Reduce false positives using the whitelist feature in EventLog Analyzer
According to the Forbes, the number of hacking and intrusion incidents resulting in data breaches have increased, highlighting the importance of securing an organization's network. This often leads to IT administrators blacklisting essential data sources and a subsequent decrease in business productivity. To cater to the security needs of an organization without exposing the network to risks, administrators need to maintain a list of trustworthy sources.
Whitelisting refers to the concept of explicitly authorizing known, trusted entities. They may appear to be malicious but will generally be harmless.
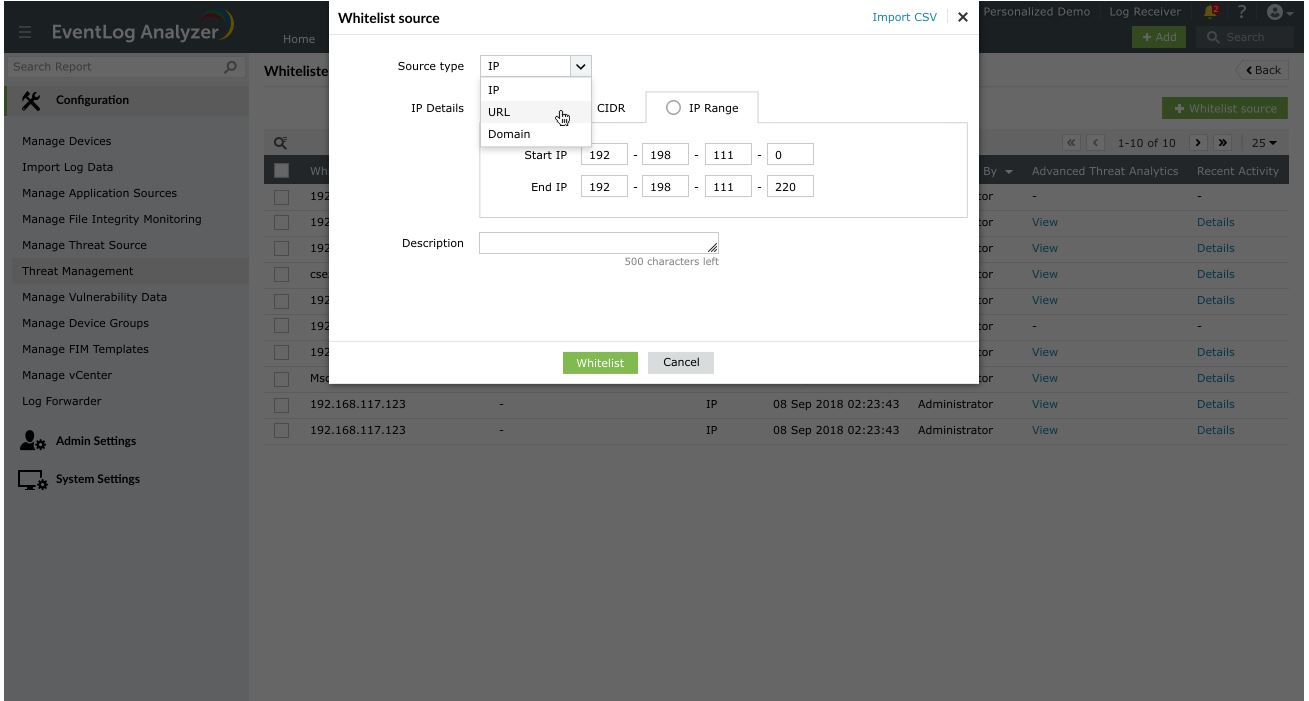
EventLog Analyzer, a log management tool, allows you to customize the list of admissible entities or sources. The tool enables you to whitelist IP addresses, URLs, and domains. It collects log information and correlates it with the list of the whitelisted sources to ensure that alerts are not triggered needlessly.
For instance, global threat feeds often flag legitimate IP addresses that your enterprise uses as "malicious." EventLog Analyzer helps you whitelist such IPs, allowing them to bypass the security check. Further, it excludes whitelisted sources from threat alerts and external threat reports to help reduce the number of false positives, and simplify the threat management process.
Integration with Advanced Threat Analytics
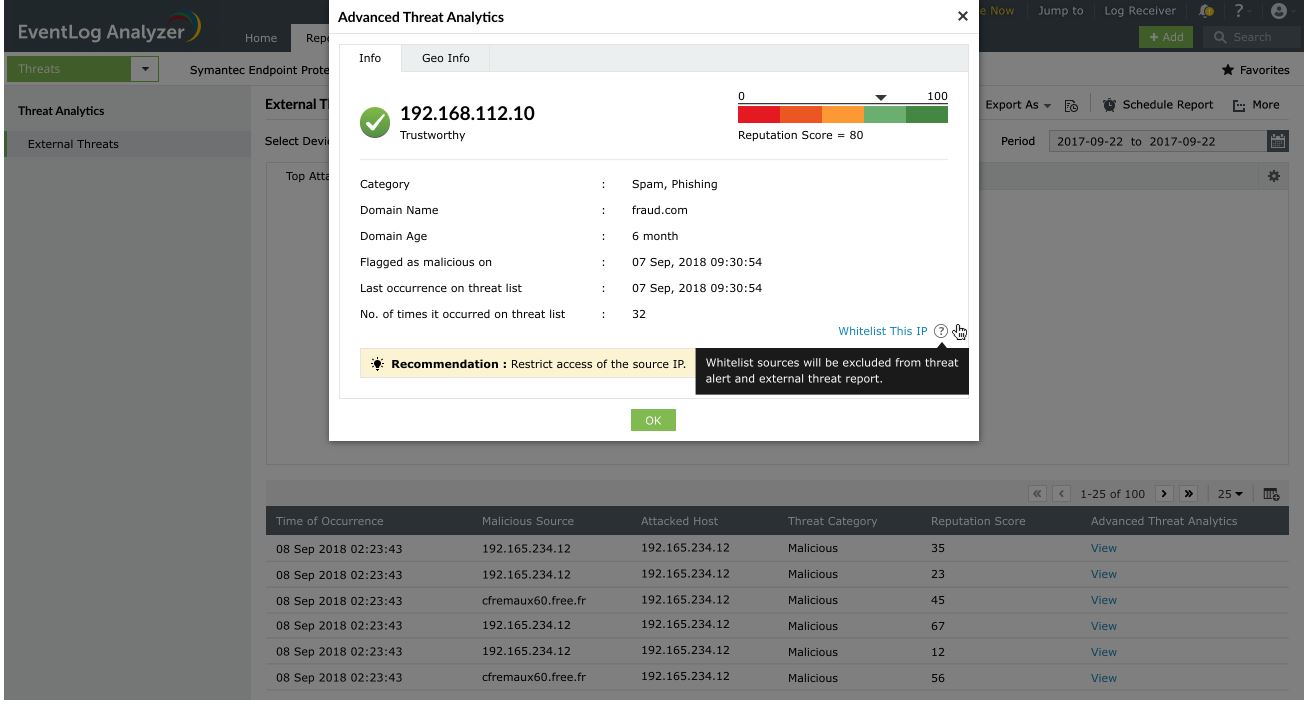
EventLog Analyzer's Advanced Threat Analytics helps you identify malicious sources based on their reputation score. Threat whitelisting is integrated with Advanced Threat Analytics to reduce the number of false positives.
For instance, let's use an IP address with a reputation score of 80. This address has been flagged as malicious even though it's trustworthy to your organization. EventLog Analyzer comes with an option to whitelist sources on the spot when the notification is shown. You can even whitelist multiple sources in a single click.
By combining the wealth of information from the collected logs and the database of global threat feeds, EventLog Analyzer gives you the necessary information on IPs, URLs, and domains to identify seemingly malicious yet useful sources, and whitelist them.
Secure your organization network with EventLog Analyzer.