Data exfiltration definition
Data exfiltration occurs when threat actors deliberately transfer, copy, or retrieve data from a computer or network without authorization. This cyberattack technique focuses on extracting sensitive information while attempting to evade detection by security systems. The exfiltrated data may include:
- Customer personally identifiable information (PII)
- Financial records and transactions
- Intellectual property
- Trade secrets
- Employee information
- Authentication credentials
How does data exfiltration occur?
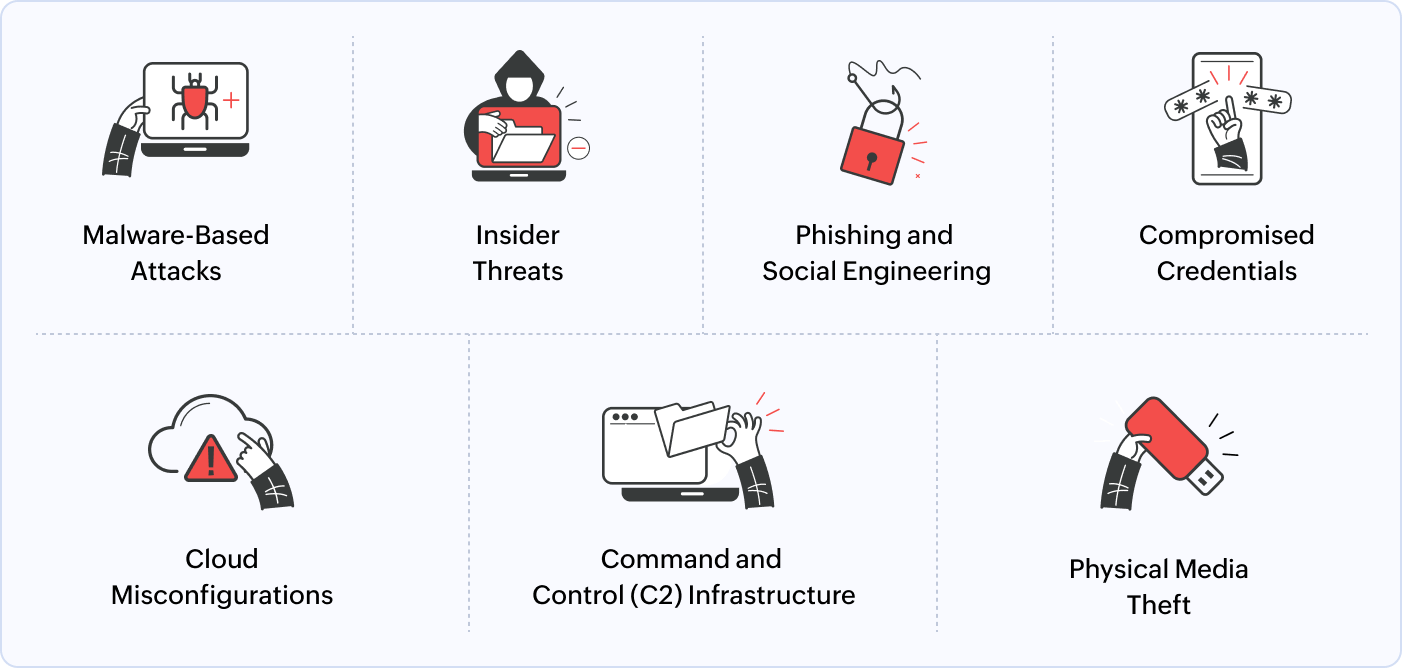
Data exfiltration happens when attackers exploit security gaps to extract sensitive information from an organization's network. This can occur through various means, including:
- Malware-based attacks: Attackers deploy malware to extract sensitive data and transfer it to external servers.
- Insider threats: Employees or contractors with legitimate access may exfiltrate data intentionally or accidentally.
- Phishing & social engineering: Attackers manipulate users into sharing credentials to enable data theft.
- Compromised credentials: Unauthorized users gain access to sensitive files and exfiltrate data.
- Cloud misconfigurations: Improperly configured cloud storage exposes data to unauthorized access and exfiltration.
- Command and control (C2) infrastructure: Attackers use C2 channels to exfiltrate data stealthily.
- Physical media theft: USB drives and external storage devices are used for unauthorized data transfers.
Data exfiltration techniques and MITRE ATT&CK® Mapping
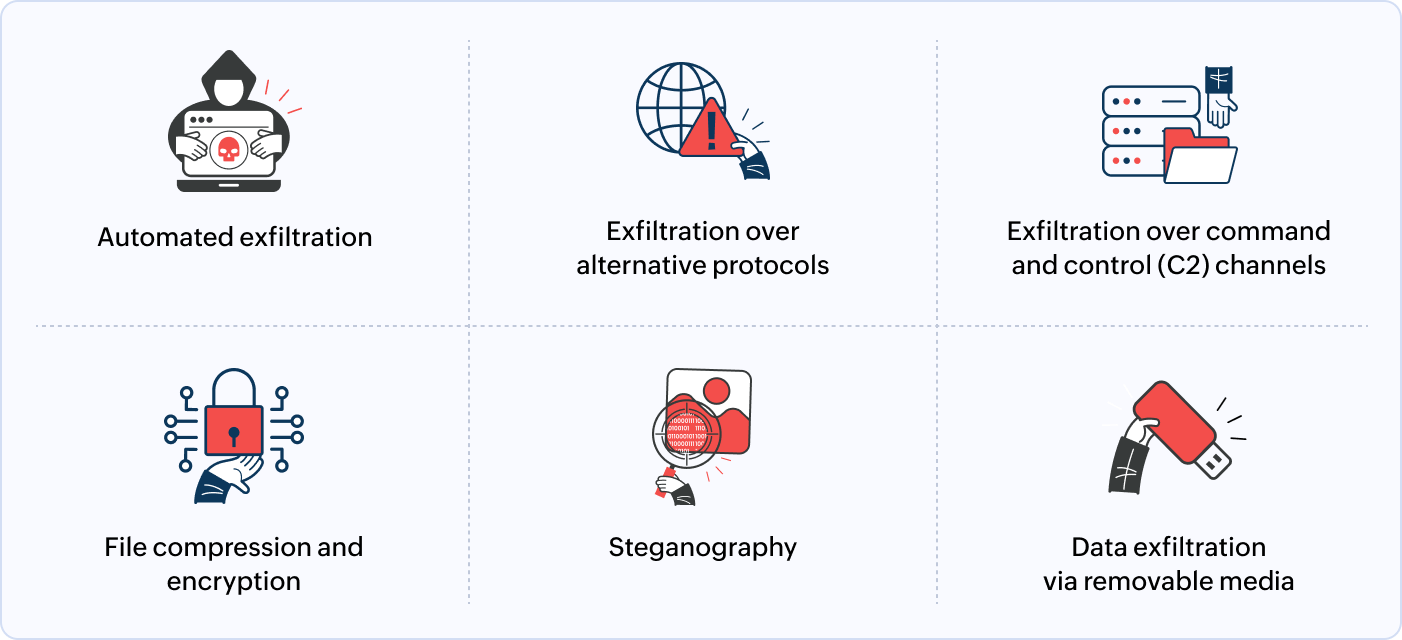
The MITRE ATT&CK framework lists several techniques that attackers can use for data exfiltration, including:
- Automated exfiltration: Cybercriminals deploy scripts and malware to extract data without manual intervention continuously. These scripts often run in the background, making detection difficult.
- Exfiltration over alternative protocols: Attackers use non-standard communication channels such as DNS tunneling, ICMP, or SMTP to bypass security measures and exfiltrate data without raising alarms.
- Exfiltration over command and control (C2) channels: Cybercriminals establish C2 communication to send stolen data to attacker-controlled servers. This method helps maintain persistence and evade detection.
- File compression and encryption: Before exfiltrating data, attackers compress and encrypt files to reduce detection risk. Encrypted data appears as harmless traffic, making it difficult to identify exfiltration attempts.
- Steganography: This method hides sensitive data within images, audio files, or video content, making it nearly undetectable by traditional security tools.
- Data exfiltration via removable media: Attackers or insiders transfer data using USB drives, external hard disks, or other removable storage devices, allowing for offline exfiltration that bypasses network monitoring.
Data exfiltration prevention
Organizations can mitigate data exfiltration risks by implementing strong security controls. Key preventive measures include:
- Network monitoring: Deploy SIEM solutions to continuously monitor network traffic and detect suspicious data movements.
- Data loss prevention policies: Enforce strict data access rules, classify sensitive data, and block unauthorized transfers.
- Zero Trust architecture: Restrict access using a least-privilege approach and continuous authentication to minimize insider threats.
- User awareness training: Educate employees on phishing threats, social engineering tactics, and best practices for handling sensitive data.
- Insider threat detection: Leverage behavioral analytics to identify unusual user activity indicative of potential data exfiltration attempts.
- Strict USB and peripheral controls: Disable unauthorized USB ports and external storage device access to prevent offline data theft.
- Email and web filtering: Monitor outbound emails and internet activity to block potential exfiltration through cloud storage or unauthorized email transfers.
Indicators of data exfiltration
Detecting data exfiltration early can prevent significant damage. Some key indicators include:
- Unusual outbound traffic, especially to unknown IPs or geographic locations.
- Large volumes of data transfers outside normal working hours.
- Multiple failed login attempts followed by successful access to sensitive files.
- Sudden spikes in compressed or encrypted file transfers.
- Unexpected use of cloud-sharing services or external storage devices.
How can ManageEngine Log360 help with detecting data exfiltration?
ManageEngine Log360 stands out as a comprehensive SIEM solution that combines log management, analysis, advanced threat detection, user and entity behavior analytics (UEBA), and robust data security controls in a unified platform.
Log360's real-time log analysis and correlation engine detects abnormal file access, unusual data transfers, and suspicious outbound connections that could indicate data exfiltration. With UEBA, it establishes a baseline of normal user activity and flags deviations such as unauthorized file downloads, abnormal access times, or sudden spikes in data movement. These insights help security teams proactively detect and mitigate exfiltration threats before they cause damage.
The platform also offers prebuilt reports and alerts mapped to the MITRE ATT&CK framework, covering techniques like automated exfiltration, exfiltration over alternative protocols, and exfiltration over C2 channels. Whether attackers use DNS tunneling, encrypted HTTPS traffic, or compromised insider credentials to move data out, Log360 identifies these attempts through advanced analytics and anomaly detection.
To strengthen cloud security, Log360 provides cloud activity monitoring that detects unauthorized access, misconfigurations, and anomalous data transfers in services like AWS and Azure. Security teams can leverage custom alerting and automated response mechanisms to block suspicious actions, quarantine affected systems, or trigger incident workflows in response to exfiltration attempts.
FAQs
- How to prevent data exfiltration?
-
Prevent data exfiltration by implementing network monitoring, endpoint security, data loss prevention (DLP) policies, access controls, user awareness training, and behavioral analytics.
- What is the difference between data exfiltration, data leakage, and data breach?
-
- Data exfiltration: A deliberate act of stealing data
- Data leakage: Unintentional exposure of data due to misconfigurations or human error.
- Data breach: A security incident where attackers gain unauthorized access to sensitive data.
What's next?
Stay ahead of data exfiltration threats with Log360
- Data exfiltration definition
- How does data exfiltration occur?
- Data exfiltration techniques and MITRE ATT&CK® Mapping
- Data exfiltration prevention
- Indicators of data exfiltration
- How can ManageEngine Log360 help with detecting data exfiltration?
- FAQs