- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
The need to protect VPN access
VPNs allow users to access various resources while outside the office through a secure tunnel. While this facilitates an uninterrupted workflow for remote employees, it also exposes the organization's network to new cybersecurity concerns.
When a VPN is synced with an organization's AD environment, users are commonly authenticated using only their domain username and password—a method that has proven to be no longer secure. Verizon reports that 81% of data breaches can be linked to compromised passwords. Exposure of VPN credentials can put your entire network at risk of data exposure. Implementing additional layers of security through MFA is an effective way to prevent the dire consequences of credential exposure.
Secure your VPN access with ADSelfService Plus
ManageEngine ADSelfService Plus, an identity security solution, enables you to fortify VPN connections to your organization's networks using adaptive MFA. This involves implementing authentication methods like biometric authentication and one-time passwords (OTPs) during VPN logons in addition to the traditional username and password. Since passwords alone are not enough to log in to the network, ADSelfService Plus renders exposed credentials useless for unauthorized VPN access.
Supported VPN providers
ADSelfService Plus allows admins to secure all RADIUS-supported VPN providers with MFA including:
- Fortinet
- Cisco IPSec
- Cisco AnyConnect
- Windows native VPN
- SonicWall NetExtender
- Pulse
- Check Point Endpoint Connect
- SonicWall Global VPN
- OpenVPN Access Server
- Palo Alto
- Juniper
How MFA for VPNs works
To secure your VPNs using MFA, the VPN server needs to use a Windows Network Policy Server (NPS) to configure RADIUS authentication, and the ADSelfService Plus NPS extension has to be installed in the NPS. This extension mediates between the NPS and ADSelfService Plus to enable MFA during VPN connections. Once these requirements are fulfilled, the process shown below takes place during a VPN login:
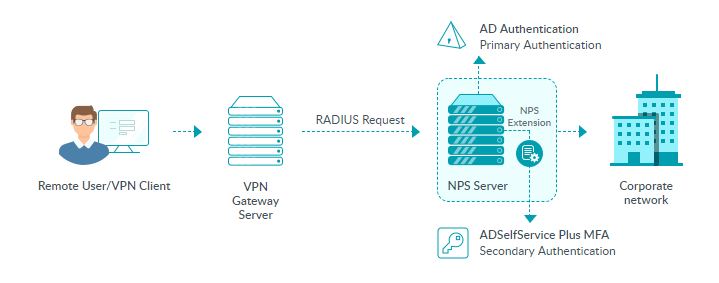
- A user tries to establish a VPN connection by providing their username and password to the VPN server.
- The VPN server sends the authentication request to the NPS where the ADSelfService Plus’ NPS extension is installed.
- If the username and password combination is correct, the NPS extension contacts the ADSelfService Plus server and raises a request for a second factor of authentication.
- The user performs authentication through the method configured by the administrator. The result of the authentication is sent to the NPS extension in the NPS.
- If the authentication is successful, the NPS conveys this to the VPN server.
The user is now granted access to the VPN server and an encrypted tunnel is established with the internal network.
Supported VPN authentication methods
ADSelfService Plus provides 20 authenticators for VPN MFA and gives flexibility in configuration based on your organization's VPN setup. You can choose either VPN-client-based verification or SecureLink-based email verification for VPN MFA.
Client-based verification presents users with MFA prompts directly from the VPN client during the login process. The following are the authentication methods you can configure for client-based authentication:
- TOTP authentication
- Microsoft Authenticator
- YubiKey Authenticator
- Zoho OneAuth TOTP
- Push notification authentication
- Biometric authentication
SecureLink-based email verification sends a verification link to users' mailboxes that they need to click to verify their identity. This method supports all authenticators provided by ADSelfService Plus, including those not supported by client-based verification, such as FIDO passkeys and smart card authentication.
ADSelfService Plus enables hassle-free configuration and administration of VPN MFA through:
- Granular configuration: Enable particular authentication methods for users belonging to specific domains, OUs, and groups.
- Real-time audit reports: View detailed reports on VPN login attempts with information like login time and authentication failures.
Benefits of using VPN MFA with ADSelfService Plus
-
Customizable configuration
Apply different authenticators to different sets of users based on their privileges.
-
Achieve regulatory compliance
Meet NIST SP 800-63B, GDPR, HIPAA, NYCRR, FFIEC, and PCI DSS regulation requirements.
-
Prevent credential-based cyberattacks
Prohibit the use of weak passwords, which make your network vulnerable to cyberattacks.
-
Secure endpoints
Use adaptive MFA to secure not just VPN access, but also local and remote machine logins—including MFA for Windows, macOS, and Linux—for complete endpoint security.
Highlights of ADSelfService Plus
Password self-service
Unburden Windows AD users from lengthy help desk calls by empowering them with self-service password reset and account unlock capabilities.
Multi-factor authentication
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, OWA, and RDP logins.
One identity with single sign-on
Get seamless one-click access to more than 100 cloud applications. With enterprise single sign-on (SSO), users can access all their cloud applications using their Windows AD credentials.
Password and account expiry notifications
Notify Windows AD users of their impending password and account expiry via email and SMS notifications.
Password synchronization
Synchronize Windows AD user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Password policy enforcer
Strong passwords resist various hacking threats. Enforce Windows AD users to adhere to compliant passwords by displaying password complexity requirements.










