Windows files are an integral part of the Windows file system and are crucial for the streamlined performance of Windows devices. These files are the prime targets for cyberthreat actors aiming to disrupt a system and its network. Therefore, it is imperative to secure the Windows file system and monitor critical Windows files.
Know your Windows files
Here is a list of critical Windows files and folders that you should monitor
| File/Folder | Location | Description |
|---|---|---|
| System32 | C:/Windows/System32/ | This folder contains essential executable files, dynamic link libraries (DLLs), and configuration files required for the proper functioning of the Windows operating system and its applications. |
| Windows Registry | C:/Windows/System32/Config | The Windows Registry is a critical database used by the operating system to store configuration settings for hardware and software, system policies, user preferences, security settings, and file associations. |
| Event Logs | C:/Windows/System32/winevt/Logs/ | These files contain information on various system activities, such as logons, log offs, software installations, directory and file changes, and more. They are crucial for security monitoring and troubleshooting on Windows systems. |
| DLLs | C:/Windows/winsxs/ | These are shared files that contain code, data, and resources required for multiple Windows programs to run simultaneously. They are essential for conserving system memory and improving system performance. |
| SysWOW64 | C:/Windows/SysWOW64/ | These files are essential for 64-bit Windows systems to maintain compatibility with legacy 32-bit software. This folder contains 32-bit versions of system files required to run 32-bit software on a 64-bit Windows system. |
| Program Files | C:/Program Files/ | This folder contains the installation files and configuration details of external applications installed on a Windows system. |
| Volume Shadow Copies | C:/System Volume Information | These files are backups of critical system data, including system files, program files, and application files. They also contain backup of the metadata required for accessing and managing files within the system. |
Secure your Windows file system with Log360
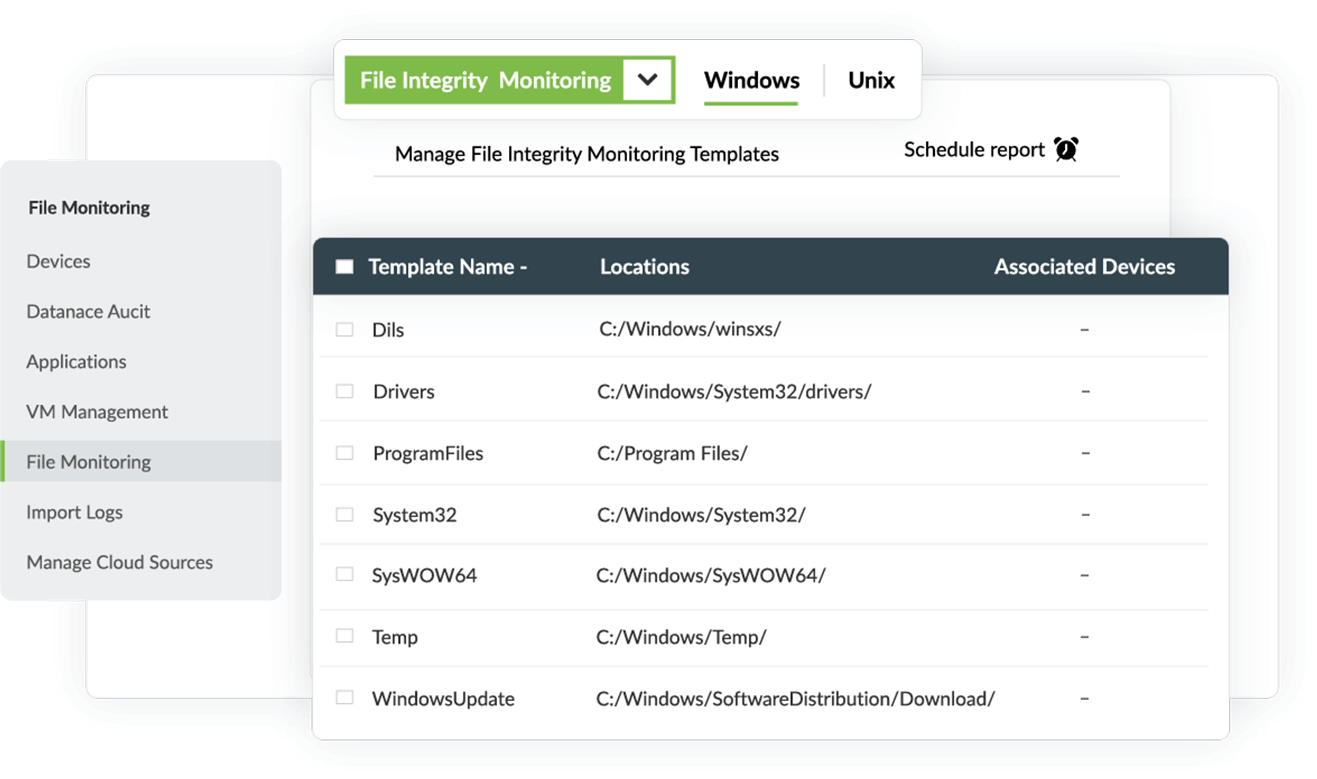
Monitor critical file locations in Windows systems
Log360 Windows file monitoring offers predefined file monitoring templates for critical file locations. These templates can be enabled while configuring file monitoring on Windows systems to detect suspicious file changes in the respective folders. The predefined templates include System32, Program Files, DLLs, and other important folders that are prone to data tampering attempts. Additionally, custom file monitoring templates can be created for other critical file locations in the system.
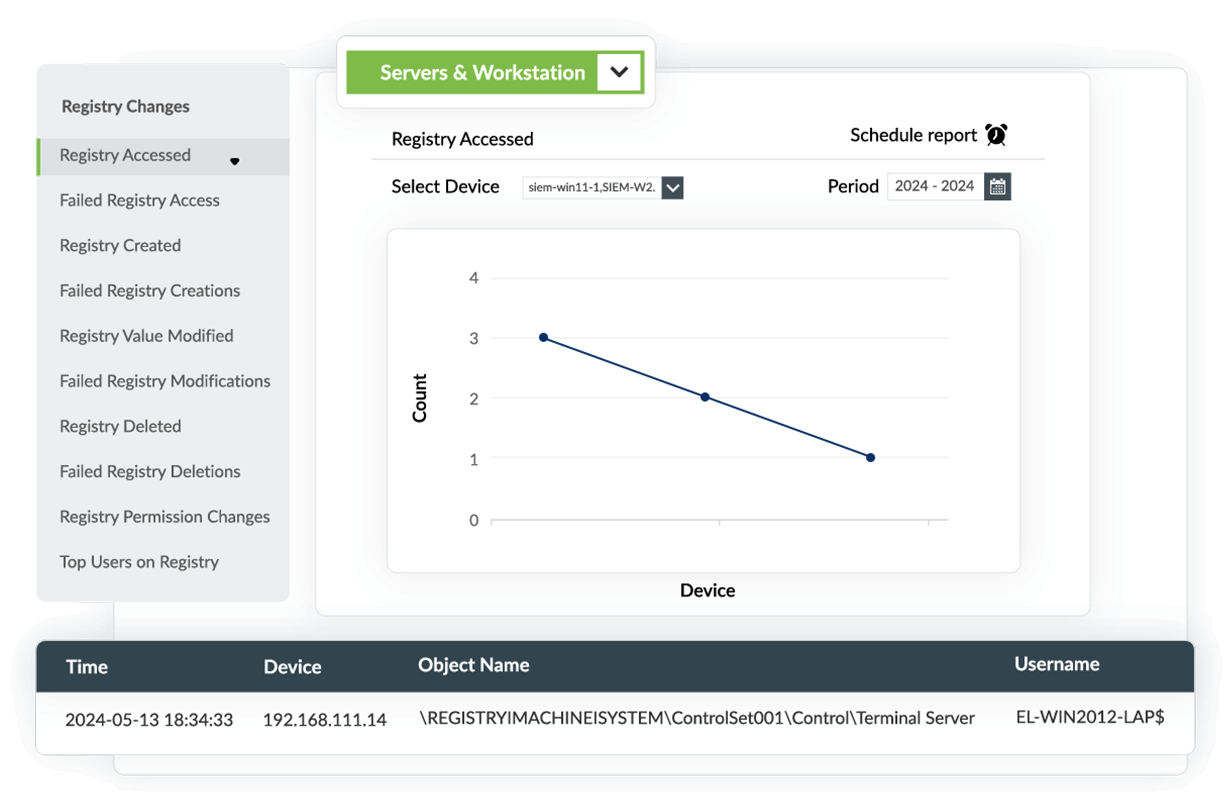
Track unauthorized changes to Windows files and folders
Log360's advanced file monitoring capabilities help track unauthorized changes to Windows files in real-time. Files such as Program Files, Registry Files, Volume Shadow Copies, and Event Logs are highly susceptible to security risks, as tampering with these files allows attackers to evade detection. Log360 offers out-of-the-box reports and alerts for changes to Windows Registry, Program Inventory, System Volume Information, and Event Logs, enabling real-time detection of unauthorized file changes.
Detect suspicious Windows file activities in real time
Log360 provides comprehensive security for Windows files through predefined correlation rules and alert profiles that detect suspicious file activities. The file monitoring feature in Log360 leverages a built-in correlation engine and smart threshold capabilities to identify and map suspicious file activities that, when viewed in isolation, might be overlooked. This approach ensures Log360 delivers complete security visibility while minimizing false positives that could hinder effective threat detection.
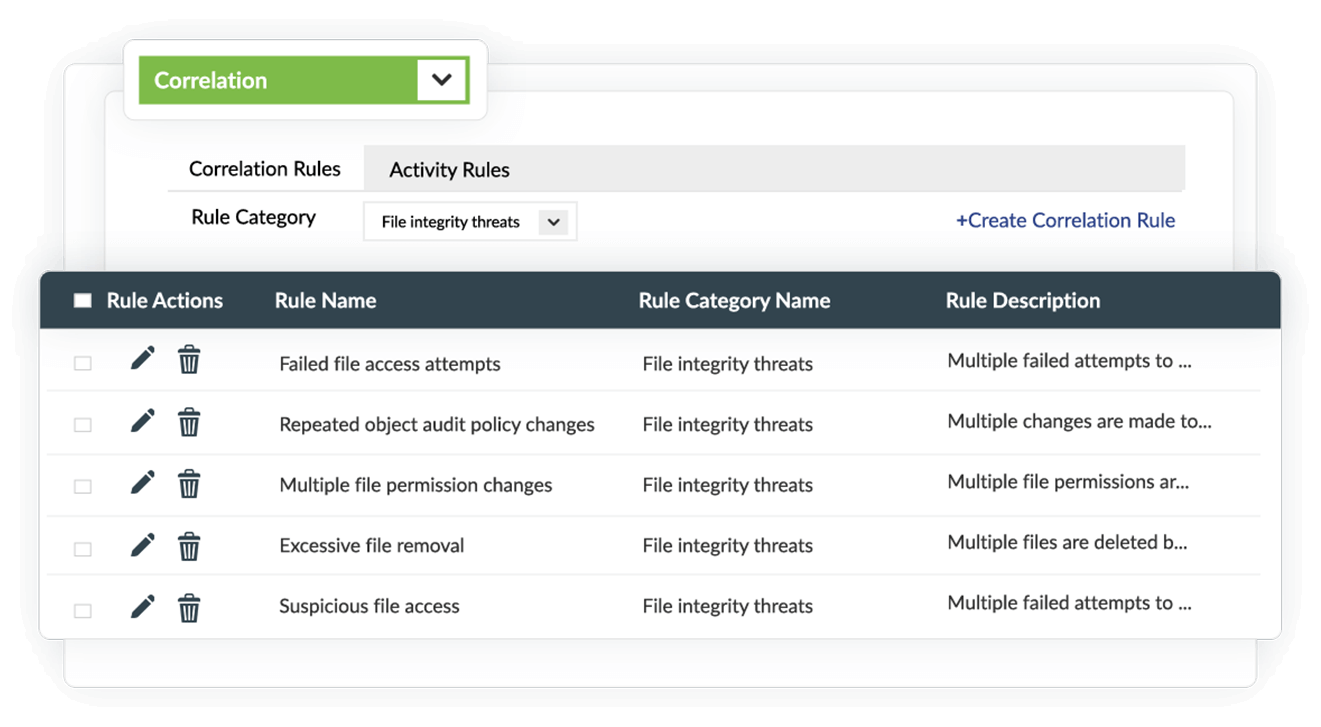
About File Integrity Monitoring in Log360
Log360 ensures comprehensive protection against data security and file integrity threats with the following FIM capabilities:
- 01
Comprehensive security
Provides a 360-degree security approach to protect critical data with out-of-the-box reports and alert profiles.
- 02
Cross-platform monitoring
Monitors both Windows and Linux environments for potential threats.
- 03
Insider threat detection
Identifies and mitigates risks from unauthorized file access and data tampering attempts.
- 04
Ransomware protection
Helps prevent ransomware attacks by detecting unusual file changes and anomalies.
- 05
Compliance assurance
Supports adherence to various data security compliance mandates.