- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Windows event logs are an indispensable part of your organization's cybersecurity defense. Manually analyzing Windows event logs is not only time-consuming but also highly error-prone. The sheer volume of data, excessive noise, and complexity of correlating events across multiple systems can quickly overwhelm even experienced IT teams. Moreover, the native Event Viewer’s limited retention capabilities make long-term analysis and forensic investigation nearly impossible.
This is where centralized log management becomes essential. With EventLog analyzer, an advanced event log analysis tool, organizations can:
- Identify suspicious behavior and insider threats: Detect anomalies such as repeated failed login attempts, logons outside business hours, or unusual access patterns that may signal account compromise.
- Gain visibility into user and system activity: Track who did what, when, and where across Windows systems to understand usage patterns and detect deviations.
- Proactively monitor system and application health: Receive alerts on critical events such as disk failures, service crashes, or application errors before they escalate into disruptions.
- Streamline troubleshooting and root cause analysis: Use advanced search and correlation features to quickly drill down into events, identify trends, and reduce mean time to resolution.
What is Windows event log analysis?
Windows event log analysis refers to the process of collecting, parsing, and interpreting event logs generated by the Windows operating system. These logs are essential for identifying system issues, tracking user activity, and detecting suspicious behavior, making them a core component of IT security and operations monitoring.
By performing event log analysis, you can uncover hidden issues, investigate security incidents, and ensure policy compliance, in addition to detecting anomalies in user behavior such as repeated failed login attempts, logins at unusual hours, sudden spikes in file access, or unauthorized privilege escalation. Log management tools like EventLog Analyzer enhance this process with automated log collection, correlation, real-time alerting, and in-depth reporting, enabling faster and more effective decision-making.
Explore our Windows logging guide for expert tips and best practices on log management.
How EventLog Analyzer simplifies Windows event log analysis
Centralized event log collection
EventLog Analyzer automates the complex task of collecting logs from diverse Windows devices and other network sources. Whether you're dealing with workstations, servers, or cloud-based assets, the tool captures logs in real time using both agent-based and agentless mechanisms. It also supports a wide variety of log formats beyond Windows, including Linux, UNIX, network devices, databases, firewalls, routers, and more. This unified log collection capability ensures that your security operations center (SOC) has a single, dependable source for all log data—enabling quicker threat detection and response.
Insight in action
Imagine a scenario where an attacker tries to erase their tracks after a successful intrusion. Logs from a Windows server show that a new user account was created (Event ID 4720), immediately granted administrative privileges (Event ID 4732), and shortly after, the security logs were cleared (Event ID 1102). With centralized log collection in place, EventLog Analyzer ensures that all these critical events are captured in real time and retained securely, making it easier to spot and respond to privilege escalation attempts before they can escalate.
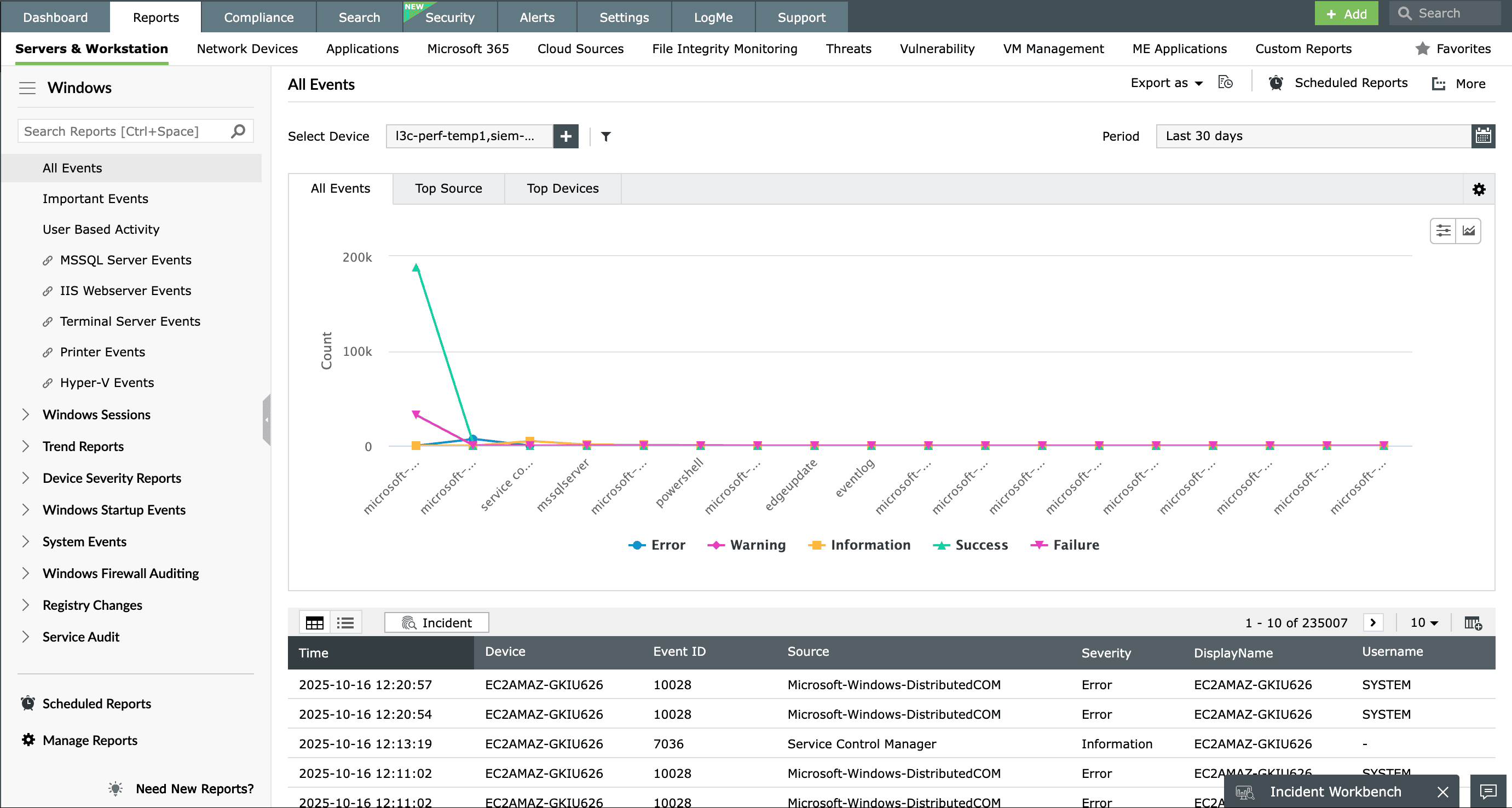
Custom log parsing
Every network environment is unique, and so are its log formats. EventLog Analyzer’s flexible log parser can be easily configured to recognize, normalize, and extract critical fields, even from proprietary or custom-built applications. If an event field isn’t parsed by default, you can define it manually, allowing EventLog Analyzer to index it for future searches and analysis. This ensures that no valuable log information slips through the cracks, helping you build a complete picture of every event across your infrastructure.
Insight in action
With custom log parsing, fields like requester ID, change type, and reason become searchable. When a user performs an access change request immediately followed by successful admin actions, EventLog Analyzer correlates custom and standard logs in real time, revealing potential security threats.
Real-time event correlation and alerting
While analyzing logs, a single log may not indicate anything out of the ordinary, but a sequence of related logs can reveal a potential attack pattern. With predefined detection rules, EventLog Analyzer can identify common attack patterns hidden within your logs and instantly alert you, enabling proactive mitigation of potential threats. You also get access to detection reports that help combat a wide range of security threats, including user account threats, web server vulnerabilities, database breaches, ransomware, file integrity violations, and more. Additionally, EventLog Analyzer provides a custom rule builder that lets you create tailored rules to suit your organization’s specific security needs.
Insight in action
A privileged user accesses a sensitive database during non-business hours (Event ID 4634), exports large volumes of data (custom application log), and then disables audit logging (Event ID 4719). EventLog Analyzer correlates these events to detect a high-risk data exfiltration attempt, allowing the SOC team to respond before data leaves the organization.
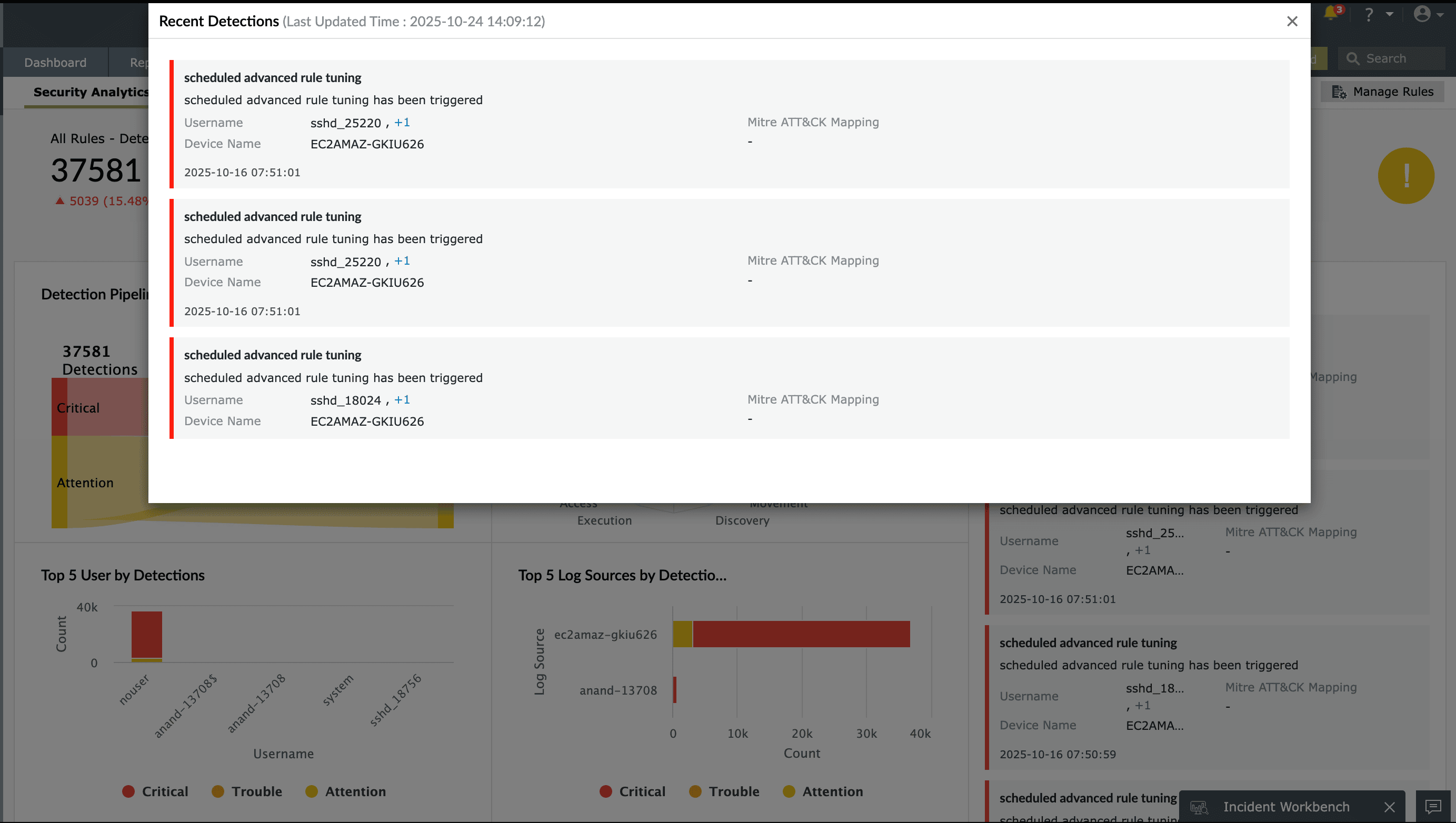
Event log forensics and investigation
The logs generated by your network devices are invaluable in reconstructing the timeline and scope of a security breach. EventLog Analyzer allows you to centrally collect, archive, search, analyze, and correlate machine-generated logs from heterogeneous systems, enabling you to generate comprehensive forensic reports such as user activity reports, system audit reports, and regulatory compliance reports. EventLog Analyzer also assists in investigating attack attempts or ongoing incidents using its advanced correlation module. The aggregated incident reports provide detailed timelines of suspicious activities and highlight both user and device involvement, helping you narrow down the root cause of an incident in seconds.
Insight in action
EventLog Analyzer's versatile log search module supports free-text searches, grouped queries, and range-based filtering using wildcards, phrases, and Boolean operators. Logs can be archived and later imported for forensic analysis. For instance, detecting a sequence of Event ID 4625 (failed logon), followed by Event ID 4624 (successful logon), and then Event ID 4670 (permissions change) can help trace a potential privilege escalation attempt.
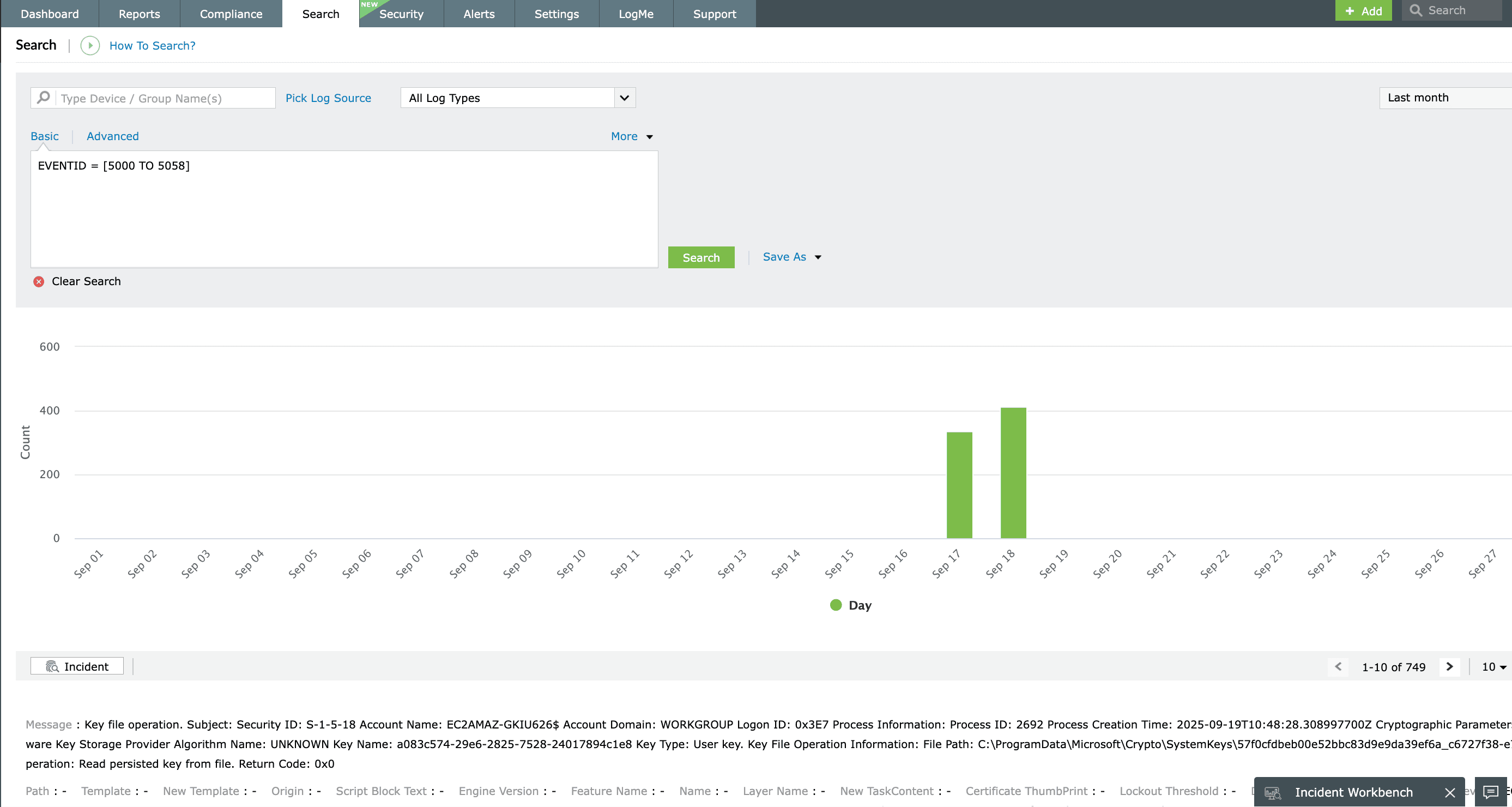
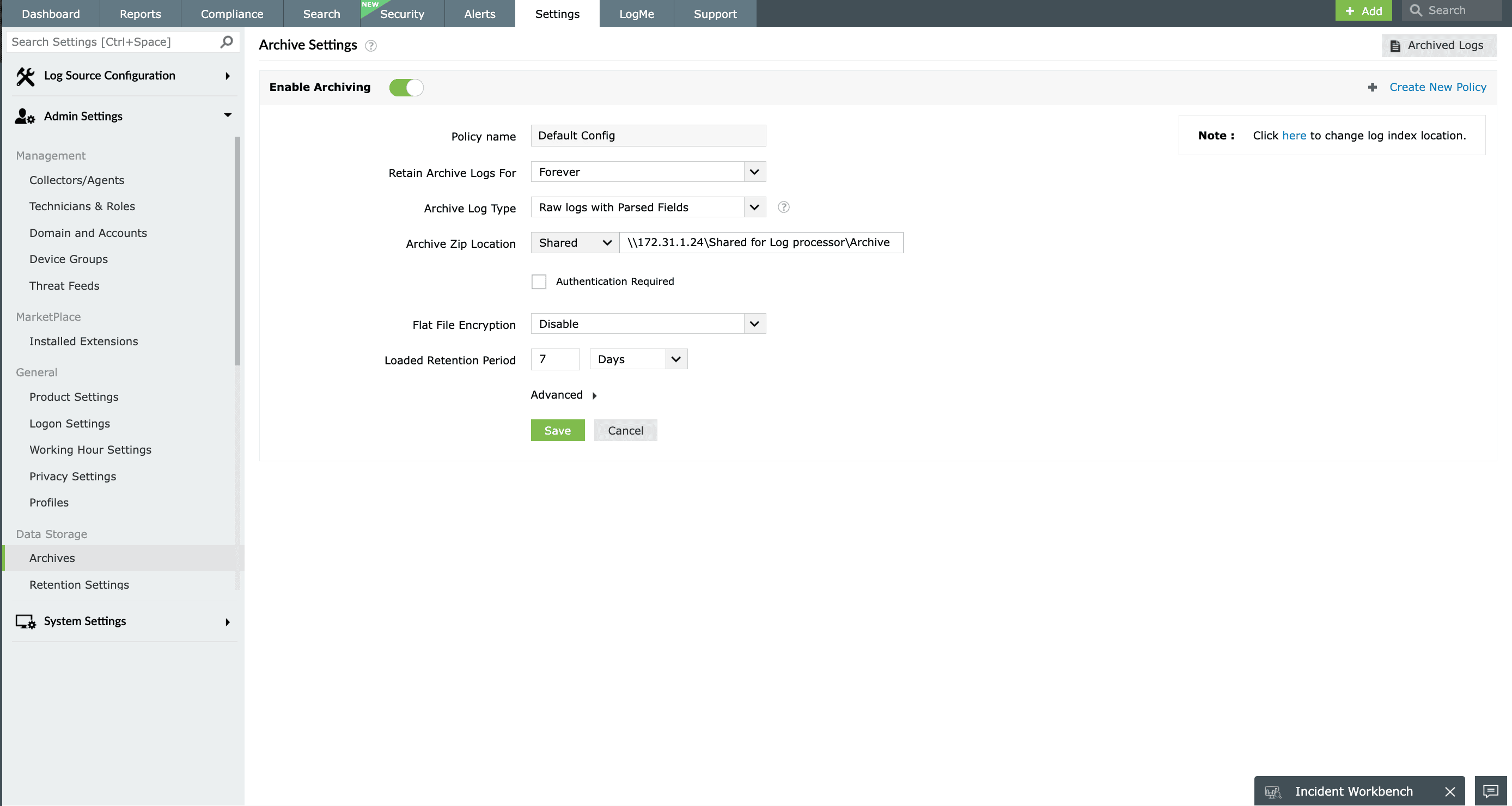
Event log archiving
Referring to historical event logs is critical when identifying patterns and predicting future occurrences of security events. However, storing vast amounts of log data can consume significant storage space and increase overhead costs. EventLog Analyzer simplifies this by enabling automated event log archival. You can configure the number of days after which logs should be moved to the archive, and the tool will automatically compress and encrypt the archived folders to ensure data integrity and prevent tampering.
Insight in action
During a compliance audit, archived logs containing Event ID 1102 (audit log cleared) were retrieved to investigate unauthorized log tampering. This secure and systematic archiving allows you to retrieve logs at any point in time for future analysis, compliance auditing, or forensic investigations.
Use cases of EventLog Analyzer in Windows event log analysis
1. Security incident detection and response
Advanced threat detection: Leverage EventLog Analyzer’s powerful correlation engine to analyze Windows event logs and identify indicators of compromise (IoCs) such as repeated failed logins, unusual login times, and privilege escalations.
Insider threat monitoring: Detect malicious or negligent insider activities by tracking unusual behavior patterns, including unauthorized access to sensitive files or changes to security policies.
Ransomware detection: Identify early warning signs of ransomware attacks by analyzing abnormal file access behaviors, such as mass file modifications or encryption attempts, helping prevent widespread damage.
2. Configuration change tracking
Audit critical changes: Monitor all changes made to user accounts, security group memberships, GPOs, and system configurations in real time.
Ensure compliance and accountability: Maintain a tamper-proof audit trail of configuration changes to support regulatory compliance (e.g., HIPAA, the PCI DSS, the GDPR) and internal audits.
Mitigate risks: Quickly identify and roll back unauthorized or misconfigured changes before they impact system integrity or security.
3. Performance and system health monitoring
Analyze system resource usage: Collect and visualize data on CPU, memory, disk, and network utilization from event logs to detect and troubleshoot performance bottlenecks.
Proactive system optimization: Set thresholds and receive alerts when resources are overused, allowing you to fine-tune system configurations or plan capacity upgrades.
4. Incident investigation and forensics
Reconstruct attack timelines: Use detailed log forensics to trace the origin, method, and impact of a security incident, helping you respond with clarity and precision.
Correlate cross-platform logs: Centralize logs from Windows systems, firewalls, antivirus software, and more, providing a unified view for thorough incident analysis.
Preserve log integrity: Ensure that logs are securely archived and tamper-evident to support legal investigations or post-incident audits.
Frequently asked questions
Event log analysis involves reviewing the records automatically generated by the Windows operating system to monitor system activities and user behavior. From failed logins to system crashes, these logs reveal the “who, what, when, and how” behind each event. By analyzing this data, IT and security teams can detect suspicious activities, investigate incidents, and trace system issues back to their root cause. It also supports compliance efforts by providing an auditable trail of events across the organization’s infrastructure.
Event Viewer is a native Windows utility for viewing local event logs, while EventLog Analyzer is an advanced log management tool. EventLog Analyzer supports centralized log collection, real-time alerting, event correlation, compliance reporting, and forensic investigation, making it better suited for enterprise IT and security operations.
To analyze Windows event logs effectively, use a centralized log management tool like EventLog Analyzer. It automates log collection, filters out noise, correlates events across systems, and generates real-time alerts and reports for faster threat detection and root cause analysis.
Other relevant features offered by EventLog Analyzer
Advanced threat intelligence
Prevent cybersecurity threats and attacks by instantly detecting malicious IPs, URLs, and domains that interact with your network.
IT compliance management
Get out-of-the-box, audit-ready compliance reports for various IT regulations such as PCI DSS, FISMA, GLBA, SOX, HIPAA, ISO 27001, and more.
File integrity monitoring
Monitor sensitive data and identify modifications made to that data with real-time alerts. Get insights with predefined reports based on information such as who made the change, as well as what was changed, when, and from where.
Privileged user monitoring
Monitor user activities—such as User Logons, Failed Logons, Objects Accessed, and more—to identify threats of privileged user abuse that can impact your business' critical operations.