With IT infrastructure becoming larger and more distributed, devoting more attention and resources to ensuring the security and integrity of data is a necessity. One way to keep tabs on the security of your infrastructure is to analyze application logs.
Collecting logs from various applications is one of the most crucial steps to ensuring the security of your IT infrastructure. Log360, with its complex log collection capabilities, uses both agent-based and agentless log collection methods to leave no entity unnoticed. Log360's custom log parser effortlessly parses all logs in human-readable format. You can also set failure alerts for when applications stop sending logs.
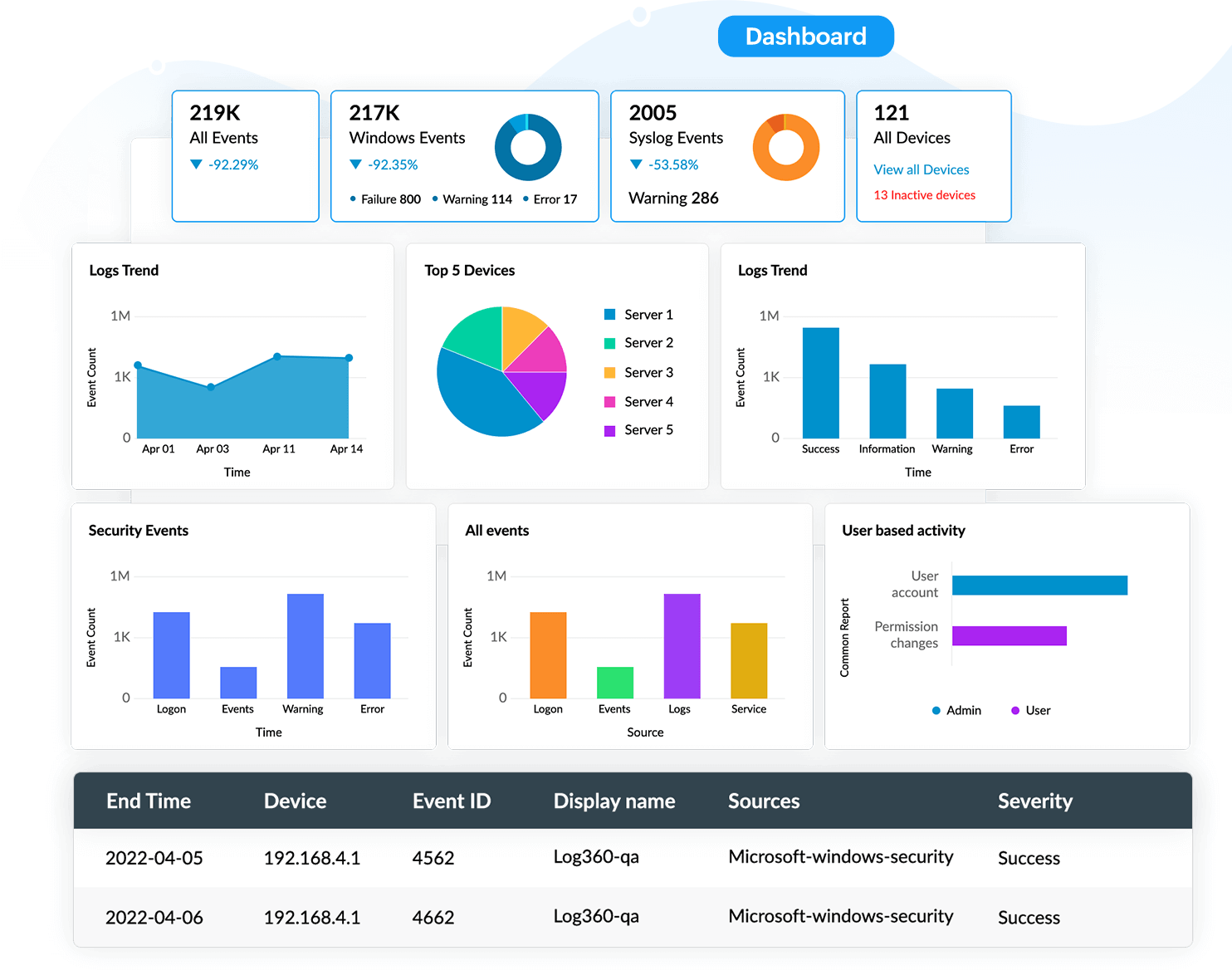
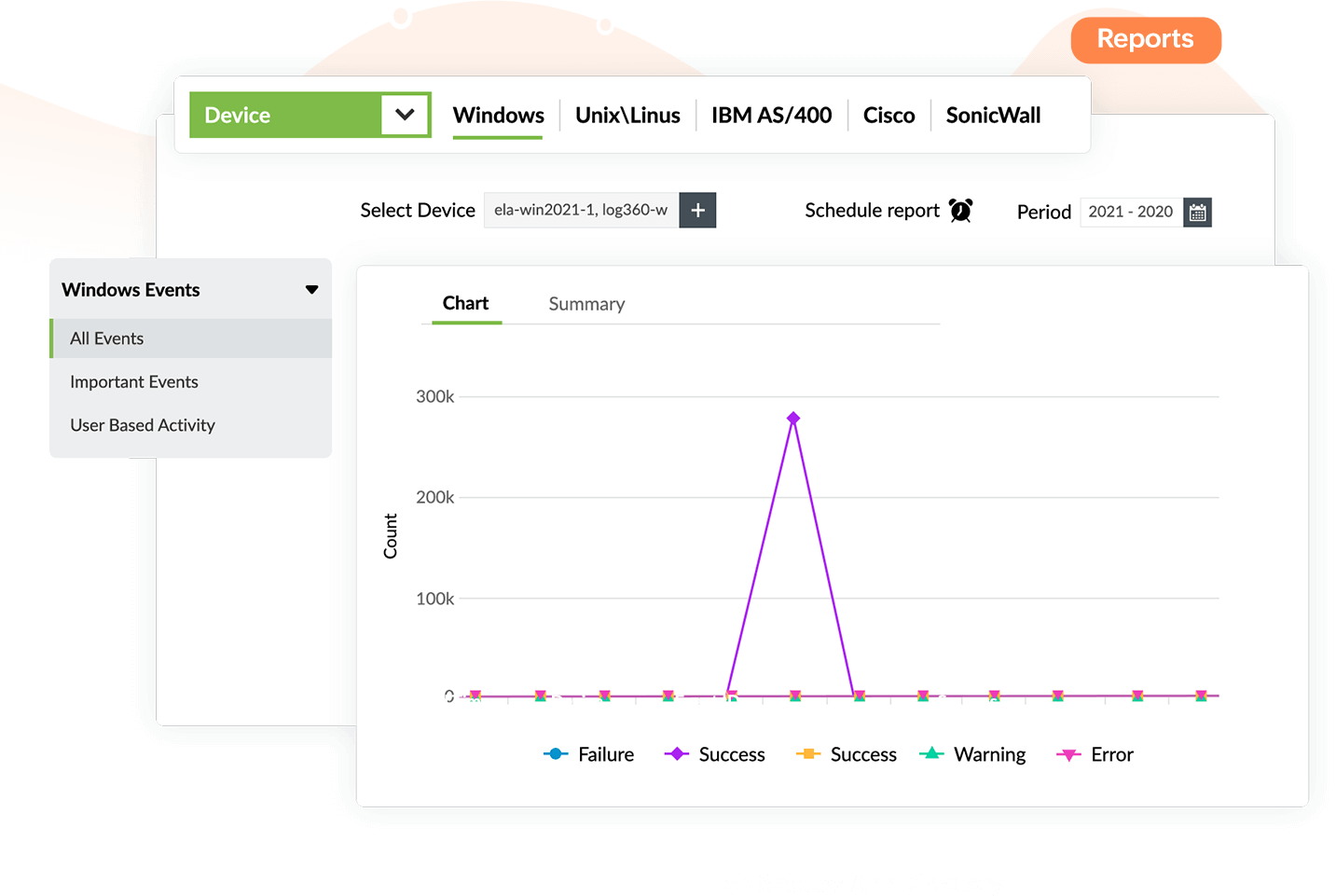
Analyzing logs can help you detect malicious activity in your organization's network. Logs are aggregated, normalized, converted into a readable format, then analyzed. Log360's forensic analysis, coupled with threat intelligence, assists with identifying the point of attack in the network. Log360 indicates how the attack was carried out and which part of the network the attackers compromised to gain entry. All this data is tabulated in the form of reports on the dashboard.
Correlating log data from different log sources helps you detect malicious threats and reduce security risks. Log360 comes with a powerful correlation engine with 30 predefined attack patterns, letting you detect attacks instantly. The custom correlation builder allows you to create custom correlation rules, specify time frames, and use advanced filters for detecting attacks. Data correlation can indicate if the log data collected from different applications corresponds to any event. Log360 checks if this event threatens the network's security posture and raises an alert if needed.
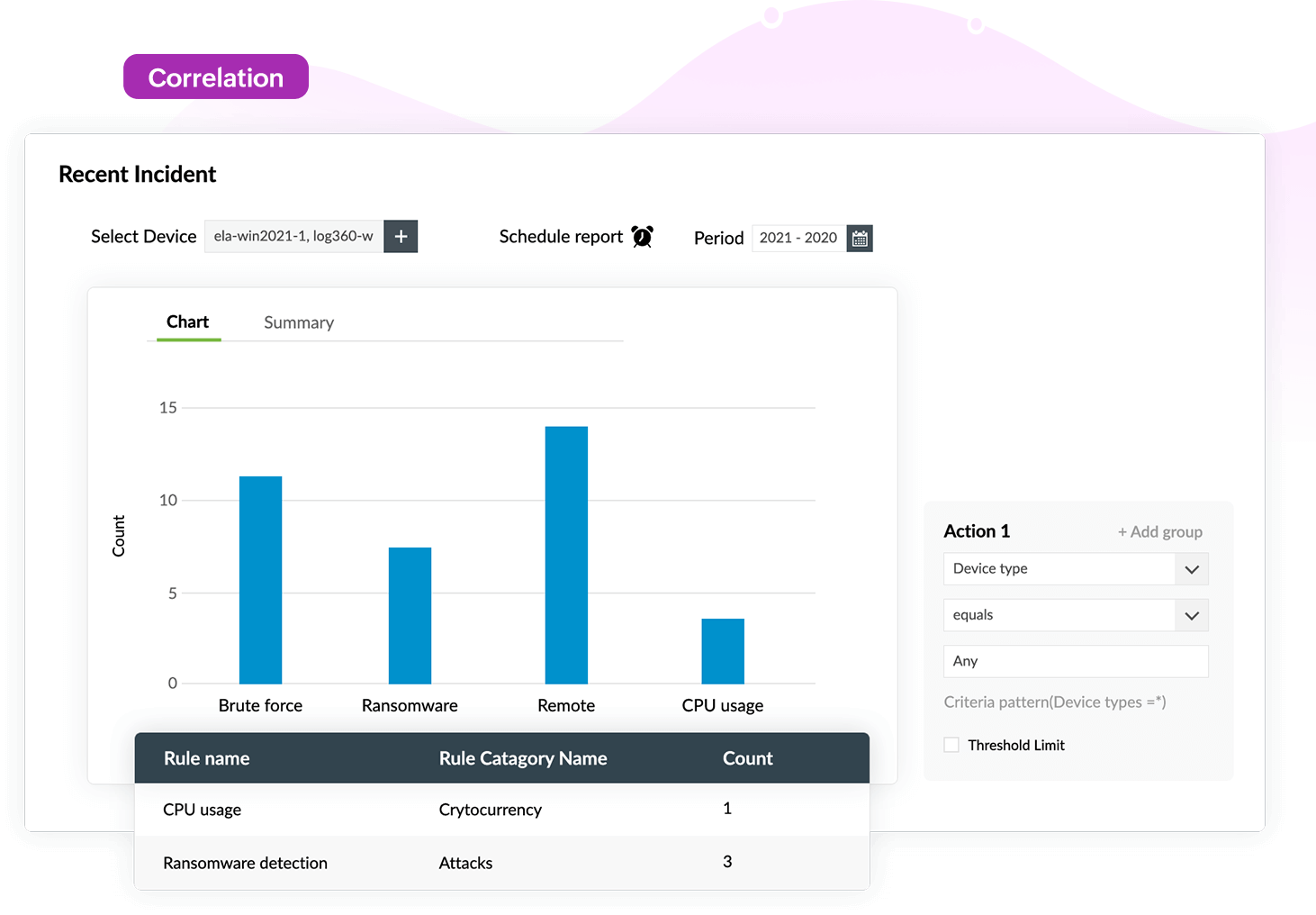

The time frame between the first occurrence of a threat and its remediation is all it takes for attackers to gain control over your network. Log360's automated incident response feature reacts to security threats by associating predefined and custom incident workflows with the events detected. An incident workflow encompasses the sequence of steps to be taken following a security event. Log360's built-in ticketing console allows you to assign and easily manage incidents or forward them to third-party help desk software.
Effortlessly comply with regulatory mandates, like the PCI DSS, HIPAA, SOX, the GDPR, and the CCPA.
Leverage threat feeds to discover malicious IPs, domains, and URLs.
Protect cloud data and cloud accounts from unauthorized access.
Speed up incident mitigation by triaging security threats and automating incident response.
Monitor changes made to your AD environment and tackle privilege escalations.