Direct Inward Dialing: +1 408 916 9892
To track changes to your AD groups you will have to enable auditing of your Active Directory.
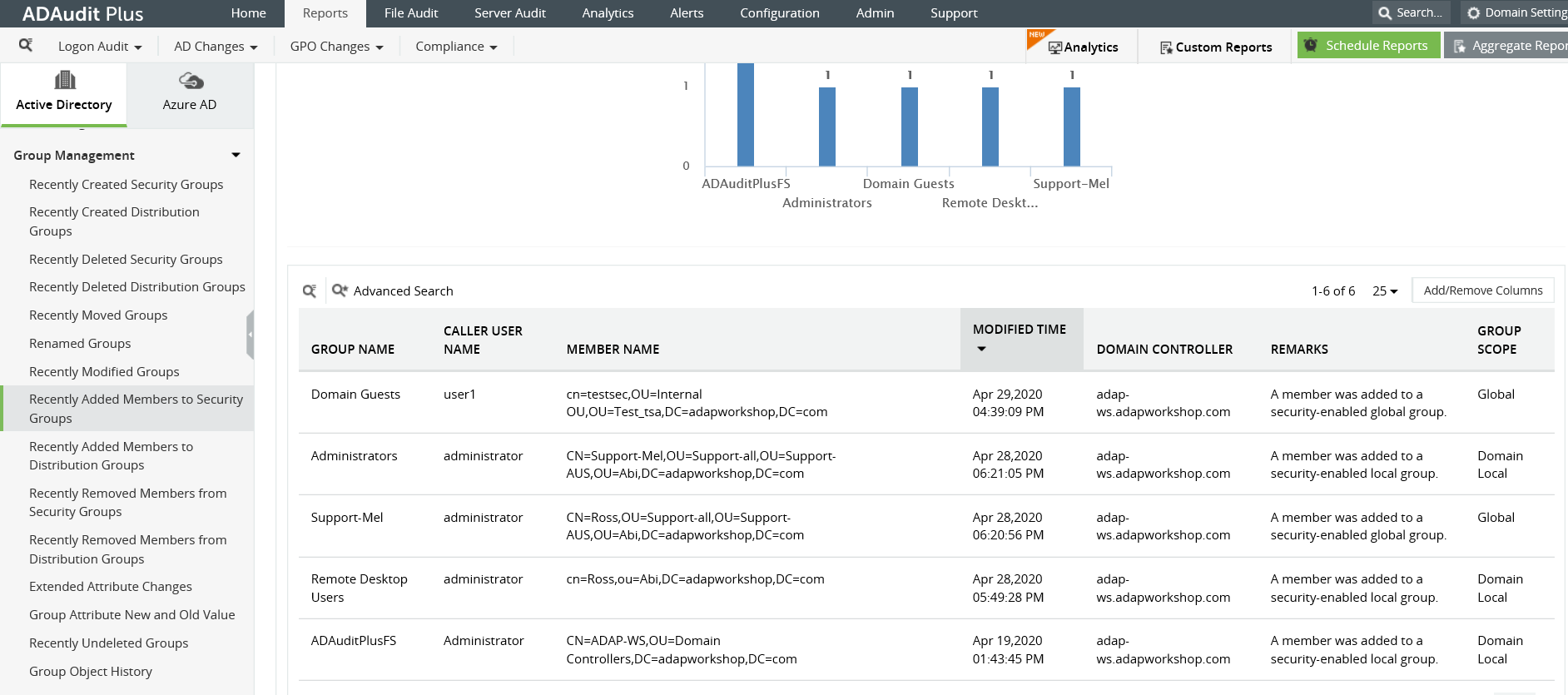
In the ADAudit Plus console, go to 'Reports' tab and navigate to 'Group Management' on the left pane. This provides you a list of pre-configured reports on group activity within AD.
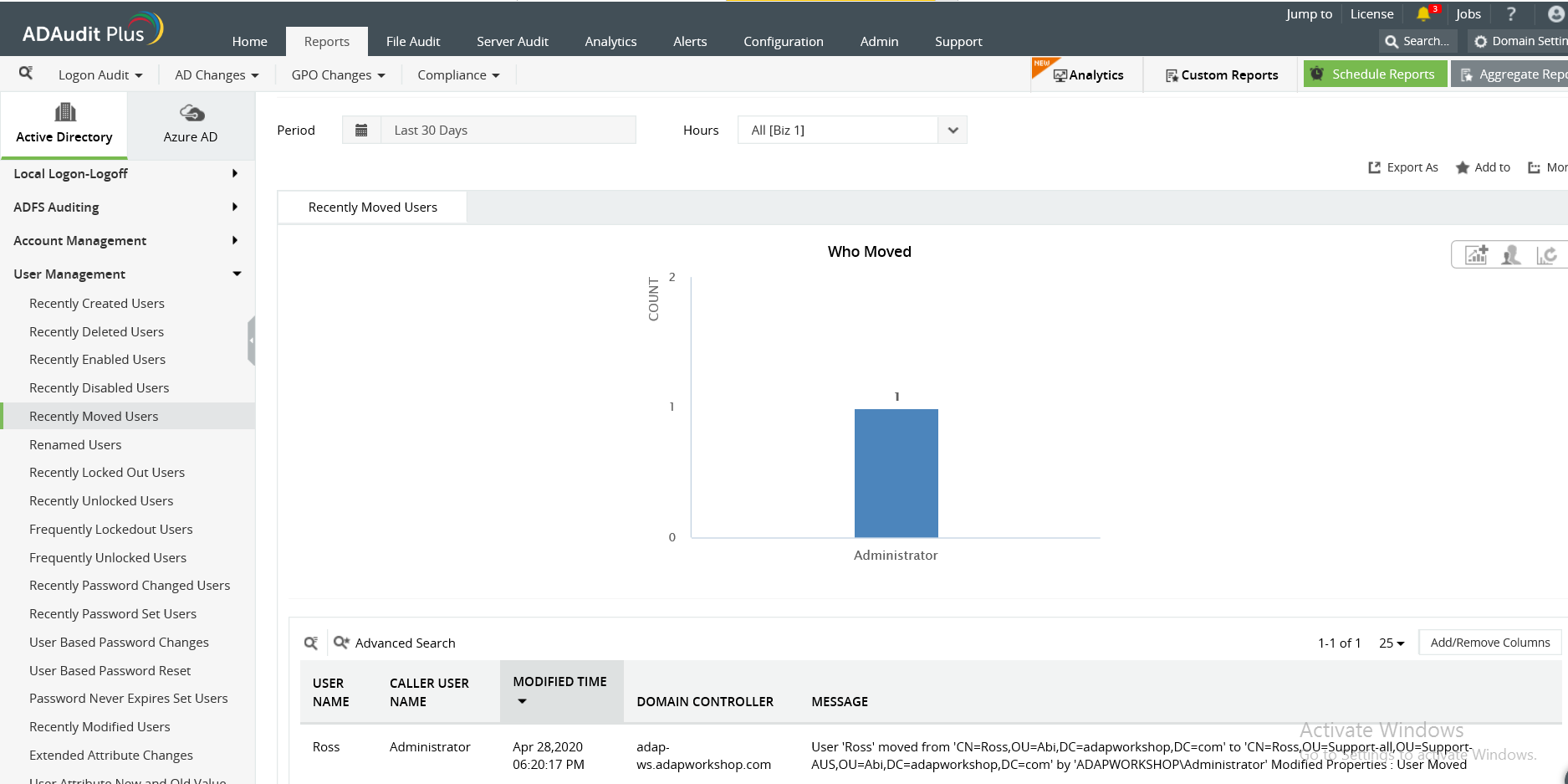
You can also access a consolidated view of user activity reports in relation to AD groups on the 'User Management' section.
The pre-configured reports include recently created and deleted security groups, any members added to or removed from a security group. You can also create custom reports and export reports in (CSV, PDF, XSL, HTML).
You can apply attribute-based filters like 'Group Name' , 'Domain Controller', 'Member Name, 'Group Scope' and more.
ADAudit Plus is a more effective solution to track AD group changes. With this solution, instead of looking for individual event IDs, you can have a consolidated view of all your group changes for a particular period. The solution's pre-configured reports also help you effortlessly track important changes to your AD with just a few clicks.
Launch the 'Server Manager' and open the Group Policy Management Console (GPMC).
In the left pane, expand the 'Forest' and 'Domains' nodes to reveal the specified domain you want to track the changes for.
Expand the domain and right-click 'Default Domain Policy'. You can also choose a domain policy that is universal throughout the domain, or create a new GPO and link it to the Default Domain Policy.
Click on 'Edit' of the desired group policy, to open up the Group Policy Management Editor.
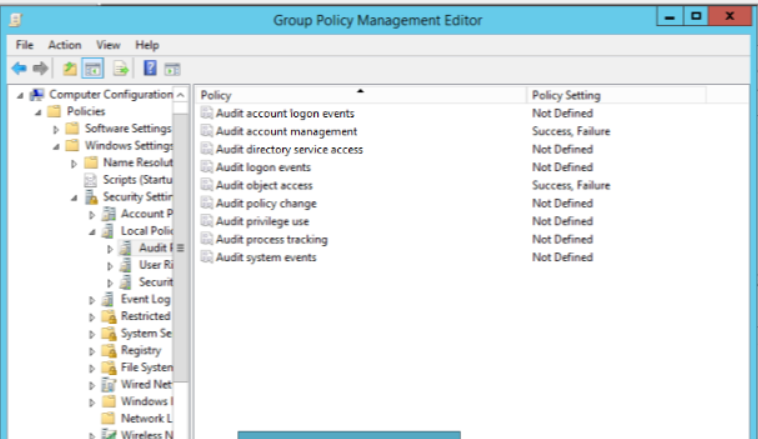
Expand 'Computer Configuration'--->Policies---->Windows Settings----->Security Settings----->Local Policies------->Audit Policies.
Enable success and failure options for 'Audit account management' and 'Audit object access' policy properties. Exit Group Policy Management Editor.
In the GPMC, choose the modified GPO, and click 'Add' in the 'Security' section on the right pane. Type 'everyone' in the text box and click 'Check Names' to "to track the changes made by everyone who has logged into the domain." or something similar would work.. Exit the GPMC.
To enforce these changes throughout the domain, run the command 'gpupdate /force', in the "Run" console.
From your 'Server Manager' go to 'Tools' and select 'ADSI Edit'.
Right click 'ADSI Edit' node from the left pane and select 'Connect to' option. This pulls up the 'Connection Settings' window.
Select the 'Default Naming Context' option from the 'Select a well-known Naming Context' drop down list.
Click 'Okay' and return to the ADSI Edit window. Expand 'Default Naming Context' and select the associated 'DC' subnode. Right-click this subnode and click 'Properties'.
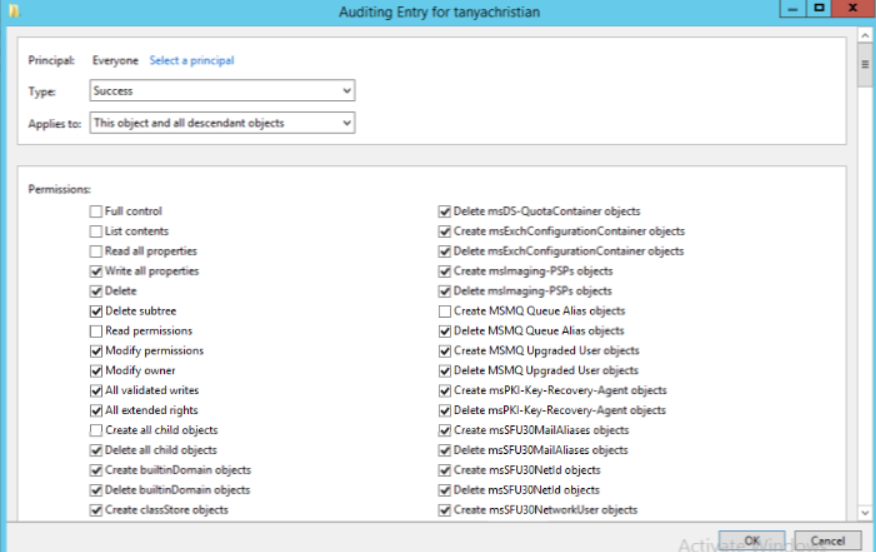
In the 'Properties' window, go to the 'Security' tab and select 'Advanced'. After that select 'Auditing' tab and click 'Add'.
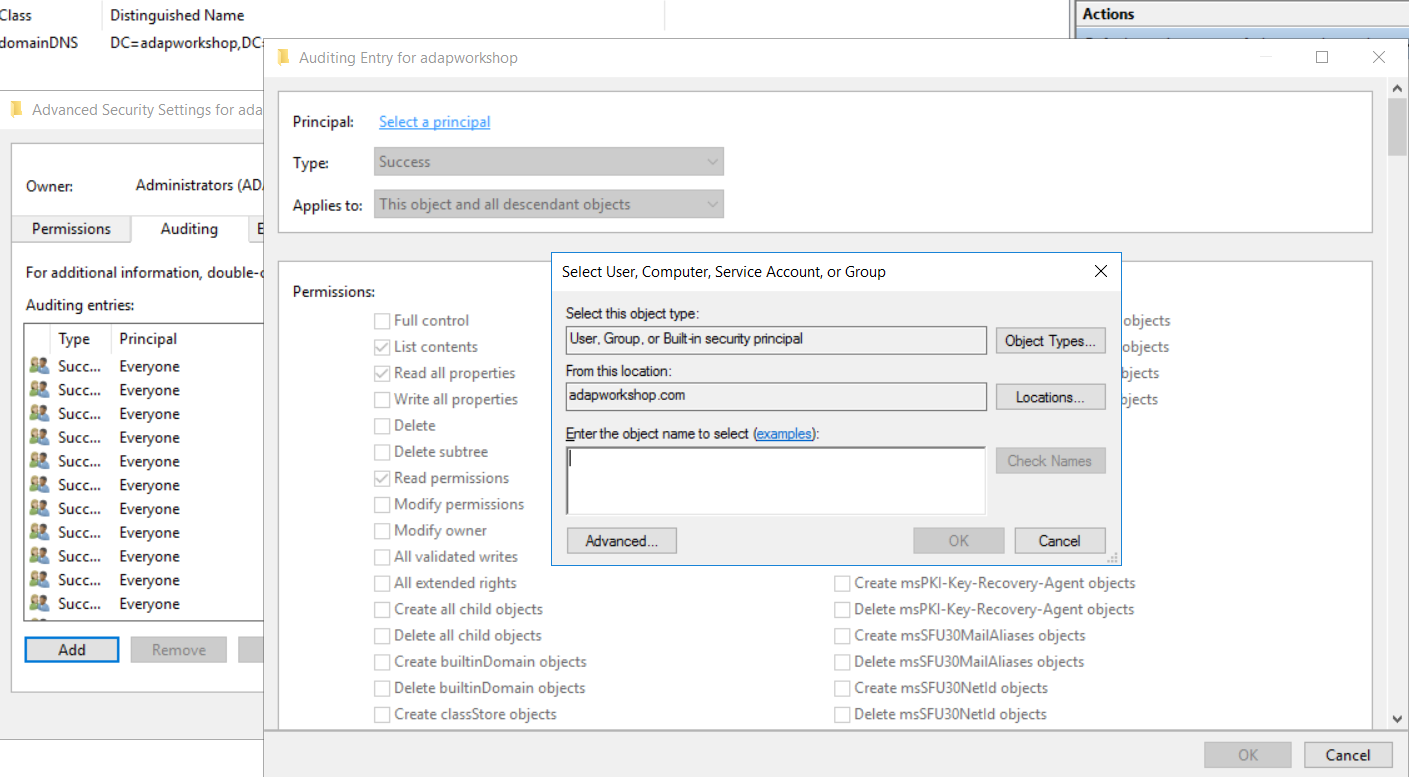
Click on ' Select a principal'. This will bring up a 'Select User, Computer or Group' Window. Type 'Everyone' in the textbox and verify it with 'Check Names'.
The 'Principal' in the 'Auditing Entry' window now shows 'Everyone'. In the 'Type' drop-down select 'All' to audit for both 'success' and 'failure' events.
In the 'Select' drop-down choose 'This object and all descendant object's. This allows the auditing of the OU's descendant objects. Select 'Full Control' in the 'Permissions' section.
This selects all the checkboxes available. Unselect the following check boxes:
Full Control
List Contents
Read all properties
Read permissions
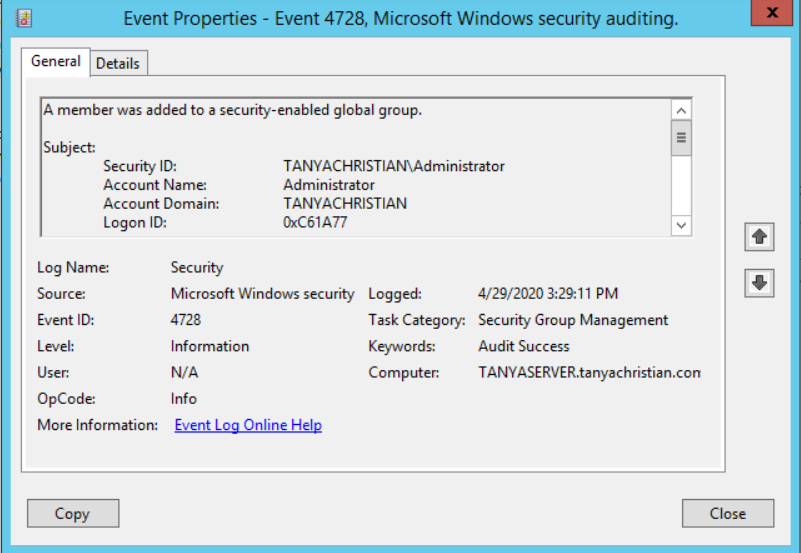
You can view changes to your groups by accessing 'Security Logs' in the 'Event Viewer'.Listed below are the events pertaining to AD group changes. You can search or filter for these events in your Event Viewer.
Event ID 4727: A security group is created
Event ID 4729: A member has been removed from a security group
Event ID 4728: A member has been added to a security group
Event ID 4730: A security group is deleted.
Does native auditing become a little too much?
Simplify group management and reporting with ADAudit Plus.
Get Your Free Trial Fully functional 30-day trial