Related content
What is threat intelligence?
Threat intelligence refers to the collection, analysis, and application of contextual data related to known or emerging cyberthreats. It includes insights into IoCs, malicious IPs, file hashes, domain names, and TTPs used by threat actors, and the overall threat landscape.
Unlike raw log data, which can be noisy and overwhelming, threat intelligence is enriched and contextualized, allowing security teams to make informed decisions and respond to threats effectively. Organizations can obtain threat intelligence from from a variety of sources, including open-source intelligence (OSINT), commercial threat intelligence platforms, industry-specific Information sharing and analysis centers (ISACs), and internal telemetry. This intelligence is delivered in multiple formats such as STIX/TAXII, JSON, CSV, and proprietary schemas and when integrated into security operations, provides the context needed to correlate events, detect anomalies, and trace the activities of threat actors across the network.
Importance of threat intelligence for proactive security
Traditional security tools often fall short when it comes to identifying sophisticated, targeted threats. Threat intelligence bridges this gap by enabling proactive threat detection, investigation, and response. It empowers organizations to:
- Identify threats early in the attack life cycle by recognizing known attack patterns and suspicious activities.
- Validate alerts with context to reduce noise and false positives, ensuring that security teams focus on high-priority incidents.
- Understand attacker behavior by mapping events to MITRE ATT&CK techniques, enabling a deeper understanding of threat actor motives and methodologies.
- Accelerate incident response with real-time threat context that helps in faster triage, investigation, and containment.
- Strengthen overall security posture by informing policies, access controls, and threat mitigation strategies with real-world threat insights.
With the right threat intelligence in place, SOCs can shift from reactive incident handling to proactive threat hunting and prevention.
Detect advanced threats, correlate global threat feeds, and respond faster with contextual intelligence.
Types of threat intelligence
Threat intelligence is categorized into three major types, each serving a unique purpose across different layers of an organization:
1. Strategic threat intelligence
Strategic threat intelligence is high-level, non-technical information focused on long-term trends, and the implications of cyberthreats. It helps executives and decision-makers make informed decisions on budget allocation, risk management, and security policies. Strategic threat intelligence typically includes trends in attacker behavior, motivations, and geopolitical factors. For instance, reports highlighting an increase in state-sponsored attacks on the energy sector due to geopolitical conflicts.
Use case: Guides CISOs and leadership teams in setting long-term security priorities and aligning cybersecurity with business strategy.
How Log360 supports: Through integrations with structured feeds like STIX/TAXII, Log360 helps you understand broader trends and actor profiles, enabling you to anticipate future threats and align your security strategy accordingly.
2. Operational threat intelligence
Operational threat intelligence provides details about specific campaigns or active attacks. It includes information such as attack vectors, targeted assets, tools used by attackers, and methods of exploitation. This intelligence helps incident response teams understand ongoing threats and prepare tailored defense mechanisms. For instance, intelligence showing that a ransomware group is distributing phishing emails with weaponized Excel attachments to target the banking industry.
Use case: Enables incident response teams to anticipate attacker methods and adjust detection and response playbooks accordingly.
How Log360 supports: By mapping events to frameworks such as MITRE ATT&CK, Log360 contextualizes the who and how behind an alert. SOC teams gain actionable insights into attacker TTPs, enabling faster and more effective incident response.
3. Tactical threat intelligence
Tactical threat intelligence is technical and detailed, aimed at detecting and blocking specific threats. It includes data such as IP addresses, malicious URLs, file hashes, and malware signatures. This type of intelligence is often integrated into security tools such as SIEMs and intrusion detection systems for automated detection and blocking. For instance, a real-time feed of IP addresses linked to a botnet launching DDoS attacks.
Use case: Enables SOC teams to quickly update firewalls, SIEMs, and intrusion detection systems to block threats before they infiltrate the network.
How Log360 supports: Log360 consumes real-time feeds from sources such as Webroot, AlienVault OTX, and VirusTotal to collect IoCs. By correlating this data with internal security events, Log360 enriches alerts, prioritizes risks, and helps SOC teams quickly block or mitigate active threats.
4. Technical threat intelligence
Technical threat intelligence goes deeper than tactical feeds. It uncovers the inner workings of attacks by analyzing malware code, exploit kits, C2 infrastructure, and adversary toolkits. This intelligence is highly detailed and often produced by security researchers, reverse engineers, or advanced forensic teams. For instance, a reverse-engineering report detailing how a new strain of ransomware encrypts files using an unpatched vulnerability in Windows services.
Use case: Helps security vendors and advanced defenders craft better detection rules, develop patches, and build long-term resilience against evolving attack techniques. Each of these types plays a crucial role in building a layered and proactive defense posture.
Threat intelligence life cycle
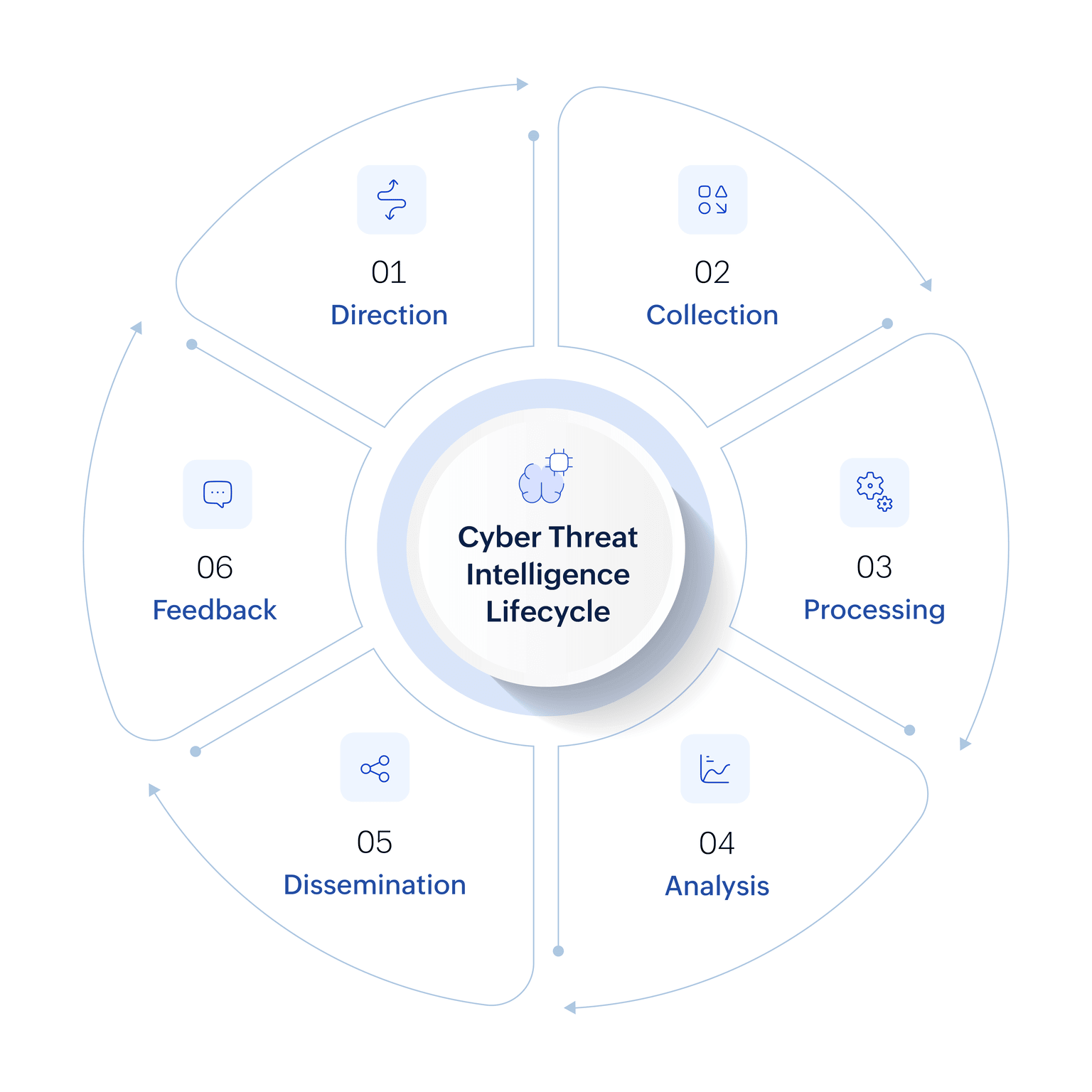
The threat intelligence life cycle is a structured process used to convert raw threat data into actionable intelligence. It comprises six key stages:
1. Planning and direction
Organizations determine what questions they want the intelligence to answer, such as which assets are most at risk, who their likely threat actors are, or what specific vulnerabilities need monitoring. Direction ensures that the threat intelligence efforts align with the organization’s security goals, compliance needs, and risk profile.
2. Data collection
In this phase, threat data is gathered from a wide range of sources, including internal logs, vulnerability scanners, threat feeds, dark web sources, and OSINT. Organizations often leverage STIX/TAXII-compatible threat feeds, OSINT, commercial threat intelligence platforms, industry-specific Information sharing and analysis centers ISACs, and internal telemetry to gain access to enriched data. This step is crucial for building a comprehensive dataset that reflects the evolving threat landscape.
3. Processing
Once the raw data is collected, it must be converted into a usable format. Processing involves filtering out irrelevant or redundant data, normalizing various data types, and organizing the information for further analysis. This step ensures that security analysts are not overwhelmed by data volume and can focus on what truly matters.
4. Analysis
During analysis, security analysts examine the processed data to identify patterns, malicious indicators, and correlations between different events. The goal is to generate actionable insights that answer the original intelligence questions. This phase may involve techniques such as behavior modeling, threat actor profiling, and correlation with known attack tactics from frameworks like MITRE ATT&CK. Attribution, while valuable, remains one of the most challenging aspects of analysis due to techniques like false flags and infrastructure reuse by different threat actors. The output of this phase includes threat assessments, risk scores, and recommendations for action.
5. Dissemination
The insights generated from the analysis phase must be delivered to the right stakeholders in an understandable and actionable format. This could include dashboards for SOC teams, reports for management, or alerts for incident response teams. Timely dissemination ensures that appropriate defensive measures can be taken before threats escalate.
6. Feedback
Feedback closes the loop of the life cycle by assessing the usefulness of the delivered intelligence. Stakeholders provide input on whether the intelligence was relevant, timely, and actionable. Key metrics for evaluation include detection rate improvements, mean time to detect (MTTD), mean time to respond (MTTR), and false positive reduction rates. Based on this feedback, the direction phase is refined, ensuring continuous improvement and adaptation to new threats and organizational priorities.
Common implementation challenges
While threat intelligence offers immense value, organizations often face roadblocks when trying to adopt and operationalize it effectively:
- Data overload and noise: Security teams often struggle to process the sheer volume of threat data, leading to alert fatigue and missed critical signals.
- Lack of context: Raw feeds provide indicators, but without enrichment or correlation, teams find it hard to understand the relevance of a threat to their environment.
- Integration complexity: Different feeds use varying formats (STIX/TAXII, JSON, CSV, proprietary), making it challenging to normalize and integrate them into SIEMs or SOC workflows.
- Skill gaps: Analyzing and interpreting threat intelligence requires expertise in malware analysis, reverse engineering, and adversary TTPs, skills many organizations lack.
- Delayed response: Without real-time integration, threat intelligence often arrives too late, limiting its effectiveness in preventing attacks.
- High cost of commercial feeds: Subscription-based feeds and platforms can be expensive, making it difficult for mid-sized organizations to access comprehensive intelligence.
These challenges highlight why organizations need a solution that not only aggregates threat intelligence but also enriches, correlates, and rationalizes it seamlessly within their security operations.
How Log360 leverages threat intelligence for proactive defense
ManageEngine Log360, a unified SIEM solution, transforms raw security data into actionable intelligence. By integrating and contextualizing threat data, it empowers organizations to detect, analyze, and respond to cyberthreats with precision. Here’s how Log360 helps enhance your threat detection and response strategy:
Real-time threat feed integration:
Log360 ingests threat intelligence from multiple trusted sources to ensure you have a comprehensive view of the global threat landscape.
Key integrations include:
- Webroot: Provides real-time data on malware, phishing sites, and suspicious URLs.
- STIX/TAXII: Enables the automated ingestion of standardized, structured threat intelligence from global feeds.
- VirusTotal: Aggregates scan results to identify known malicious files, domains, and URLs.
- AlienVault OTX: Leverages community-driven IoCs from security experts worldwide.
- Constella: Delivers intelligence from dark web monitoring campaigns to detect advanced threats early.
These integrations allow SOC teams to enrich alerts, prioritize risks, and respond faster to high-impact threats, making Log360 a threat intelligence–driven SIEM that empowers proactive defense.
Enriching security data for true context:
Threat intelligence is most powerful when it’s contextualized and easy to consume. Log360 automatically correlates the global threat feeds with internal security events and correlated alerts, turning isolated data points into a clear, connected narrative.
Its powerful rule library, mapped to the MITRE ATT&CK® framework, cross-references your system data (like logins or file access) against known IoCs—such as malicious IPs, domains, or file hashes. This process enriches your internal data, validates alerts, eliminates false positives, and provides a single pane of glass to trace suspicious activity back to known threat campaigns.
AI-driven investigation and response with Zia Insights
Log360’s AI-powered Zia Insights enhances threat intelligence by automatically summarizing logs and alerts, categorizing security events, attributing threat actors to entities, and mapping attack patterns to MITRE ATT&CK tactics. It also provides actionable insights, enabling security teams to understand threats quickly, prioritize responses effectively, and accelerate incident resolution.
Discover the threat feeds Log360 supports
Log360 integrates with leading threat intelligence providers including Constella Intelligence, Webroot, STIX/TAXII, AlienVault, Threat Fox, Barracuda, Symantec, and Trend Micro. By enriching raw feeds with contextual insights, Log360 transforms them into intelligence that empowers faster detection, sharper investigations, and proactive threat hunting.
FAQs
What is cyberthreat intelligence?
Cyberthreat intelligence (CTI) is evidence-based knowledge about existing or emerging threats. This data including Indicators of Compromise (IoCs), attacker tactics, and malicious domains is collected, processed, and analyzed to provide the context needed to fight cyberattacks.
Cyberthreat intelligence enhances an organization's security posture by:
- Identifying threats early through Indicators of compromise and TTPs.
- Reducing false positives through contextual analysis and behavior profiling.
- Enabling faster incident response by mapping threats to frameworks like MITRE ATT&CK.
- Guiding investments in defense tools, threat detection capabilities, and employee training.
When integrated with a SIEM solution like Log360, CTI empowers security teams with real-time threat visibility, automated threat correlation, alert prioritization, and actionable response workflows.
How does threat intelligence help combat common cyberthreats?
Cyberthreats are malicious acts that attempt to compromise digital systems and data. These threats evolve constantly in complexity and scale. Some of the most common and persistent cyberthreats include:
- Malware: Software designed to disrupt, damage, or gain unauthorized access to systems. This includes trojans, worms, spyware, and viruses.
- Ransomware: A form of malware that encrypts data and demands ransom for decryption. Notable examples include WannaCry, Ryuk, and LockBit.
- Phishing and spear phishing: Deceptive emails or messages crafted to trick users into sharing credentials or installing malware.
- Denial of service (DoS) and Distributed denial of service (DDoS): Attacks that overwhelm a system or network, making it unavailable to legitimate users.
- Credential stuffing: Using stolen username-password pairs from previous breaches to gain unauthorized access.
- Zero-day exploits: Attacks targeting unpatched software vulnerabilities before developers release a fix.
- Advanced persistent threats (APTs): Long-term targeted attacks carried out by highly skilled threat actors, often state-sponsored.
Why is threat intelligence important?
Threat intelligence is essential because it empowers organizations to understand and anticipate cyberthreats before they turn to attacks. According to a 2025 Gartner report, organizations utilizing real-time threat intelligence reduce the average detection time by 45%. It enables faster incident response, reduces false positives, and strengthens threat-hunting capabilities. By understanding the latest attacker techniques and mapping them to internal risks, organizations can fine-tune their defenses, protect critical assets, and reduce the impact of security breaches. For a business, this proactive stance delivers tangible results:
- Reduced business risk: By identifying and stopping threats faster, you minimize the potential financial and reputational damage of a breach.
- Improved SOC efficiency: Context-rich alerts and fewer false positives allow your security analysts to investigate and resolve real threats more quickly.
- Informed security strategy: Understanding which threat actors and TTPs are targeting your industry helps you make smarter investments in security controls and training.
Ready to strengthen your cybersecurity posture with advanced threat intelligence capabilities of Log360?
- What is threat intelligence?
- Importance of threat intelligence for proactive security
- Types of threat intelligence
- Threat intelligence life cycle
- How Log360 leverages threat intelligence



