Disclaimer: This guide cites guidance and documents about HIPAA published on the Department of Health and Human Services (HHS) website and the U.S. Government Publishing office.
What is HIPAA compliance?
Health Insurance Portability and Accountability Act of 1996 is a set of regulations that aims to:
- Safeguard the confidentiality and integrity of personally identifiable information (PII), protected health information (PHI), and electronic protected health information (ePHI) of patients.
- Protect workers by making their health insurance plans portable and renewable when they change jobs.
- Set guidelines for group health plans and life insurance policies.
According to the official document, the purpose of the Act is:
"To amend the Internal Revenue Code of 1986 to improve portability and continuity of health insurance coverage in the group and individual markets, to combat waste, fraud, and abuse in health insurance and health care delivery, to promote the use of medical savings accounts, to improve access to long-term care services and coverage, to simplify the administration of health insurance, and for other purposes."
HIPAA is structured into five titles:
- Title I -- Health Care Access, Portability, and Renewability: Ensures health insurance coverage for workers and their dependents during a time of a job change or loss of employment.
- Title II -- Preventing health care fraud and abuse; Administrative Simplification; Medical Liability Reform: Focuses on setting guidelines for establishing a fraud and abuse control program, and for the efficient and effective transmission of health information.
- Title III -- Tax-related Health Provisions: Establishes rules for pre-tax medical spending accounts.
- Title IV -- Application and Enforcement of Group Health Plan Requirements: Establishes rules for group health plans.
- Title V -- Revenue Offsets: Governs tax-related measures and offsets that help healthcare initiatives.
From a data privacy and security point of view, the Administrative Simplification provisions contained within Title II are the most important. They require the Department of Health and Human Services (HHS) to create standards for the effective, safe, confidential, and secure transmission of health information. Note that the Administrative Simplification provisions directly address the HHS and give them guidelines to create standards, as opposed to enshrining the standards themselves.
According to the requirements of Administrative Simplification of Title II, the HHS has developed six rules:
- Privacy Rule
- Security Rule
- Breach Notification Rule
- Enforcement Rule
- Transactions and Code Sets Rule
- Unique Identifiers Rule
In addition to these six rules, the HHS has also developed an Omnibus Rule that can be considered as a part of the Privacy Rule. The Omnibus Rule consists of updates and changes to existing regulations. See Figure 1 for a visual representation of the structure of the HIPAA.
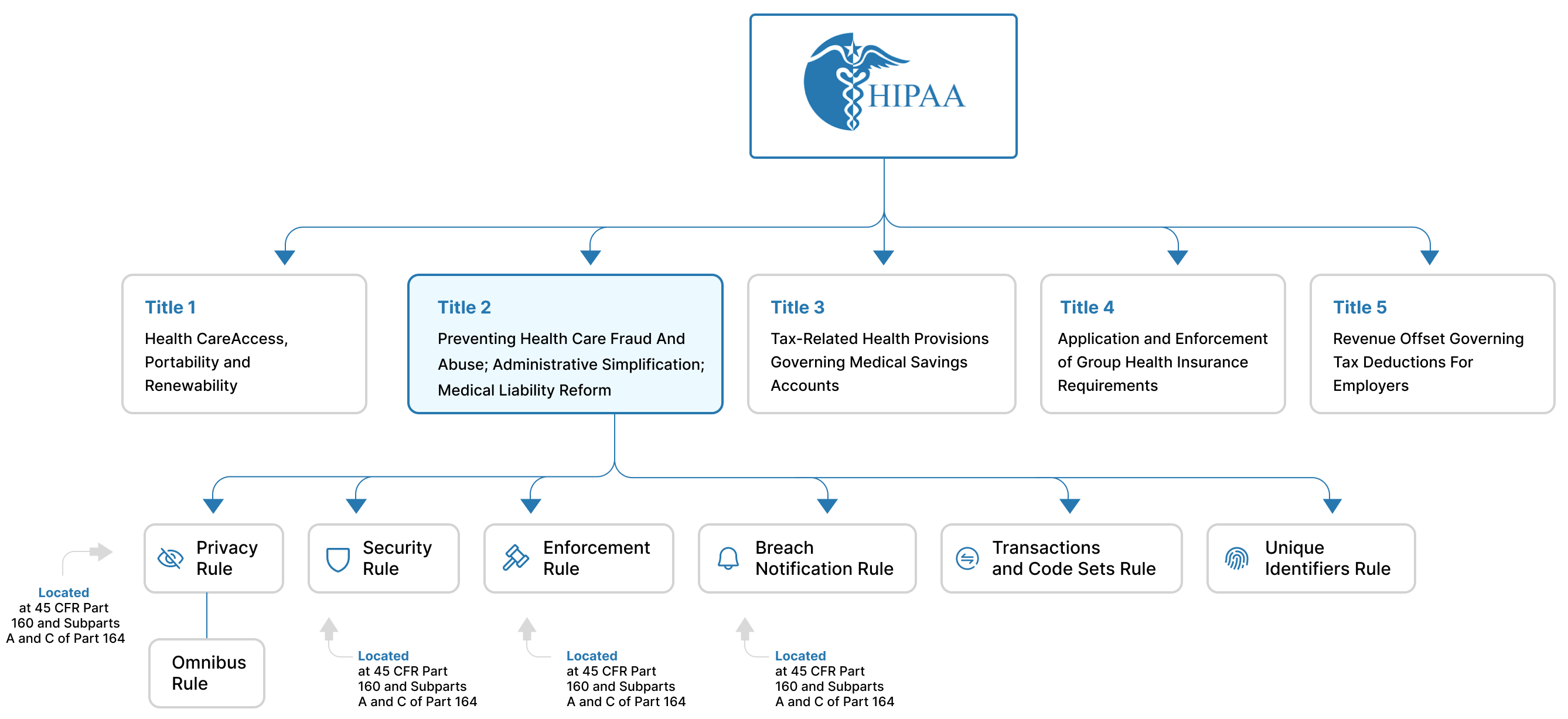
Figure 1: The structure of the HIPAA with details about Titles and Rules
These six rules consist of several regulations that have been developed by the HHS. These regulations have been codified into the Code of Federal Regulations (CFR). They can be found in several several parts of the CFR. (See Figure 2).
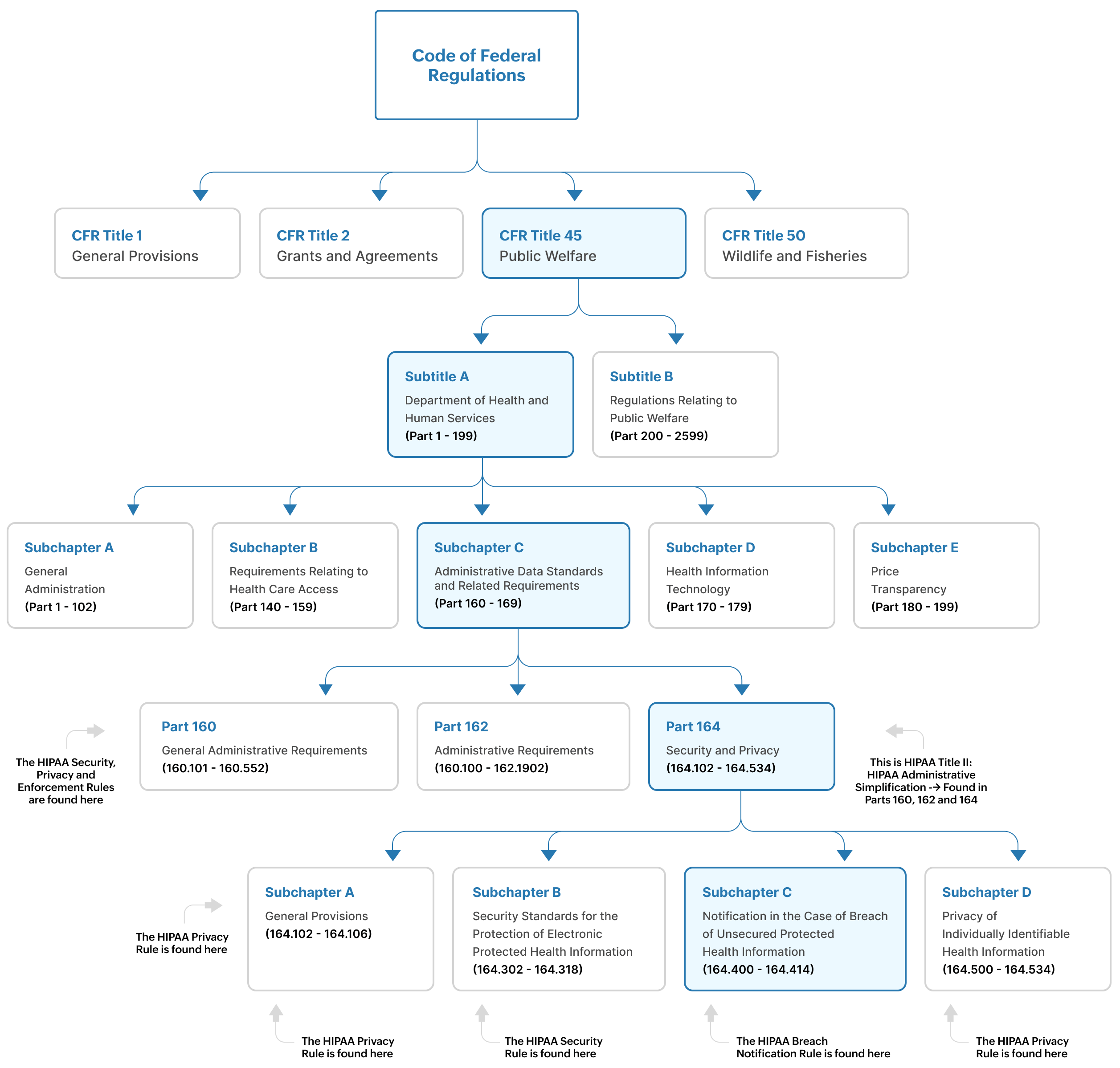
Figure 2: The location of HIPAA rules and requirements within the code of federal regulations
As you can see in Figures 1 and 2:
- The Privacy Rule is found at 45 CFR Part 160, and Subparts A and E of Part 164
- The Security Rule is found at 45 CFR Part 160, and Subparts A and C of Part 164
- The Enforcement Rule is found at Subparts C, D and E of 45 CFR Part 160
- The Breach Notification Rule is found at 45 CFR Part 164, 164.400-164.414
The regulations in 45 CFR are administered by the HHS and other federal agencies involved in public welfare programs.
Who must comply?
HIPAA is applicable only to entities and individuals operating within the United States. The mandate describes two groups of institutions that need to comply with HIPAA:
Covered entities (CEs):
Any healthcare provider, health plan provider or healthcare clearing house in charge of transmitting any health information under the purview of the HIPAA. Examples of CEs include doctors, therapists, dentists, hospitals, healthcare insurance companies, and government programs that pay for a patient's healthcare.
Business associates (BAs) who serve the CEs:
A third-party individual or entity that carries out certain functions or activities on behalf of a covered entity, that could involve the use or disclosure of PHI. Examples include MSPs, IT providers, faxing companies, and cloud storage providers.
Here's a guide by the HHS to determine if you're a covered entity or not.
Requirements of HIPAA
Title II of the HIPAA--known significantly for the Administrative Simplification provisions--aims to improve the efficiency of the healthcare system by establishing electronic healthcare transaction standards and ensuring protection of health information. The requirements of Title II are found in the Privacy, Security, Data Breach Notification, Enforcement, Transactions and Code Sets, and Unique Identifiers Rules as put forth by HHS. These are in turn found in Parts 160, 162 and 164 of 45 CFR.
The Privacy Rule
The privacy rule is designed to guard "individually identifiable health information" commonly called PHI. This includes health-related information such as a patient's physical or mental health, healthcare services received by the patient, and healthcare-related payments. The privacy rule also ensures the rights of individuals to access their health-related information. The Privacy Rule also mandates that CEs and BAs must acquire written authorization from patients for the disclosure of healthcare data that goes beyond treatment, payments and healthcare operations.
The Security Rule
If the privacy rule is focused on establishing what patient data should be protected, then security rule defines the standards on how that data must be protected. This rule focuses on ways the data's integrity and availability can be ensured by diving into how it must be stored, audited, transmitted, etc. The security rule makes it imperative to establish tools and policies that protect ePHI against entities that might want to misuse patient heath information.
The Security Rule establishes administrative, physical, and technical safeguards for the protection of PHI. (See Figure 3).
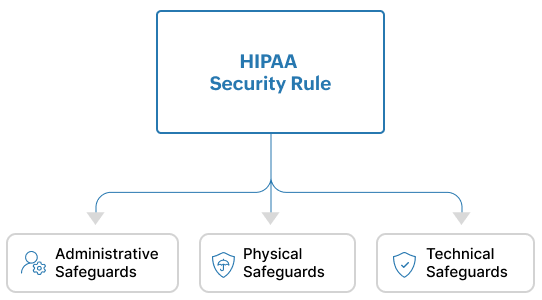
Figure 3: The HIPAA Security Rule comprises of Administrative, Physical and Technical Safeguards
Administrative Safeguards are policies and procedures that ensure that a covered entity or business associate is able to detect risks to or the tampering of ePHI.
Physical safeguards ensure that organizations have access control mechanisms in place to limit physical access to their facilities only to authorized personnel. They also make it mandatory for organizations to enforce policies for the proper physical access of devices, workstations, servers, etc.
Technical safeguards require organizations to:
- Implement and invest in technical solutions that act as access control mechanisms to only allow authorized access to ePHI.
- Deploy the right software such as security information and event management (SIEM) solutions to detect, analyze and investigate any activity that happen on servers that contain ePHI.
- Ensure that ePHI is not tampered, sabotaged or destroyed.
- Protect against attacks such as man-in-the-middle that attempt to maliciously intercept ePHI as it moves through a network.
Breach Notification Rule
This rule lays out the procedures that CEs and BAs must carry out in the event of a breach of unsecured PHI. Unsecured PHI is patient health information that has not been encrypted or protected by any security measures, thus making it vulnerable and easily accessible to unauthorized entities.
This Rule gives clear instructions about when to notify affected individuals, the HHS, and the media in the event of a breach. It also gives details about how a breach notification must be communicated and the documentation required for the purposes of audits.
Transactions and Code Sets Rule
This rule establishes national standards for electronic healthcare transactions such as claims, remittance advices, eligibility inquiries, and claim status inquiries. It introduces specific code sets such as ICD (International Classification of Diseases), CPT (Current Procedural Terminology), and HCPCS (Healthcare Common Procedure Coding System) for healthcare organizations to use in their billing and reporting practices.
Unique Indentifiers Rule
Through the use of unique identifiers, this rule ensures the accurate identification of entities involved in healthcare activities and transactions. For example, National Provider Identifiers (NPIs) are used to identify healthcare providers. Another important identifier is the Health Plan Identifier (HPID) which is used for health plans.
Enforcement Rule
The Office for Civil Rights (OCR) within the HHS oversees the enforcement of the Privacy and Security Rules. Covered entities and business associates may face penalties for HIPAA violations. The Enforcement Rule lays out the procedures for investigation in case of a HIPAA violation.
Apart from these six rules, the Omnibus Rule was issued by the HHS in 2013 to strengthen and expand certain provisions of HIPAA, particularly those related to privacy and security of protected health information. It brought about significant enhancements and updates to the HIPAA Privacy, Security, Enforcement, and Breach Notification Rules.
Some key changes of the Omnibus Rule include the Expansion of Business Associate Liability, Increased Penalties for Non-Compliance, more stringent Breach Notification Requirements, and increased patient rights.
Resources
Log360 Enables Guthrie Medical Group to Easily Audit Changes to its IT Infrastructure
Learn moreInvivoscribe Technologies, Inc. Effectively Detect Threats and Combats Cyberattacks using Log360
Learn moreHow SIEM solutions help organizations comply with HIPAA requirements
Use case 1: Establish policies and procedures to monitor threats to ePHI
This use case maps directly to HIPAA Security Rule 164.312(c)(1),which requires covered entities and their associates to"implement policies and procedures to protect ePHI from improper alteration or destruction."
Problem
The ePHI held by covered entities and their associates is often the target of threat actors. 2023 witnessed a staggering 725 breaches and the compromise of over 133 million patient records.
In a healthcare network, ePHI is usually stored within centralized systems, cloud storage systems, backup systems, databases, email servers, etc. These storage components are often a major target for attackers. The theft of sensitive patient data is a lucrative venture for attackers looking to sell information on the dark web. The loss of ePHI andePHI tampering have other concerning consequences, such as delayed patient treatment, the disclosure of sensitive information, and legal and financial consequences for the healthcare facility.
Solution
The covered entity must have the right policies and procedures in place to protect patient data. To do this, the organization needs to establish a policy to collect and audit logs from critical servers holding ePHI. Additionally, the SOC team needs to have an alerting mechanism in place to notify it of any suspicious events. Some suspicious events a SOC team should watch out for include:
- Unauthorized user activities (like access attempts, deletions, and permission changes) performed on sensitive patient information.
- Suspicious processes targeting ePHI.
- Suspicious logins on devices containing ePHI.
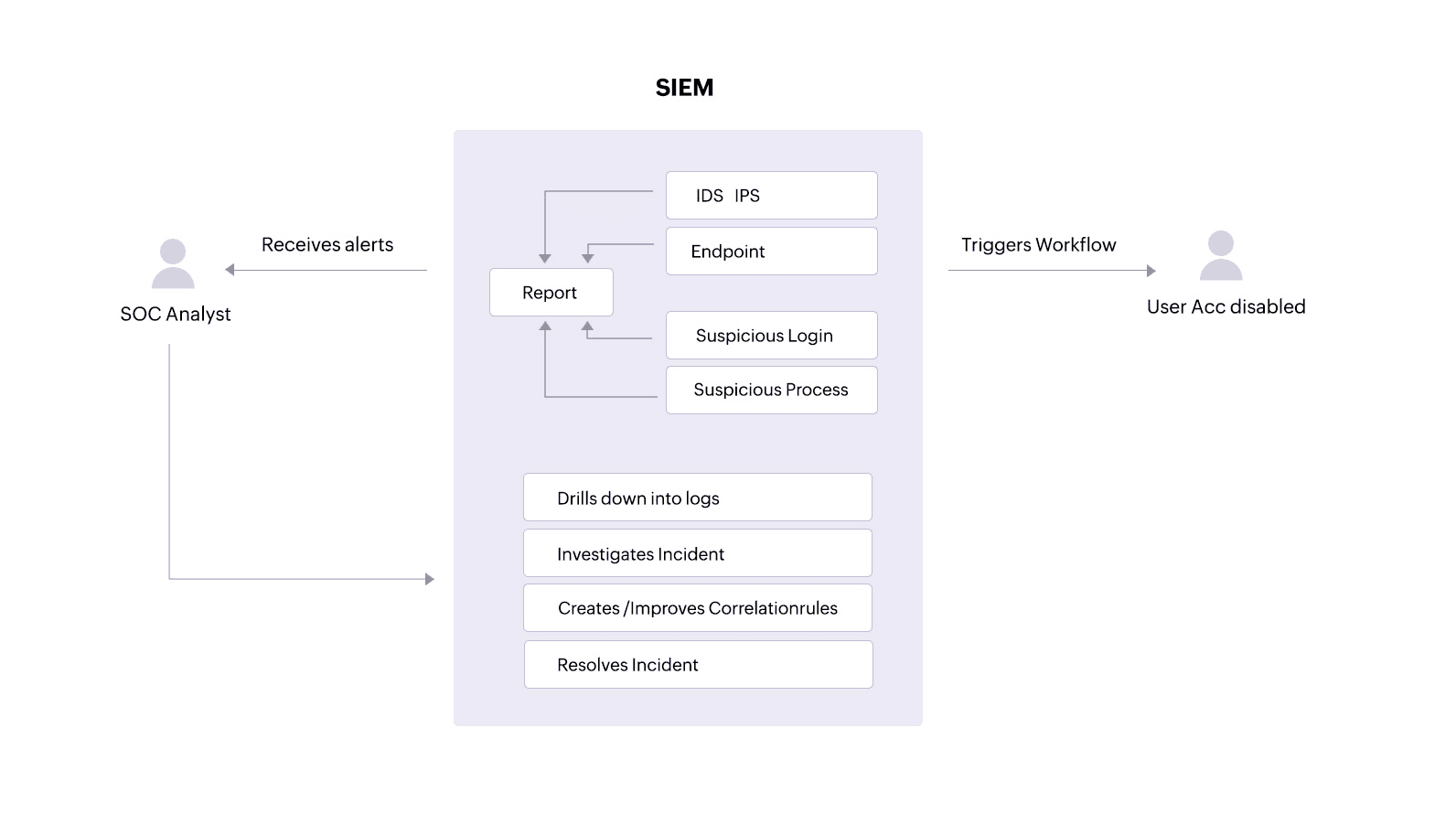
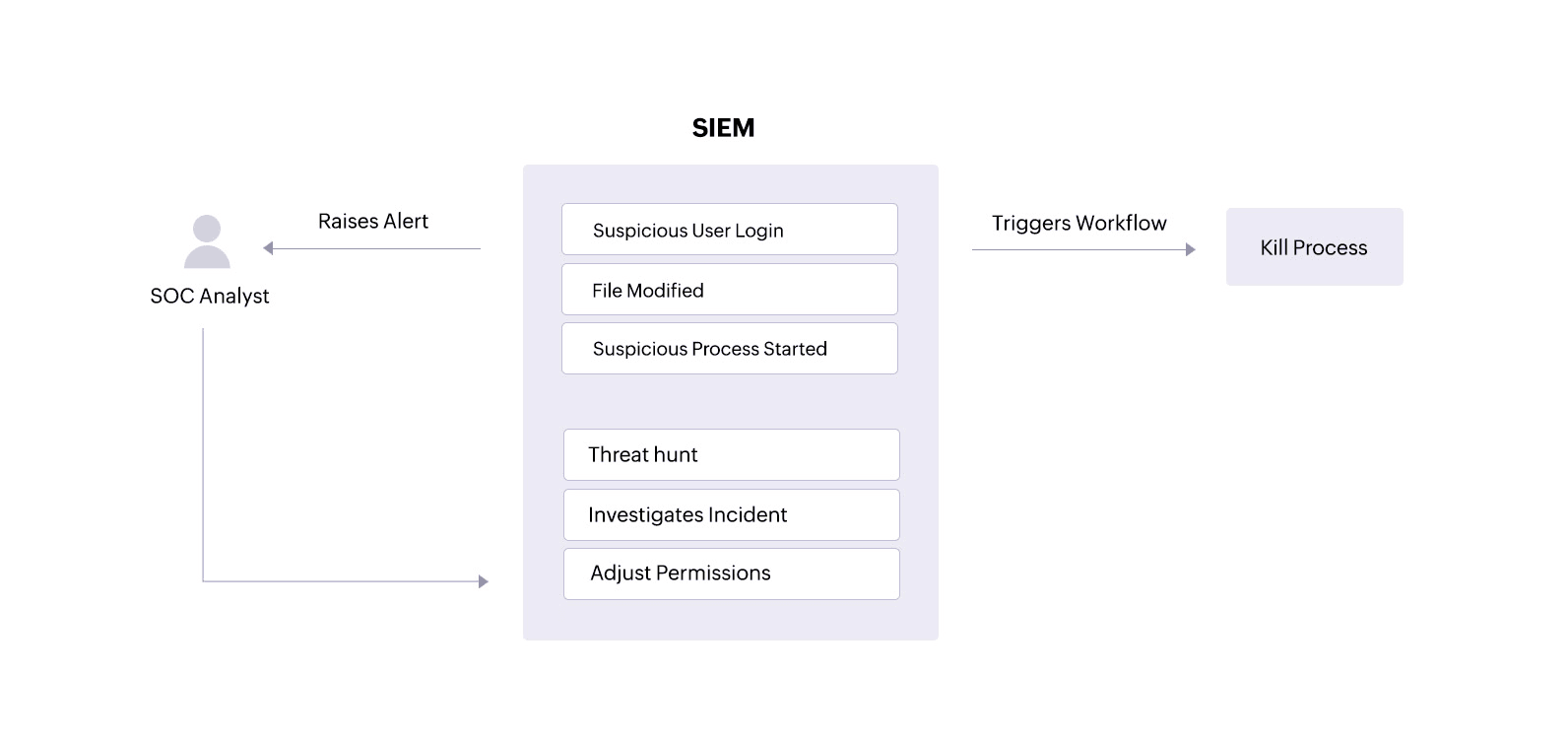
A SIEM solution can alert an analyst about unauthorized access attempts or ePHI tampering. With clear reports, the analyst can track down users, malware, or processes that might threaten the security and integrity of the patient information. The analyst can also drill down into logs from devices holding ePHIto investigate and resolve incidents.
Additionally, a SIEM solution equipped with incident response capabilities can trigger an automated response to an alert, performing predefined actions like disabling user accounts that might be trying to access devices where ePHI is stored or stopping processes that are targeting sensitive patient files.
Use case 2: Monitor user activity on different endpoints
This use case maps directly toHIPAA Security Rule 164.308(a)(3)(ii)(A), which requires covered entities and their associates to "implement procedures for the authorization and/or supervision of workforce members who work with ePHI or in locations where it might be accessed."
Problem
HIPAA mandates user activity monitoring in the covered entities' networks. This allows a security analyst to know if any suspicious activity is going on in their network so they can thwart it immediately.
Solution
A SIEM solution can alert a SOC analyst about suspicious user activities that could indicate an insider threat on servers and in other storage systems containing patient information. The SOC analyst can review suspicious user logins, abnormal processes started by particular users, and any ePHI file tampering connected to specific user accounts—all within the SIEM solution.
Beyond monitoring, a SIEM solution also facilitates log forensics. This allows security analysts to threat hunt for malware that might have bypassed network defenses and accessed ePHI. With this information, analysts can investigate and swiftly resolve incidents to minimize damage and data loss.
Use case 3: Cooperate with compliance auditing processes
This usecase directly maps to HIPAA Enforcement Rule 160.310(b), which states that the covered entities and their associates must "cooperate with complaint investigations and compliance reviews."
Problem
Audits can be a stressful time for organizations. An audit where a company fails to prove compliance can result in severe penalties. HIPAA violations can result in monetary penalties, legal action, and, in severe cases, jail time.
Solution
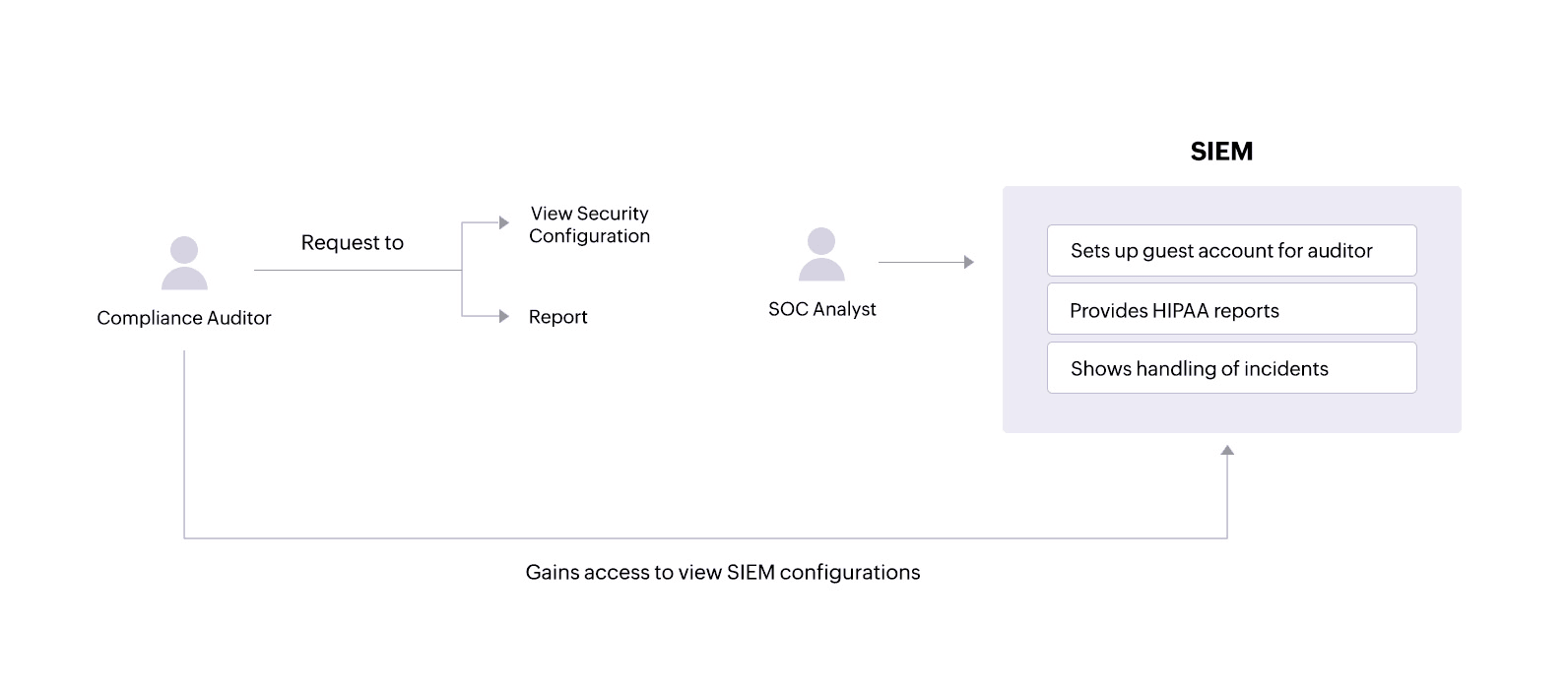
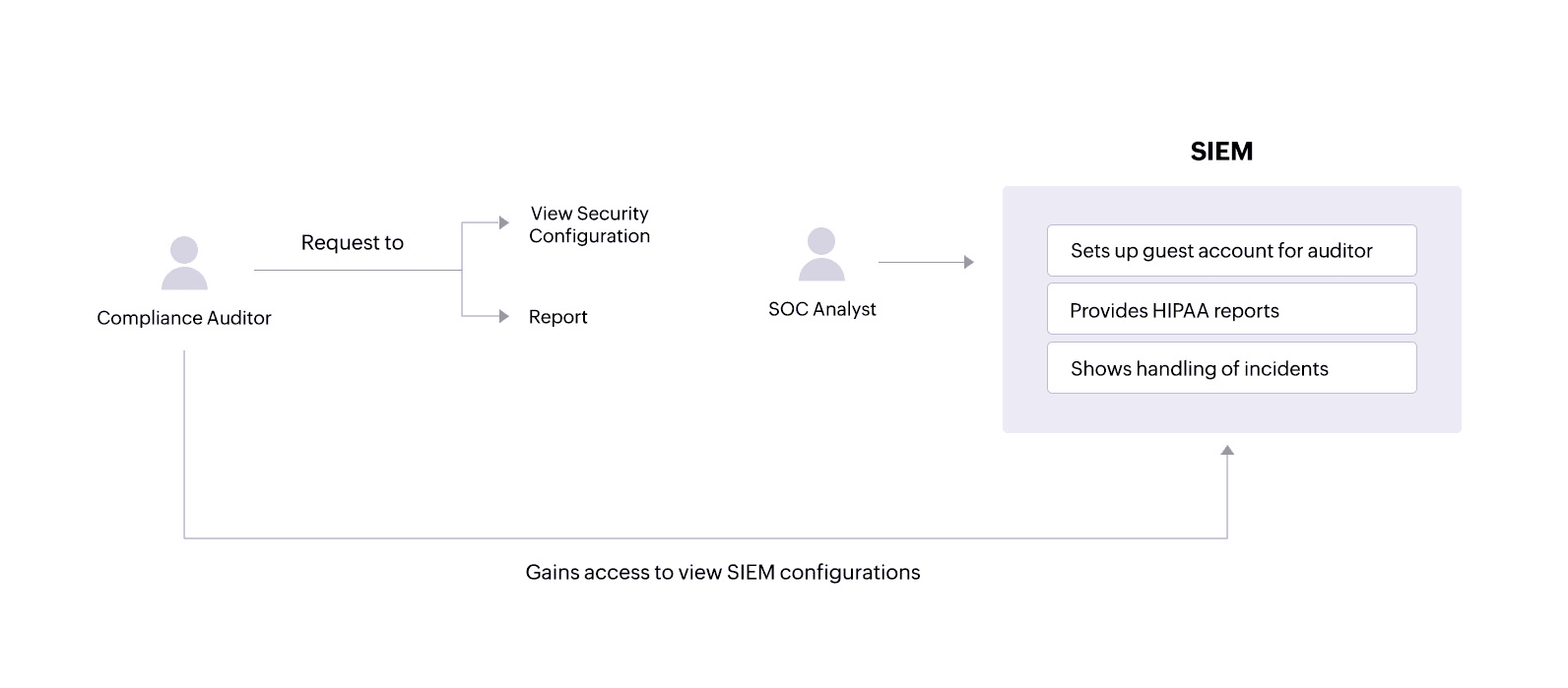
During audits, a compliance auditor may require access to various network activity reportsand might also want to view security configurations within the SIEM solution.
A SIEM solution like Log360 allows administrators to set up guest accounts with certain privileges that an auditor can use to view only the necessary configurations. The solution also provides tailored reports that offer important information and help covered entities and their associates comply with specific HIPAA standards.
SOC analysts can:
- See in-depth reports on actions performed on sensitive patient files.
- Get details on successful and failed login attempts on critical servers that hold ePHI.
- Receive reportsidentifying local system processes that are malicious and might compromise ePHI security.
All of this helps organizations successfully clear HIPAA audits.
Use case 4: Monitor and analyze audit logs
This usecase directly maps to HIPAA Security Rule 164.312(b), which requires covered entities and their associates to "implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use ePHI."
Problem
Deleting logs is a tactic used by attackers to cover their tracks after a security breach. Malicious insiders might also try to erase their actions by deleting logs.
Solution
ASIEM solution can help SOC teams comply with HIPAA auditing rules by securing all logs on information system activity. A SIEM solution brings together logs from devices containing ePHI, other endpoints, and threat intelligence sources so that SOC analysts can get a comprehensive view of the attack patterns that could breach ePHI. SOC analysts can also get alerted about log file tampering or deletion,investigate these incidents, and make changes to security permissions accordingly.
Use case 5: Retain logs
This usecase directly maps to HIPAA Enforcement Rule 160.310(c)(1),which requires that "acovered entity or business associate must permit access by the Secretaryduring normal business hours to its facilities, books, records, accounts, and other sources of information, including protected health information, that are pertinent to ascertaining compliance with the applicable administrative simplification provisions."
Problem
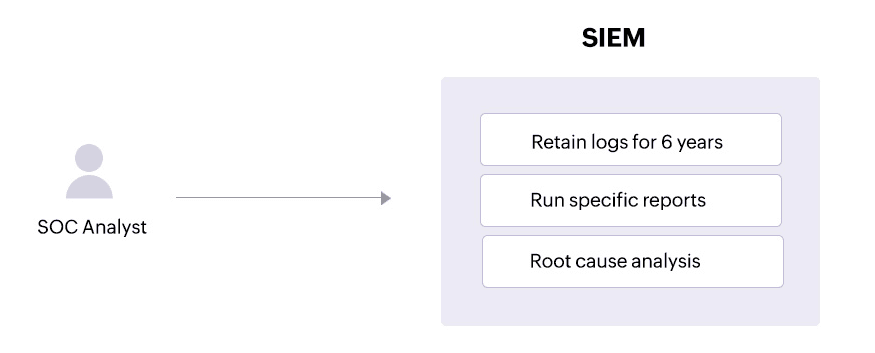
HIPAA's record retention requirements specifythat all HIPAA-related documentsmust be retained for a minimum of six years from the date when a policy or procedure was last in force.
Solution
A SIEM solution like Log360 allows SOC admins to configure retention requirements for their logs according to their needs. This helps organizations stay compliant and cooperate with compliance audits.
How to be HIPAA compliant
Security Rule: General rules
Requirement 164.306(a)(1)
Safeguard all ePHI to ensure its privacy, accuracy, and accessibility.
To comply, you need to monitor the sensitive files, folders, and directories where ePHI may be stored. You can use capabilities such as file integrity monitoring to accomplish this.
Requirement 164.306(a)(2)
Your organization must be able to protect ePHI against any reasonably anticipated threats.
You must first develop security use cases to help your organization address potential risks. These can then guide your organization to create detection rules that target these threats.
Requirement 164.306(a)(3)
Protect ePHI against illegitimate use or access that can be reasonably anticipated.
Your organization must be able to monitor access to sensitive information continuously and prevent illegitimate access.
Requirement 164.306(a)(4)
Your organization must ensure that all employees comply with the Security Rule.
To meet this requirement, you must be able to track employee activity at the file level, and receive alerts if an employee performs any activity that is not allowed.
Requirement 164.306(b)(2)(i)
Your organization must use security measures that take into account your business complexity, size, and capabilities.
The security measures you use should be highly scalable and fit your security needs.
Requirement 164.306(b)(2)(ii)
Your organization must use security measures that take into account your technical or network infrastructure, hardware, and software capabilities.
The security measures you use should be highly scalable. In case you use a security solution or software, it should be able to integrate and communicate with your existing infrastructure.
Requirement 164.306(b)(2)(iii)
Your organization must use cost-effective security measures while not compromising on the quality.
As long as they are effective, the security measures you use can provide a good ROI and need not be expensive.
Requirement 164.306(b)(2)(iv)
Your organization must use security measures that take into account the probability of potential risks to ePHI.
You must be able to create detection rules in your security solution based on the probability of a particular risk. Your security solution should also be able to give you a view of user and entity risk before an incident actually takes place.
Security Rule: Administrative Safeguards
Requirement 164.308(a)(1)(i)
Implement policies to detect and contain security violations.
To comply, you must be able to create detection rules in your security solution based on the probability of a particular risk. Your security solution should also be able to give you the ability to respond to security violations automatically.
Requirement 164.308(a)(1)(ii)(A)
Perform a risk analysis and assess the vulnerabilities to the confidentiality, integrity and availability of the ePHI.
Your security solution must highlight potential vulnerabilities in your network. It must also show a risk score for entities including file servers that hold sensitive information.
Requirement 164.308(a)(1)(ii)(D)
Implement procedures to regularly review records of information system activity
An effective SIEM or security analytics solution will be able to provide a centralized view of important information system activity such as audit logs, access reports, and security incident tracking reports.
Requirement 164.308(a)(3)(ii)(A)
Implement procedures to authorize and supervise employees who work with ePHI.
Implementation of an effective SIEM or security analytics solution that monitors user activity on the network will be able to accomplish this for you.
Requirement 164.308(a)(3)(ii)(B)
Implement procedures to determine if access levels an employee has are appropriate.
You must be able to check access levels of employees for a specific file or folder by running on-demand reports. You must also be able to perform file analysis to detect any inappropriate access.
Requirement 164.308(a)(3)(ii)(C)
Implement the policy of least privilege.
An employee who has access to ePHI should no longer have access to it once their job has been completed. You can automate your access control policies using criteria such as time and role.
Requirement 164.308(a)(4)(ii)(A),(B),(C)
Implement policies and procedures for authorizing and granting access to ePHI
It can be within departments or divisions. You must also be able to modify a user's privileges as needed.To comply, you need to set the right access control policies and watch for violations.
Requirement 164.308(a)(5)(ii)(B)
You need procedures for guarding against, detecting, and reporting malicious software.
You need to monitor the installation and use of all software, services and processes within your organization.
Requirement 164.308(a)(5)(ii)(C)
You need procedures for monitoring log-in attempts and reporting discrepancies.
A SIEM or security analytics solution that tracks both successful and unsuccessful user logons and logoffs can help you do this.
Requirement 164.308(a)(5)(ii)(D)
You need to safeguard your users' passwords.
To comply, ensure that you have an effective password policy while also monitoring the use of the passwords.
Requirement 164.308(a)(6)(i)
In case of a security incident, you need to be able to respond effectively.
To comply, ensure that you have an effective policy in place. This policy must include ways to automate your response to a security incident, where possible.
Requirement 164.308(a)(6)(ii)
In case of a security incident, you need to be able to respond effectively. You should be able to respond to mitigate the incident as much as possible.
To comply, ensure that you have an effective policy in place. This policy must include ways to automate your response to a security incident. For example, you can make use of playbooks and workflows to implement the first level of response to an incident.
Security Rule: Technical Safeguards
Requirement 164.312(b), ( c)(1)
You need to implement a hardware or a software solution that can audit, record and analyze any activity on servers that contain ePHI. You should also protect ePHI from from tampering and destruction.
A SIEM solution that can connect to different parts of your network and monitor all activity will accomplish this for you. In case of an unauthorized access or modification,you need to ensure IT security at the organization can be alerted.
Requirement 164.312(c)(2), (d)
Protect ePHI from improper access.
You need to implement an effective identity and access management solution to authenticate and authorize users.
Enforcement Rule
Requirement 160.308
In case the HHS conducts an investigation about a possible violation of the HIPAA, your organization must be able to cooperate and furnish relevant details about the compliance status.
You need to be able to provide proper reports to show that your organization is compliant along with proof of security configurations during an audit
Requirement 160.310(a)
Provide records and compliance reports during an investigation
Your organization must possess records and reports that give information about the privacy and security of PII and PHI.
Requirement 160.310(c)
Permit access to relevant information to the auditors appointed by the HHS
At the time of an investigation, the HHS may require your organization to permit access to certain sensitive information for ascertaining if your organization is in compliance.
Breach notification rule:
Requirement 164.404(2)(c)(A)
Provide a concise summary of the incident, including the breach date and the date it was discovered, if available
You can use a SIEM solution to study forensic data from logs to determine what occurred on the network. Along with time stamps and other metadata, notifications must be sent out to the individuals impacted by the security incident.
Requirement 164.404(2)(c)(B): Description of Affected Information:
Detail the categories of unsecured protected health information compromised in the breach, including but not limited to full name, social security number, date of birth, home address, account number, diagnosis, disability code, and any other pertinent data.
A proper SIEM solution will also give you information on what information was breached. This helps the covered entity notify the individual about what personal information was exposed.
Requirement 164.406 (2)(c)
The notification mandated under paragraph (a) of this provision must adhere to the specifications outlined in § 164.404(c). This includes a succinct overview of the incident, encompassing the breach date and, if ascertainable, the date of its discovery.
You can use a SIEM solution to study log forensics to determine what occurred on the network. A brief explanation from this analysis can be used to notify the media.
Requirement 164.410
The notification should include the identification of each individual whose ePHI was accessed, acquired, used, or disclosed during the breach.
A proper SIEM solution will give you information on what information was breached. This helps the covered entity notify the covered entity about what personal information was exposed.
Requirement 164.410(c)(2)
A business associate must provide all required details of the breach to the covered entity with any additional information required for notification. A clear summary of the incident, with the breach date and date of its discovery should be a part of this.
You can use a SIEM solution to understand the pattern of events that led to the breach. This can be used to notify covered entities.
Privacy Rule
Requirement 164.524
Individuals have the right to access and obtain a copy of their protected health information. Exceptions include psychotherapy notes and information prepared for legal proceedings.
The covered entity uses access controls within their system to ensure only authorized personnel with the appropriate permissions can access ePHI. SIEM monitors these access attempts. When staff retrieve the requested ePHI, SIEM logs the activity, creating an audit trail for compliance purposes. If there's any unusual access attempt during the retrieval process, SIEM can alert security personnel for investigation.
Requirement 164.526(d)(4)
If a patient disagrees with something in their medical records, the patient can request a change. The covered entity can accept or deny the request. If denied, both sides can add their explanation (patient's disagreement and doctor's reason for denial) to the medical record.
SIEM solutions can't change records, but it keeps a log of who accessed the record and when. This log can help prove that only authorized personnel made the amendments.
Requirement 164.528
You must provide an account of all disclosures of an individuals ePHI.
While SIEM isn't directly involved in generating the accounting report, it can indirectly support compliance by collecting logs from various systems, including those that may contain PHI access attempts. By monitoring PHI access logs, SIEM can help create an audit trail demonstrating that only authorized personnel accessed the information for disclosures.
The HIPAA compliance checklist
To comply with the HIPAA, you need to implement standard policies and educate the concerned personnel through proper awareness training. Here are a few IT best practices for managing PHI, and avoiding non-compliance with HIPAA and subsequent OCR penalties:
Password Policy and Multi-Factor Authentication:
- Strengthen password policies and employ multi-factor authentication on all devices accessing medical records for heightened security.
Zero Trust Model for Access Control:
- Adopt the Zero Trust security model to limit access to patient information strictly to essential requirements or with explicit patient consent, enhancing network monitoring, and reducing unauthorized access.
Prohibition of Credential Sharing:
- Enforce strict prohibitions against sharing credentials among employees to prevent unauthorized access to sensitive data.
Minimization of PHI in Emails:
- Reduce reliance on emails containing PHI due to email security vulnerabilities and the risks of unauthorized access or forwarding.
Regular HIPAA Security Assessments:
- Conduct routine HIPAA security assessments to ensure ongoing compliance with updated security policies and guidelines.
Antivirus Software Updates:
- Ensure continuous updating of antivirus software on all devices to mitigate malware risks and potential security breaches.
Compliance of Storage Services and Applications:
- Verify that all storage services and applications used adhere to HIPAA security guidelines to protect patient information adequately.
Incident Response Plan Implementation:
- Activate the incident response team and execute the incident response plan promptly in case of a data breach to minimize damage and expedite recovery. Investigate and eliminate security threats at their root.
Document Access Control and Submission:
- Verify that shared documents do not contain sensitive data accessible to unauthorized individuals.
- Provide specified documents to auditors upon request, ensuring they are updated and submitted in compliant formats (Microsoft Excel, Word, or PDF) via the OCR web portal.
How to check if you're compliant
Memo on Security Policies and Procedures:
- Have all staff members received a memo on security policies and procedures?
- Have they read and attested to it?
- Is the attestation documented?
Security Policies Review and Updates:
- Is there documentation on reviews and updates to the security policies?
HIPAA Compliance Training:
- Has HIPAA compliance training been conducted for all employees?
- Is documentation available for the conducted training?
- Is there a designated employee overseeing effective training sessions and HIPAA compliance?
Business Associates and HIPAA Compliance:
- Have all business associates been identified?
- Is there a Business Associate Contract in place with third parties handling healthcare information?
- Have the business associates been audited for HIPAA compliance?
- Is there proper documentation for these business associate audits?
Security Incident Management:
- Is there technical and administrative infrastructure in place to handle security incidents?
- Are there systems to track breaches to the network?
- Is there documentation for investigations into security incidents?
- Are comprehensive reports available for all security incidents and their causes?
What happens to organizations that violate HIPAA?
When an organization does not comply with HIPAA regulations, it may face severe consequences:
Civil Monetary Penalties (CMPs)
- The OCR enforces HIPAA rules and applies civil monetary penalties for non-compliance which can range from $100 to $50,000 per violation. This is subject to the level of negligence and the severity of the violation.
- For violations due to willful neglect that are not corrected, higher penalties can apply, up to $1.5 million per violation per year.
Corrective Action Plans (CAPs)
- In addition to monetary penalties, non-compliant bodies have to execute corrective action plans (CAPs). These plans define corrective measures the organization must take to solve existing deficiencies to comply with HIPAA regulations.
- CAP measures such as revising policies and procedures, conducting staff training, enhancing security controls, and implementing safeguards to protect protected health information (PHI) will help penalized organization achieve HIPAA compliance.
Loss of Reputation and Trust
- HIPAA violations can damage the organization's reputation with patients, clients, and stakeholders. They also lead to negative publicity and loss of revenue.
Legal Consequences
- HIPAA violations also have legal consequences, in the form of civil lawsuits by affected individuals or class-action lawsuits. These legal actions create financial distress for the organization.
Denial of Medicare/Medicaid Payments
- In higher tiers of non-compliance, Medicare or Medicaid payments to the organization can be denied by the HHS, which worsen the financial position for healthcare providers that rely on government programs to reimburse them.
Audits and Investigations
- Not being HIPAA compliant can result in audits or investigations by the OCR or other regulatory agencies. These audits include thorough review on whether the organization is HIPAA compliant. Entities found to be non-compliant may face enforcement actions.
Take the lead in data protection best practices with our unified SIEM solution!



