitigate data exfiltration attacks.
With all these advanced features, Log360 goes above and beyond to safeguard your database and prevent cyberattacks. Give these features a spin with a free, 30-day trial of Log360.
Download Now