| ISO 27001 requirements |
Requirement Description |
EventLog Analyzer reports |
| 9.2.1 User registration and de-registration |
A formal user registration and de-registration process should be implemented to enable assignment of access rights. |
- Windows User Access
- User Account Changes
- Computer Account Changes
- User Group Changes
- Unix User Access
|
| A.9.2.5 Review of user access rights |
Asset owners shall review users access rights at regular intervals. |
|
| A.9.4.2 Secure log-on procedures |
Where required by the access control policy, access to systems and applications should be controlled by a secure log-on procedure. |
- Windows User Access
- User Account Changes
- Computer Account Changes
- User Group Changes
- Unix User Access
|
| A.12.4.1 Event logging |
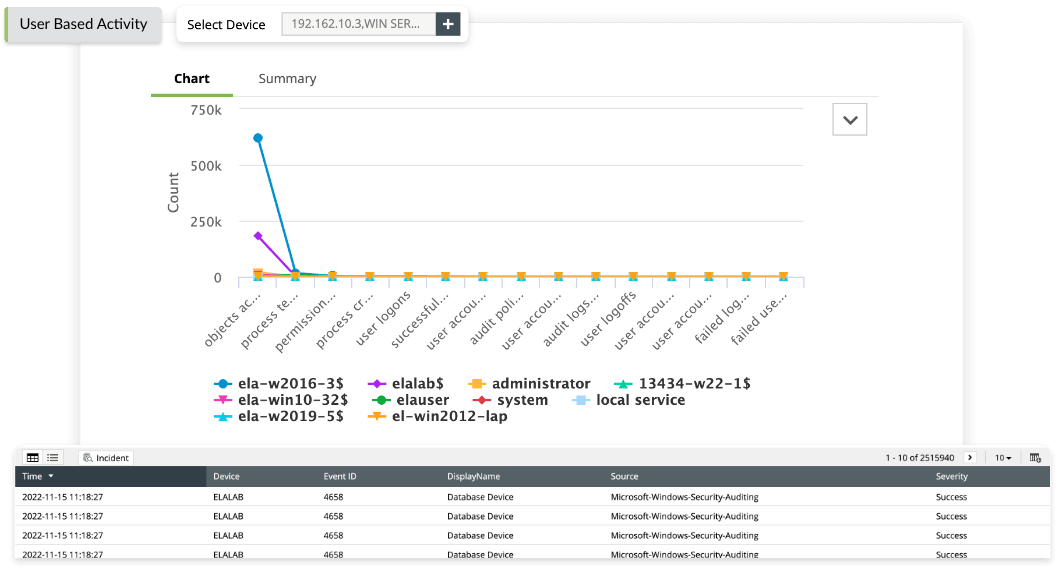
Event logs recording user activities; exceptions, faults and information security events shall be produced, kept and regularly reviewed. |
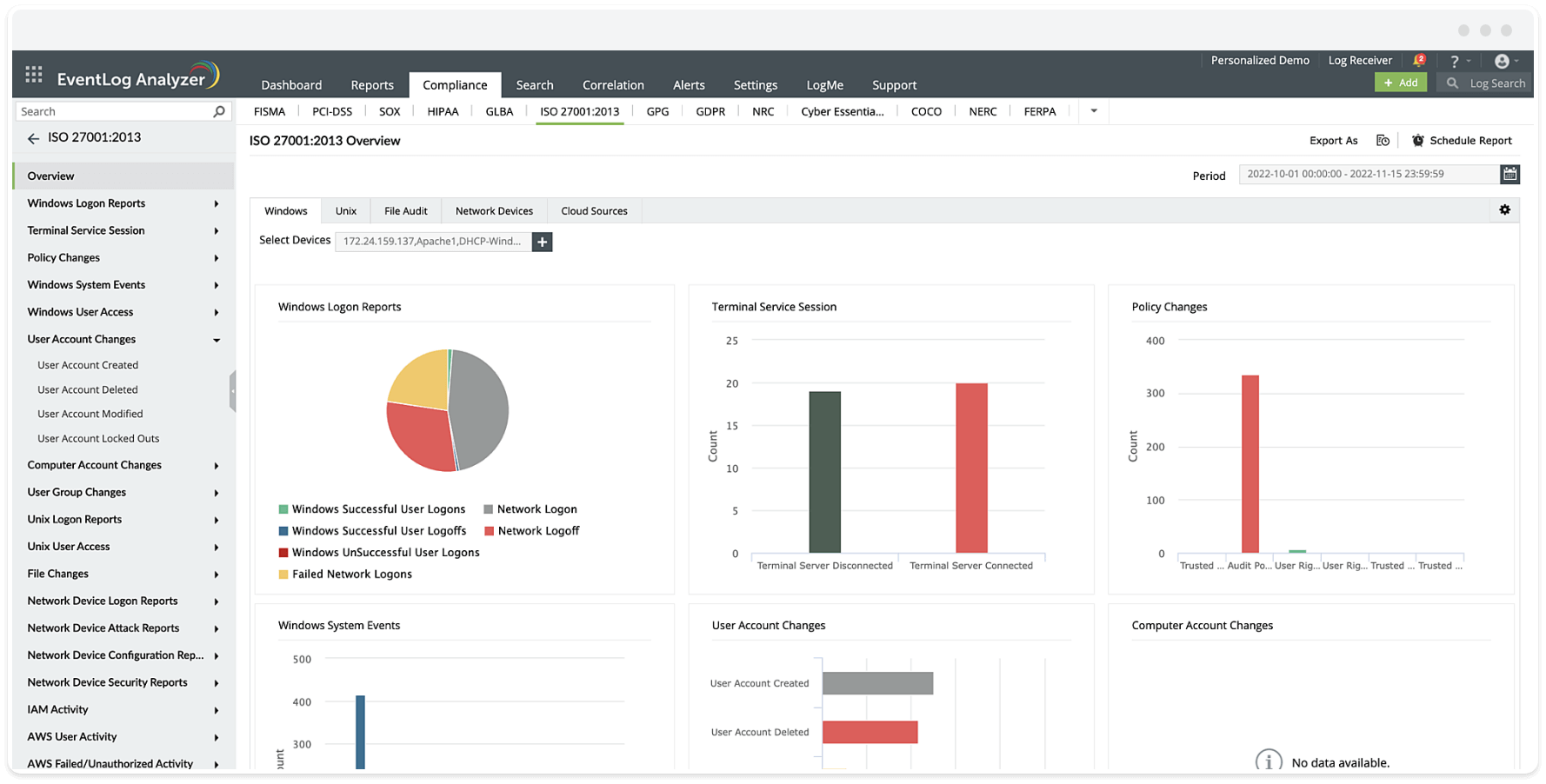
- Policy changes
- Windows User Access
- User Account Changes
- Computer Account Changes
- User Group Changes
- Unix User Access
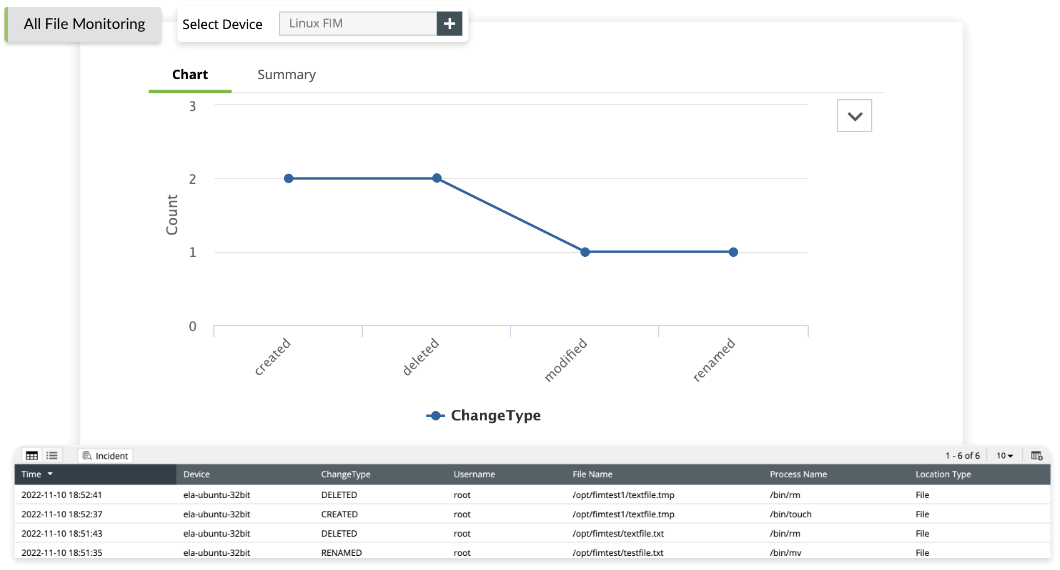
- File Changes
|
| A.12.4.2 Protection of log information |
Logging facilities and log information shall be protected against tampering and unauthorized access. |
- Policy Changes
- Windows System Events
- File Changes
|
| A.12.4.3 Administrator and operator logs |
System administrator and system operator activities shall be logged and the logs protected and regularly reviewed. |
- Windows Logon Reports
- Terminal Service Session
- Policy Changes
- Windows User Access
- User Account Changes
- Computer Account Changes
- User Group Changes
- Unix Logon Reports
- Unix User Access
|