with integrated DLP and CASB capabilities that detects, prioritizes, investigates, and responds to security threats. It provides holistic security visibility across on-premises, cloud, and hybrid networks with its intuitive and advanced security analytics and monitoring capabilities.
SOC analysts are the unsung heroes of the digital world, constantly monitoring every aspect of the network, reacting to cyber emergencies, and adapting to new threats to keep an organization safe.They work tirelessly behind the scenes, analyzing vast amounts of data to detect anomalies before they escalate into major breaches. Their quick decision-making and expertise help minimize damage, ensuring business continuity even in the face of sophisticated cyberattacks. Without them, organizations would be vulnerable to ever-evolving threats that could compromise sensitive data and operations. But still, they deal with a number of challenges, including:
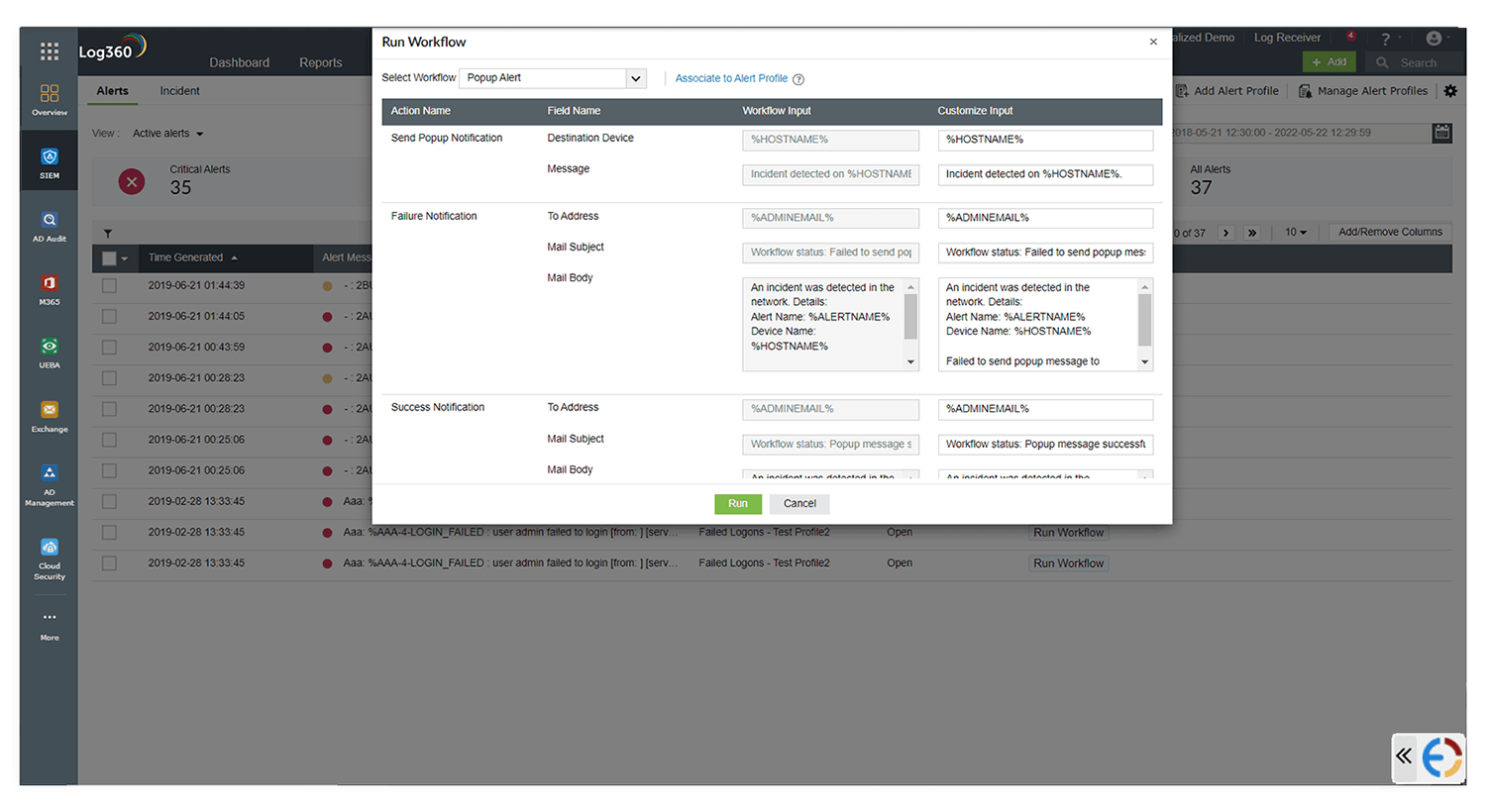
With Log360, alerts can be categorized into three severity levels (Attention, Trouble, and Critical) which can then be prioritized and remediated accordingly. Incident response workflows can also be executed automatically when an alert is triggered.
With the addition of Smart Threshold in Log360, analysts can easily specify the desired time interval while creating alerts. The ML algorithm evaluates the environment and creates a baseline with the expected number of events for a few hours, which it will modify if it detects an actual threat.
You will be able to actively identify and eradicate hidden risks, therefore eliminating alert fatigue, with the use of preconfigured and customizable threat feeds, fast alert notifications, forensic reporting features, and an integrated ticketing system.
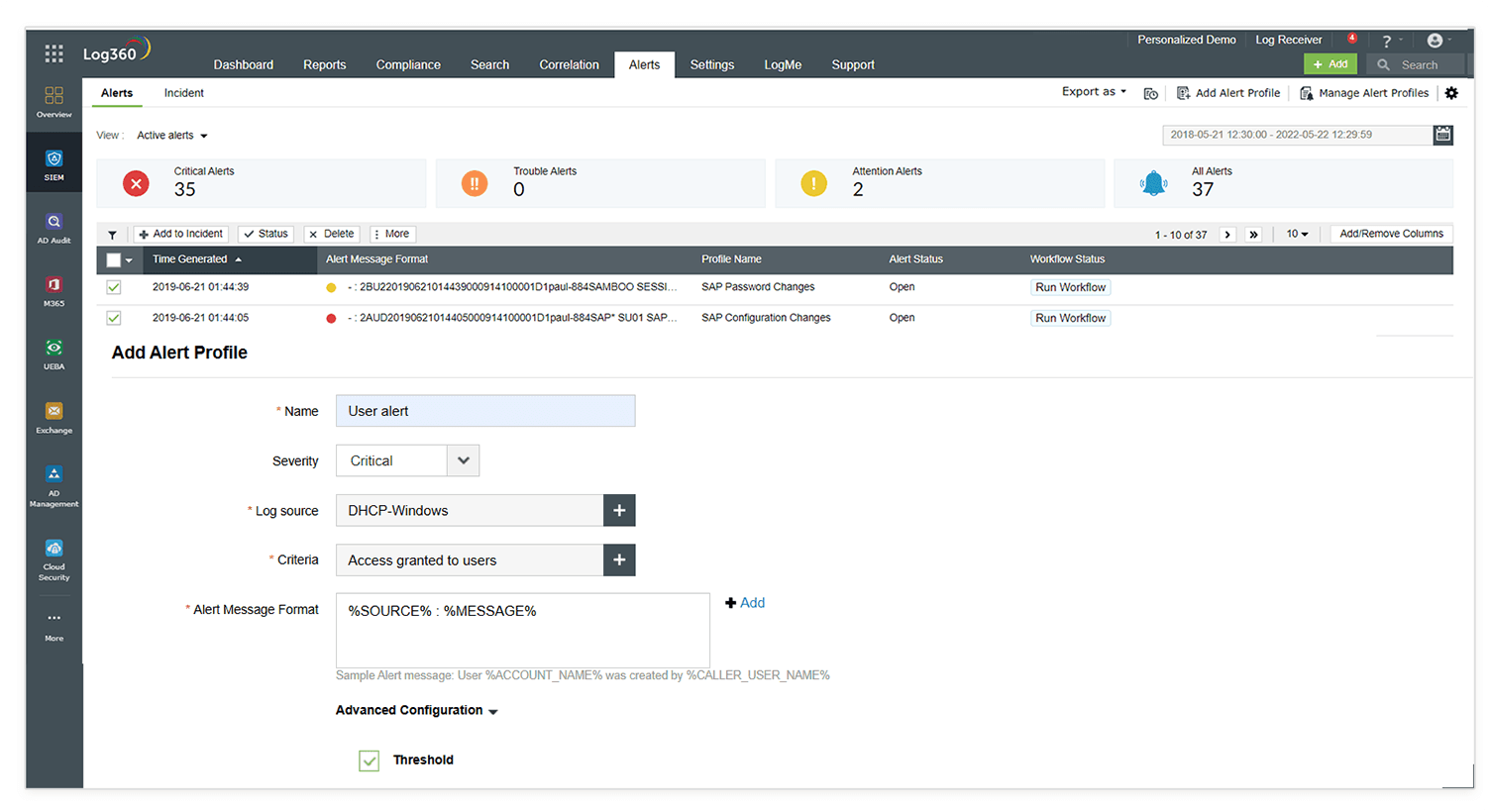
A robust search engine helps identify hidden threats by aggregating data from diverse sources in real time and using advanced filtering to detect anomalies and critical indicators efficiently. It enables swift analysis and prioritization of potential risks for proactive action.
Log360, with its robust search engine, lets you search for specific criteria in your entire log bucket and export the results. This helps with performing root cause analysis for security incidents. This search can be performed with the help of basic and advanced SQL based queries, wild card, Boolean, and logical operators.
Also, the advanced search criteria let you use multiple search criterion groups simultaneously instead of creating queries from scratch. Filters can also be applied to refine searches by event type, severity, and other attributes.
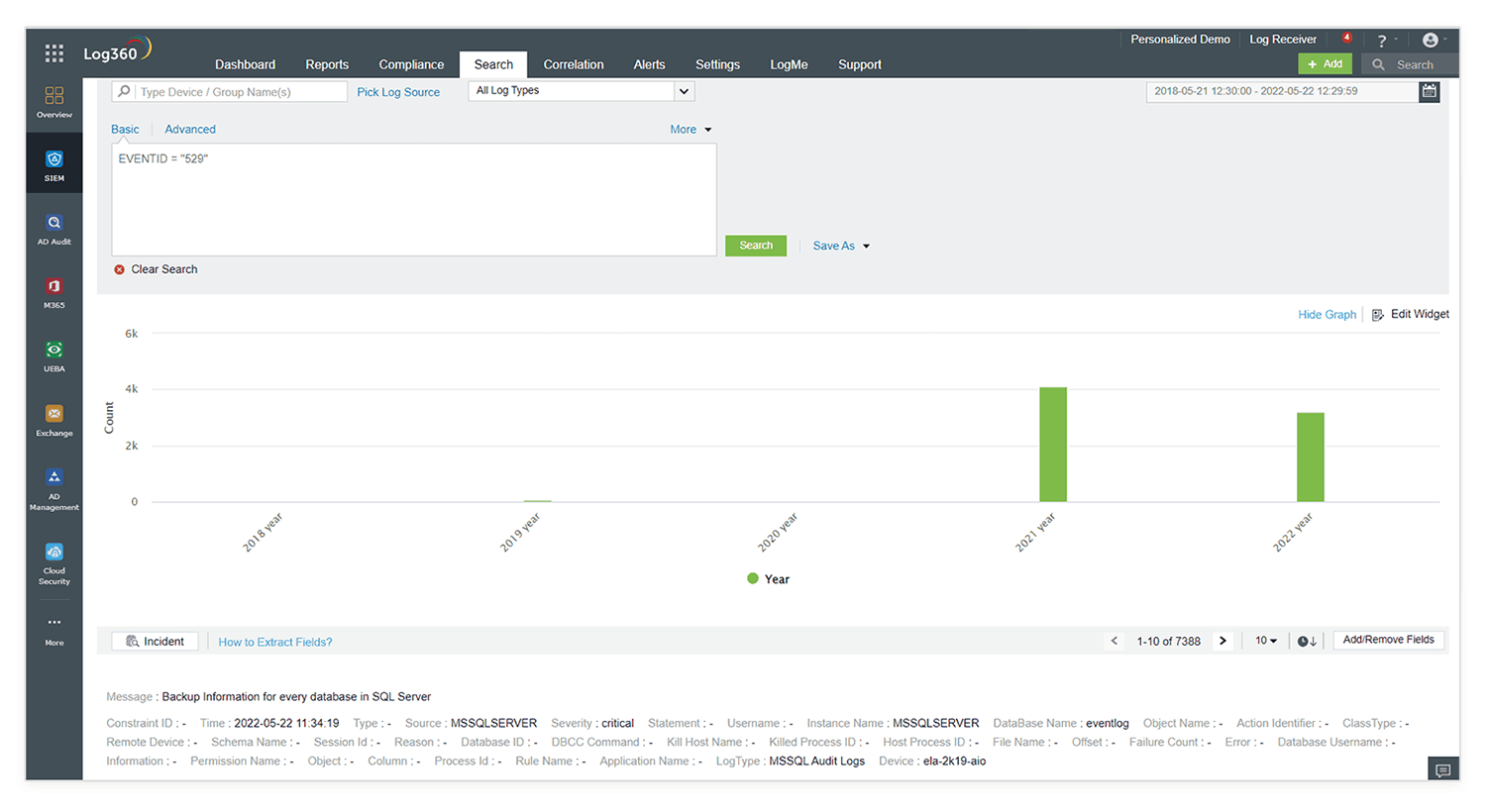
By providing insights into important indicators like mean time to detect (MTTD), mean time to respond (MTTR), and more, Log360's incident dashboard helps organizations streamline and improve their security operations. Using this dashboard, SOC analysts can keep tabs on recent and important incidents, as well as ongoing and unresolved ones, and learn about their workload. This will help them prioritize and triage the incident resolution.
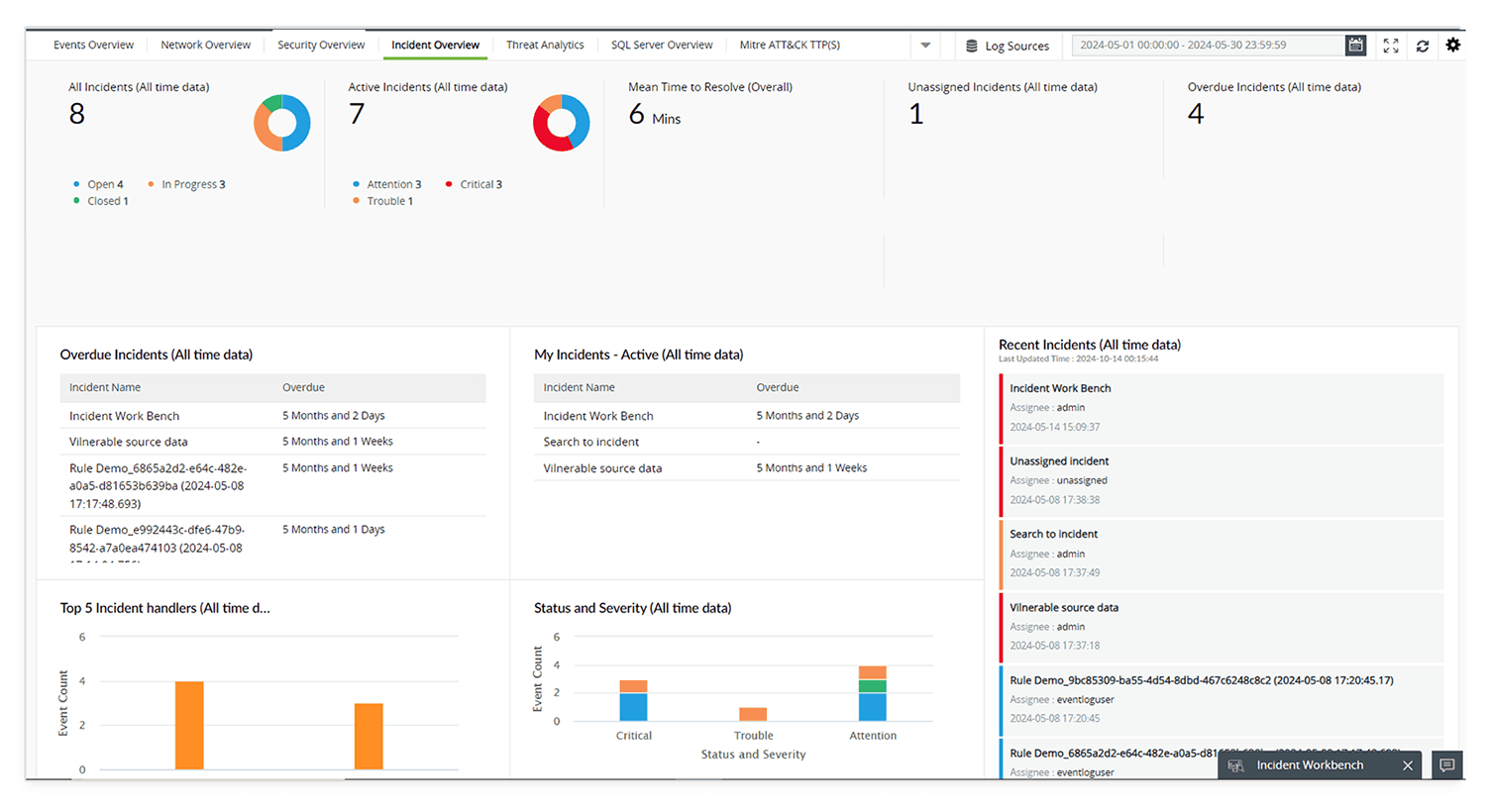
Log360 UEBA is powered by ML, and can detect anomalies by recognizing subtle shifts in user activity. It continuously analyzes user activity patterns to identify abnormalities, such as unusual or suspicious behavior. Based on the anomalies, it assigns risk scores to users and entities in your network. This helps you identify, qualify, and investigate threats that might otherwise go unnoticed, by extracting more information from your logs to give better context.
Log360 provides full visibility into AWS, Azure, Salesforce, and GCP with predefined reports providing deep insights into user activity, identity and access management, network security, cloud functions, GCP resource management, and more.
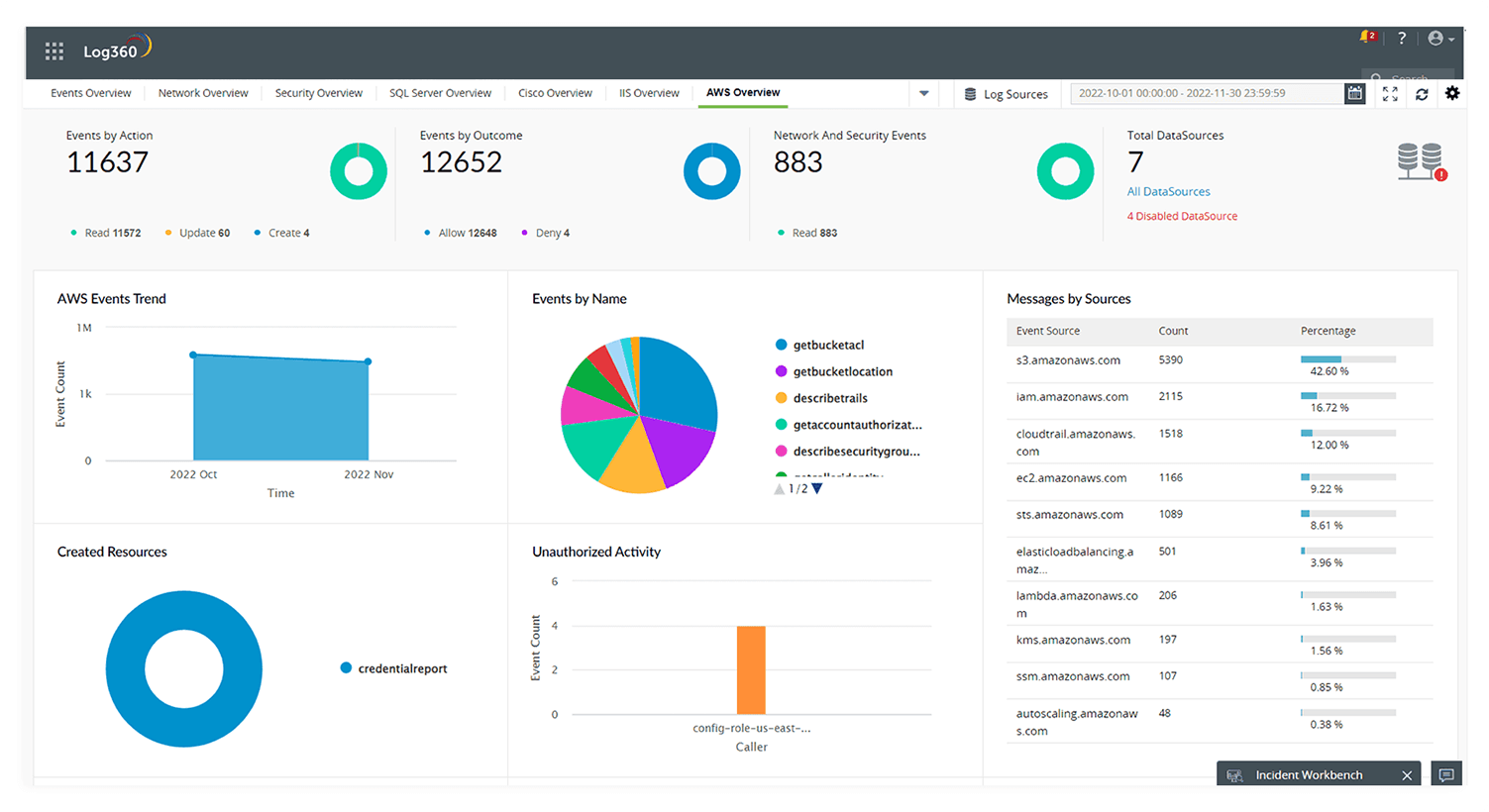
Log360 integrates with Constella Intelligence to allow users to identify personal information that has been leaked on the dark web, such as credit card numbers, email addresses, usernames, and other credentials. This integration provides you with a key first line of defense against supply chain threats. Within an organization's network, Log360 continuously gathers and examines logs and events data from several sources. It provides early warning and instant visibility into possible threats.
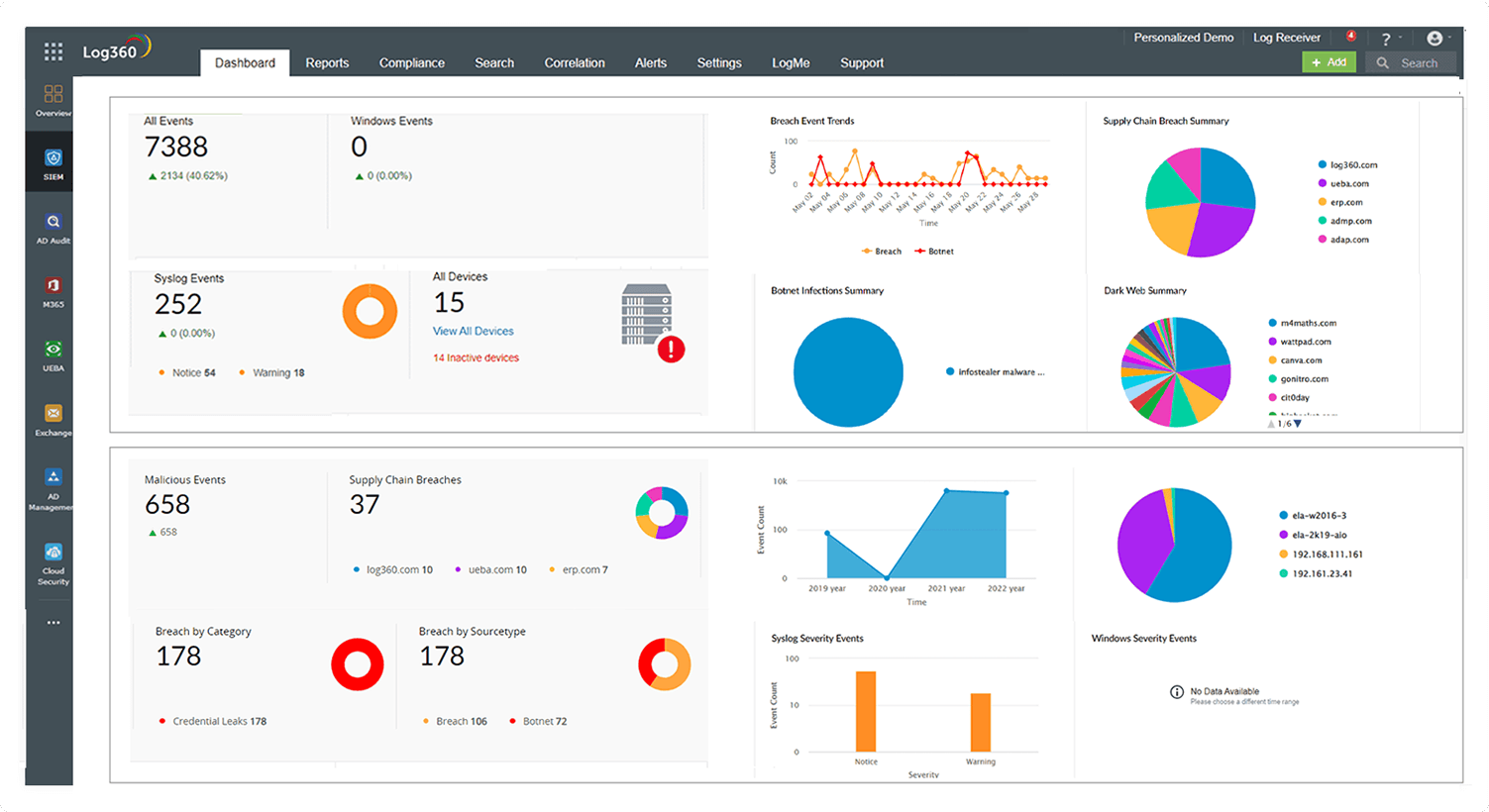
Log360 is a SIEM solution that provides UEBA, CASB, and SOAR capabilities in a single platform, enabling your security teams to detect and respond to threats from one comprehensive console.
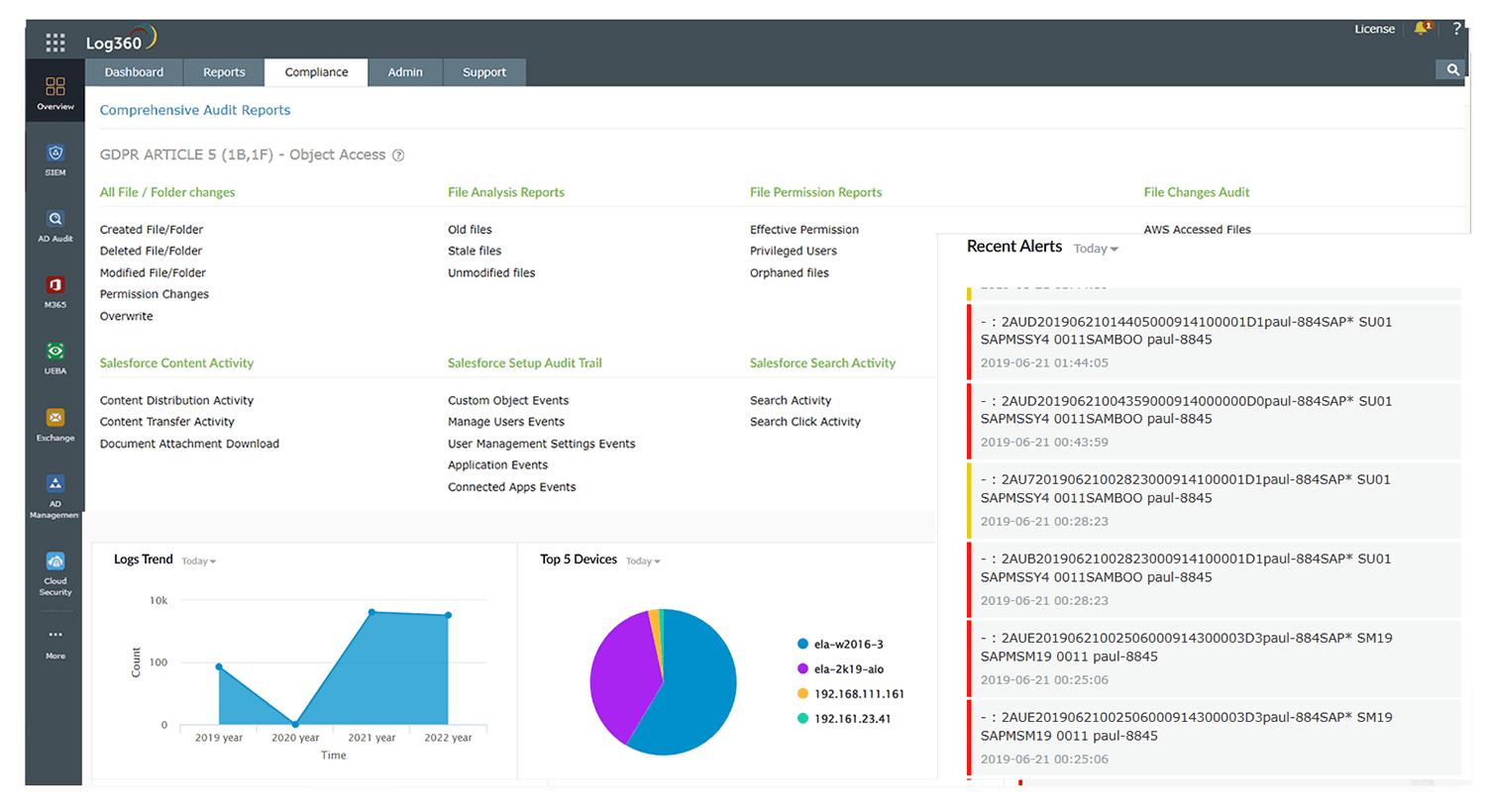
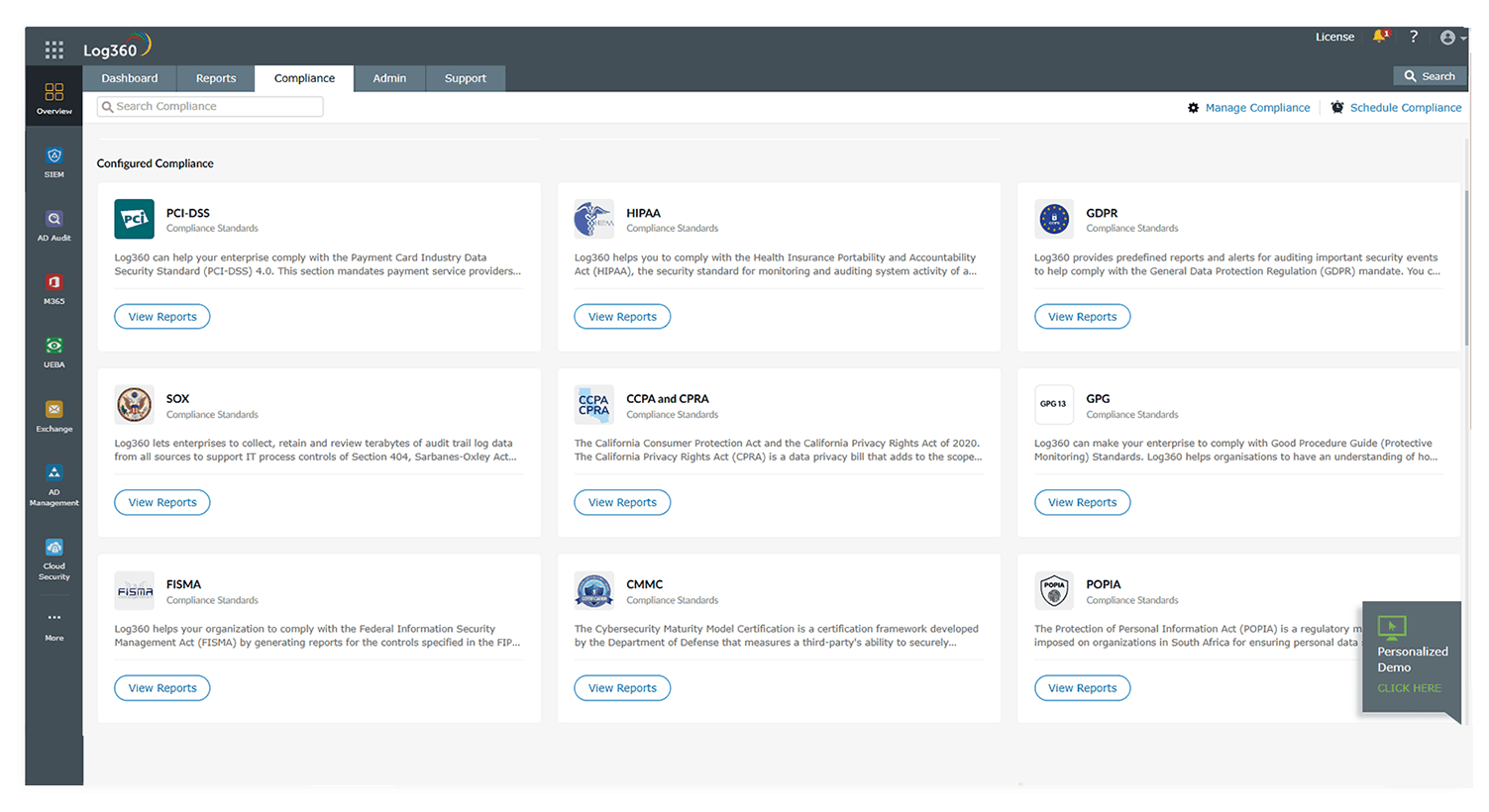
Log360 helps organizations fulfill the compliance requirements by providing audit-ready reports for a wide range of policies, including PCI DSS, SOX, HIPAA, FISMA, GLBA, ISO 27001, and the GDPR. These reports contain granular details of what, when, where, and how various activities occur within an organization.
Log360 facilitates the development of automated incident response workflows and response playbooks. Once a threat has been detected, the security operations center can start the required remediation procedures, collect forensic evidence, and take predetermined actions to contain the issue. This reduces mistakes and speeds up incident response.
| Key security challenge | Log360's capabilities |
|---|---|
| Detecting and responding to security incidents |
|
| Handling phishing attacks |
|
| Dealing with insider threats |
|
| Responding to DDoS attacks |
|
| Compliance reporting and audit trials |
|
Log360 is an all-in-one SIEM solution that provides exceptional bang for your buck.
I like that we can do GDPR reporting and audit anyone accessing sensitive patient information. It helps with compliance and reporting, which is heavily relied on by the NHS.
Log360 won the 2023 Cybersecurity Excellence Award for IAM and identity governance (Asia)
Log360 won the 2022 Fortress Cyber Security Award for Authentication and Identity.
A unified SIEM solution with integrated DLP and CASB capabilities, Log360 detects, prioritizes, investigates, and responds to security threats.It combines threat intelligence, machine learning-based anomaly detection, and rule-based attack detection techniques to detect sophisticated attacks and offers an incident management console to help manage detected incidents. Also, the workflow feature helps in order to remediate threats.