Fileless malware and living off the land (LOTL) attacks are executed from the system's random access memory (RAM) alongside critical Windows processes, all while evading detection. These attacks leverage native Windows tools to maintain persistence within a system and move laterally across the network.
Conventional security solutions fail to detect such attacks because they rely on indicators of compromise (IoCs), which are typically forensic evidence that an attack has taken place. In contrast, Log360 takes a radical approach by identifying the indicators of attack (IoAs) that detect an ongoing attack. This enables Log360 not only to detect such attacks but also to ensure proactive incident response.
Windows tools leveraged by fileless malware
PowerShell
PowerShell is exploited by attackers to execute remote code, communicate with command and control servers, and obscure scripts to avoid detection.
WMI
WMI allows attackers to move laterally, exfiltrate sensitive data, manipulate system settings, and maintain control over compromised systems.
Command Prompt
Attackers utilize command-line tools, such as certutil.exe, to fetch files and execute them directly in memory, bypassing security measures.
Windows Registry
Attackers exploit the Windows Registry Editor to alter registry entries, causing malicious scripts to execute alongside system processes.
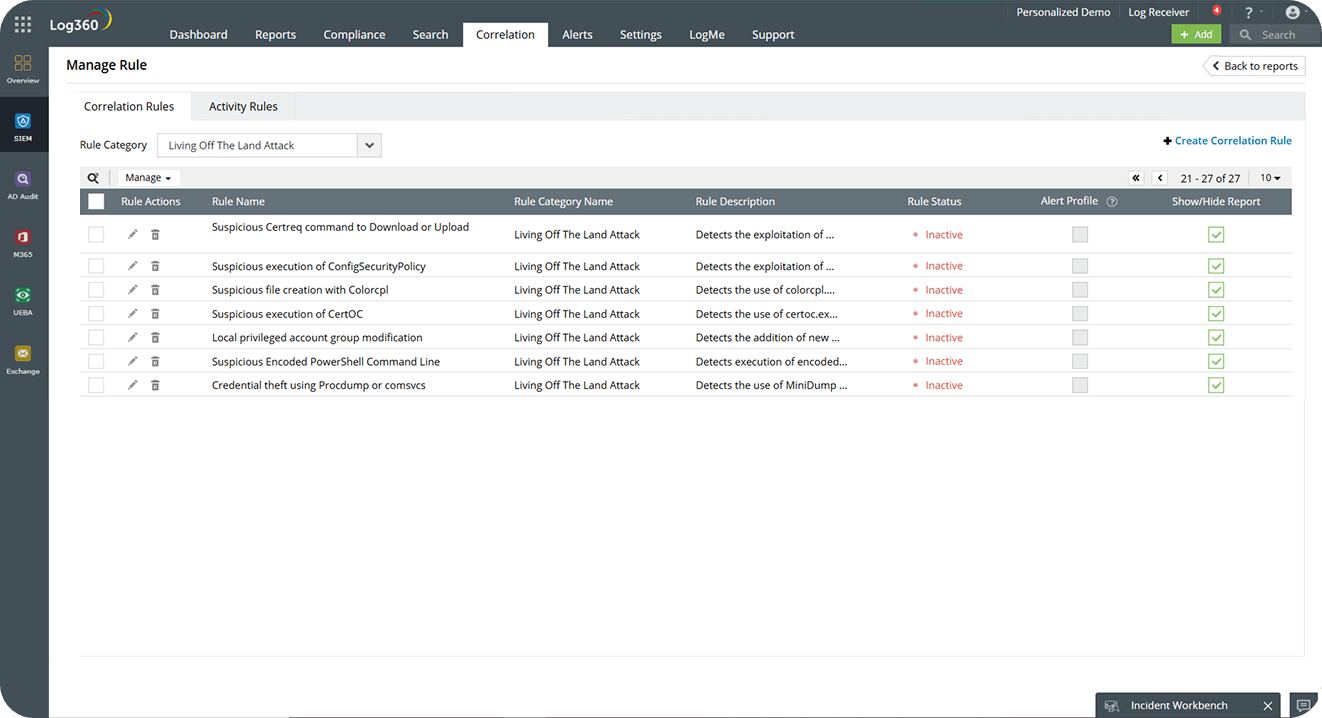
Defend against fileless malware and LOTL attacks with Log360
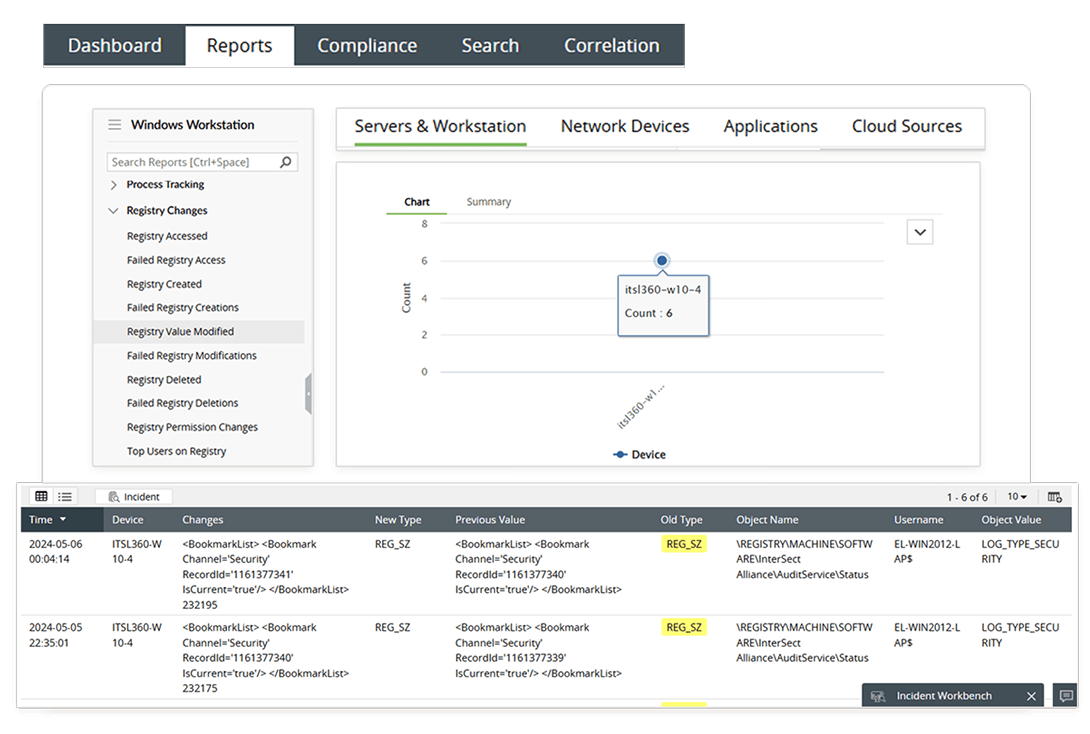
Track unauthorized changes to the Windows Registry
Problem: Attackers modify Windows Registry entries and manipulate legitimate system processes to execute malicious scripts alongside them.
Solution: Log360 tracks such unauthorized changes made to the Windows Registry, and provides out-of-the-box reports that track registry access, creation, modification, and deletion. You can also flag compromised user accounts and devices by identifying top users and devices frequently associated with registry changes. Additionally, compromised accounts can be disabled using predefined incident workflows to prevent the attack from spreading further.
Outcome: This reduces the mean time to detect (MTTD) for stealthy persistence mechanisms and enables proactive containment of fileless malware attacks.
Monitor suspicious remote executions and file downloads
Problem: Fileless malware infiltrates systems and propagates across the network by executing WMI queries that run PowerShell scripts on multiple remote devices. These scripts establish a communication channel with an external command-and-control server, from which the fileless malware is downloaded directly into a remote system’s memory.
Solution: Log360’s proactive threat hunting capabilities effectively flag suspicious file downloads and remote code executions running in memory. It also enables rapid incident response to prevent data exfiltration (which could escalate into ransomware attacks).
Outcome: Log360 helps prevent attack escalation and data loss that could disrupt business operations or lead to financial and regulatory consequences.
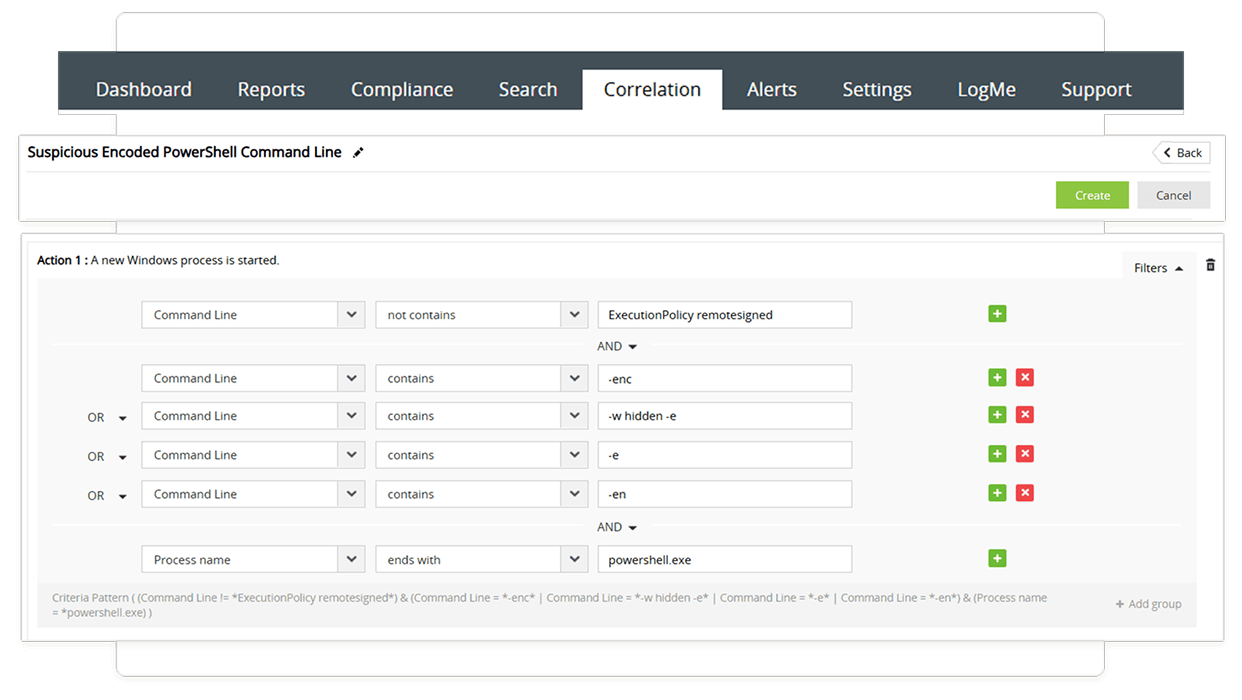
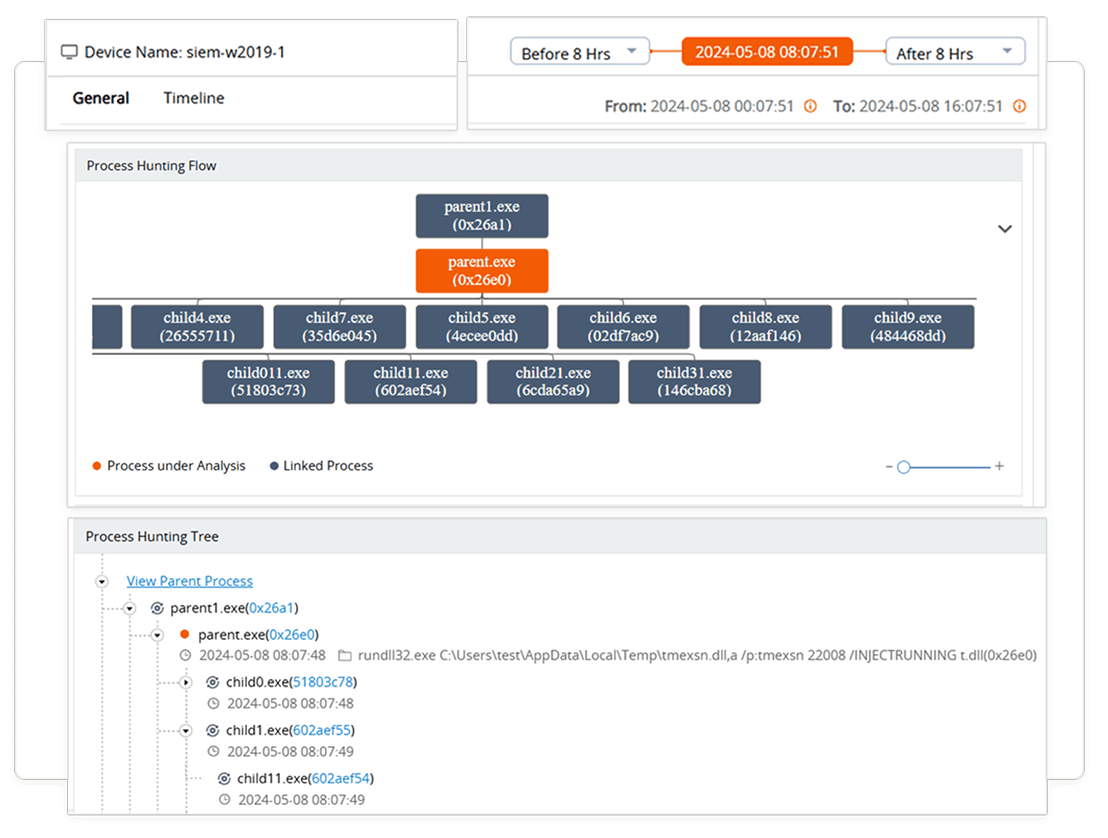
Identify suspicious process creations and associations
Problem: Fileless malware often operates alongside legitimate processes, making it difficult to detect.
Solution: Log360 provides the Incident Workbench feature, with advanced process hunting capabilities. The process flow diagram and process hunting tree help visualize the attack’s propagation, the extent of compromise, and its progression. With built-in security orchestration, automation, and response (SOAR) capabilities, you can identify suspicious process creations, correlate parent-child relationships, trace lateral movement, and terminate the process to stop the propagation of the attack.
Outcome: Log360 reduces false positives, supports root cause analysis, and enhances digital forensics, thereby improving overall SOC efficiency.