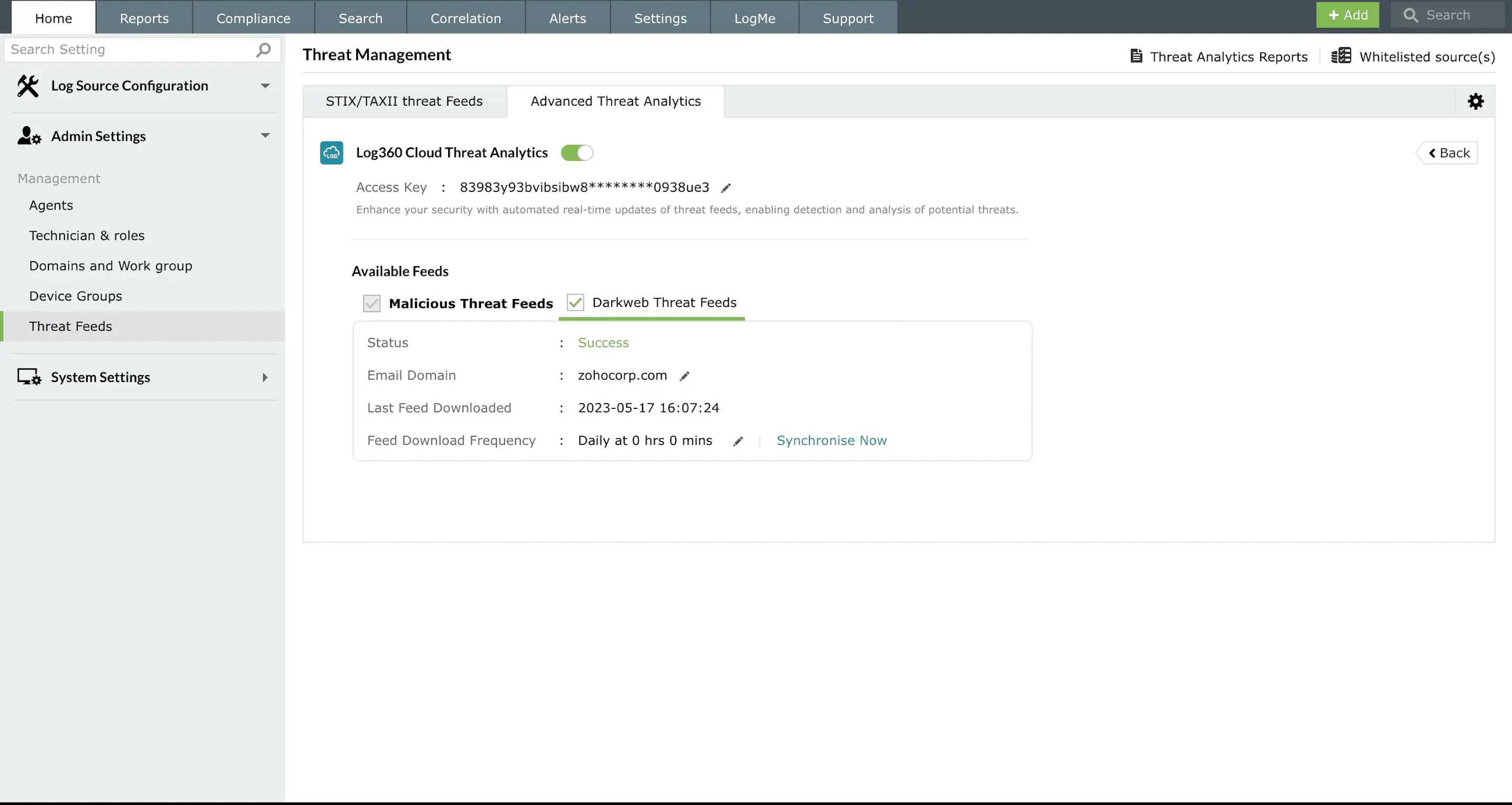
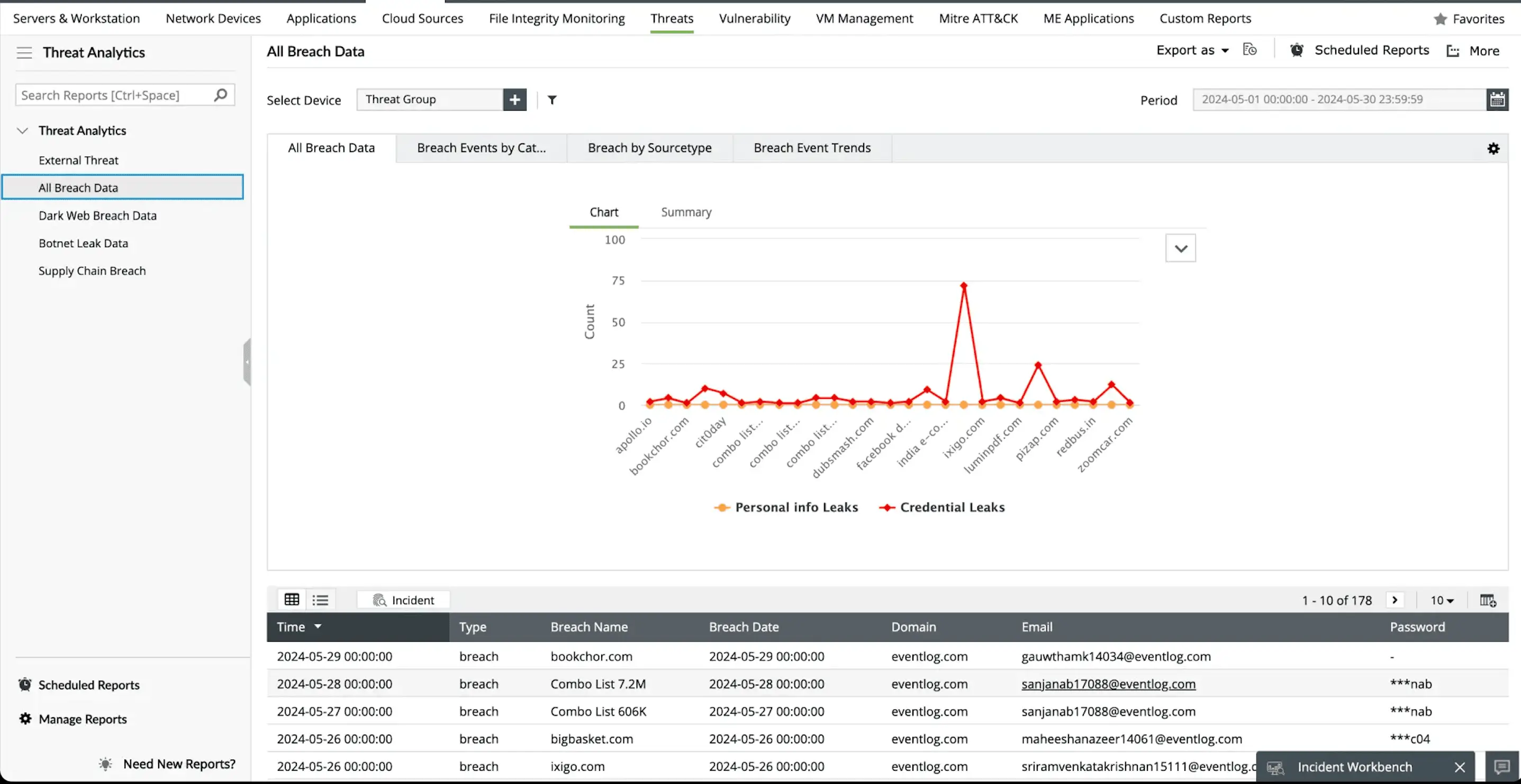
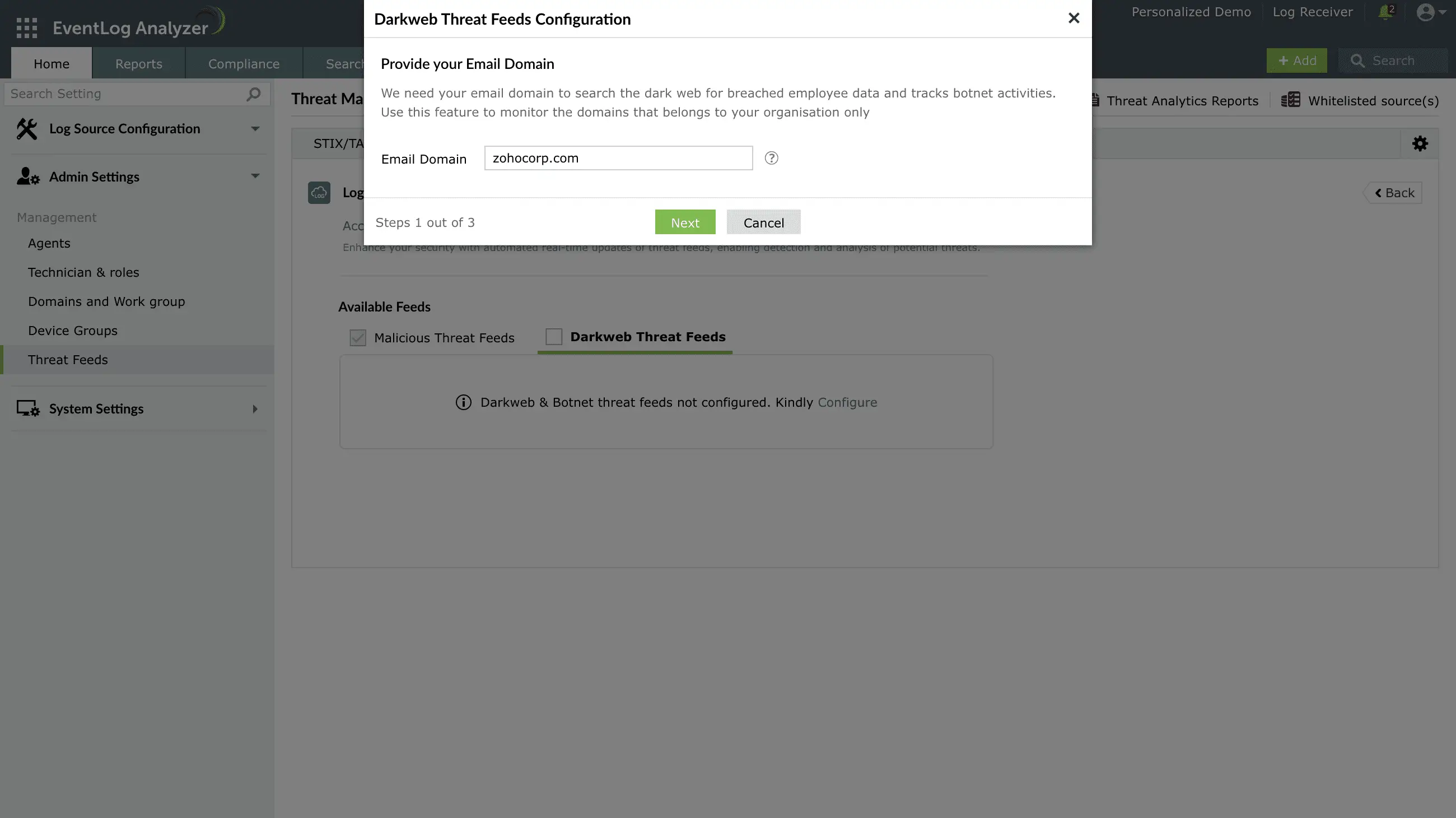
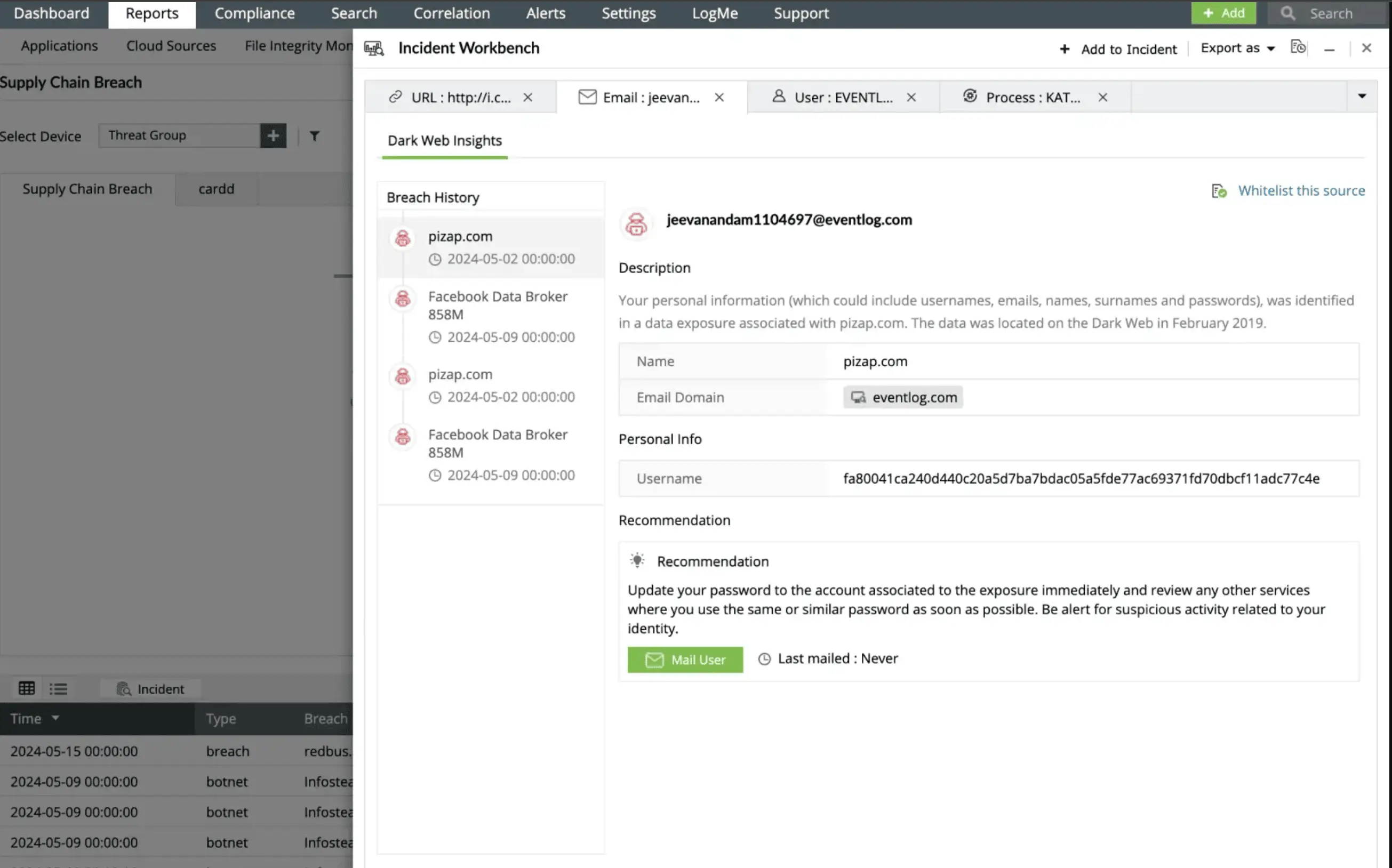
Threat intelligence is a critical cybersecurity component that provides actionable insights into potential malicious actors, campaigns, and tactics. By aggregating and analyzing threat data from multiple sources such as STIX/TAXII feeds, open-source intelligence (OSINT), and internal telemetry organizations can detect potential attacks early, improve incident response, and strengthen their overall security posture.
Threat intelligence helps enhance proactive defenses, accelerate incident response with context-rich data, support risk management and compliance efforts, It improves collaboration between security teams and stakeholders to stay ahead of threats, make informed decisions, and strengthen their overall cybersecurity posture.