Anomaly detection or outlier detection in cyber security is the process of observing and analyzing the actions of all the users and entities inside a network or system. The objective is to detect unusual or anomalous activities that could flag potential security threats or irregularities. It is done by analyzing data over a period of time and identifying any events or data points that deviate from what is usual or expected.
What are anomalies?
In short, an anomaly is a deviation from the established normal pattern. What is normal needs to be established to identify the abnormal. Normal is a subjective perceptive and differs from user to user, department to department, and organization to organization. Therefore, contextual information is also crucial in identifying anomalies.
Types of anomalies
Point anomalies (global outliers)
This is the simplest and most widely observed anomaly category. If a single object stands out completely from the rest of the observed objects, then it is a point anomaly.
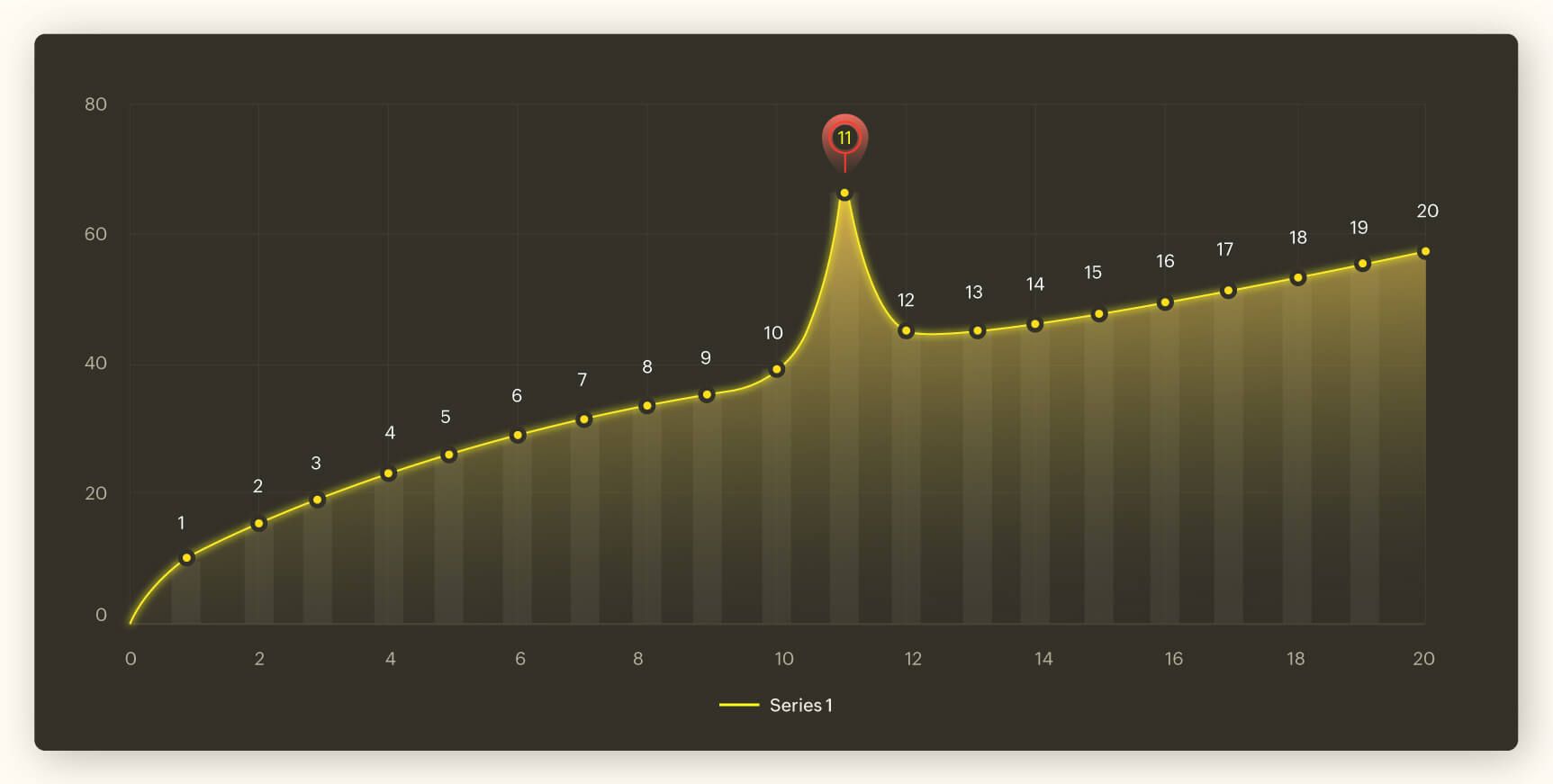
In the graph above, Point 11 is an anomaly. It can be observed that there is a gradual and steady increase in the data set, but at point 11, the increase is abnormal. The data dips down to the regular range from point 12.
Example of a point anomaly in cybersecurity: A single server crashing at a particular time could be due to a multitude of reasons. But if numerous servers in an organization crash within a short span of time, that is definitely an anomaly and could be a security threat. In this case, the IT security team should be cautious and be on red alert.
Contextual anomalies (conditional outliers)
These kinds of anomalies occur at a particular time or during specific circumstances.
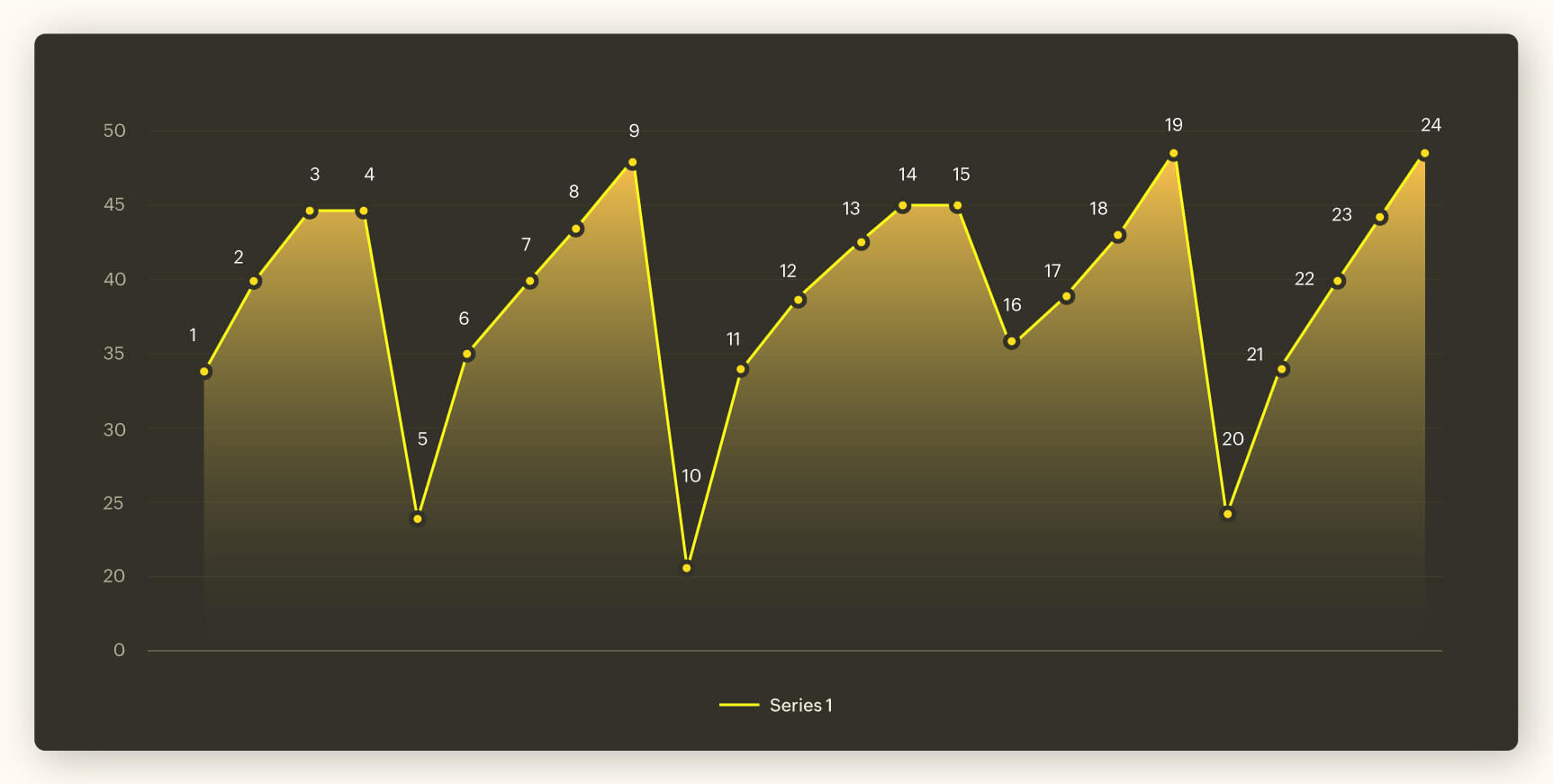
In the graph above, a dip normally happens at an interval of 5. Let us assume there is a legitimate cause or reason behind this dip. But if we take a closer look at the graph, there is no dip at Point 15, as it must be. This is a contextual anomaly. You can identify an anomaly of this kind only if you know the context that the graph is set upon.
Example of a contextual anomaly in cybersecurity: Your human resources manager logs in everyday around 10 am and logs out before 7 pm. On a random day, you notice her account has been logged in at 3am. This could be the result of a mistake or an emergency. But a security analyst needs to investigate this anomaly, particularly if the user is already on a watchlist. If not for her previous log in and log out information, this particular incident will not sound an alarm. A contextual anomaly is anomalous in a specific context but not outside of this context.
Collective anomalies:
A collective anomaly occurs when a subset of data points significantly deviates from the rest of the data, but the individual data points on their own are not anomalous.
In the graph below, we see the number of active privileged users on each server during a typical working day. Server 4 seems to have an abnormal number of privileged users. This would not have been considered abnormal if we did not have the data from the other three servers. This is an anomalous activity can be called a collective anomaly.
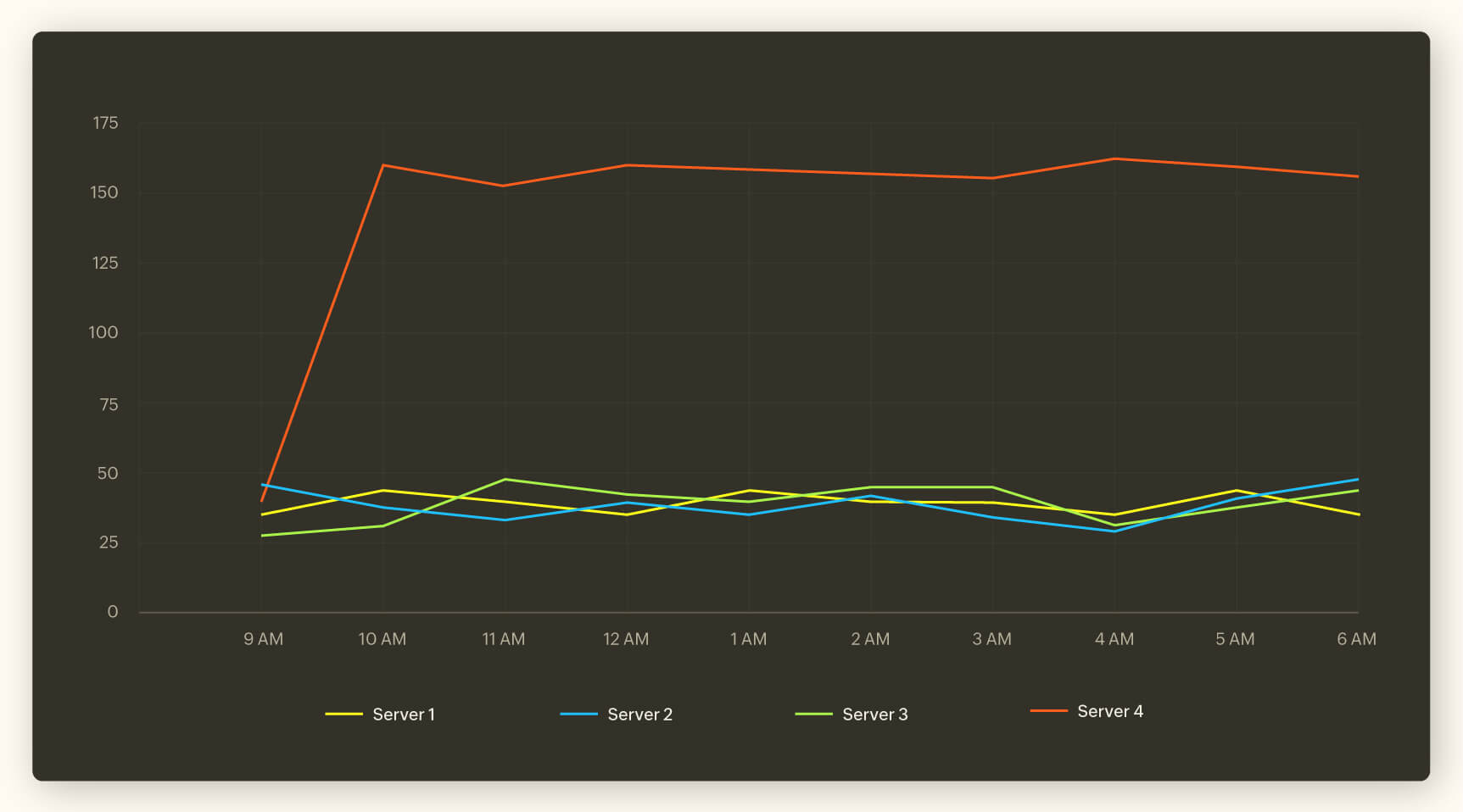
Example of a collective anomaly in cybersecurity: Let us assume that there is an increase in the number of privileged users accesses for a particular server. An IT security analyst might not have noticed the unusual activity if not for the entirety of the data from other three servers. Collecting and comparing data is a major part of an analyst's role in keeping the network secure as it helps detect anomalies at the right time.
Anomaly detection use cases
Anomaly detection in time series data: A series of data collected and collated over a particular period of time could indicate normal and abnormal behavior. For example, the check-in data of employees collected during regular intervals of time can be considered time series data, and it can be used to detect abnormal check-in times.
Anomaly detection in FIM: In this scenario, anomaly detection is used to identify unauthorized changes to critical files and system configurations. By establishing a baseline of file attributes such as size, hash values, and modification timestamp, security systems can monitor for unexpected changes or tampering. For instance, if an attacker alters system files or installs malicious software, these changes would deviate from the established baseline. Detecting such anomalies can help identify potential breaches, malware infections, or unauthorized changes to system configurations.
Anomaly detection and UEBA
User and Entity Behavior Analytics is closely connected to anomaly detection, but it extends beyond traditional anomaly detection techniques by focusing specifically on the behaviors of users and entities within a system. Leveraging machine learning algorithms, UEBA utilizes historical data to establish a standard pattern of behavior for each user and entity. It continuously monitors these entities in real-time to assess whether their current behavior aligns with this established baseline. Any departure from this norm is flagged as an anomaly, with the severity of deviation contributing to a risk score. This approach has revolutionized cybersecurity by enhancing the detection of potential threats and vulnerabilities.
ManageEngine Log360 is a unified SIEM solution with integrated UEBA, DLP, and CASB capabilities that can help organizations thwart various cyberattacks. The UEBA module in ManageEngine's Log360 comes equipped with both pre-built and customized anomaly models. To know more about how anomaly modeling works in UEBA, watch this video.



