The clock starts ticking the moment an employee finds encrypted files or a ransomware note, or when your SIEM tool throws a ransomware detection alert. The first 24 hours are the most crucial time to deploy everything in your arsenal to mitigate the effects of the attack. This blog discusses a step-by-step incident response plan you can adopt with a few prerequisites. But first, here's a brief introduction to ransomware.
A ransomware attack is a cyberattack wherein malicious software encrypts the victim's files or data and holds it for ransom. The attackers demand a ransom payment from the victim to provide the decryption key to restore access to the data or files. There are five stages of any ransomware attack: Initial exploitation, malware installation, backup destruction, encryption, and blackmail or extortion.
There are three fundamental requirements that need to be met in order to effectively respond to a ransomware attack.
Your ransomware response strategy for the first 24 hours should primarily involve steps to contain and investigate the attack. Containment and impact assessment involves thoroughly analyzing the situation to learn about the attack's severity. The second stage, investigation and response, is where the malware is more closely examined and specific response measures are taken.
The containment and impact assessment stage involves detaching the reported user and host from the network as the first action. Following this, you can notify and assemble your incident management team and further assess the situation as described in the steps below.
Isolate the user and the machine in which ransomware was reported from the rest of the network. Files may have already been encrypted, and isolating the device may hinder business operations, but it's a critical decision. Moreover, containment helps forensic analysts work on the infected machine safely and proceed with restoration.
Notification: Alert the relevant stakeholders and assemble a team of decision-makers, analysts, and system admins for the next set of actions. It is vital to have these roles clearly defined.
Start with the infected file location: Ransomware creates TXT and HTML files at encrypted file locations to deliver the ransom note. Check for user details of such newly created files. This will reveal information about the user account being used to perform ransomware operations.
If the encrypted files were found in the shared network folder, check the file owner permissions to identify other possibly affected users.
Isolate all the hosts and check the associated users' risk scores and privileges.
Check for Active Directory compromise: Are users unable to access their AD accounts? Look for changes to AD users, groups, and DCs. This could denote that the ransomware has been potentially deployed at scale with AD access.
Checking the state of backup storage is a vital component of impact analysis because many ransomware programs tend to delete backups before starting the encryption process.
The investigation and response stage begins with probing into the malware variant, then identifying and plugging the malware entry points as listed below.
Identify the malware variant: Ransomware typically follows a specific attack pattern, and identifying the pattern can lead to ascertaining the ransomware variant. Initial exploitation method used, executable file names and hashes, targeted file locations and types, and process names are some areas to look during your investigation.
Closely examine the ransom note: The text and image in the ransom message can help in identifying the threat group and the ransomware variant. The ransom message is also a crucial artifact to include in your incident report.
Initial access vector: Phishing and email attachments are the most widely used ransomware delivery methods. Other entry methods include drive-by downloads and exploitation of software vulnerabilities.
The below image shows the critical ransomware response actions to take in the first few hours.
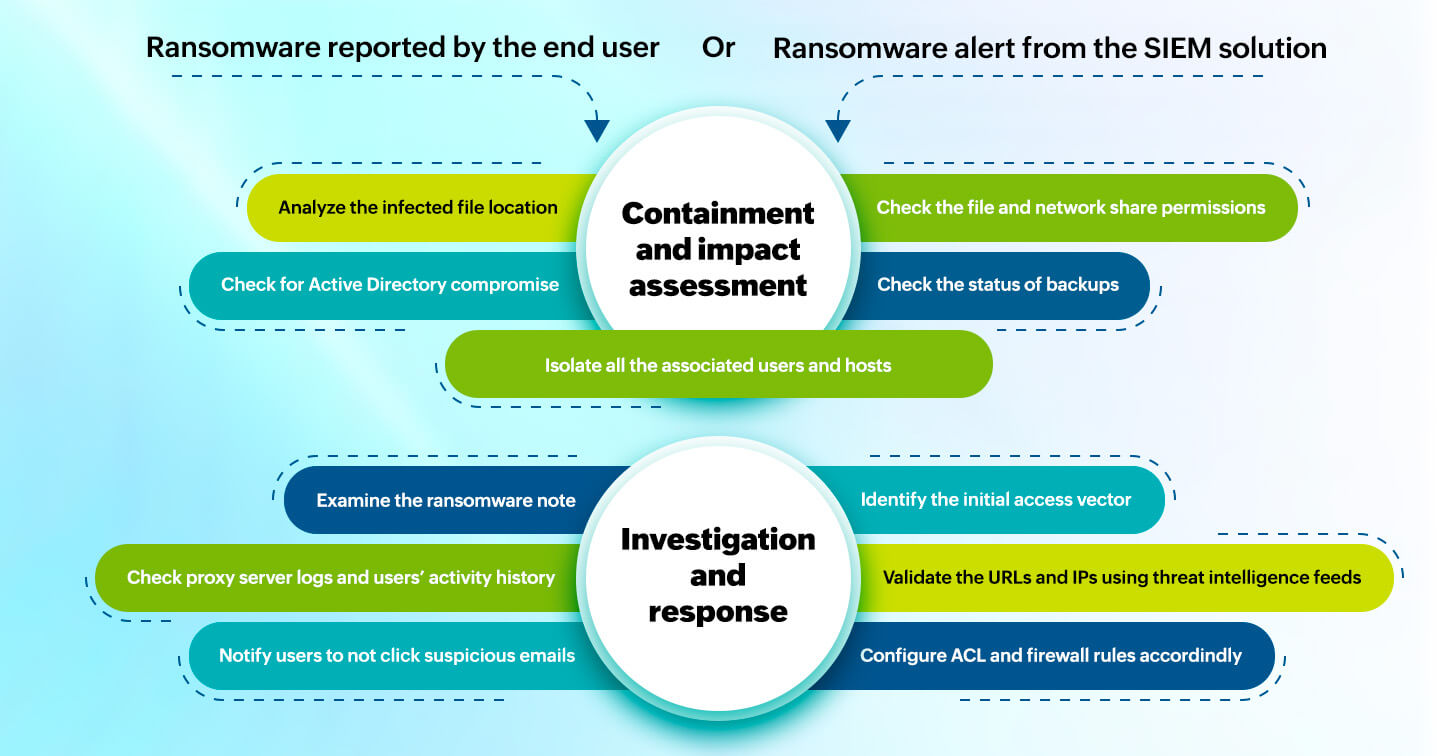
The aforementioned steps comprise a ransomware incident response playbook for the first 24 hours after detection. Backup restoration can only be started after complete containment, impact assessment, and initial investigation. It is essential to conduct test runs for backup restorations.
Create incidents and tickets with all the evidence gathered for further forensic analysis and cleanup. The typical evidence includes user and host details, associated URLs and IPs, IoCs, file locations, process names, and all associated event logs. You can notify the board, public relations, and legal team at this stage.
Event correlation: A SIEM solution with real-time log collection enabled can correlate events from different sources like workstations, servers, firewalls, and antivirus solutions to identify malware patterns and raise alerts.
Response workflows: Outbound firewall rules can be set using workflows after corroborating IPs and URLs with real-time threat intelligence feeds. Automated workflows can also execute AD actions, such as disabling users and workstations, running scripts, and stopping processes. Emails and SMS alerts to notify users and IT admins can be automated based on conditional logic.
Forensics: Drill through logs to perform root-cause-analysis at a granular level using historical and real-time log data.
File integrity monitoring and data loss prevention: Locate and classify sensitive files, track permissions, and track file modifications and creations.
Incident management: Automatically create incidents, assign technicians, and track the status of any malware or ransomware detections.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.