Individual events often don't look suspicious on their own, but when they are considered in the context of other events, a bigger picture that could indicate a security threat develops. Correlation is the process of identifying a sequence of events, across one or more devices, which are all related, and form a single notable incident. Some benefits of event correlation-based threat detection include reduced alert fatigue, lower false positives, and real-time attack detection.
Event correlation can be performed using time-consuming manual methods or through automated tools (such as SIEM solutions), which use rule-based detection to collect and correlate events from various sources in real time. By analyzing the correlated events, security teams can identify potential threats and take proactive measures to mitigate them before they cause harm to the system or network. This blog discusses three interesting benefits of event correlation that ease and enhance threat detection in your network. The three benefits of using event correlation in your SIEM are:
You can use correlation rules to detect security risks. You can consolidate multiple individual events that happen over a period of time to generate one correlation alert. Figure 1 below shows a correlation rule built to detect and alert repeated application crashes on Windows. The security analyst will now have only one alert to investigate.
Action 1 in the image below triggers a single correlation alert when an application crashes multiple times in a given time.
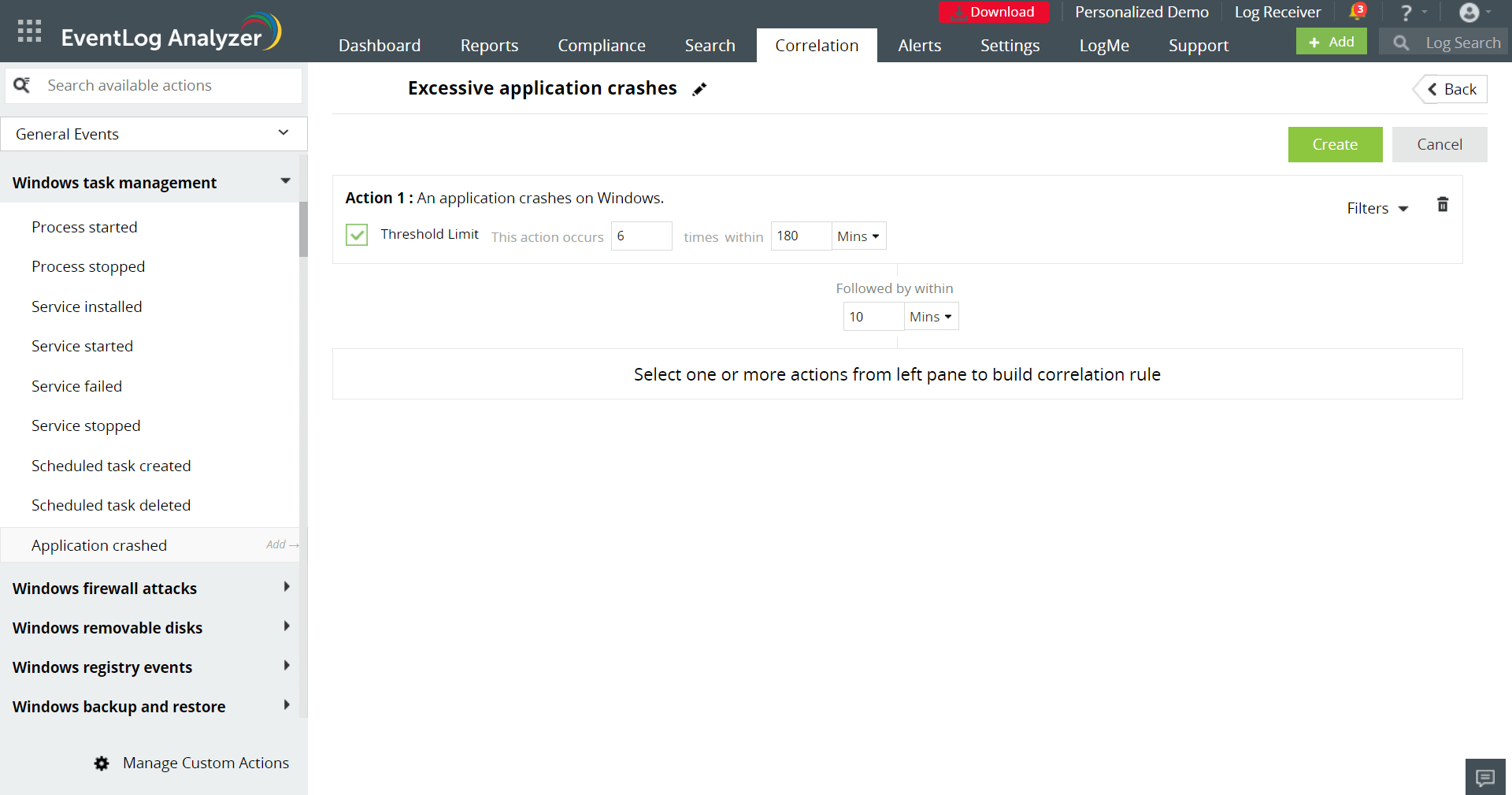 Figure 1: Correlation rule to detect excessive application crashes
Figure 1: Correlation rule to detect excessive application crashes
You can use a correlation rule to validate an alert from one source using another source or device. You can create a rule to be notified whenever a request to your webserver from a URL which is tagged malicious is seen, and your IDS device detects a possible attack from the same IP Address. The correlation rule in Figure 2 confirms a malicious URL detected by a threat intelligence feed (Action 1) with what is detected by an IDS device (Action 2). We set the condition filter to link the client IP address in Action 1 with the source IP address in Action 2. This will help corroborate a possible attack on your web server and reduce false positives.
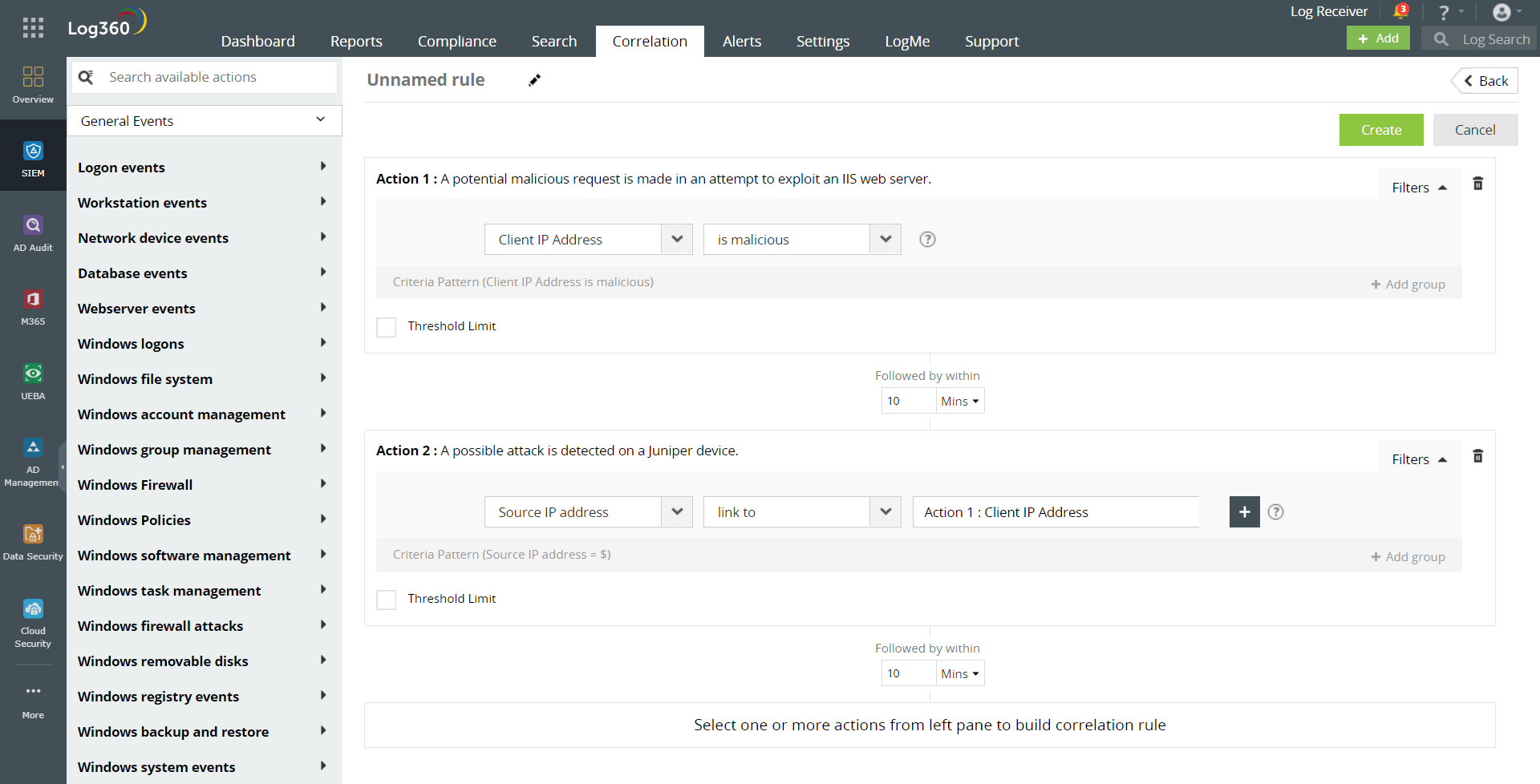 Figure 2: Correlation rule to detect and validate dubious URL requests
Figure 2: Correlation rule to detect and validate dubious URL requests
You can create a correlation rule to detect any specific malware or ransomware behavior by building the sequence of actions to look for. The correlation rule, as shown in Figure 3, checks for three sequential actions, each occurring within a time interval of 10 minutes: interaction of network devices with a malicious IP, a file downloaded to the Downloads or TEMP folder, and the start of the Volume Shadow Copy Service (VSS) process. This detects any malware that enters through phishing or drive-by download, downloads the payload to the TEMP folder, and starts the VSS process to delete Windows backups.
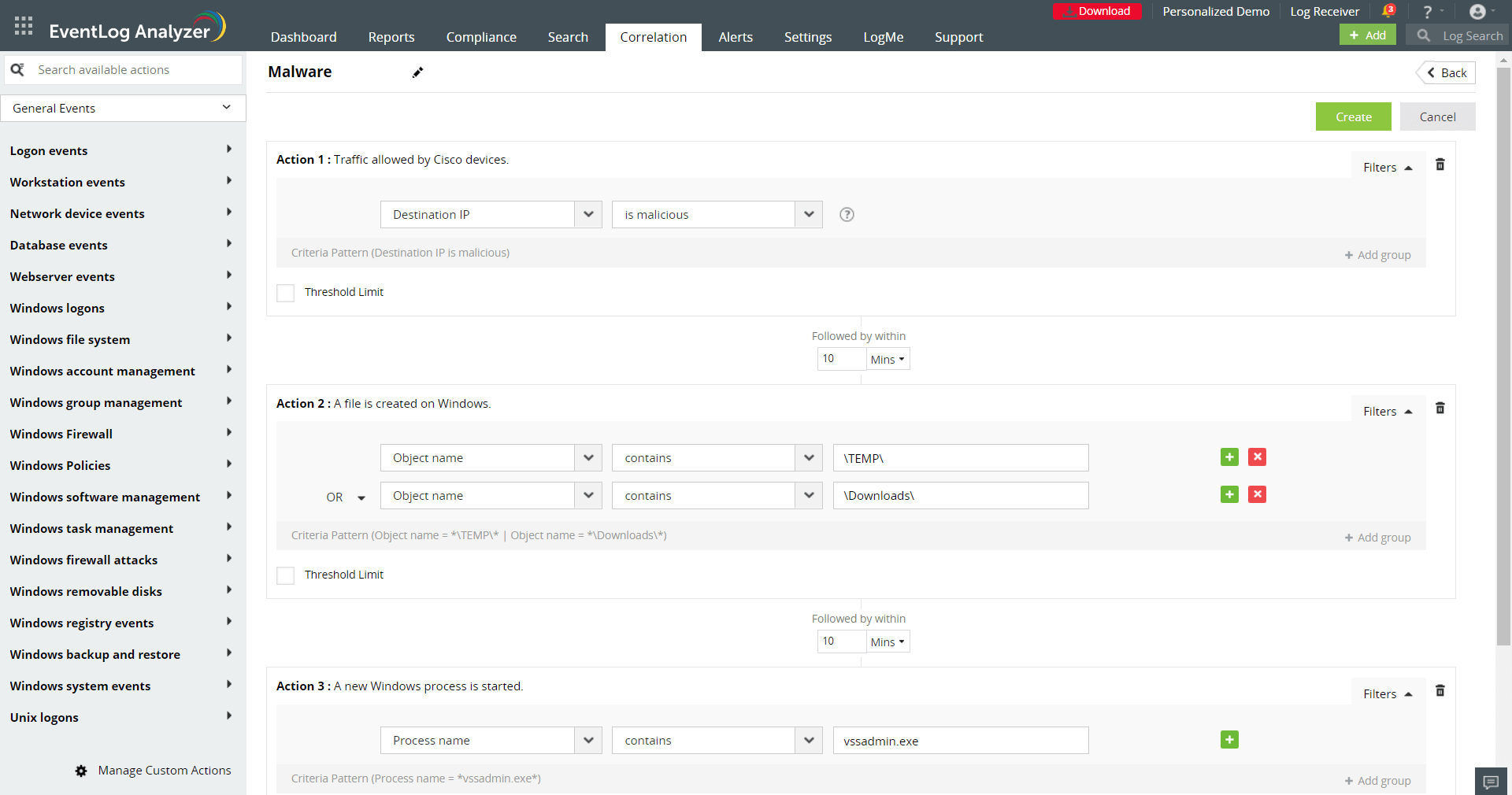 Figure 3: Correlation rule to detect malware
Figure 3: Correlation rule to detect malware
An effective SIEM solution comes with predefined correlation rules and also lets users build custom rules for specific attack scenarios. After the correlation rule is triggered, you can create incidents automatically and implement mitigation strategies. If you are interested in learning how a SIEM solution can help with incident creation and management, check out this blog.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.