Experience Log360's
3-way threat investigation workbench
Designed to achieve efficient and faster threat analysis and resolution
Managing network security for enterprises involves the cyclical process of monitoring for incidents, detection, verification of threat cases, remediation, and proactive threat hunting. Among these, proactive threat hunting and verifying threat cases are time-consuming, manual processes that require extensive investigations.
Log360's incident workbench provides an advanced analytical console that:
- Significantly diminishes the time required to compile essential information for impactful investigations.
- Improves the investigative process with ML-powered contextual data.
Explore what the feature offers:
Unified analytics of core digital artifacts
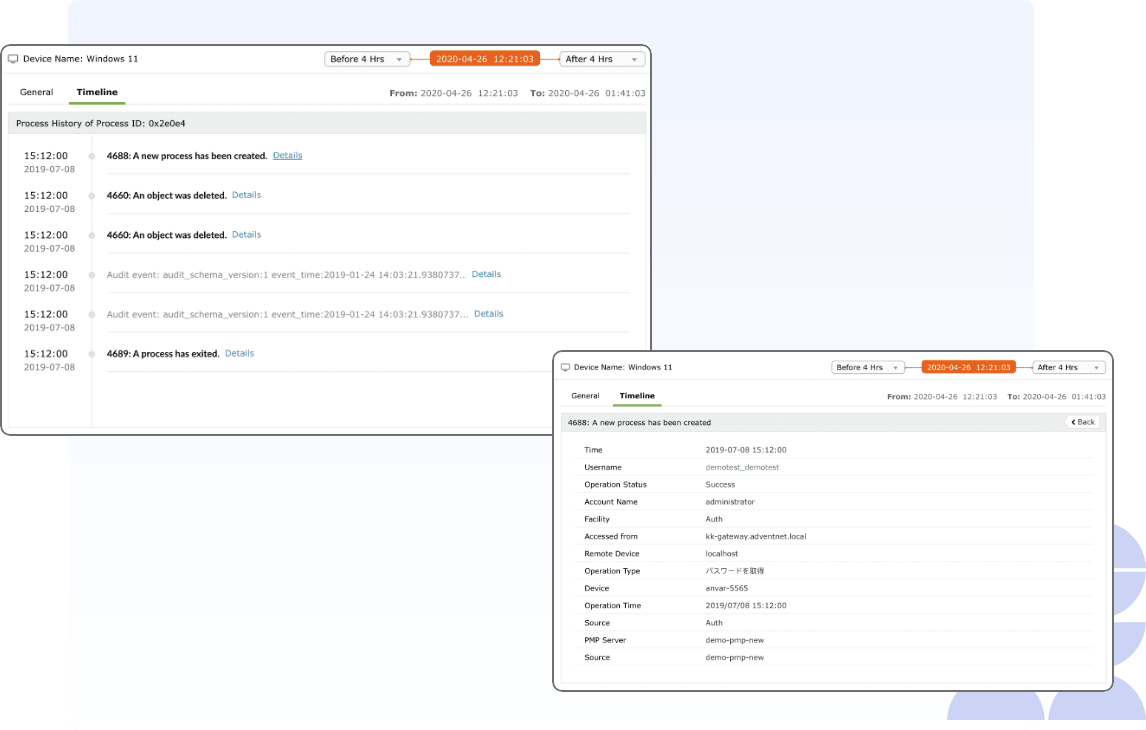
The incident workbench is the investigation component of Log360's threat detection, investigation, and response (TDIR) engine, Vigil IQ. It enables you to add, compare, and analyze core digital entities like users, devices, and processes.
- The investigation assistant: The incident workbench can be invoked from anywhere inside the SIEM console of Log360 as you traverse through different dashboards like Reports, Log Search, Compliance, Correlation, and others.
- Simplified access: It offers the flexibility of a simple point-and-probe mechanism to select any entity and delve deep into investigation with additional analytical data.
Advanced integrations
In addition to unifying analytics, the threat investigation workbench also enriches analytical data with the following integrations:
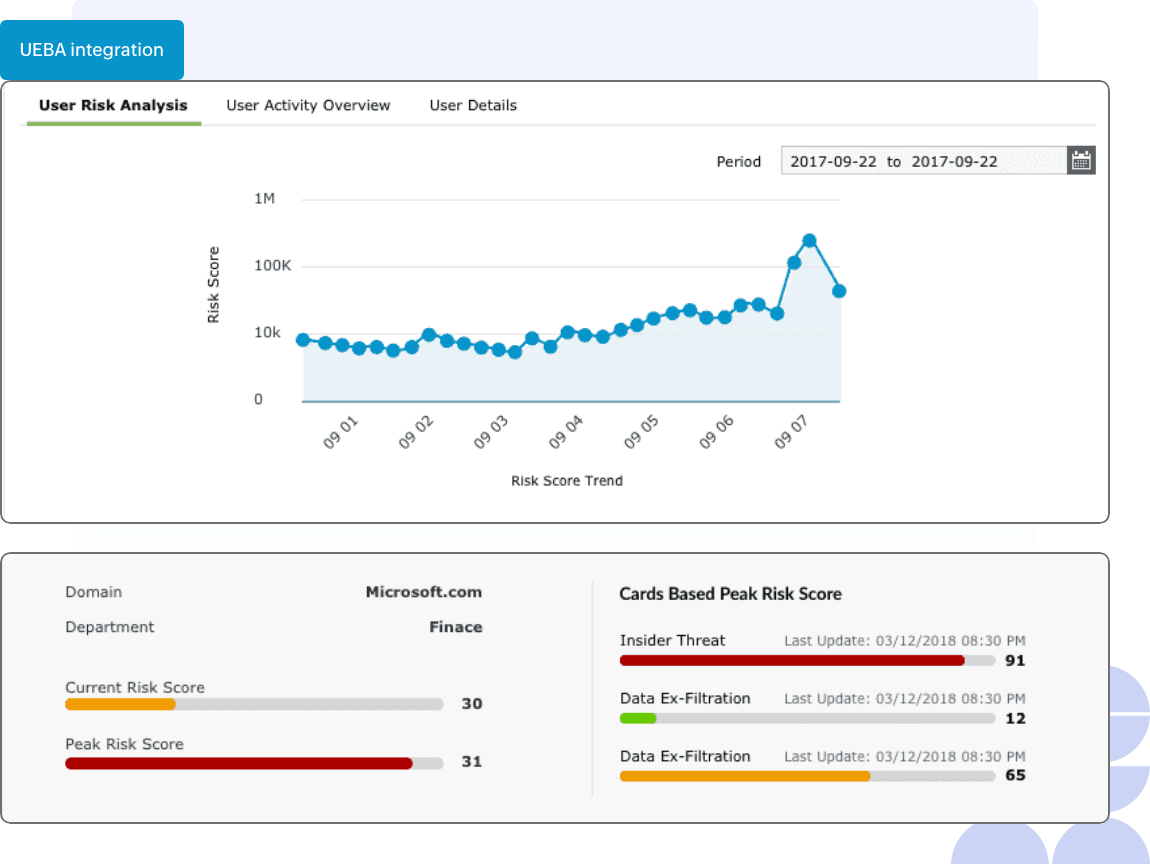
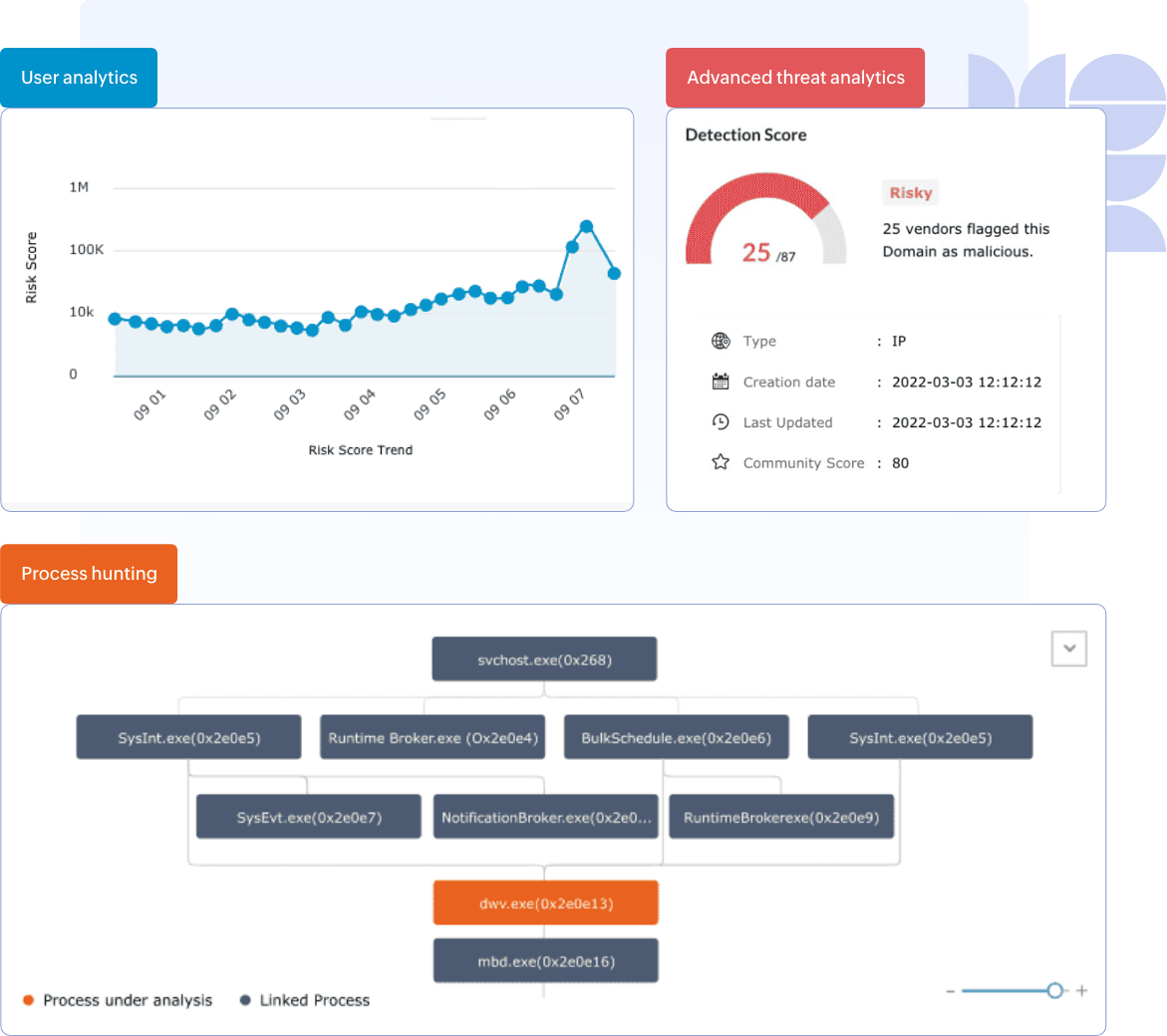
- ML-based user analytics Integration: UEBA from the Log360 suite
The incorporated UEBA data provides user activity overview for the selected period, behavioral risk analysis, and risk score trend.
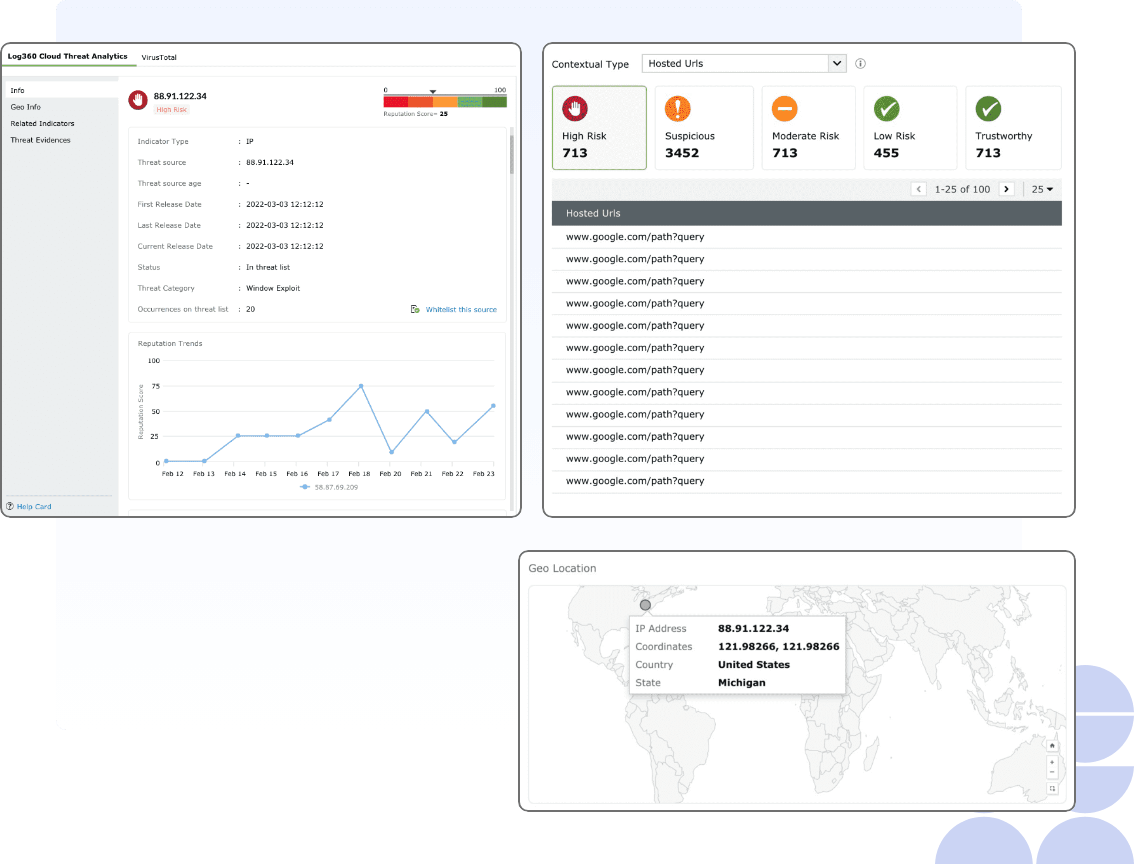
- Advanced threat intelligence Integration: VirusTotal, a third-party tool
Analyze IPs with Log360's advanced threat analytics (ATA) integrations, including VirusTotal, one of the largest live threat feeds offering domain risk scores consolidated from multiple security vendors, Whois information of the threat source, and the associated files.
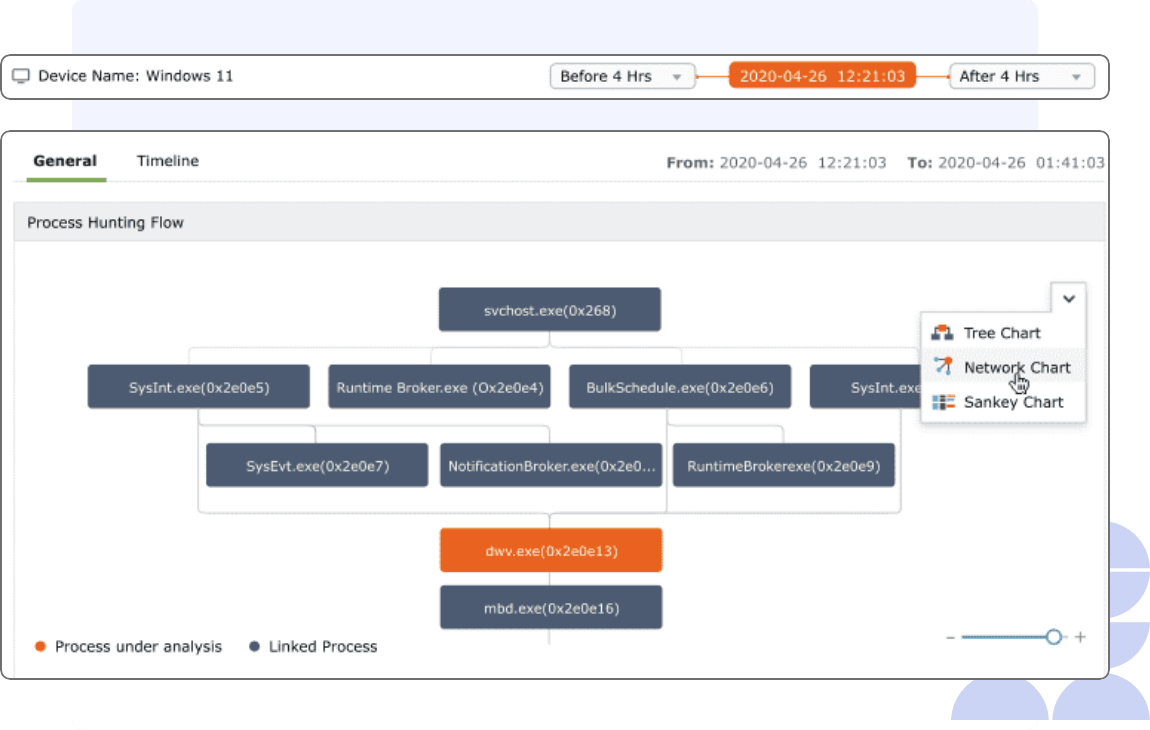
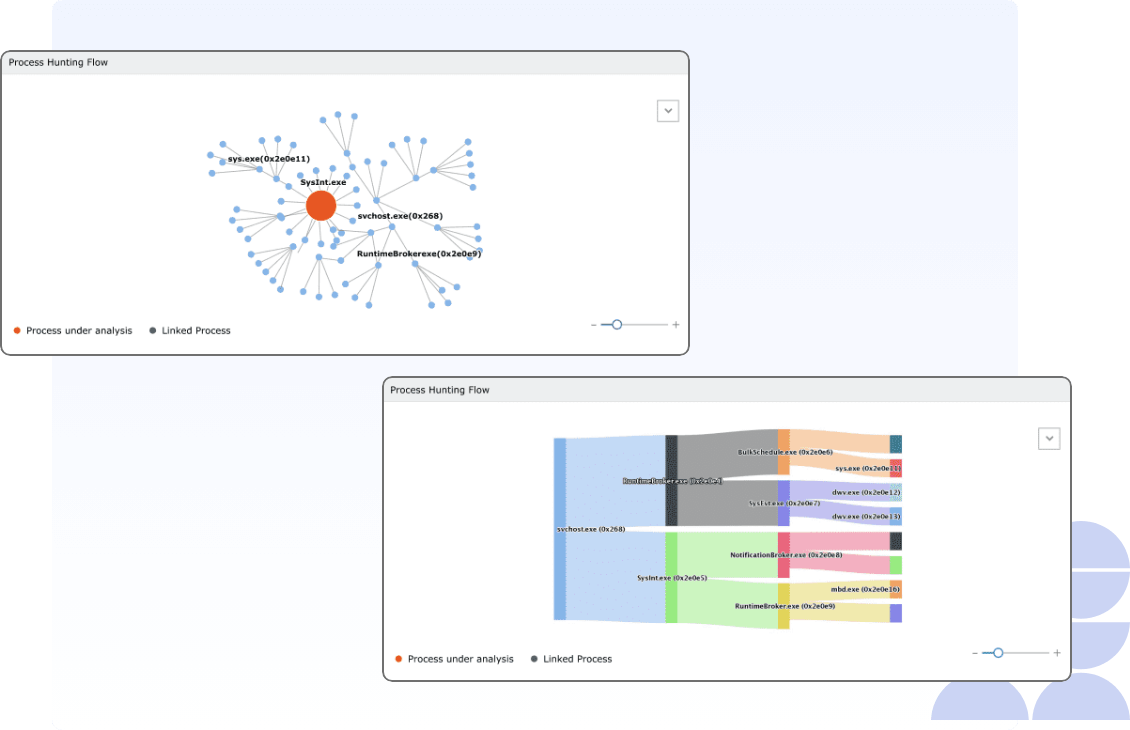
Process hunting
Process hunting, a crucial threat investigation mechanism that provides contextual information on suspicious process spawning, has often taken the back seat due to the complexities of mapping the parent-child relationships. Log360 addresses this by providing process flow visualization in the threat investigation workbench through graphical formats, such as:
- Parent-child tree.
- Process clusters.
- Process flow with Sankey charts.
Along with this, the event timeline and event details are also available in the workbench. This drastically reduces the time taken by security analysts to uncover malicious activities by probing processes.
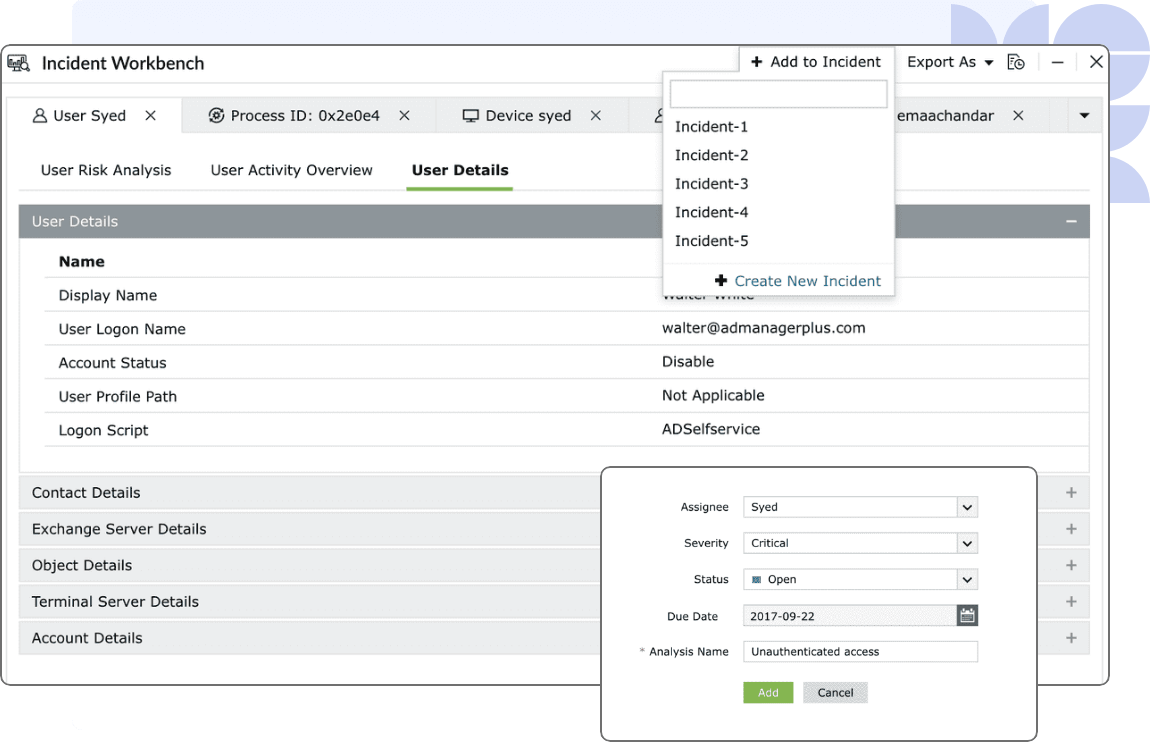
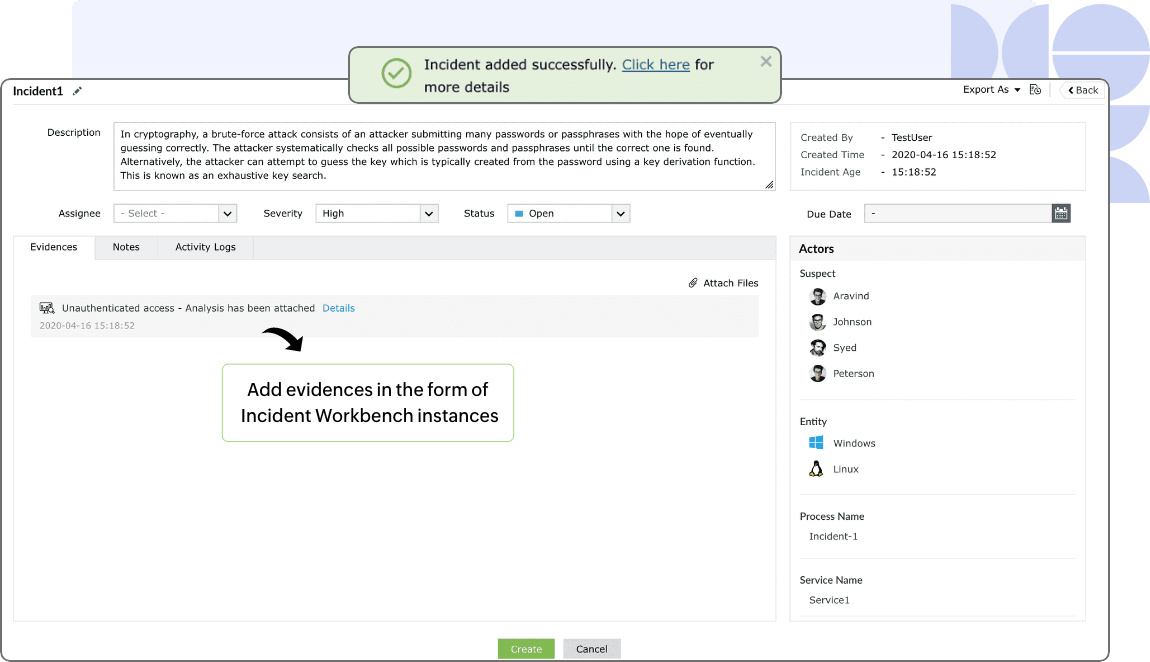
Enriched incident building
The threat investigation workbench can also be utilized as an evidence collection board by adding the instances of the workbench to the incident management console. You can add up to 20 tabs containing analytical data from different sources to the workbench and save it. Instead of populating incidents with disparate reports, a single instance of the workbench will contain the entire picture.
Why choose Log360 for threat investigation?
- Central console
- TDIR suite
- Process hunting
- SOC focused
Centralized console for data-driven investigation
Log360 is a SIEM suite that brings security analytics of enterprise networks into a single centralized console. It equips data-driven investigation by collecting, parsing, and analyzing logs from 750+ sources. This vast data is appropriately curated to offer impactful insights through multiple analytical dashboards.
Advanced features that cut down investigation time
A substantial part of conducting threat investigations involves verifying the threat cases reported by SIEM alerting modules. In Log360, alerts are meticulously adjusted using the ML-based adaptive threshold functionality, aided by Vigil IQ, to minimize the false threats that majorly consume investigation time and resources.
Process hunting suite
While the threat investigation workbench helps analyze the parent-child tree, the correlation engine has 30+ predefined rules to identify suspicious processes spawning with illegitimate parent and child processes. This makes Log360 a complete suite for process hunting.
SOC-friendly solution
With Log360, analysts have access to hundreds of predefined reports, alerts, and correlation rules for a quick start, coupled with the flexibility of customizing the solution to suit different environments. The consistent enhancements to the functionalities and UX, with features like the threat investigation workbench, makes it a SOC-friendly solution focused on addressing issues in real time.
Frequently asked questions
What is threat investigation?
Threat investigation is the systematic process of analyzing and responding to potential cybersecurity incidents within enterprise networks to identify and detect malicious activities or vulnerabilities. This process is done proactively and on a regular basis to evaluate the network security posture and also post-detection of breaches to find the root cause and attack trail.
What are the roadblocks in active threat investigation?
Here are some of the hurdles faced by organizations in threat investigation:
- Expanded attack surface with huge volumes of log data making it difficult to streamline information.
- Complex security tools that pose difficulties in terms of configuration, overload of features and integrations, and lack of intuitive UX.
- Huge time invested in validating alerts, which mostly consist of false positives.
- Lack of skill and awareness among analysts.
- Investing in too many security tools while under-utilizing their capabilities.
How do SIEM solutions help with threat investigations?
SIEM solutions like Log360 offer the following features and benefits to help investigate threats:
- Data aggregation achieved by centralized log collection through agents and agentless methods using APIs.
- Analytical dashboards with reports on network events.
- Anomaly detection through predefined alerts, correlation rules, and UEBA.
- Integrated threat intelligence feeds.
- Forensic analysis through log search capabilities.
- An incident management console to build, validate, and respond to incidents.
Along with these, Log360's threat investigation workbench takes it up a notch with a comprehensive analytical console that allows users to probe data flexibly and arrive at swift conclusions.
Try Log360 for free
Experience the extensive capabilities of unified SIEM utilizing Log360
Download nowWalkthrough with experts
Schedule a one-on-one call with our solution experts to explore Log360
Schedule demo