Direct Inward Dialing: +1 408 916 9892
Follow step 1 and step 2 from the native auditing section to set up auditing for the particular group.
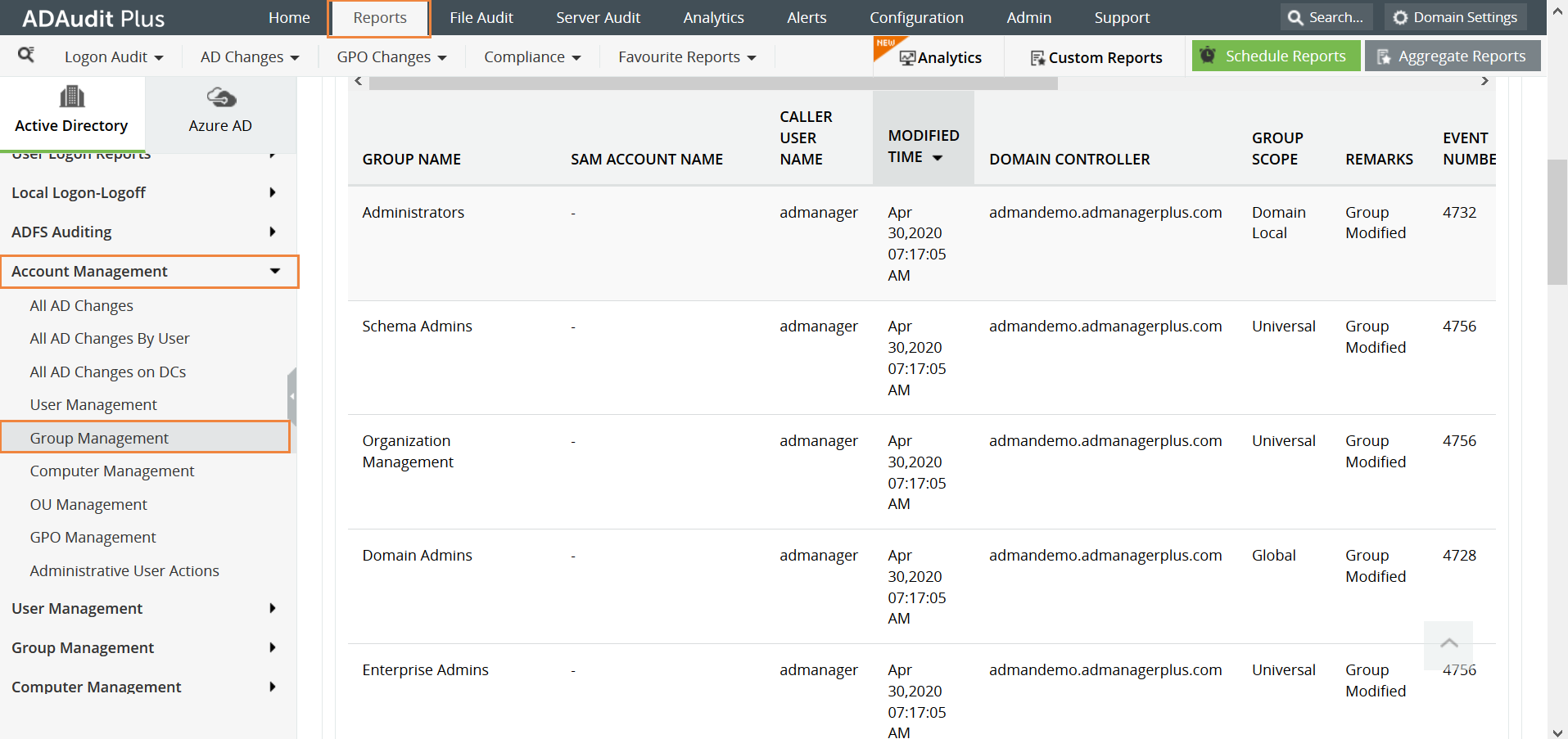
Then, open the ADAudit Plus console and click on the Reports tab, navigate to Account Management and select Group Management. This report gives you all the details about the changes that have been made in the group. Here is a sample report:
Open 'Server Manager' on your Windows server.
Under the 'Manage' tab, click on 'Group Policy Management' to open the 'Group Policy Management Console'.
Navigate to Forest>Domain>Your Domain>Domain Controllers.
You can choose to either edit an existing group policy object or create a new one.
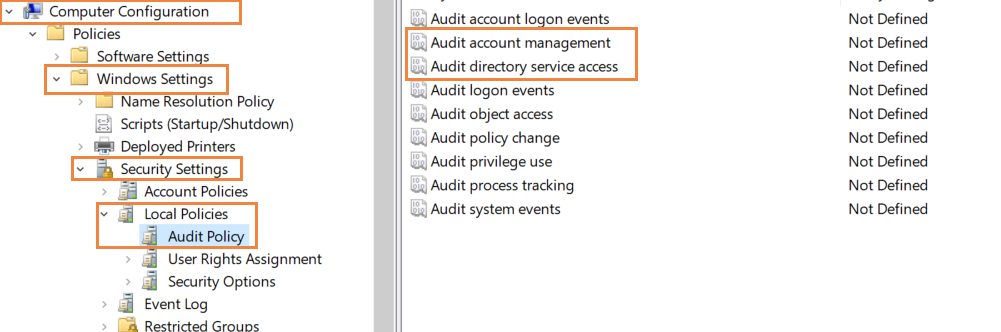
In the Group Policy Editor, navigate to Computer Configuration>Windows Settings>Security Settings>Local Policies>Audit Policy.
Here, configure 'Audit account management' and 'Audit directory service access' and enable them for 'Success' and 'Failure'.
Open Active Directory Users and Computers. Click on the 'View' tab at the top and select 'Advanced Features'.
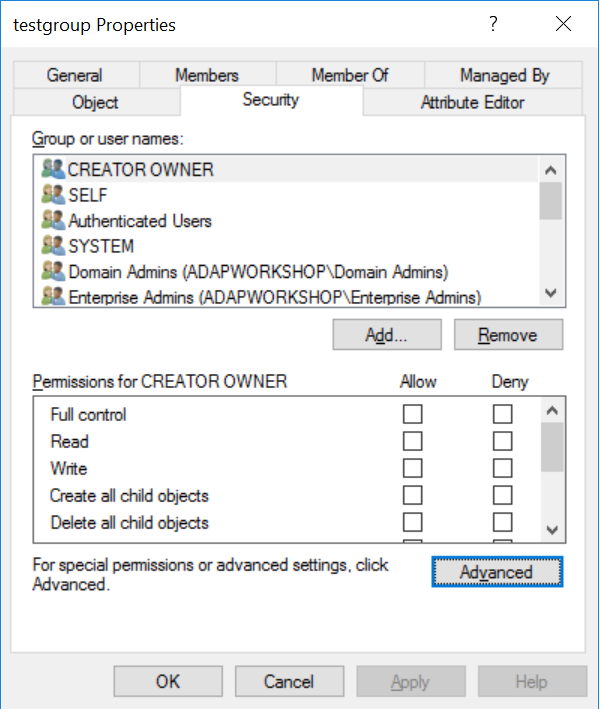
Right-click on the particular group and select 'Properties'.
Click on 'Security' and navigate to 'Advanced' tab at the bottom of the window.
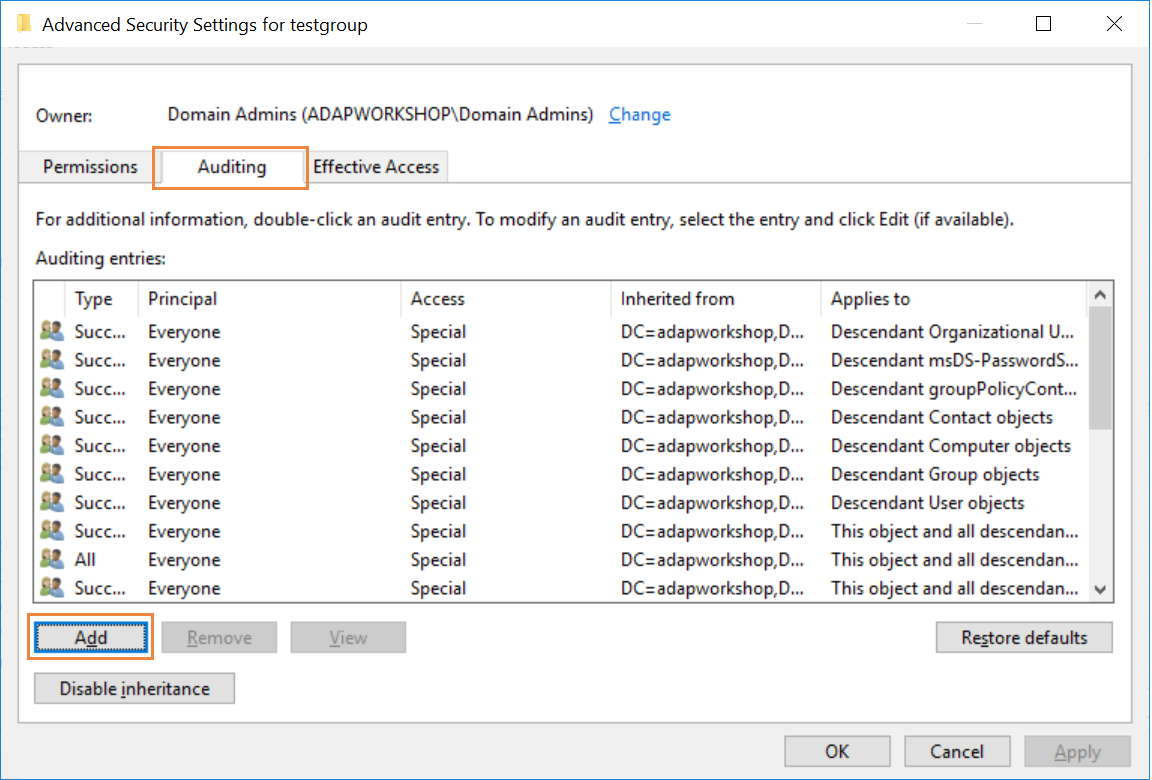
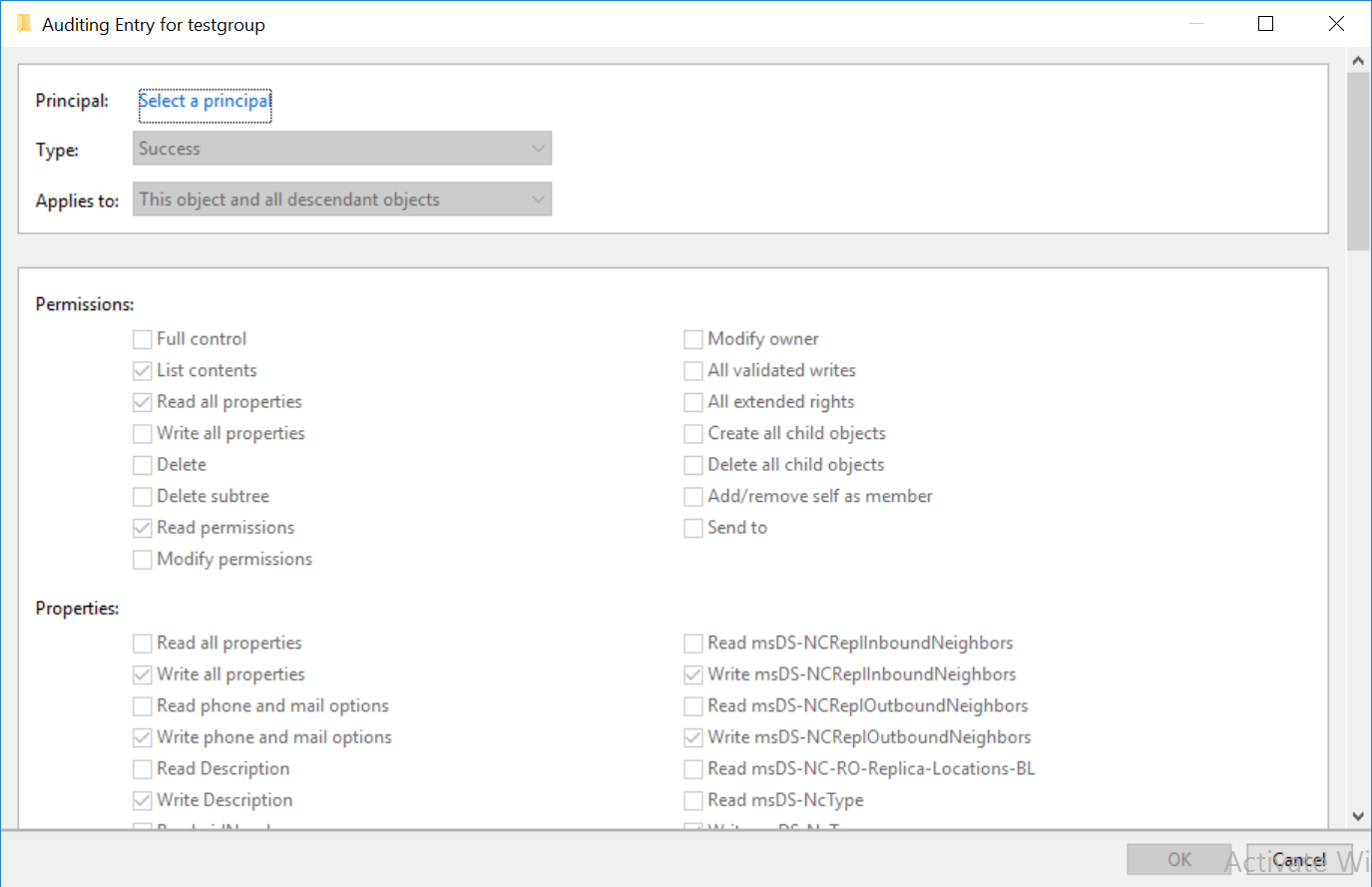
In the window that opens, select the 'Auditing' tab at the top and click on 'Add' to configure auditing.
Enter Principal as 'Everyone' and enable it for 'Success'. Also, select all permissions except for Full Control, List Contents, Read all properties, Read permissions. Then, click 'OK'.
The Event Viewer records the events that have been set up for auditing with their respective event IDs. Look for event IDs 4627 (group membership information), 4657 (registry value was modified), 4660 (an object was deleted), 4662 (An operation was performed on an object), 4727 (A group was created), 4728(A member added to a group), 4729(A member removed from a group), 4730(A group was deleted).
To find the events, open Event Viewer. On the left side, navigate to Windows logs>Security. The events can be viewed in the center pane.
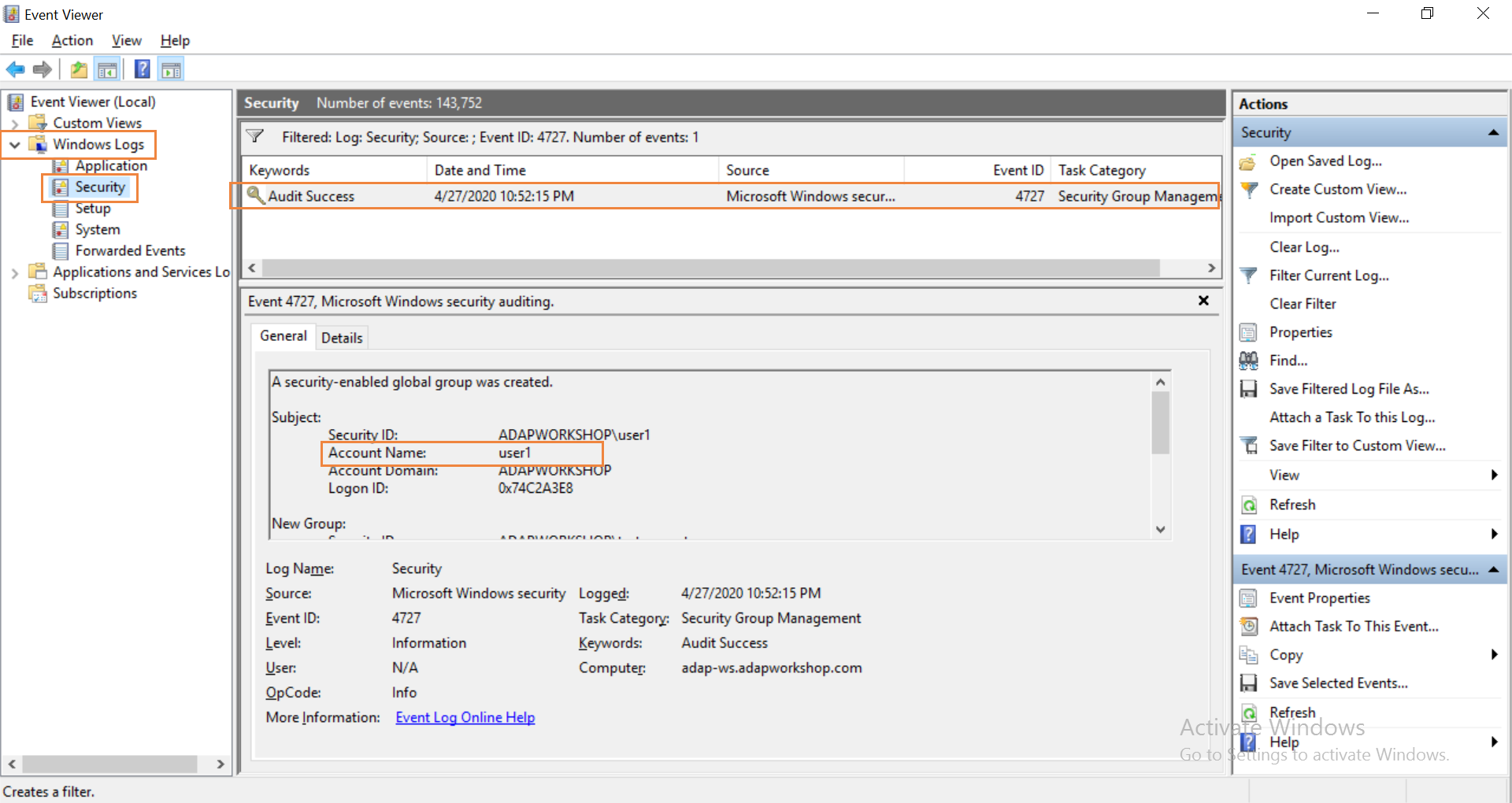
To find the user who initiated the event, click on the event. This can help check if the change was made by a non-admin user. You can filter the events by event IDs, the time range and more. Some of these event IDs are not exclusive to groups and therefore an administrator will have to inspect them in more detail to find if they are relevant to them. The administrator will have to sift through these events every time they want to find the changes made in a group.
Native auditing becoming a little too much?
Simplify Active Directory auditing and reporting with ADAudit Plus.
Get Your Free Trial Fully functional 30-day trial