- Tips & Tricks
- NIST MFA guidelines
NIST MFA guidelines
The password guidelines laid down by the National Institute of Standards and Technology (NIST) have been helping organizations worldwide to strengthen end users' passwords since 2014. In its latest revisions, NIST has been drafting new identity security rules that focus more on multi-factor authentication (MFA).
Are complex passwords alone enough?
A study on AI password cracking conducted by Home Security Heroes, a cybersecurity firm, found that AI could crack a password of seven characters containing numbers, uppercase letters, and lowercase letters in just 42 seconds.
MFA effectively defends against today's cyberattacks in a way that even complex passwords containing a variety of symbols and numbers cannot. Many organizations are streamlining their cybersecurity efforts by switching to NIST's user-friendly and strongly encrypted MFA framework.
NIST MFA recommendations—A detailed overview
NIST SP 800-63B Section 4 classifies authentication mechanisms into three categories and calls them Authenticator Assurance Levels (AAL): AAL1, AAL2, and AAL3. This classification is done based on the strength of the authentication mechanism and, therefore, its reliability or trustworthiness. So, as defined by NIST, AAL1 authentication mechanisms have some reliability, AAL2 authentication mechanisms have high reliability, and AAL3 authenticators have very high reliability.
Authenticator Assurance Level 1
AAL1 authentication mechanisms require a single authentication factor, and the permitted authenticators are as follows:
- Memorized secret
- Look-up secret
- Out-of-band devices
- Single-factor one-time password (OTP) device
- Multi-factor OTP device
- Single-factor cryptographic software
- Single-factor cryptographic device
- Multi-factor cryptographic software
- Multi-factor cryptographic device
NIST requires all AAL1 authentication mechanisms using out-of-band authenticators to communicate authentication information between the parties involved via a secure channel. Using a secure channel resists man-in-the-middle (MITM) attacks and adds credibility to the authentication mechanism. All cryptographic authenticators that are classified under AAL1 should employ approved cryptographic techniques. FIPS 140 Level 1 validation is required for the AAL1 authentication mechanisms that are used by government agencies.
What is out-of-band authentication?
In out-of-band authentication (OOBA), the secondary verification method uses a separate communication channel to authenticate a user. Examples of OOBA include push notifications, QR codes, voice authentication, and SMS OTPs.
When the endpoint that is running an AAL1 software-based authenticator gets compromised, the authentication software should attempt to detect the compromise and halt the authentication process. In AAL1, users must be reauthenticated at least once every 30 days, regardless of their session activity. After 30 days, the session must be terminated and the user must be logged out.
Authenticator Assurance Level 2
AAL2 authentication mechanisms are required to have either a multi-factor authenticator or a combination of two single-factor authenticators. The permitted multi-factor authenticators are:
- Multi-factor OTP device.
- Multi-factor cryptographic software.
- Multi-factor cryptographic device.
AAL2 authentication mechanisms that have a combination of two single-factor authenticators should mandatorily include one knowledge-based authenticator (something you know) along with any of the following possession-based authenticators (something you have):
- Look-up secret
- Out-of-band device
- Single-factor OTP device
- Single-factor cryptographic software
- Single-factor cryptographic device
All AAL2 authentication mechanisms involving out-of-band authenticators should communicate authentication information via a secure channel to defend against MITM attacks. All cryptographic authenticators that are classified under AAL2 should employ approved cryptographic techniques. FIPS 140 Level 1 validation is required for the AAL2 authentication mechanisms that are used by government agencies.
When the endpoint that is running an AAL2 software-based authenticator gets compromised, the authentication software should attempt to detect the compromise, and the authentication process should be stopped in such cases. Of the two authenticators used in AAL2, at least one must be replay-resistant and explicitly demonstrate the user's authentication intent.
What is a replay-resistant authenticator?
A replay-resistant authenticator makes it impossible to record and replay the authentication message from a previous authentication attempt in order to make the current authentication attempt successful.
A password or memorized secret, for instance, is not considered replay-resistant, since it can be recorded and reused multiple times to achieve a successful authentication result during every attempt. Some examples of replay-resistant authenticators are, TOTPs, cryptographic authenticators, and look-up secrets.
What is authentication intent?
Authentication intent is the act of verifying a user's underlying intention of the authentication process. This is done to distinguish a legitimate authentication request from a fraudulent one. Authentication intent is demonstrated when an authenticator requires an explicit response from the user requesting authentication.
In AAL2, users must be reauthenticated in either of these two scenarios: at least once every 12 hours or after 30 minutes of inactivity. If any of these limits is reached, the session must be terminated and the user must be logged out. During reauthentication before a session limit is reached, just a memorized secret or biometric, in addition to the still-valid session secret, is sufficient to authenticate the user. Verifiers are allowed to prompt users to initiate activity just before the inactivity timeout.
Authentication Assurance Level 3
AAL3 authentication mechanisms, which carry increased confidence when compared to the other assurance levels, require the use of a combination of authenticators. The possible combinations are as follows:
- Multi-factor cryptographic device
- Single-factor cryptographic device and a memorized secret
- Multi-factor OTP device (software or hardware) and a single-factor cryptographic device
- Multi-factor OTP device (hardware only) and single-factor cryptographic software
- Single-factor OTP device (hardware only) and a multi-factor cryptographic software authenticator
- Single-factor OTP device (hardware only), a single-factor cryptographic software authenticator, and a memorized secret
All AAL3 authentication mechanisms should communicate authentication information via a secure channel to defend against MITM attacks and to improve credibility. All AAL3 hardware cryptographic multi-factor authenticators should be validated at FIPS 140 Level 2 or higher, with a physical security of at least FIPS 140 Level 3. All AAL3 single-factor authenticators used should be validated at FIPS 140 Level 1 or higher, with a physical security of at least FIPS 140 Level 3.
Of the authenticators used in AAL3, at least one of them should be verifier-impersonation-resistant and replay-resistant. All AAL3 hardware-based authenticators and verifiers should resist side-channel attacks. Attackers use side-channel attacks to collect information about authentication processes by observing miscellaneous system characteristics such as execution time, power consumed, and memory consumed.
What is a verifier-impersonation-resistant authenticator?
A verifier-impersonation-resistant authenticatior is an authenticator that should withstand phishing attacks by employing relevant phishing-resistant authentication technologies.
NIST also requires that at least one of the AAL3 authenticators must be verifier-compromise-resistant.
What is a verifier-compromise-resistant authenticator?
Authenticators that store a copy of the authentication message or secret for comparison against the user-entered secret are considered susceptible to compromise and are not verifier-compromise-resistant. A verifier-compromise-resistant authenticator, however, is expected to store the authentication secret in hashed form or store a public key corresponding to the subject's private key.
In AAL3, users must be reauthenticated in either of these two scenarios: at least once every 12 hours or if there has been 15 minutes of inactivity. If any of these limits is reached, the session must be terminated and the user must be logged out. During reauthentication, the user must be authenticated with both authentication factors. Verifiers are allowed to prompt users to initiate activity just before the inactivity timeout.
Adhere to NIST-recommended MFA best practices with ADSelfService Plus
ADSelfService Plus, an integrated identity security solution, provides adaptive MFA to secure all your organization's endpoints, like machine (Windows, macOS, and Linux systems) logins and enterprise application logins through SSO, RDPs, VPNs, and OWA. With 19 different authenticators, including biometrics, YubiKey, smart card, and TOTPs, ADSelfService Plus provides comprehensive, NIST-recommended security for your organization.
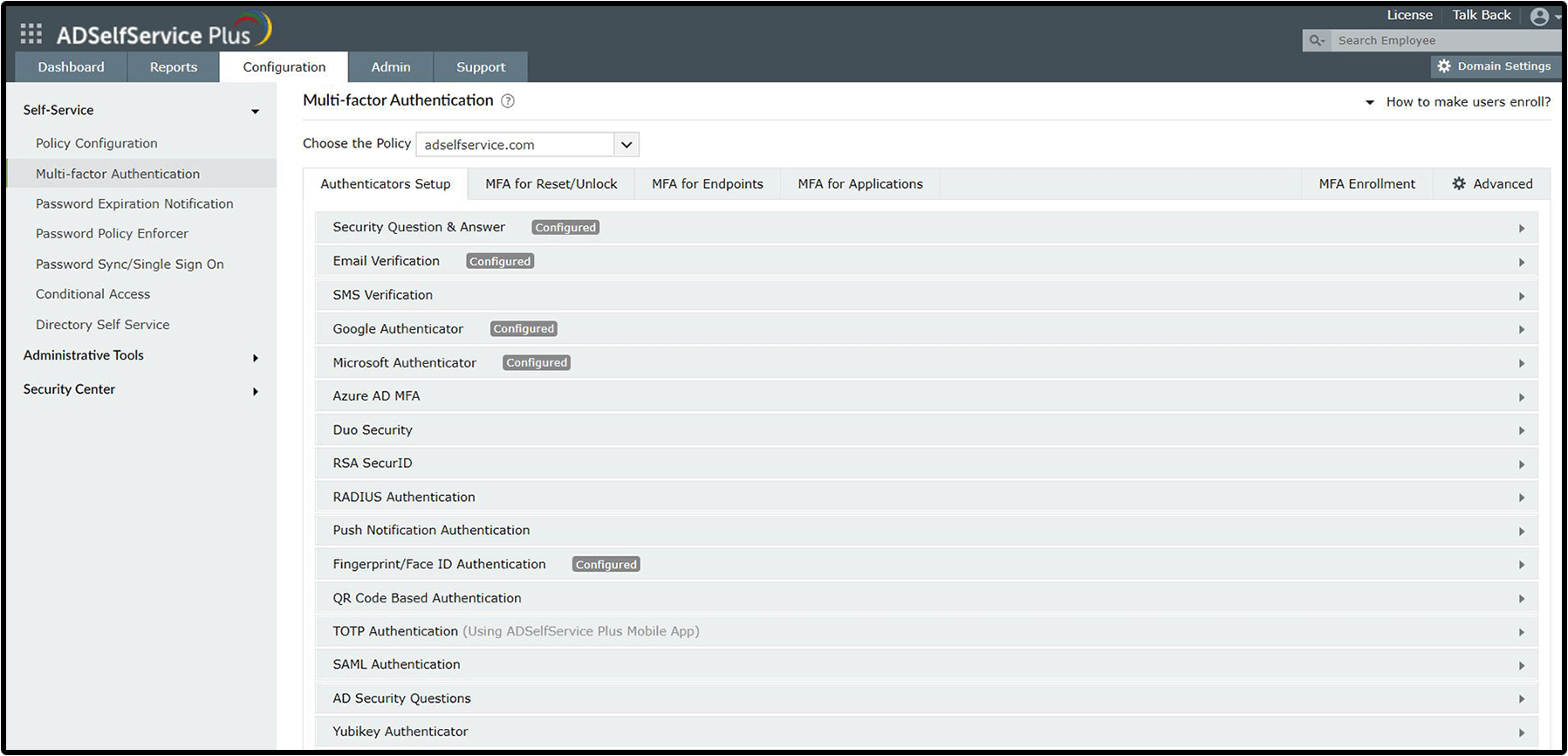
MFA authenticators
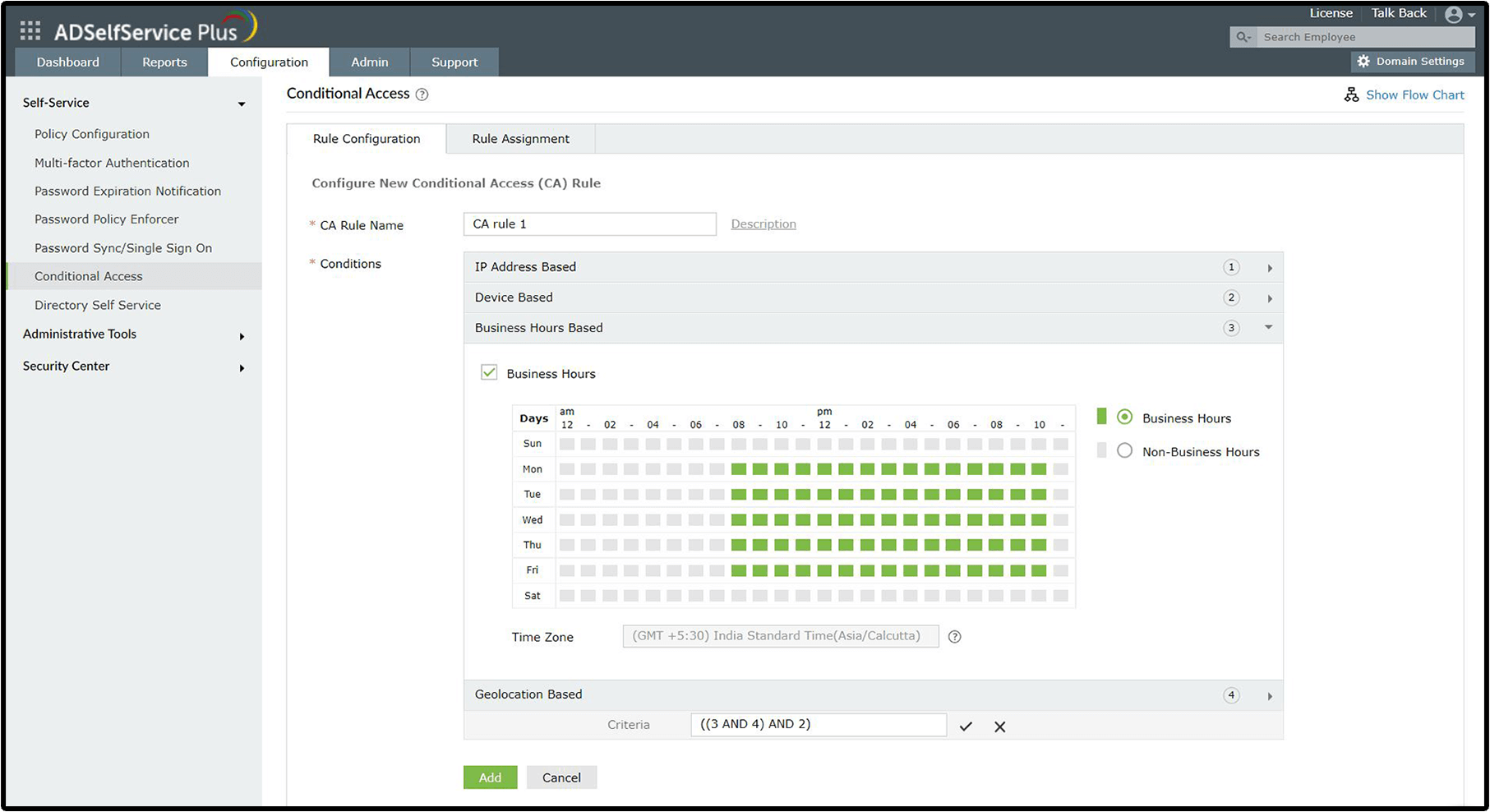
ADSelfService Plus enables IT administrators to configure different authenticators for different users based on their OU, domain, and group memberships. Moreover, you can fine-tune user access conditions based on their IP address, business hours, device used, and geolocation.
Conditional access
ADSelfService Plus' enhanced password policy and MFA features help your organization comply with other regulatory standards aside from NIST, like the PCI DSS, the GDPR, HIPAA, the CJIS, and the Essential Eight.
Secure and streamline your company's MFA policies to match NIST-recommended standards
Download nowYou may also like
ADSelfService Plus also supports
-
Adaptive MFA
Enable context-based MFA with 19 different authentication factors for endpoint and application logins.
Learn more -
Enterprise single sign-on
Allow users to access all enterprise applications with a single, secure authentication flow.
Learn more -
Remote work enablement
Enhance remote work with cached credential updates, secure logins, and mobile password management.
Learn more -
Powerful integrations
Establish an efficient and secure IT environment through integration with SIEM, ITSM, and IAM tools.
Learn more -
Enterprise self-service
Delegate profile updates and group subscriptions to end users and monitor these self-service actions with approval workflows.
Learn more -
Zero Trust
Create a Zero Trust environment with advanced identity verification techniques and render your networks impenetrable to threats.
Learn more
Fill this form todownload the solution brief
Thank You!
You'll be receiving the savings report in your inbox shortly.