What is a pass-the-ticket attack?
A pass-the-ticket attack is a type of cyberattack that involves the theft and reuse of authentication credentials called tickets in a Windows Active Directory environment.
When a user logs in to a Windows domain, the authentication process generates a ticket that contains the user's identity and privileges. The ticket is then used to access network resources, such as files, folders, and applications.
In a pass-the-ticket attack, an attacker steals an existing ticket or creates a forged one, and then uses it to gain unauthorized access to network resources without having to authenticate again. The attacker can use this technique to move laterally across a network, gain access to sensitive data, or take control of systems.
Attack flow
- The attacker gains access to a user's machine or a domain controller in a Windows Active Directory environment.
- The attacker steals or creates a Kerberos ticket-granting ticket (TGT) or service ticket associated with a user account or a privileged domain account.
- The attacker then uses the stolen ticket to authenticate and access resources on other machines in the network without needing to know the account's password.
- The attacker can use this access to move laterally through the network, access sensitive data or systems, or perform malicious activities such as installing malware, creating new accounts, and modifying settings.
- The attacker can repeat the process of stealing and reusing tickets to maintain access and control of the network for an extended period.
Detection mechanism:
You can monitor your network by auditing all Kerberos authentication events and reviewing for discrepancies. For example, to investigate pass-the-ticket attacks at endpoints, carry out the following steps:
- Check for the current logon sessions for that system.
- Inspect the Kerberos ticket associated with that session.
- Check for Kerberos tickets that do not match.
During legitimate authentication to the domain, the following event IDs can be found in this order:
4768 – A Kerberos authentication ticket (TGT) was requested
4769 – A Kerberos service ticket was requested
4770 – A Kerberos service ticket was renewed
If an attacker targets the Kerberos Key Distribution Center and takes control of the KRBTGT account, they essentially have an all-access pass, also known as a golden ticket. If a request is being made through a golden ticket, no request for a TGT would be made. This implies that any authentications that log only event ID 4769 and event ID 4770 are an indication of the presence of a golden ticket.
Detecting and mitigating pass-the-ticket attacks using Log360
Learn how to set up Correlation Rules, alerts, and incident workflows, and customize them to detect and remediate pass-the-ticket attacks.
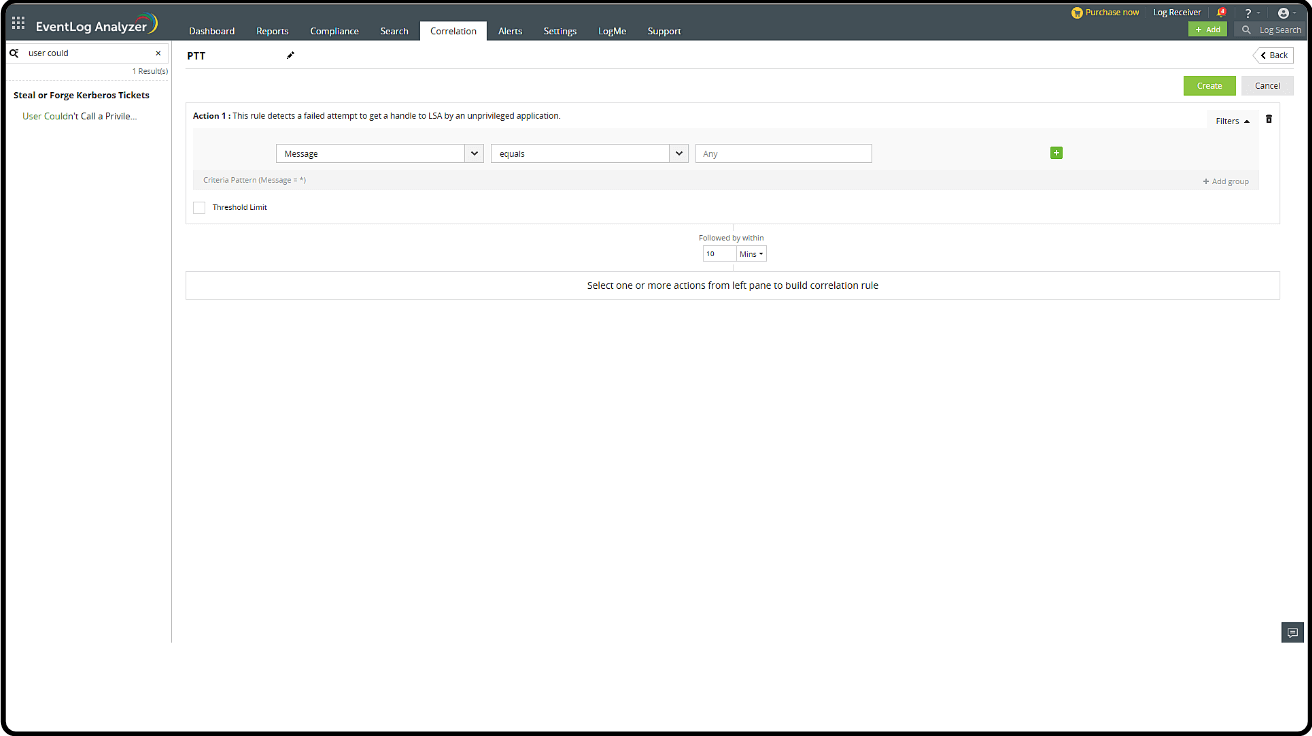
Correlation
Steal or Forge Kerberos Tickets - User Couldn't Call a Privileged Service 'LsaRegisterLogonProcess'
Related Event ID
4673 — A privileged service was called
Detecting
You can detect a pass-the-ticket attack using either a MITRE ATT&CK® Correlation Rule or MITRE ATT&CK Alert Profile.
Creating a Correlation Rule
- Go to the Log360 console > SIEM > Correlation and click Manage Rule in the top-right corner.
- Click Create Correlation Rule.
- Select the Mitre ATT&CK TTP(S) section from the left drop-down box.
- Search for User couldn't call a privileged service.
- Click Create.
Mitigation
The mitigation process includes:
1. Creating an Alert Profile with the Correlation Rule
2. Activating a Workflow for the Alert Profile
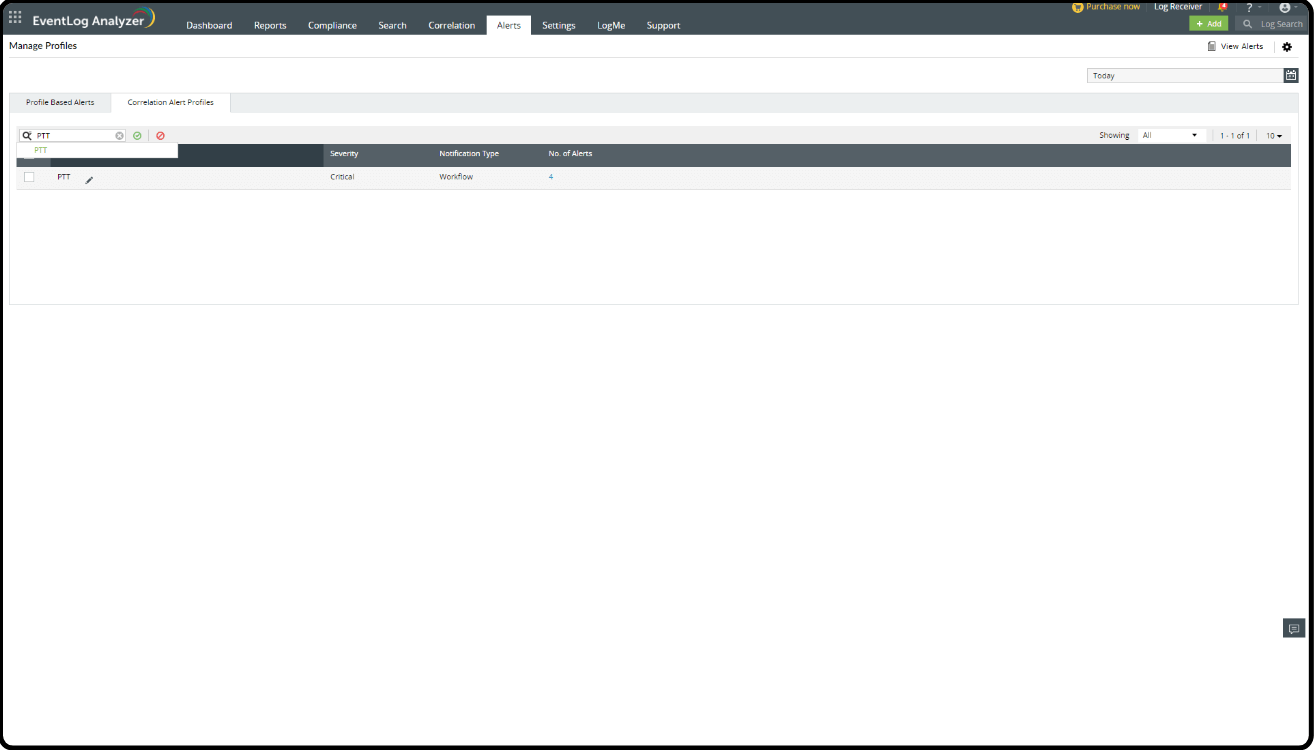
Creating an Alert Profile:
- Go to the Log360 console > SIEM > Alerts.
- Click the settings icon in the top-right corner and select Manage Profiles.
- Under Manage Profiles, select Correlation Alert Profiles. Then, click the search icon and select PTT (the Correlation Rule name).
- Click Configure.

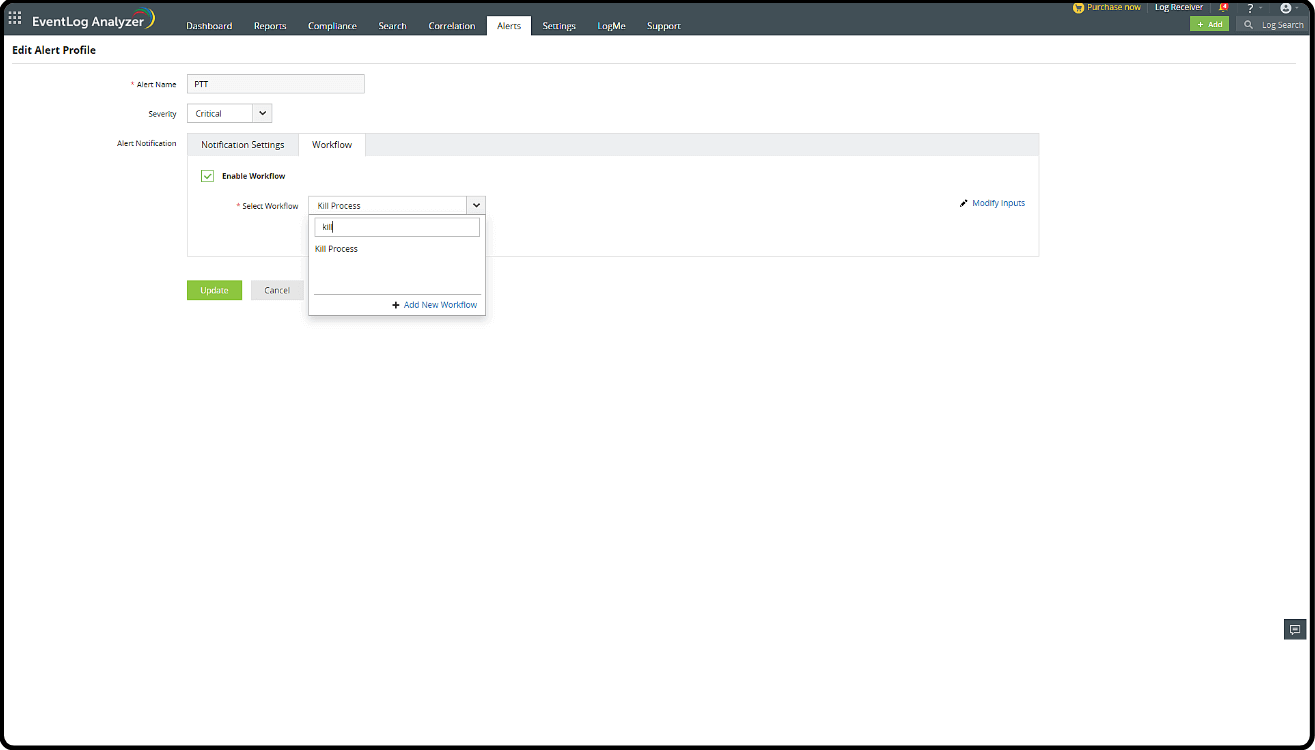
1. Activating a Workflow
- In the Alert Profile, select Workflow next to the Notification Settings.
- Check Enable Workflow and select a suitable action from the list of options, like Disable Computer, Log Off and Disable User, or Kill Process.
- Click Add New Workflow to create a custom Workflow. You can explore the list of Windows actions and Active Directory actions to construct a new flow of incident responses.
2. Adding a Workflow
- Add the Workflow in the Alert Profile.
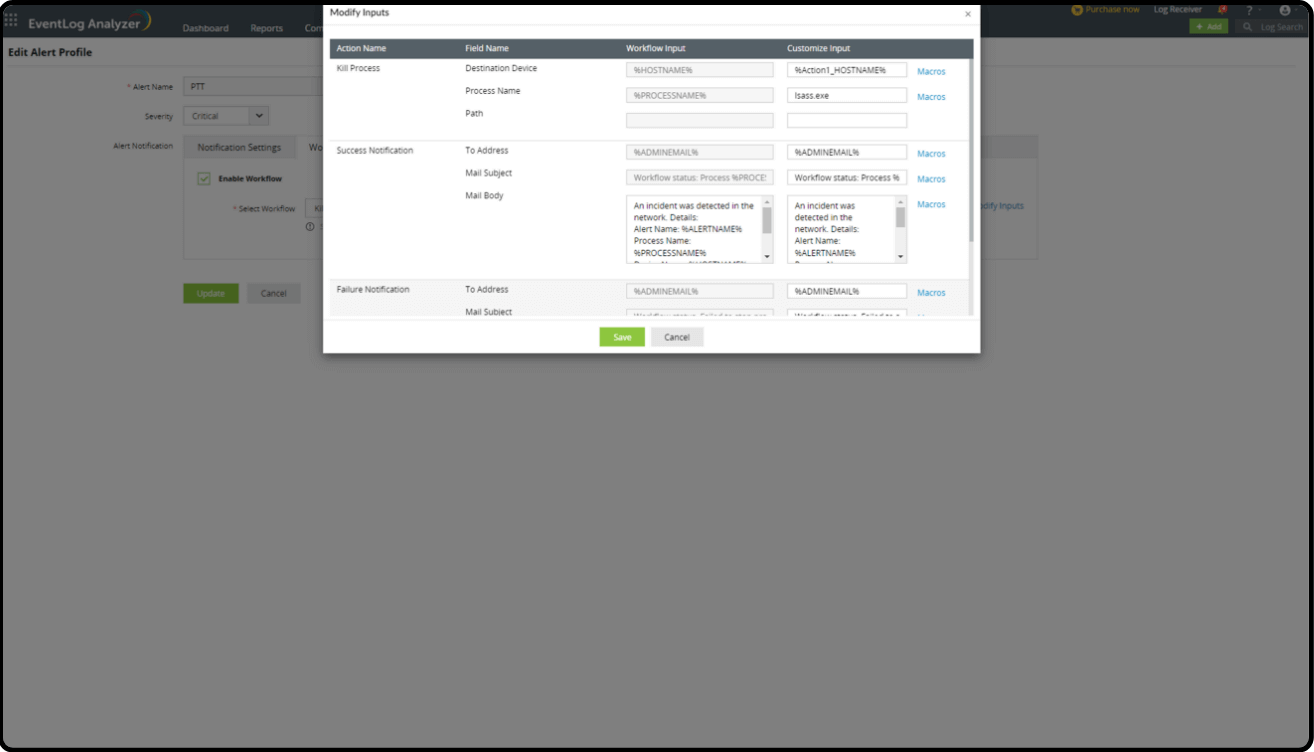
- Select Modify Inputs if there are any fields that need to be modified.
- Once the fields are updated, click Save and Update on the main page.
3. Creating an Alert Profile
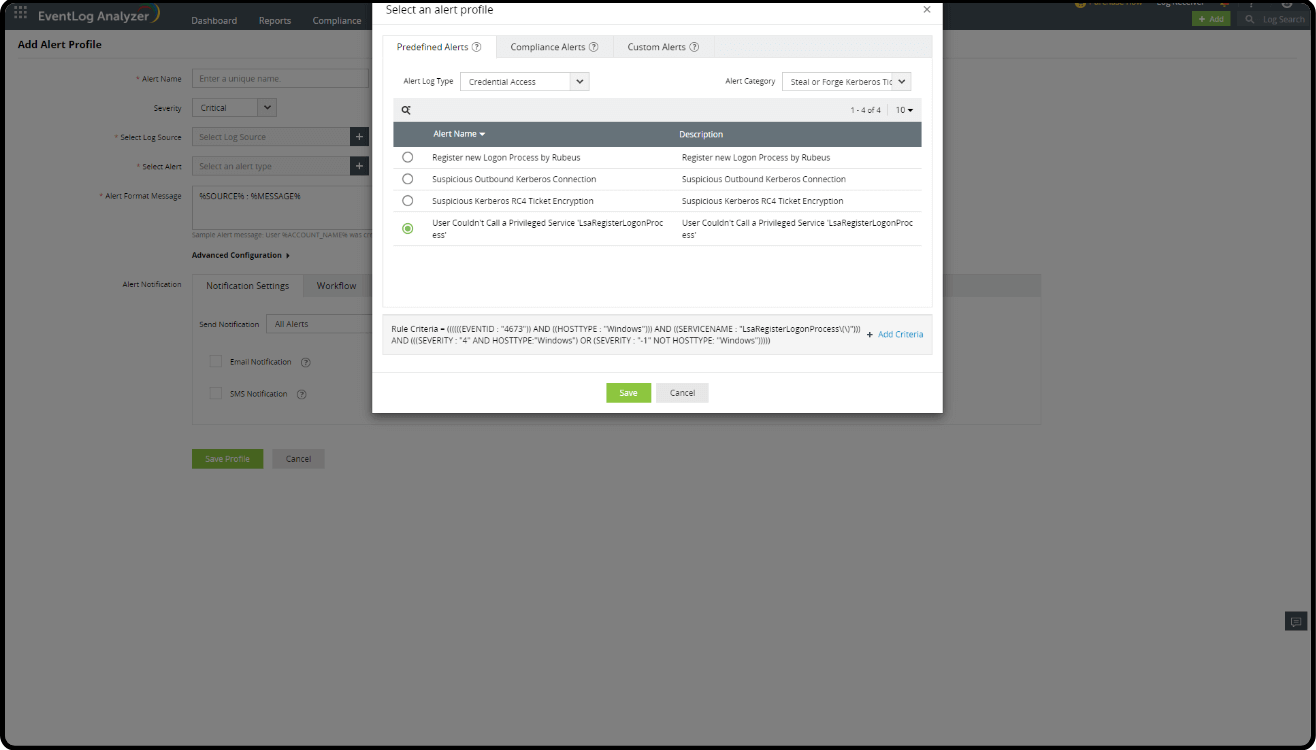
- Go to the Log360 console > SIEM > Alerts > click Add Alert Profile in the top-right corner.
- Click the Select Alert field.
- Search for Credential Access in Alert Log Type.
- Search for User couldn't call a privileged service in the search field and select it.
- Click Save.
Predefined reports
- Go to the Log360 console > select SIEM > Reports.
- Select Mitre ATT&CK from the drop-down box in the top-left pane.
- Select Credential Access > Steal or Forge Kerberos Tickets.
- Select the User Couldn't Call a Privileged Service 'LsaRegisterLogonProcess' report.
What's next?
Implement defensive strategies and incident response measures using the advanced security features of Log360.
- What is a pass-the-ticket attack?
- Attack flow
- Detection Mechanism
- Detecting and mitigating pass-the-ticket attacks using Log360