ManageEngine Log360 is a comprehensive SIEM solution that helps you streamline the log management process for your network. The solution ingests logs from diverse sources, which enables you to zero in on every potential threat from a single console.
Beyond log management, Log360 packs powerful features to help you redefine network security. It lets you add to existing logs by enriching them with data from threats intelligence feeds to stay vigil on cyberthreats.
Log360 monitors your Cisco devices to keep you informed of all the activities that go on in your environment. This guide discusses the types of logs Log360 monitors and how it gives you all the insights that you need to improve your overall security.
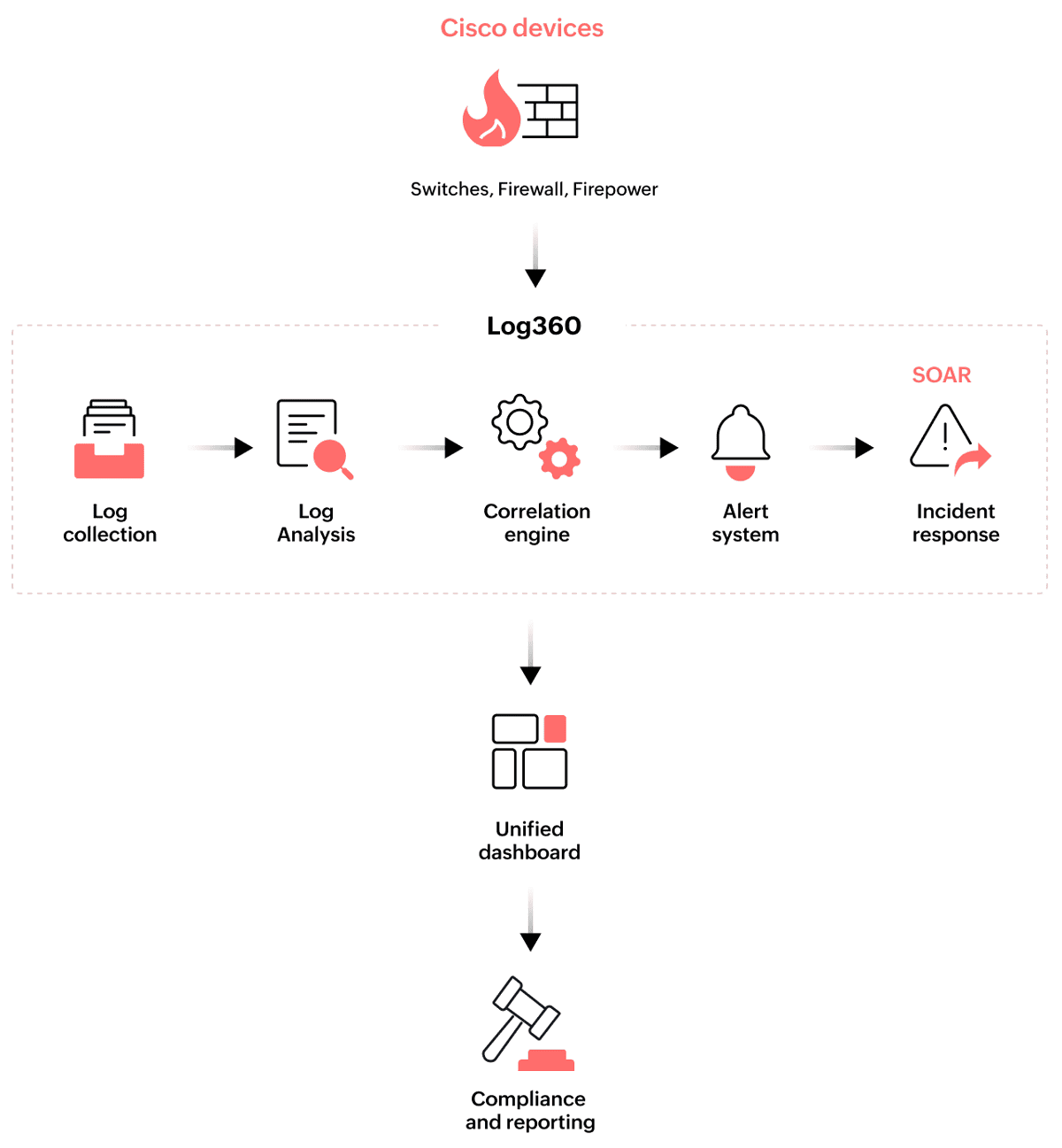
Log360 collects and analyzes logs from Cisco firewalls, switches, and firepower devices. These devices monitor network traffic, enforce security policies, and detect potential threats. Log360 consolidates these logs, providing a unified platform for comprehensive visibility and in-depth analysis of security events with alerting and incident response features.
Log360 collects logs over UDP, TCP, or TLS from Cisco devices supporting the Syslog protocol.
The solution extracts and structures critical data points such as event ID, severity, source IP, and policy names to enhance search and correlation.
To configure the Syslog service on Cisco devices, please refer to the links listed below.
Configure the syslog service on Cisco switches
Configure the syslog service on Cisco devices
Configure the syslog service on Cisco firepower devices
Log360 monitors and analyzes log data from a broad range of Cisco devices and services:
| Challenges | How Log360 helps |
|---|---|
| Centralizing logs from different sources | Log360 centralizes logs from Cisco ASA, Firepower, Meraki, and more via syslog/SNMP and normalizes them for further analysis. |
| Tracking user/admin actions | Monitors device access, configuration changes, and privileged actions to identify anomalous behavior that may indicate privilege abuse. |
| Firewall activity monitoring | Analyzes traffic patterns, ACL enforcements, and intrusion activities to identify threats to your network. |
| Audit readiness | Provides prebuilt and custom reports aligned with major regulatory frameworks. |
Go beyond siloed device monitoring:
Have questions about Log360’s integration capabilities or need technical guidance?