IT administrators frequently need to check Active Directory password policy settings and complexity requirements to ensure compliance, troubleshoot user access issues, or verify security configurations. Understanding what password policies are currently applied to users and groups is essential for maintaining a secure Active Directory environment.
This can be accomplished through several methods: the native Group Policy Management Console (GPMC), PowerShell, or by utilizing comprehensive password policy enhancer solutions like ManageEngine ADSelfService Plus. Let's explore these different approaches below.
Before diving into the specific methods, it's helpful to understand where to find the password policy in Active Directory and the different locations where these settings are stored:
gpedit.msc on individual computers.Understanding these locations helps administrators quickly navigate to the appropriate configuration area based on their specific requirements.
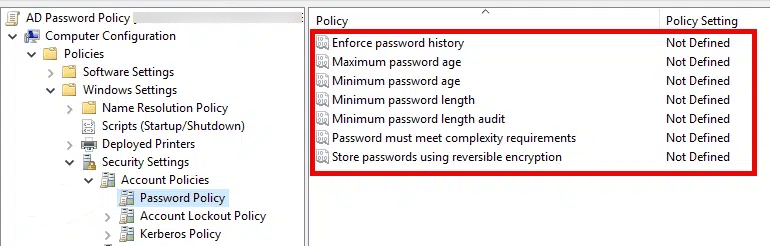
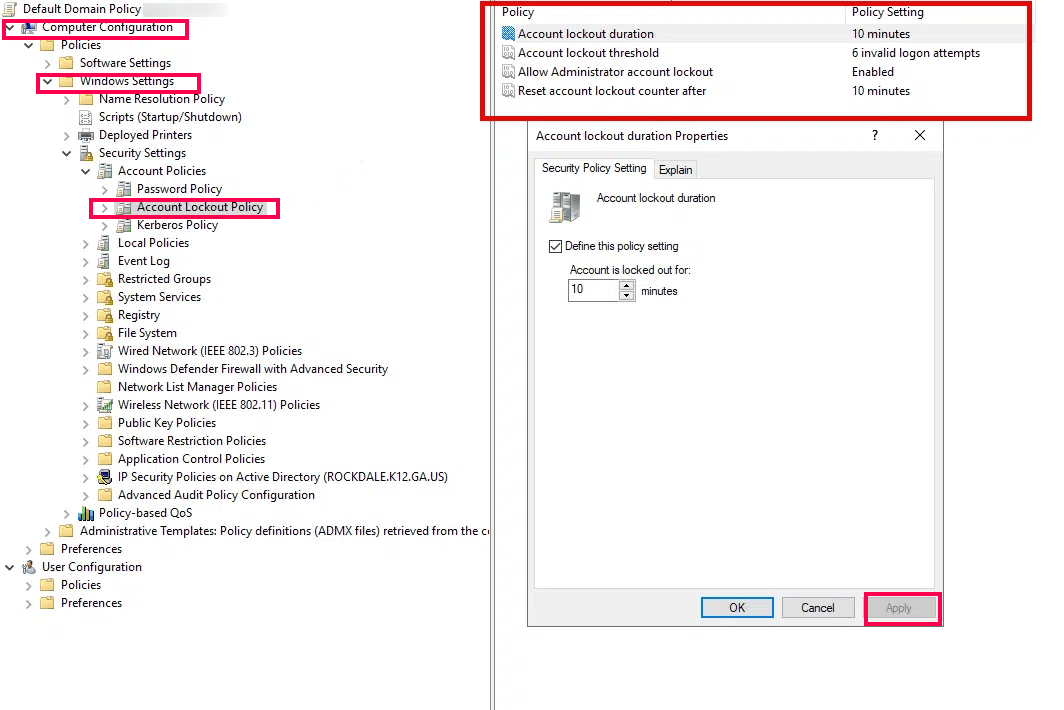
Note: The Group Policy Management Console method above only displays the default domain password policy that applies to all users in the domain. To check FGPPs, you will need to use either the PowerShell methods described below or navigate to Active Directory Administrative Center → System → Password Settings Container. In addition, FGPPs override the default domain password policy for targeted users. Always verify FGPPs using Active Directory Administrative Center or PowerShell.
Before checking Active Directory password policy requirements using PowerShell, please verify that the following prerequisites are satisfied:
The Get-ADDefaultDomainPasswordPolicy and Get-ADFineGrainedPasswordPolicy cmdlets can be used in PowerShell to check the password policy requirements in Active Directory. The former cmdlet displays the default domain password policy, while the latter displays the FGPP governing the user account.
The syntax for both these cmdlets is given below.
# Current (Default) parameter set
Get-ADDefaultDomainPasswordPolicy
[[-Current] <ADCurrentDomainType>]
[-AuthType <ADAuthType>]
[-Credential <PSCredential>]
[-Server <String>]
[<CommonParameters>] # Identity parameter set
Get-ADDefaultDomainPasswordPolicy
[-Identity] <ADDefaultDomainPasswordPolicy>
[-AuthType <ADAuthType>]
[-Credential <PSCredential>]
[-Server <String>]
[<CommonParameters>] # Filter parameter set (Default)
Get-ADFineGrainedPasswordPolicy
-Filter <String>
[-AuthType <ADAuthType>]
[-Credential <PSCredential>]
[-Properties <String[]>]
[-ResultPageSize <Int32>]
[-ResultSetSize <Int32>]
[-SearchBase <String>]
[-SearchScope <ADSearchScope>]
[-Server <String>]
[<CommonParameters>] # Identity parameter set
Get-ADFineGrainedPasswordPolicy
[-Identity] <ADFineGrainedPasswordPolicy>
[-AuthType <ADAuthType>]
[-Credential <PSCredential>]
[-Properties <String[]>]
[-Server <String>]
[<CommonParameters>] # LdapFilter parameter set
Get-ADFineGrainedPasswordPolicy
-LDAPFilter <String>
[-AuthType <ADAuthType>]
[-Credential <PSCredential>]
[-Properties <String[]>]
[-ResultPageSize <Int32>]
[-ResultSetSize <Int32>]
[-SearchBase <String>]
[-SearchScope <ADSearchScope>]
[-Server <String>]
[<CommonParameters>] The following table contains some parameters that can be used along with the Add-ADFineGrainedPasswordPolicySubject cmdlet to check the default Active Directory password policy requirements.
| Parameter | Description |
|---|---|
| -AuthType | Defines the authentication method for connecting to AD. Valid options: Negotiate (default; uses Kerberos or NTLM) or Basic (requires SSL). |
| -Credential | Supplies alternate credentials (PSCredential object from Get-Credential) when running the cmdlet under a different account. |
| -Current | Specifies whether to get the policy from the domain of the currently logged-on user (LoggedOnUser) or from the local computer's domain (LocalComputer). Useful in multi-domain environments. |
| -Identity | Specifies an AD domain object (Distinguished Name, GUID, Security Identifier, or DNS domain name) whose default password policy you want to retrieve. |
| -Server | Specifies which domain controller to query (FQDN, NetBIOS name, or IP). If omitted, the default DC for the logon context is used. |
The following table contains some parameters that can be used along with the Get-ADFineGrainedPasswordPolicy cmdlet to check the applied FGPP.
| Parameter | Description |
|---|---|
| -Identity | Specifies an Active Directory FGPP object by distinguished name, GUID, or name. |
| -Filter | Specifies a query string using PowerShell expression language syntax to retrieve specific policies. |
| -LDAPFilter | Specifies an LDAP query string for filtering policies. |
| -Properties | Specifies properties to retrieve from the server (use * for all properties). |
| -SearchBase | Specifies an Active Directory path (DN) to search under. |
| -SearchScope | Specifies search scope (Base, OneLevel, or Subtree). |
Retrieving the default domain password policy from the current logged on user domain
Get-ADDefaultDomainPasswordPolicy -Current LoggedOnUser
Retrieving the default domain password policy from the current local computer
Get-ADDefaultDomainPasswordPolicy -Current LocalComputer
Retrieve all FGPP in the domain
Get-ADFineGrainedPasswordPolicy -Filter *
Retrieve policies with names containing "admin"
Get-ADFineGrainedPasswordPolicy -Filter "name -like '*admin*'"
For this cmdlet, you can replace the term admin with any search term of your choice to check whether any FGPP containing that term exist.
Although ADSelfService Plus does not provide a direct view of the applied Active Directory password policies, it provides a significant advantage with its ability to enforce granular, customizable password policies tailored to specific organizational requirements. Unlike native AD, the Password Policy Enforcer feature in ADSelfService Plus enables admins to fine-tune password complexity rules, restrict patterns, and integrate advanced checks such as compromised password detection, providing stronger security and enhanced compliance.
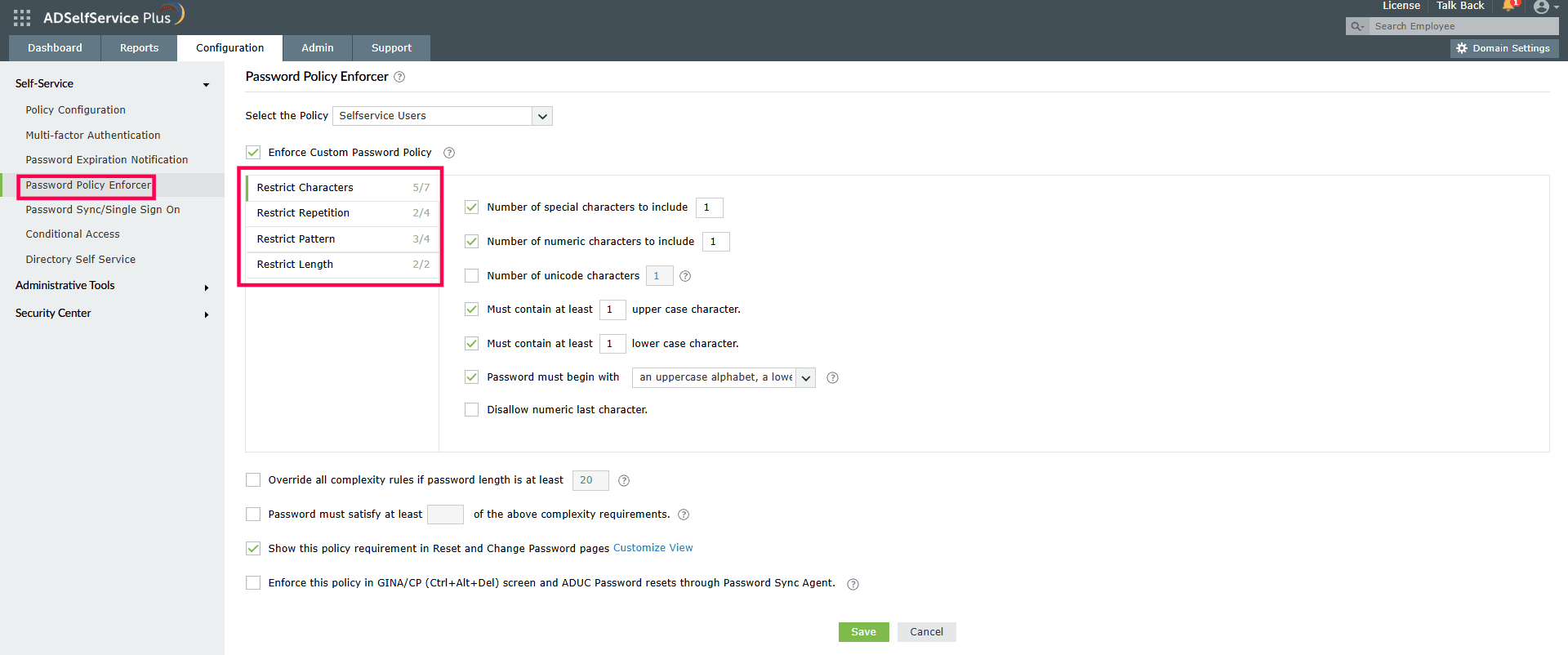
Dynamic password policy enforcement: ADSelfServicePlus enables admins to set custom password rules using the Password Policy Enforcer. Policies enforced through ADSelfService Plus can include restrictions on character types, password length, repetition, patterns, and even dictionary words or palindromes. This goes beyond the native AD capabilities, supporting granular and organization-specific requirements.
Compromised password protection: ADSelfService Plus integrates with Have I Been Pwned to prevent users from selecting passwords exposed in previous breaches, guarding against credential stuffing attacks.
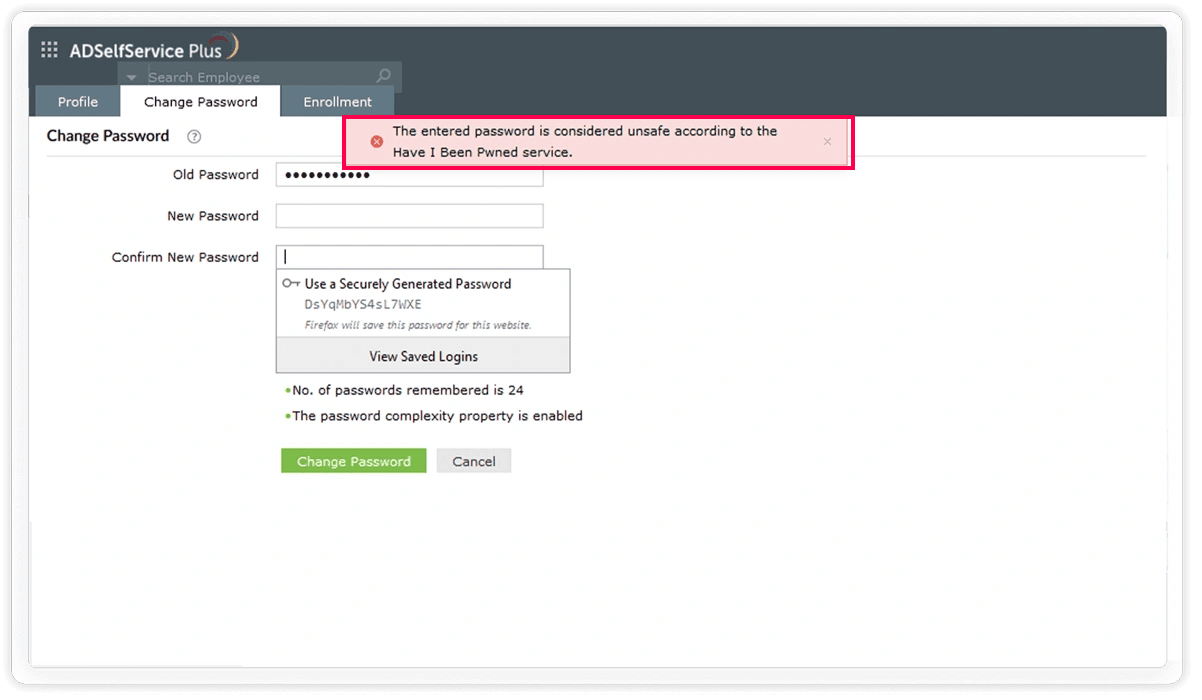
Displaying the current password policy: When a user accesses the password reset or change console, the password policy requirements are displayed. This includes necessary details like minimum length, required character types (uppercase, lowercase, numbers, symbols), and other complexity rules. Users get to see these requirements before they attempt a reset, ensuring compliance and reducing failed password change attempts.
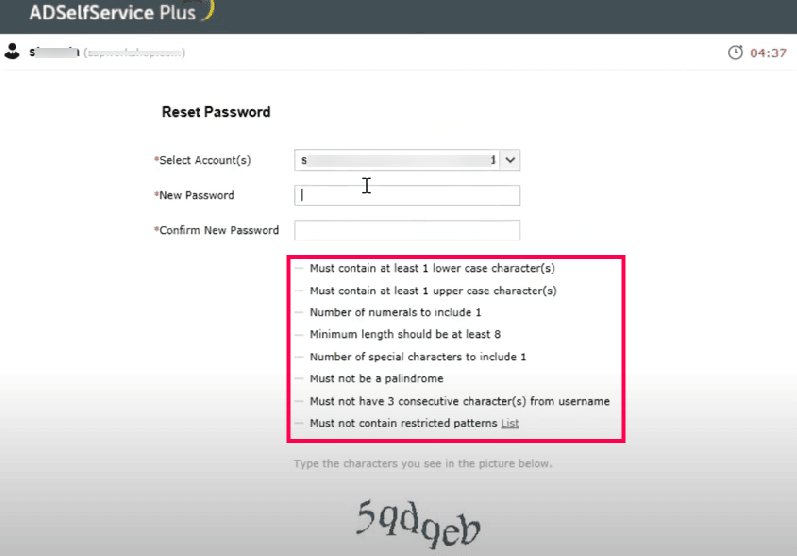
Self-service empowerment: Instead of contacting help desks, users can reset or change their passwords themselves, with real-time checks and guidance to meet policy requirements. This reduces the IT team workload while strengthening security.
While checking Active Directory password policies is essential for maintaining security standards, ADSelfService Plus enhances your password management strategy by addressing common challenges organizations face:
Generate reports to audit users' Active Directory passwords and the self-service actions they perform using consolidated, user-friendly reports. This helps administrators track password policy compliance and identify areas where additional security measures may be needed.
Enable visual feedback on user password strength by employing the Password Strength Analyzer during password creation. This feature provides immediate guidance to help users create passwords that meet both Active Directory requirements and any additional organizational standards.
Present password policy requirements in multiple languages to ensure all users can understand and comply with security standards regardless of their primary language.