- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
Understanding FIDO2 and passkeys
FIDO2 authentication is an open authentication standard developed by the FIDO Alliance, an industry consortium that aims to reduce reliance on passwords and improve the overall security of online authentication.
FIDO2 utilizes public key cryptographic credentials, also known as FIDO passkeys, to ensure interoperability with various vendors' hardware, mobile authenticators, and biometric authentication methods, including facial recognition, on diverse browsers and operating systems. This enables passwordless authentication, facilitating smoother logins to numerous web services.
FIDO2 passwordless authentication and phishing-resistant MFA
FIDO2 eliminates passwords and replaces them with native authentication mechanisms on users' devices, like Windows Hello and Apple TouchID, and portable security keys.
Alongside its ability to eliminate passwords, FIDO2 is recognized for its robust security standing, and here's why: All communication between the parties involved in FIDO2 authentication is done using public key cryptography. That is, instead of communicating the actual user-entered authentication secret—such as a PIN, an OTP, or biometric information—to the authentication server, a FIDO passkey (a mathematically generated key corresponding to the secret) is communicated. Therefore, user credentials are not shared between services. Even if one service is compromised, the credentials cannot be used to access other services, making FIDO2 authentication resistant to phishing, replay, and manipulator-in-the-middle (MITM) attacks.
This makes the FIDO login experience a secure, user-friendly, cost-effective, and more resilient substitute for traditional password-based logins.
How does FIDO2 authentication work?
FIDO2 works using two open standards—the Client to Authenticator Protocol (CTAP) and the W3C standard WebAuthn. These work together to provide passwordless authentication and MFA.
- WebAuthn: This is a standard web API built into browsers. It provides an interface to manage and create public keys and communicate with CTAP1 and CTAP2 authenticators.
- CTAP1: This provides the second-factor authentication experience, which requires users to connect security devices to access an online service.
- CTAP2: This allows an authenticator to be used for both the first and second authentication factors and provides users with passwordless authentication and MFA.
Here's a breakdown of the FIDO authentication process using FIDO passkeys:
- The authenticator generates an asymmetric key pair, also known as FIDO passkeys, and sends the public key to the server during registration.
- The user performs local verification using biometrics, PIN, or a security key to unlock the private key.
- The server stores the public key and links it to the user’s account.
- During logins, the server issues a cryptographic challenge to the client.
- The authenticator signs the challenge with the private key, and the server verifies it using the stored public key to grant access.
FIDO vs FIDO2
"FIDO" is a generic term that includes different protocols. The first iteration, FIDO 1.0, was released back in 2014 and aimed to enable passwordless authentication. However, it lacked standardization, which led to the launch of FIDO2 in 2018. Let's see how each of FIDO's protocols work:
- Universal Authentication Framework (UAF): The UAF allows online services to offer passwordless logins using local methods like biometrics or PINs. During registration, a key pair is created—the private key stays on the device, and the public key is sent to the server. For logins, the user verifies locally to unlock the private key, which signs a challenge the server verifies to grant access without a password.
- Universal Second Factor (U2F): U2F, currently known as CTAP1 in FIDO2, acts as a complement to traditional password logins and adds an additional factor with something you have, like security devices (USB devices and key fobs). During login, the user enters their password, and the service sends a challenge to the registered security device. The device proves its possession of the private key and sends the signed challenge to the online service, which grants the user access.
- FIDO2: This is the latest protocol and works with two open standards—the Client to Authenticator Protocol and the W3C standard WebAuthn. FIDO2 includes additional security features, such as domain association and runtime checks, which help prevent phishing attacks by ensuring FIDO passkeys cannot be replayed or redirected to unauthorized domains.
Implementing FIDO2-based passkeys authentication using ADSelfService Plus
ManageEngine ADSelfService Plus supports FIDO2 authentication to secure access to cloud applications, OWA logins, and more. Using the WebAuthn API, ADSelfService Plus provides secure and customizable FIDO2 authentication, supporting both platform and roaming FIDO2 authenticators.
Customizable configuration
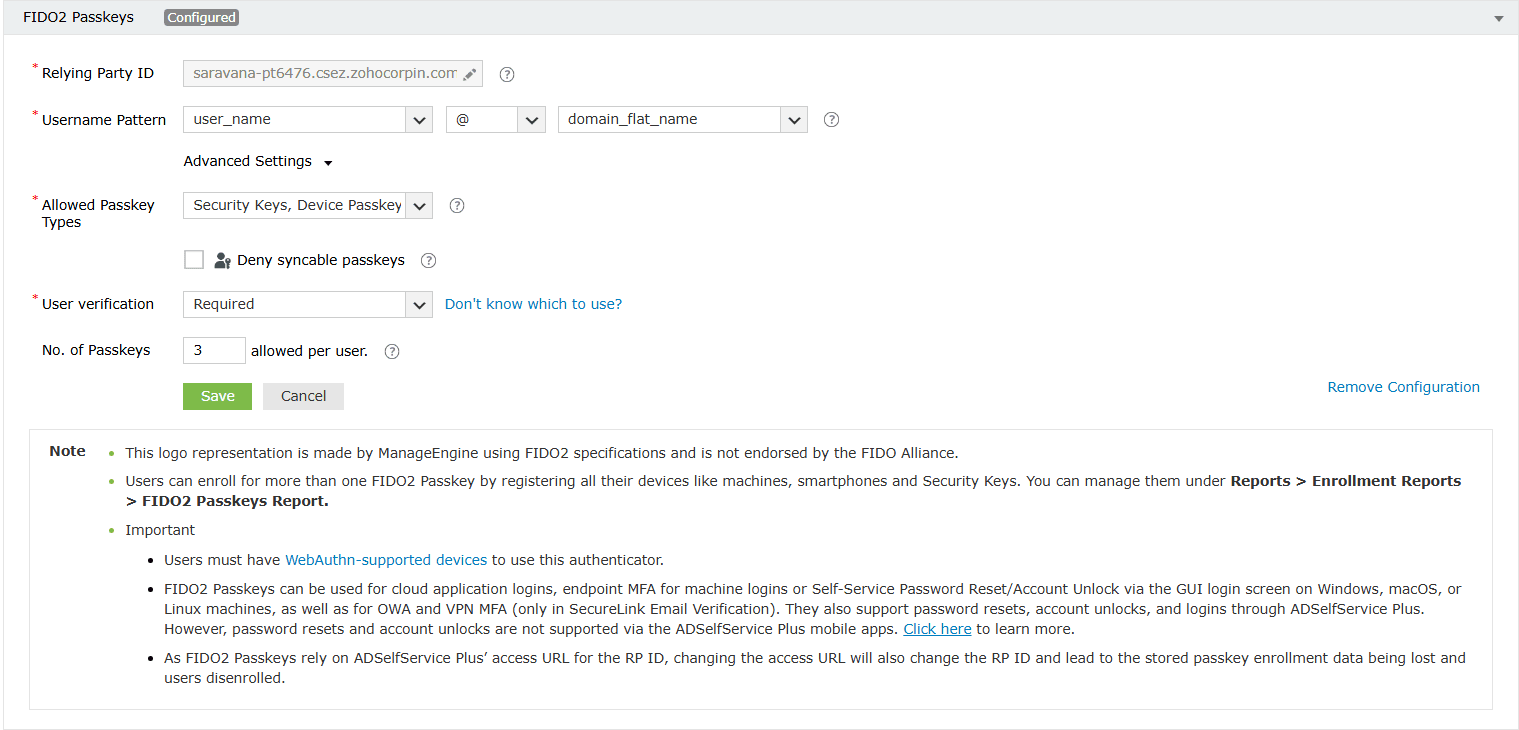
Configure your preferred username pattern.
Choose whether you want users to enroll using security keys, device passkeys, or both.
Choose how many credentials users are allowed to enroll for FIDO2 authentication.
Comprehensive reports
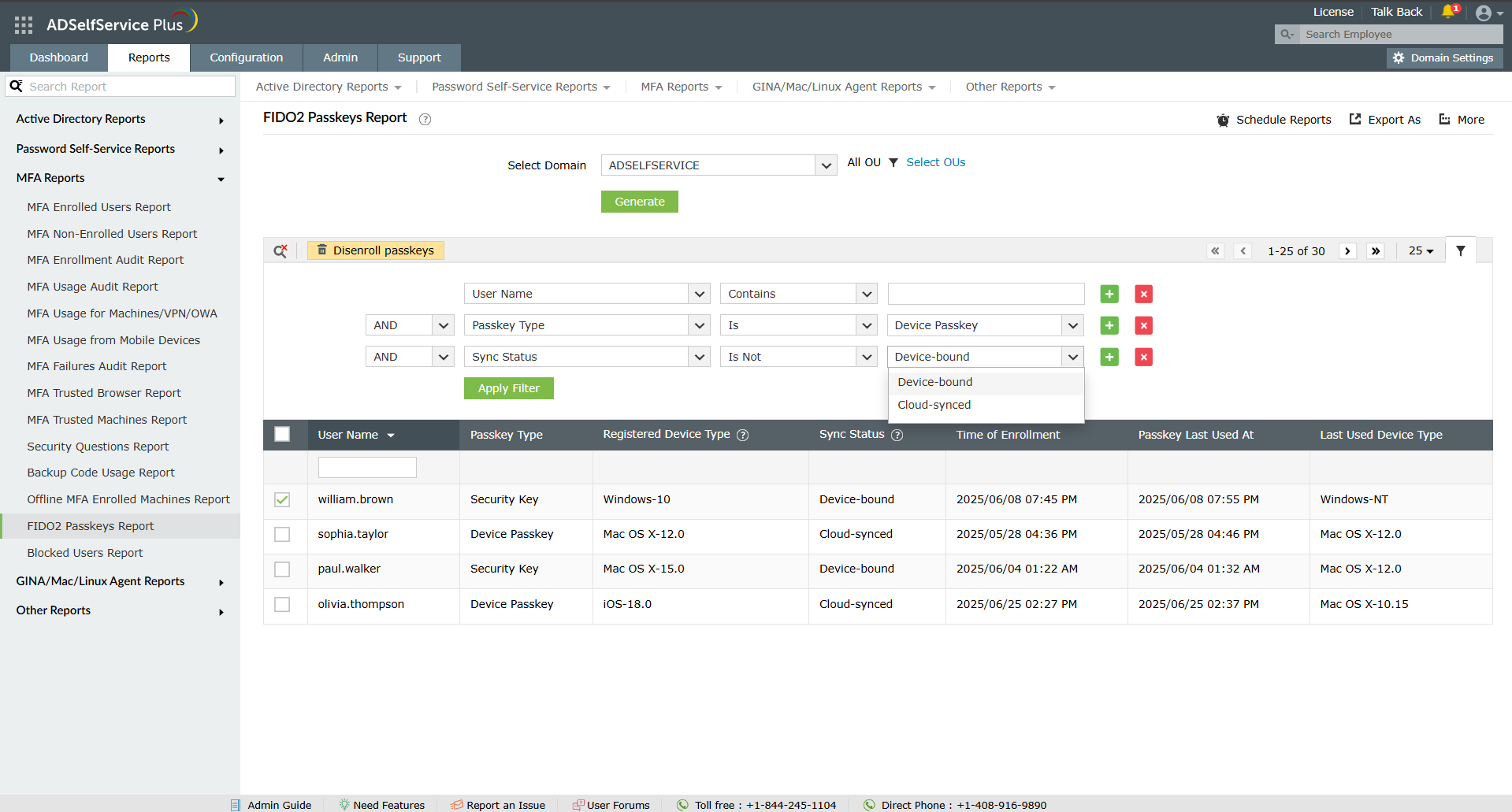
Generate comprehensive reports on users' FIDO2 enrollment status.
Instantly disenroll FIDO2 credentials for users upon detecting suspicious activities.
Employ filters to effortlessly locate specific users within a large pool of records.
Easy enrollment
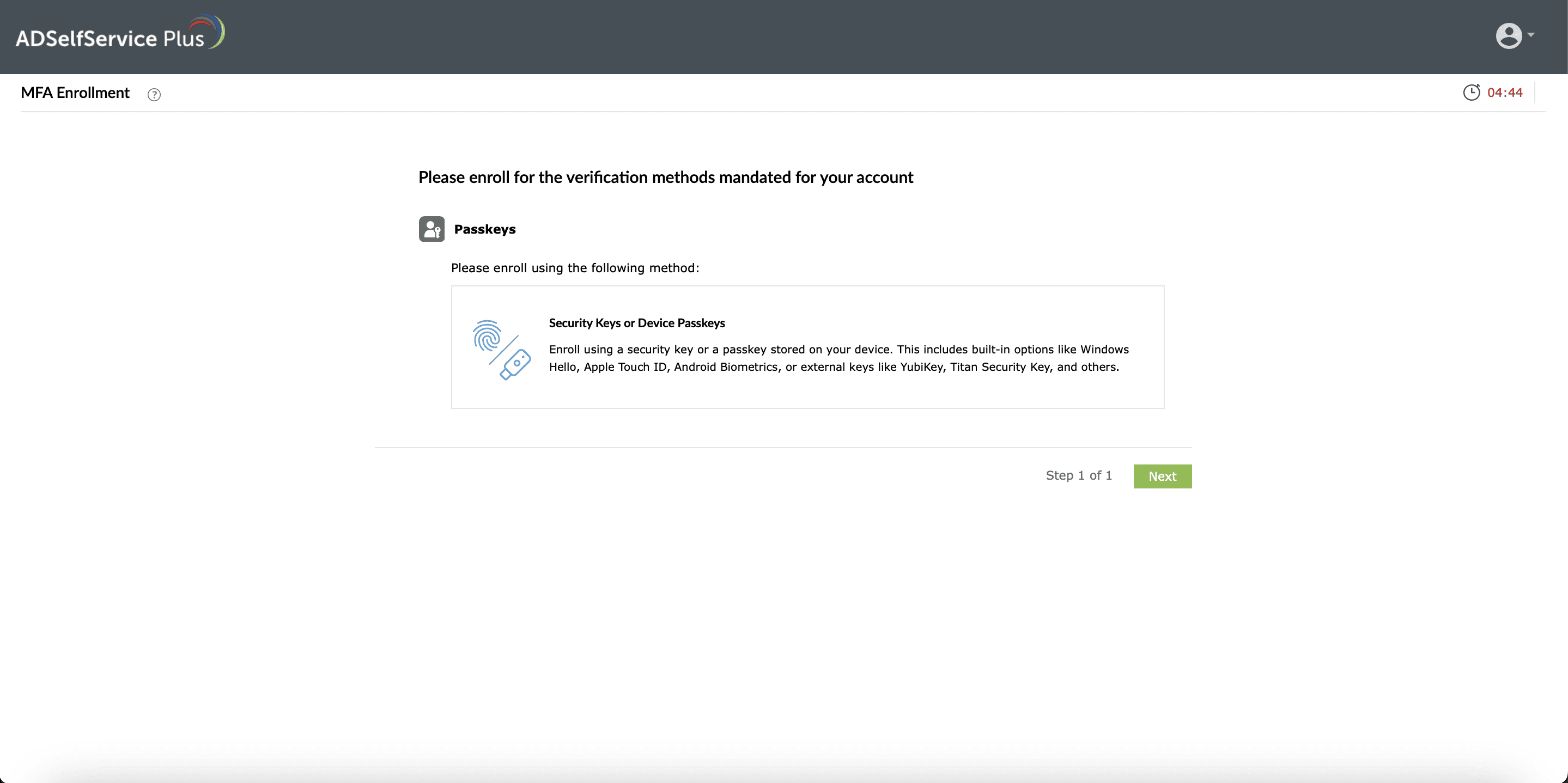
Provide a simple, user-friendly console for hassle-free FIDO2 enrollment and authentication for your users.
FIDO2 authentication methods supported by ADSelfService Plus
ADSelfService Plus supports both platform and roaming FIDO2 authentication methods. Platform authenticators are native to a computer or mobile device, and roaming authenticators are portable and can be used for identity verification on any device. The following authentication methods are supported by ADSelfService Plus:
- Device passkeys: Built-in authenticators native to the device and controlled by the operating system, such as Windows Hello, Apple TouchID and Face ID, and Android Biometrics.
- Security keys: FIDO2- and U2F-compliant hardware security keys like YubiKey, and Google Titan.
Benefits of FIDO2 authentication with ADSelfService Plus
- No more passwords
FIDO2 replaces passwords with secure, device-based authentication methods, shielding users from password-related cyberthreats.
- No sharing of user secrets
User secrets are translated into encrypted keys using public key cryptography and are not exposed to the network.
- Phishing resistance
Phishing, replay, and MITM attacks are repelled since attackers cannot obtain user credentials over the network.
- Support for multiple credentials
Using ADSelfService Plus, users can enroll up to three FIDO2 passkeys corresponding to different devices and platforms.
- Customizable FIDO MFA
ADSelfService Plus provides customizable configuration controls for FIDO2, offering both single- and two-factor authentication options to protect sensitive resources.
- Compliance with regulatory standards
Deploying FIDO2 authentication with ADSelfService Plus ensures compliance with regulatory standards such as the NIST Cybersecurity Framework, HIPAA, the PCI DSS, and the PSD2.
FAQs
A FIDO passkey is a cryptographic key pair created during registration and safely kept on a user's device. The public key is kept on the server, while the private key is always on the device. The FIDO passkey is used to sign a challenge during login, confirming the user's identity without sending any confidential information over the network. FIDO passkeys help prevent phishing and enable passwordless logins
FIDO stands for Fast Identity Online, a passwordless login method that uses biometrics like your fingerprint or face scan, or a physical security key like a USB stick instead of passwords. It is a set of open, standardized protocols developed by the FIDO Alliance designed to reduce reliance on vulnerable, shared secrets.
Passwordless authentication verifies a user's identity using something they have (like a phone with a push notification or a security key) or something they are (like a fingerprint or face scan), instead of a password. This relies on cryptographic keys or one-time codes to establish trust. Passwordless authentication helps prevent common password-based cyberattacks like phishing and credential stuffing while also relieving users of password fatigue.
A FIDO key, also known as a FIDO security key or a FIDO token, is a physical device that provides secure authentication for online services. It works using public-key cryptography to verify your identity. Instead of entering a password, a user can simply plug in the FIDO key, tap a button, or use biometrics to confirm your login. This method is highly secure because your private key never leaves the device, making it extremely difficult for attackers to steal your credentials through phishing or malware.
Highlights of ADSelfService Plus
Password self-service
Unburden Windows AD users from lengthy help desk calls by empowering them with self-service password reset and account unlock capabilities.
Multi-factor authentication
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, OWA, and RDP logins.
One identity with single sign-on
Get seamless one-click access to more than 100 cloud applications. With enterprise single sign-on (SSO), users can access all their cloud applications using their Windows AD credentials.
Password and account expiry notifications
Notify Windows AD users of their impending password and account expiry via email and SMS notifications.
Password synchronization
Synchronize Windows AD user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Password policy enforcer
Strong passwords resist various hacking threats. Enforce Windows AD users to adhere to compliant passwords by displaying password complexity requirements.










