- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Firewalls offer visibility into the source and type of network traffic entering your organization's network. This makes firewall logs a vital source of information, including details such as source addresses, destination address, protocols, and port numbers for all connections. This information can provide insights into unknown security threats and is a vital tool in threat management.
EventLog Analyzer is a central log management solution that collects logs from your firewall devices and organizes them in a single location. This solution is also a firewall auditing tool that makes it easy for security admins to monitor firewall logs, conduct firewall analysis, and detect abnormalities. EventLog Analyzer uses correlation and real-time alerts to actively detect and mitigate potential threats.
Firewall auditing with EventLog Analyzer
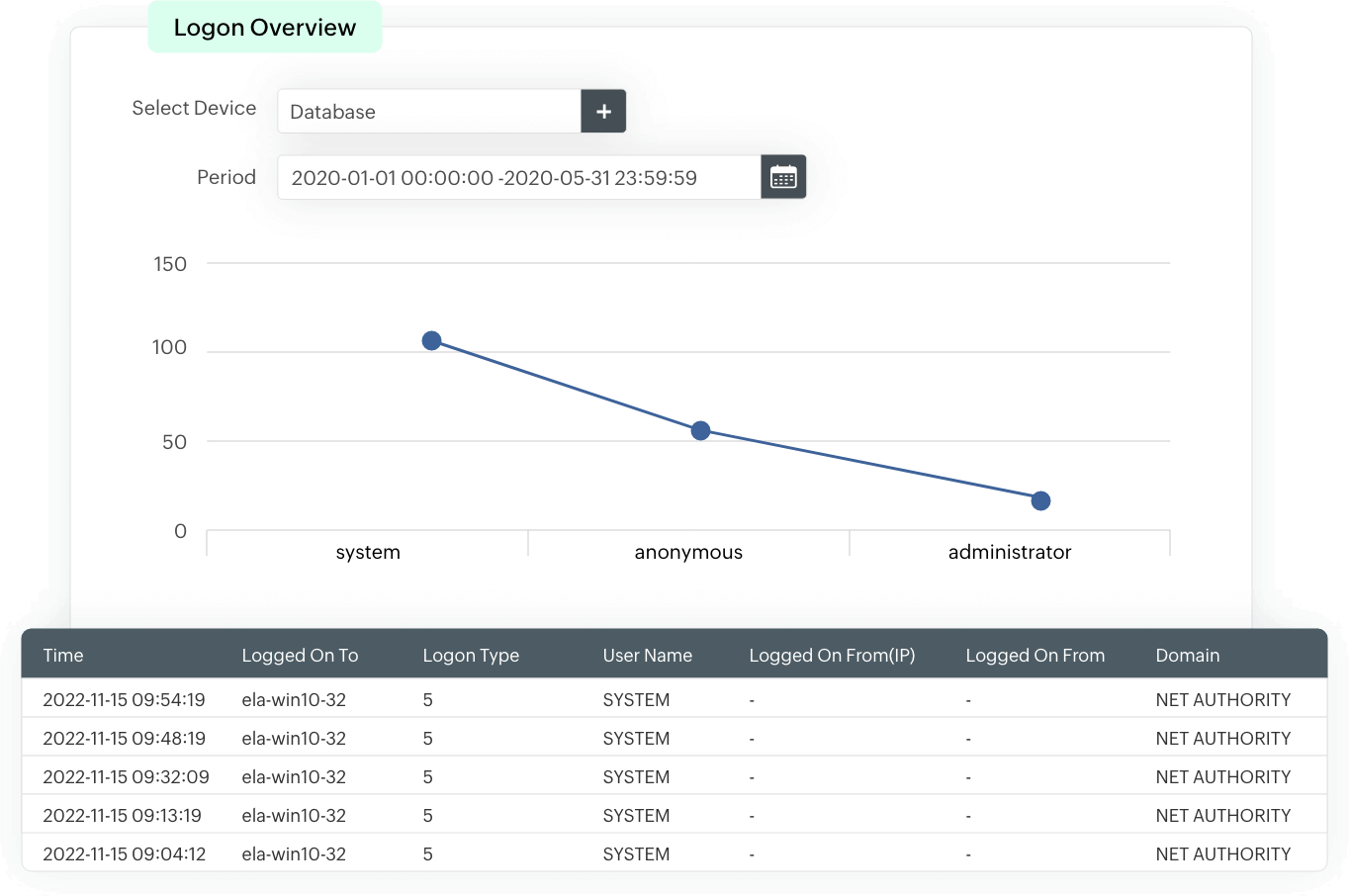
Logon auditing
The solution provides insights to successful and failed user logons in the form of analytical reports. These reports include information on the source of a logon event, time of occurrence, and more. Events are consistently monitored to identify login patterns, and used as a baseline to detect suspicious login attempts that could indicate an attack or an insider threat.
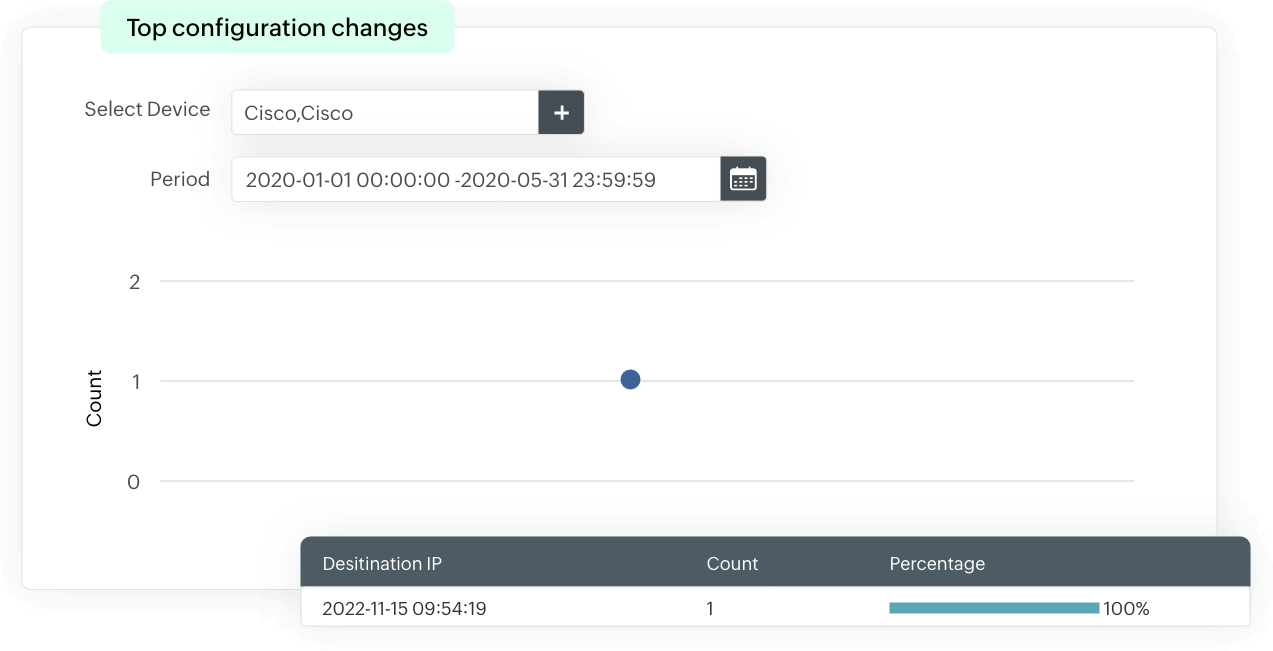
Configuration change auditing
EventLog Analyzer analyzes firewall log data and provides insights into configuration changes and configuration errors. The tool provides details such as who made the configuration change, when it was made, and from where. This information not only helps with effective auditing but also with complying with the regulatory requirements of PCI DSS, HIPAA, FISMA, etc., which mandates that enterprises audit firewall configuration changes.
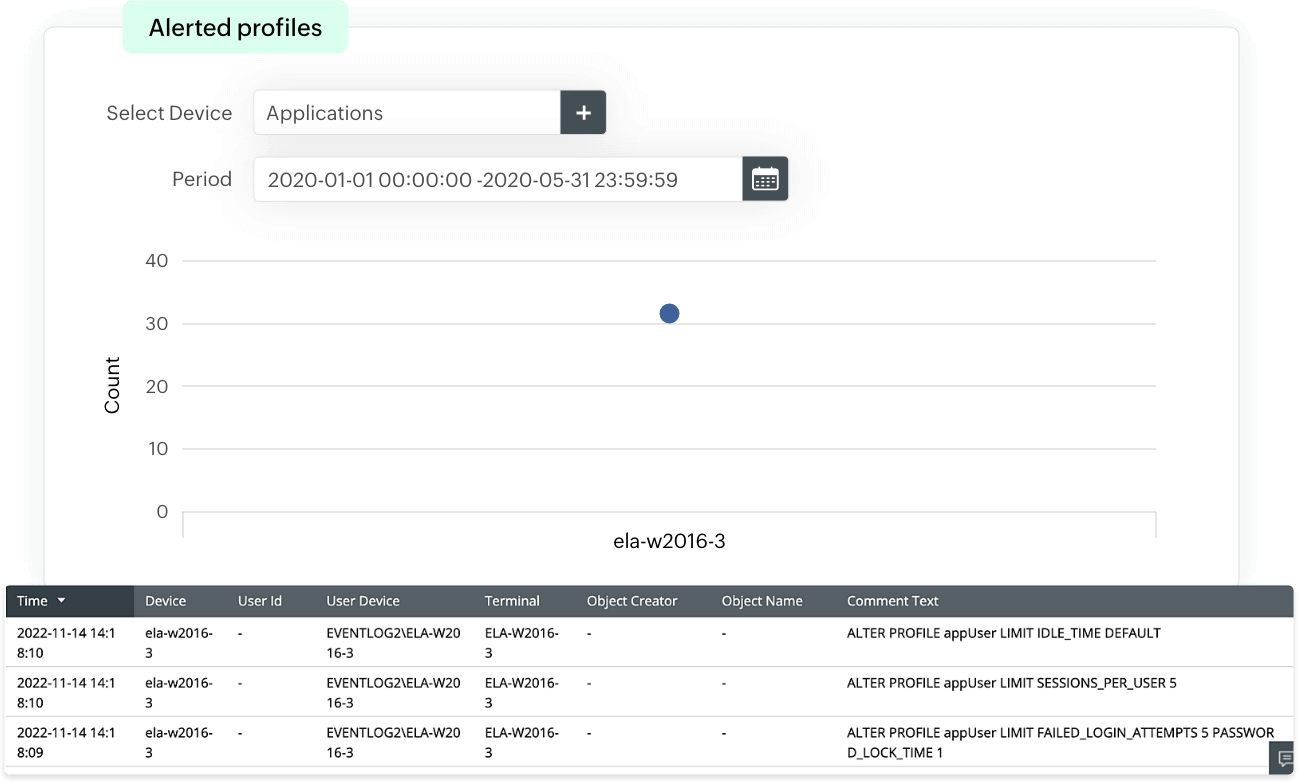
User account change auditing
These reports provide insights into the addition, modification, disabling, or deletion of users along with user privilege level changes, which provides visibility into user account activities. EventLog Analzyer uses this information to detect any suspicious or unusual user account activity, and identify any insider threats or privilege escalation attempts.
Firewall traffic monitoring
EventLog Analyzer provides traffic information from allowed and denied connections. The detailed information provided by these reports is categorized and visually represents the traffic based on sources, destinations, protocols, and ports along with timestamps, enabling security admins to track network traffic. This helps identify trends in abnormal traffic from suspicious sources, and prevents threat actors from gaining access to the network.
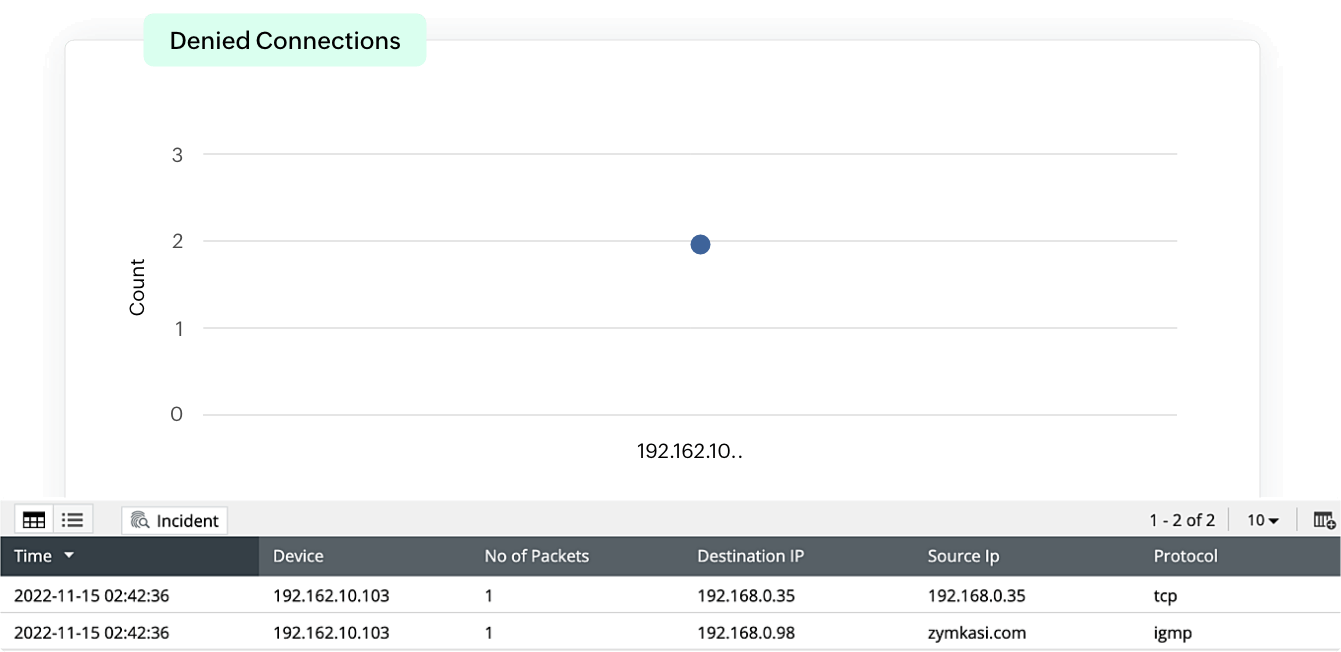
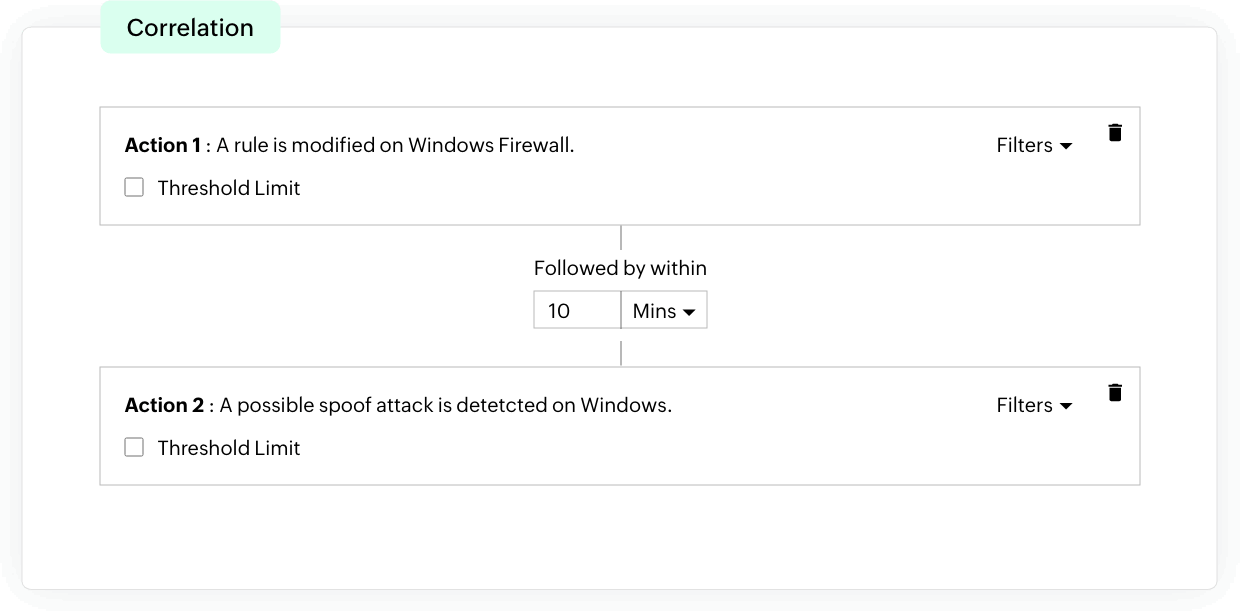
Incident response
EventLog Analyzer offers an effective incident detection process through event correlation. With the help of built-in correlation rules, you can detect security threats in firewall events. When any suspicious activity is spotted, instant alerts are sent out to security admins. This helps speed up the response process, alerting your admins to possible threats at their earliest stages so they can effectively protect your organization's network from experiencing major damage.
Frequently asked questions
Firewall logs contain information on an event such as:
- Event type
- Source and destination IP address
- Port number
- Protocol
- Timestamp
- Action
- Rule ID
The firewall logs are parsed and analyzed by either a firewall analyzer or a log management solution to identify patterns or anomalies to detect an attack, and generate reports. The information contained in the firewall logs are analyzed to provide insights into network traffic patterns, security events, and connection statistics.
Monitoring firewall logs provides insights into network activity and potential security threats. It helps with:
- Network visibility: Firewall logs provide insights into a network's traffic and activities. This helps identify trends and any anomalous behavior within the network. Enhanced network visibility contributes to proactive measures in security management.
- Threat detection: Analyzing firewall logs helps organizations detect any suspicious activity, port scanning, unauthorized access attempts, or any unusual traffic patterns that could be indicative of an attack. Analyzing these logs allows for suspicious behavior to be detected in real-time, which helps organizations take immediate action to mitigate risks and prevent security incidents.
- Intrusion detection: Firewall logs can be used to detect network intrusions. Analyzing the logs for indicators of compromise or known attack techniques can help identify potential threats and mitigate unauthorized access attempts.
- Incident response: Firewall logs provide valuable insights into a security incident. This helps IT security teams understand the nature, scope, and impact of the incident to facilitate incident response.
- Compliance: Firewall logs help organizations demonstrate adherence to compliance mandates and regulations, and industry-specific security requirements.
When a firewall log analyzer monitors and analyzes the logs automatically, it helps detect threats in real-time and takes immediate actions to minimize the incident's impact. Automation of firewall log monitoring can be achieved with a firewall log management solution, such as EventLog Analyzer. The solution correlates suspicious events and uses automated workflows to mitigate threats immediately.
EventLog Analzyer offers out-of-the-box support for firewalls, next-generation firewalls (NGFWs), intrusion detection systems (IDS), and intrusion prevention systems (IPSs) from leading vendors.
EventLog Analyzer as a firewall monitoring tool
EventLog Analyzer is a centralized log management tool that monitors firewall logs and activity to
- Performs comprehensive firewall log management and analysis.
- Presents exhaustive information in predefined firewall auditing reports to help you track firewall activity.
- Shows reports in table, list, and graphical formats, with support for several graph types.
- Sends real-time predefined or customizable alerts through SMS or email.
- Identifies suspicious activity and alerts the administrator through correlation rules.
- Displays raw log information from reports in a simple click.