Related content
Why monitor the dark web?
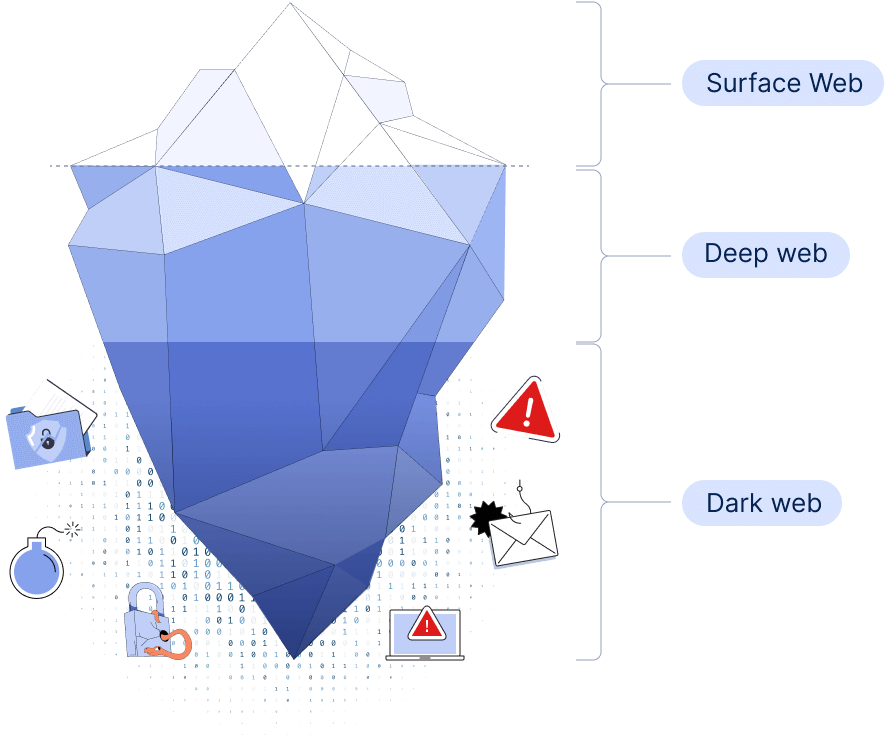
The dark web is the hidden part of the internet that cannot be accessed through traditional search engines like Google and Bing. Often associated with illicit activities, one of the more concerning issues for businesses and individuals alike is the leakage of personal information on the dark web—data like email addresses, passwords, credit card details, and more.
While dark web search engines provide a way to access this concealed network, they often fall short of offering comprehensive security insights. For businesses, manually navigating the dark web is risky and inefficient, making automated monitoring solutions a critical line of defense.
This guide delves into how dark web search engines work, the limitations of manual searches, and the advantages of leveraging advanced monitoring tools like Log360. Whether you’re concerned about leaked credentials or supply chain vulnerabilities, understanding and addressing dark web risks is essential for safeguarding your digital assets.
Suggested reading: Explore what the dark web is and how credential leaks can affect your business.
What are dark web search engines?
Dark web search engines are specialized tools designed to navigate the hidden part of the internet that is inaccessible via traditional search engines like Google or Bing. Unlike the surface web, the dark web operates through encrypted networks such as Tor (a.k.a., The Onion Router), where websites use the .onion domain. These search engines allow users to locate content on the dark web by indexing .onion sites, which are otherwise difficult to find without direct links.
Dark web search engines function by crawling and indexing .onion websites using specialized algorithms. Unlike mainstream search engines that provide indexed results, dark web search engines often face challenges that include unreliable data sources, lack of standard site indexing, and rapid changes in the availability of .onion sites. Since the dark web is not indexed like the surface web, users must rely on specialized search engines to locate information safely. Some examples of dark web search engines include Ahmia, Torch, DuckDuckGo Onion, and Haystack.
How to search for personal information leaks on the dark web
Searching the dark web for personal information leaks requires caution, preparation, and the right tools.
Why manual searches fall short on the dark web
Dark web search engines, such as Ahmia, Torch, or DuckDuckGo Onion, are tools designed to locate .onion websites within the encrypted Tor network. While these tools provide a way to search the dark web, they come with several limitations.
Dark web search engines often miss a significant portion of .onion sites due to the transient nature of the dark web. Many sites frequently go offline or change addresses, leaving gaps in search results. Additionally, these engines do not comprehensively index every site, meaning key information might be missed. Manually browsing the dark web exposes users to various risks, such as phishing scams, malware-laden links, and unverified content. Even experienced users can inadvertently click malicious links, leading to potential data breaches or device compromise.
Moreover, dark web search engines are passive tools; they do not actively monitor for data leaks or alert users to potential threats. Searching for personal or business information requires repeated manual effort, which can be time-consuming and inefficient.
While dark web search engines offer a basic way to explore the hidden web, their limitations make them unsuitable for effectively detecting and mitigating personal information leaks. With dark web monitoring solutions like ManageEngine Log360, you can go beyond manual searches and benefit from advanced analytics, real-time alerts, and automated monitoring to uncover potential dark web threats quickly and act decisively.
Personal information leak monitoring with Log360
Log360 is a unified SIEM solution that includes robust dark web monitoring features to detect activities targeting your organization. Through its integration with Constella Intelligence, a digital risk intelligence provider, Log360 offers continuous monitoring of the dark web for potential data leaks. This integration ensures that any exposure of PII such as names, email addresses, credentials, and credit card information on the dark web is immediately flagged. This advanced feature ensures organizations stay ahead of potential threats by continuously monitoring the dark web for exposed personal information.
How Log360’s dark web monitoring works
Integration with Constella Intelligence
Log360 leverages its integration with Constella Intelligence, a leading digital risk protection provider, to identify exposed personal and credential data. By scanning marketplaces, forums, and other dark web repositories, Log360 helps uncover leaks involving:
- Email addresses.
- Compromised credentials like usernames and passwords.
- Financial details like credit card numbers.
- Sensitive business data like domain and IP information.
Real-time alerts
When Log360 detects leaked personal information, it provides instant alerts, allowing IT teams to take immediate action. These real-time notifications help mitigate risks before they escalate into larger breaches, such as large-scale identity theft, account compromise, or fraud.
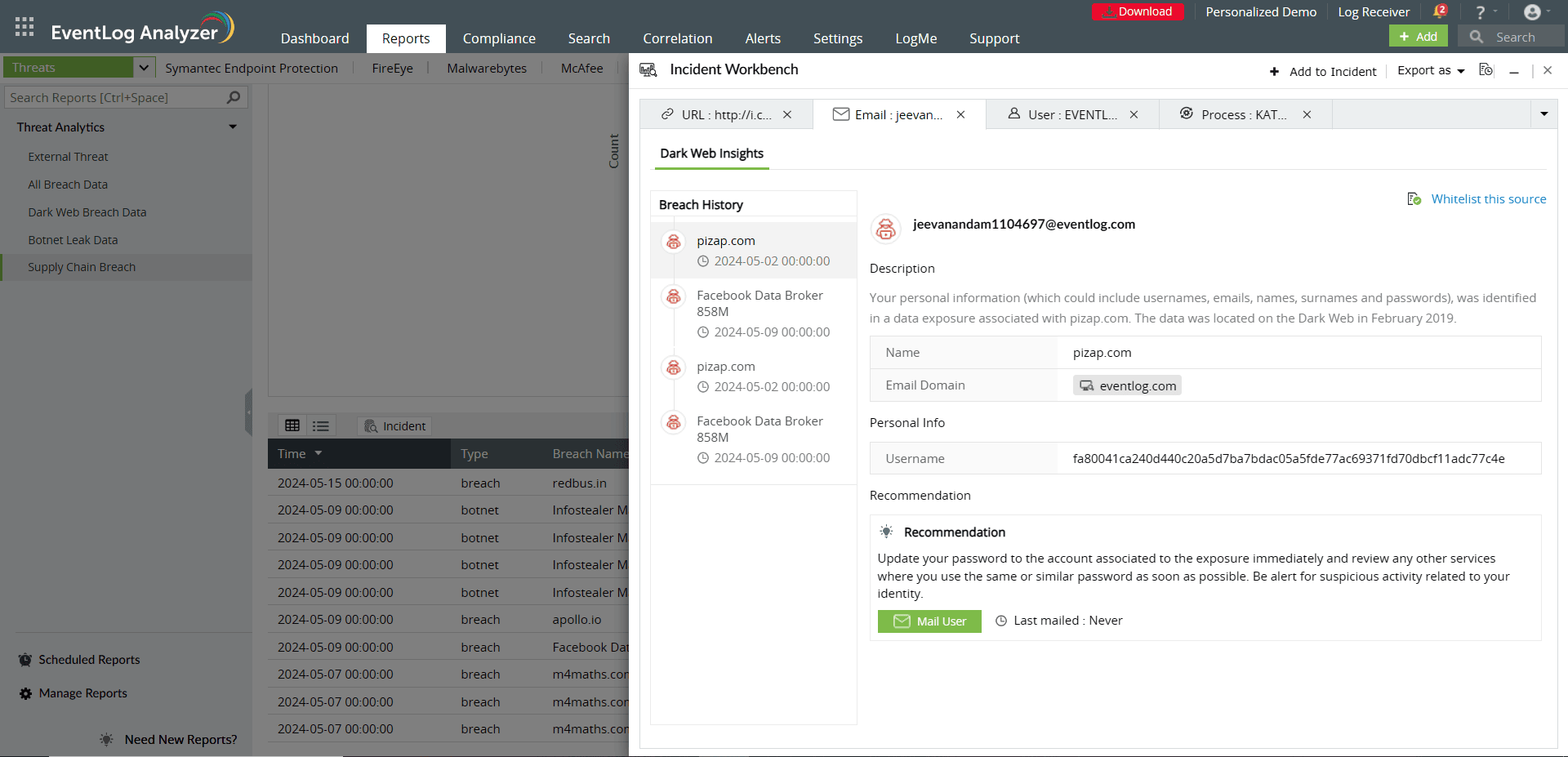
Comprehensive threat analytics with Incident Workbench
Log360’s Incident Workbench facilitates advanced analytics on detected threats. Once a data leak is identified, users can:
- Gain contextual data, such as breach history, leaked data related to login credentials like username and password, and leaked personal information, for effective threat hunting.
- Analyze the breach to understand its scope and impact.
Why choose Log360 for dark web monitoring?
By providing 24/7 monitoring and actionable insights, Log360 allows businesses to:
- Prevent supply chain compromises through early detection of credential leaks.
- Safeguard customer and employee trust by addressing vulnerabilities proactively.
- Minimize the impact of breaches by acting swiftly.
Log360’s dark web monitoring capabilities combine threat intelligence and seamless integration with Constella Intelligence to provide a robust layer of protection against personal information leaks on the dark web. Whether it’s detecting compromised credentials or securing sensitive business data, Log360 will equip you to monitor and protect your organization's digital assets. This proactive approach ensures that you remain vigilant and prepared in the fight against emerging dark web threats before they cause significant damage.
What should I do now?
You can begin your journey of staying safe on the dark web through the links below:
- Schedule a product tour with us to see Log360's powerful dark web monitoring capability in action.
- Download a free trial of Log360 to try out the solution in your environment.
- Explore use cases on the type of dark web threats that can be detected.
- Why monitor the dark web?
- What are dark web search engines?
- How to search for personal information leaks on the dark web
- Personal information leak monitoring with Log360