- HOME
- Endpoint Management Analytics
- Stay on top of security threats from rogue IoT devices
Stay on top of security threats from rogue IoT devices
- Last Updated: July 1, 2024
- 557 Views
- 3 Min Read

After a hectic week at work, John arrives home on a Friday night, and settles comfortably on his couch with a bucket of popcorn to binge-watch his favorite show. Unfortunately for John, his streaming service failed to load. Not just John, scores of people had their Friday night plans blown away. The reason for this massive shutdown was later discovered to be a DDoS attack orchestrated with the help of IoT botnets. Unlike traditional botnets that sit on computers, IoT botnets have a wide range of devices (such as digital cameras and DVRs) to prey upon. This gives botnets a large and distributed surface to infect.
Over the years, various PC makers have taken utmost care to secure systems from hackers. The advent of IoT devices, coupled with the lack of built-in remote patch updates, have made life easy for hackers as they can attack vulnerable IoT devices to install malware.
According to TechJury, the number of connected IoT devices will hit a staggering landmark of 46 billion by end of 2022. An estimated 125 billion IoT devices will be around us by 2030. IoT devices are usually equipped with single-board computers such as Raspberry Pi and BeagleBone.
Raspberry Pi is a tiny and affordable single-board computer that can perform complex tasks ranging from playing chess to building a model of an international space station. Similarly, the BeagleBone is also a high-performance, low-power, single-board computer that's powered by an open-source Linux operating system.
These palm-sized, single-board computers fall under the broad spectrum of IoT devices that can be connected to any endpoint using USB ports. They constantly learn and try to adapt to their respective environments, and this makes it difficult for organizations to track them and prevent them from being used in cyber attacks. While it might be difficult to identify the number of devices attached to endpoints, it is possible to prevent their entry into an organization's secure network using endpoint security analytics.
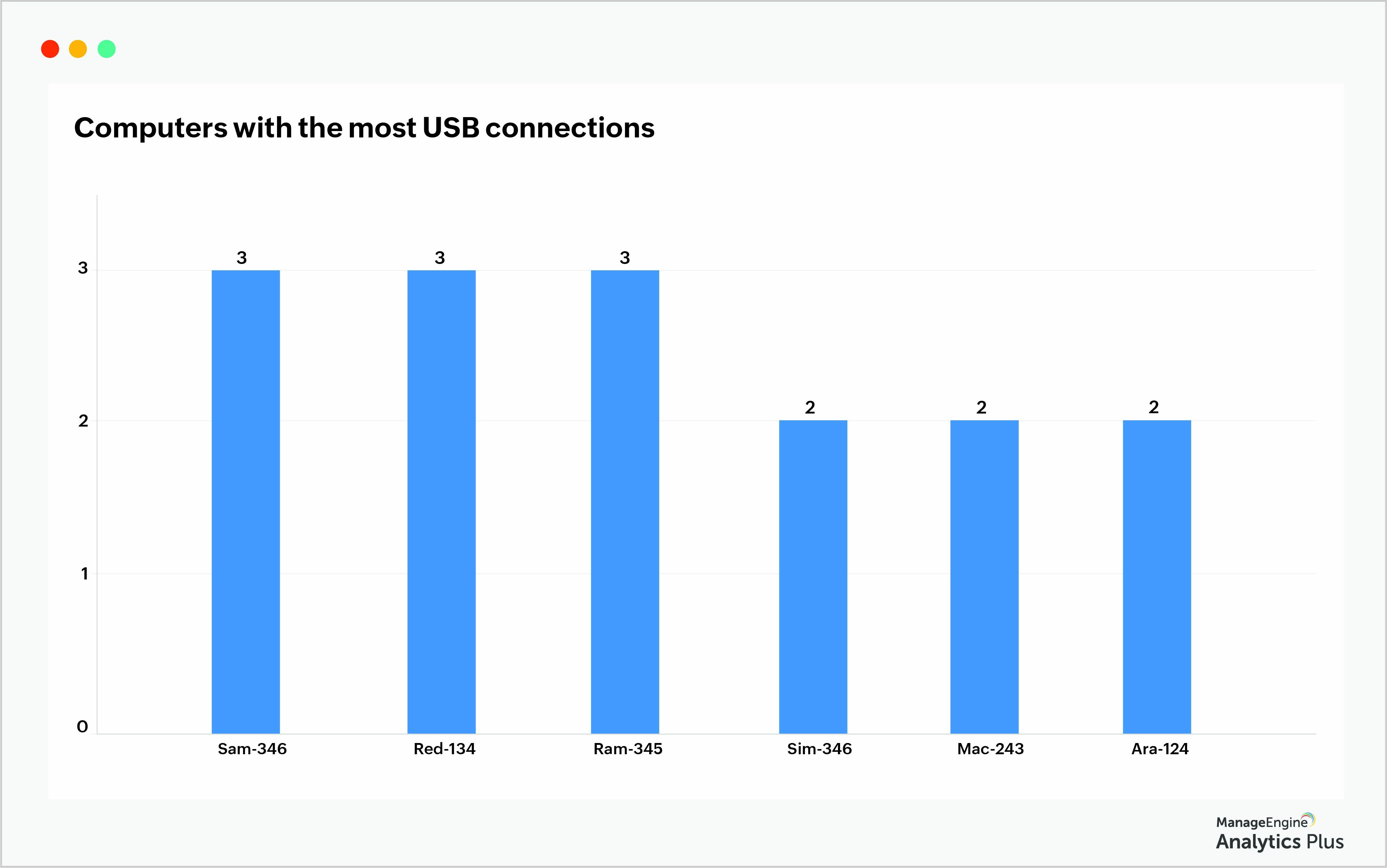
Watch for computers with several USB connections
Most of the peripheral devices accessed by users connect to their computers through USB ports. To track USB connections, focus on the number, frequency, and duration of USB port use.
The Computer with the most USB connections report illustrates computers that have had the maximum number of USB connections. Even though it is not imperative to consider a high count as a security hazard, it's necessary to flag them for further analysis and clearance.
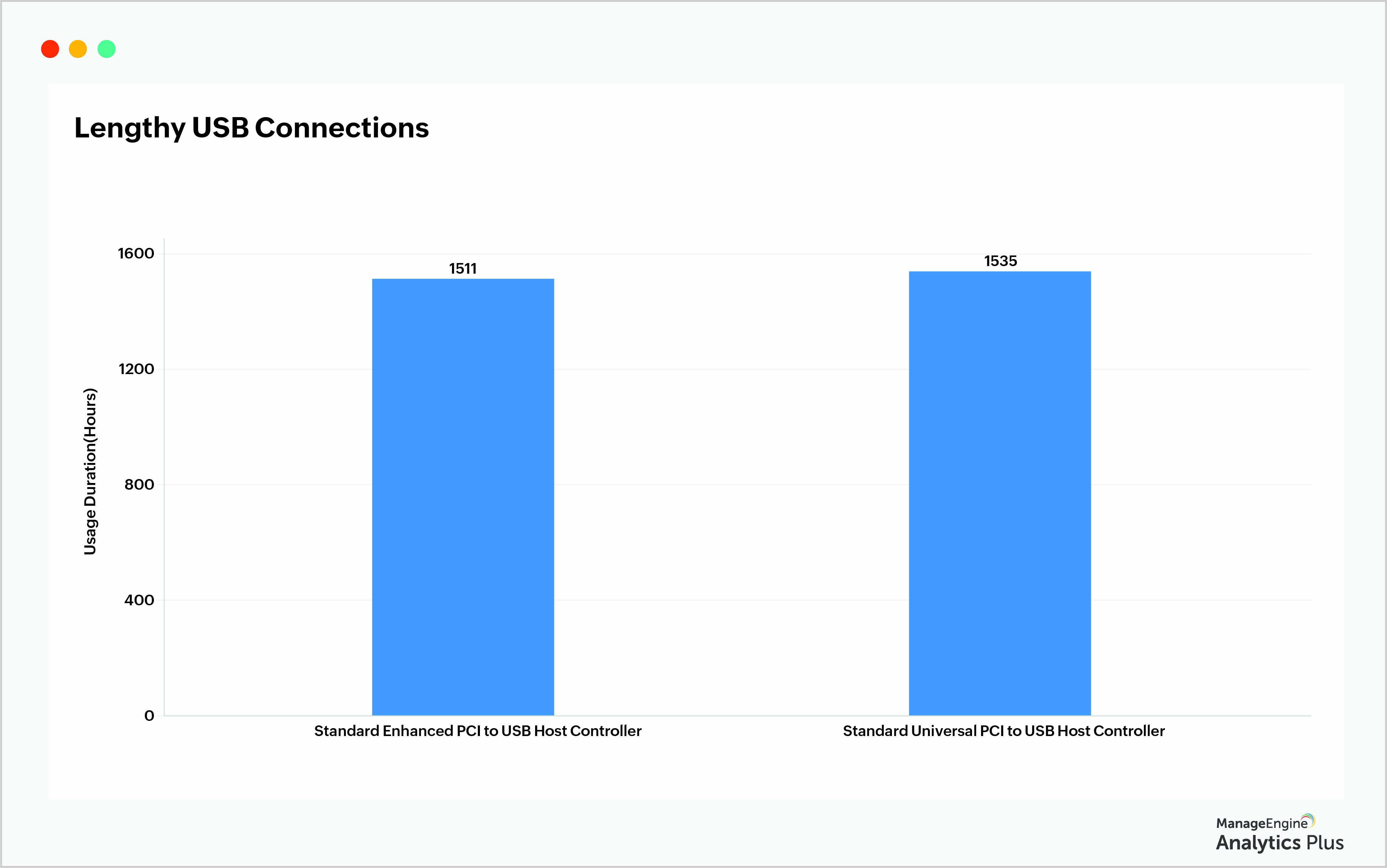
Connection duration matters
Ten minutes—that's all it takes for a user to copy critical information out of your servers, which is why it's important to track the duration of USB connections. Taking a cue from the previous report, we can filter systems that have many connections and see their duration. The Lengthy USB Connections report displays two devices that have been connected for over 1500 hours. As the next step, the device owners need to be contacted to uncover the reason behind those lengthy USB connections.
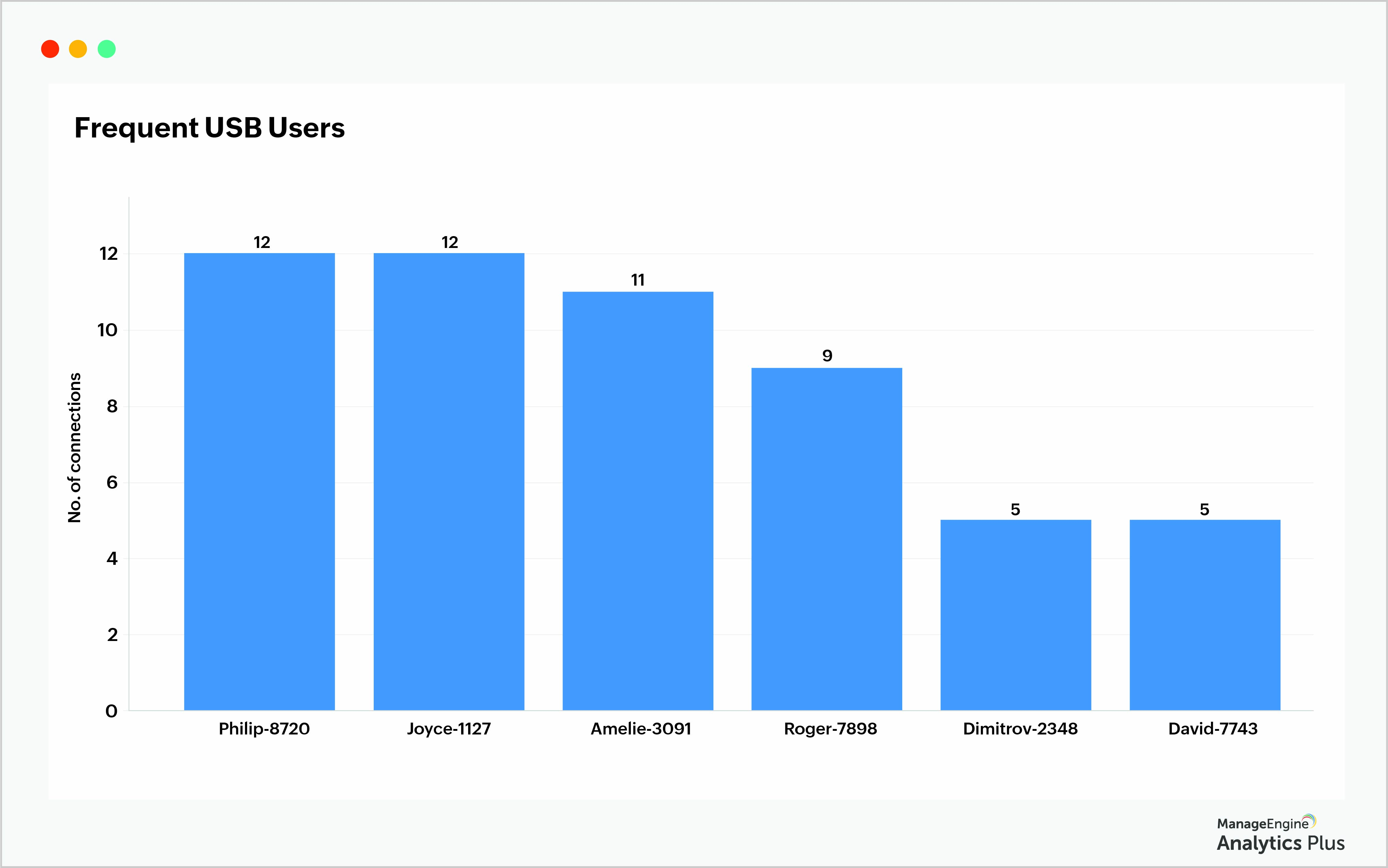
Pay attention to users who frequently connect USB devices
Finding the list of users who frequently connect USB devices to their computers helps security teams keep a close watch. From the report below, users Philip-8720 and Joyce-1127 have connected USB devices 12 times in a span of six hours. Their systems need to be flagged for further investigation due to how often they connect USB devices during a short time period.
Flagging USB actions individually might be a cumbersome task especially when the volume of endpoints to manage is high. Assigning vulnerability scores to users and endpoints based on potentially risky behavior can make the IT admin's life easier. Click here to learn how vulnerability scoring works.
The reports above are generated using ManageEngine Analytics Plus, an AI-enabled analytics solution custom-built for IT users to help secure their environment and enhance efficiency.
Click here to check out more interesting reports and dashboards built using Analytics Plus.
Schedule a personalized demo of Analytics Plus today with one of our solution experts who can answer your product-related questions. Or try Analytics Plus for free to explore on your own this powerful business intelligence and IT analytics application.
 Sailakshmi
SailakshmiSailakshmi is an IT solutions expert at ManageEngine. Her focus is on understanding IT analytics and reporting requirements of organizations, and facilitating blended analytics programs to help clients gain intelligent business insights. She currently spearheads marketing activities for ManageEngine's advanced analytics platform, Analytics Plus.





