Oracle Database Auditing
Organizations often store confidential business data such as customer records, credit card information, financial details, and more in Oracle Database servers. Such data repositories are often the target of both internal and external security breaches. Any compromise of such sensitive data can gravely tarnish customer's trust on the organization. Hence, database security is a high priority for any IT administrator. To ensure database security, it is important to audit Oracle Database servers. This can be achieved with Oracle Database log analysis, as logs are the best source of detailed information on the server activity and events.
EventLog Analyzer is the perfect auditing and reporting tool for Oracle Database, and facilitates auditing and monitoring with its out-of-the-box reports and alerts. The Oracle audit reports cover several areas, such as:
- User activity in database
- Changes made to user accounts
- User accesses to Oracle database servers
- Security breaches attempted and more
With EventLog Analyzer you can also get real-time email/SMS notification upon any changes in your database server, anomalies in user activities, unauthorized user accesses, security breach attempts, access to confidential data and more.
Audit Oracle Database Account Changes
Continuous monitoring and auditing of user account changes viz., privileged user account creation, modification, role modification etc., through reports and helps identify the security attack attempts at the intrusion level. This also helps you to stop the back door account creation and unauthorized attempt to access data.
EventLog Analyzer provides out-of-the-box reports that help administrators to:
- Monitor user account creation, modification and deletion.
- Audit role creation, modification and deletion.
- Audit role granted to or revoked from user accounts.
- Monitor who created/modified or deleted the user account or role, from where, and when did the event occur.
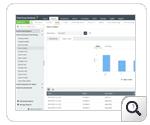
Available Reports
Profiles Created | Profiles Altered | Profiles Dropped | Users Created | Users Altered| Users Dropped | Roles Created | Roles Altered | Roles Dropped | Roles Granted | Revoked Roles | System Granted | System Revoked
Audit Access to the Oracle Server
As Oracle database servers store confidential data, tracking the user access and activities of the server will help prevent unauthorized access attempts.
EventLog Analyzer provides detailed reports that give you information on who accessed the server, when it was accessed, and from where. These reports enable administrators to identify the unauthorized access attempts at its earliest thus protecting the sensitive data.
The reports allow you to:
- Audit user logon, user log off and remote user logon.
- Monitor failed user logon attempts and user credentials with maximum failed logon attempts.
- Audit trend reports for logon, failed logons and logon failures.
- Audit server startup and shutdown details.
Available reports
Connect events report | Sever startup report | Server shutdown report | User logon report | Failed logon attempts report | Logon trends reports | Failed logon trends reports | Oracle event trend reports | Remote logons report
Security attacks always target the customer data or confidential information that are stored in the database.
Security administrators have to react to the attack attempts instantly to either prevent the attack or to reduce the data damage caused. To do this, they might need to conduct the root cause analysis and recreate the attack pattern as well.
EventLog Analyzer provides predefined Oracle database specific security reports that help in visualizing the exact events that had happened. The reports provide information on
- SQL Injection and Denial of Service attacks or attack attempts that can be analyzed to further strengthen the database's security.
- When the attack has happened, source of attack, target of attack and more that help to completely understand the attack pattern
- User accounts that can be possibly exploited by the attacker such as the user accounts that are locked out due to logon failures or user accounts with expired passwords.
EventLog Analyzer lets you identify the attack patterns with pre-defined auditing and monitoring reports and attack attempts at the earliest with its real-time email/SMS alert notifications. Learn more
Available reports
SQL Injection report | Account lockouts | Denial of Service report | Expired passwords report
Oracle Database Monitoring
Audit and monitor operations occurring within an Oracle database with EventLog Analyzer's predefined reports, which provide detailed information on structural changes to the database, database queries executed, and details of who made what changes. Learn more
Conduct real-time Linux log auditing with EventLog Analyzer.