A security operations center (SOC) is a centralized function that monitors, detects, analyzes, and responds to cybersecurity threats and incidents in real time. The SOC serves as the first line of defense for safeguarding an organization's networks, systems, and data, and it is staffed with knowledgeable analysts and outfitted with cutting-edge tools. It operates 24/7, ensuring around-the-clock monitoring of possible threats across infrastructure, apps, and endpoints.
Key SOC functions include threat detection, incident response, vulnerability management, and threat intelligence. A SOC relies on technologies like security information and event management (SIEM), cloud detection and response (CDR), firewalls, and endpoint detection and response (EDR) to identify and mitigate risks efficiently. Organizations can maintain a strong security posture by integrating technology, people, and procedures. SOCs can be in-house, outsourced, or a combination of both, based on the needs and scale of the company.
Key functions of a SOC
Protecting an organization's digital assets through the detection, mitigation, and prevention of cybersecurity threats is the main responsibility of a managed SOC. These functions include:
- Threat monitoring: One of the main functions of a SOC is real-time monitoring of the organization network. With effective log management tools, SOCs monitor every action that takes place in a network to detect any malicious activities. ManageEngine Log360 caters to SOC teams with support for over 750 types of log sources across the network for extended network monitoring.
- Threat intelligence analysis: Collecting, evaluating, and using telemetry information about risky IPs, domain information, indicators of compromise (IoCs), and indicators of attack (IoAs) to improve defenses and get one step ahead of attackers plays a major role in preventing threats from happening. After detection, analysts have to perform a detailed investigation to understand the attacker's tactics. A successful investigation can reveal insights into the initial access point of the attacker, zero-day vulnerabilities, and more.
- Threat hunting: In a SOC, threat hunting plays a crucial role in strengthening an organization’s defense strategy. It involves proactively searching for sophisticated or hidden threats that automated tools could miss, leveraging human expertise and advanced techniques. By integrating threat hunting into SOC operations, organizations can detect and respond to advanced attacks, reducing the risk of potential breaches.
- Incident detection: Detecting an intruder within the network as quickly as possible is the goal. By monitoring malicious activity such as abnormal process execution, firewall setting changes, and more, analysts are able to detect attackers swiftly using tools like SIEM, intrusion detection systems (IDSs), intrusion prevention systems (IPSs), and EDR.
- Incident response: Similar to detection, the mean time to respond (MTTR) is also critical. This includes the time taken to determine the underlying cause, mitigate the attack , and restore the systems. Allowing the attacker to linger within the network can result in lateral movement, gaining credential access, and enablement of other methods that allow them to propagate within the network and make response difficult. This is where features like security orchestration, automation, and response (SOAR) come in handy, which can help SOC teams swiftly respond with predefined workflows without requiring human intervention. Reduce your team's MTTR with ManageEngine Log360, a unified SIEM solution with integrated SOAR capabilities.
- Vulnerability management: SOC analysts identify weaknesses in systems and applications, ensuring regular updates and patches to reduce the attack surface.
- Log management and analysis: SOC analysts collect, classify, and examine logs from different systems in order to monitor activity and identify anomalous trends.
- Compliance and reporting: Compliance and reporting are integral to SOC operations , as they ensure the organization adheres to regulatory standards and industry best practices. The SOC generates reports on security events, incidents, and risk management efforts for audits and post-incident analysis. These processes also help identify gaps, mitigate risks, and provide transparency to stakeholders and auditors.
- Documentation: SOC analysts are also tagged with the task of effective documentation. Documentation helps them streamline the incident response process. By documenting the actions taken in an attack, analysts can respond swiftly to similar threats in the future.
Suggested read: A SOC analyst's journey and strategies for improvement.
Understanding the SOC structure: Key components and roles
In order to ensure effective and efficient cybersecurity operations, a SOC is designed to integrate people, procedures, and technology. Its structure can vary depending on the organization's size and complexity, but typically includes the following components (refer to Figure 1):
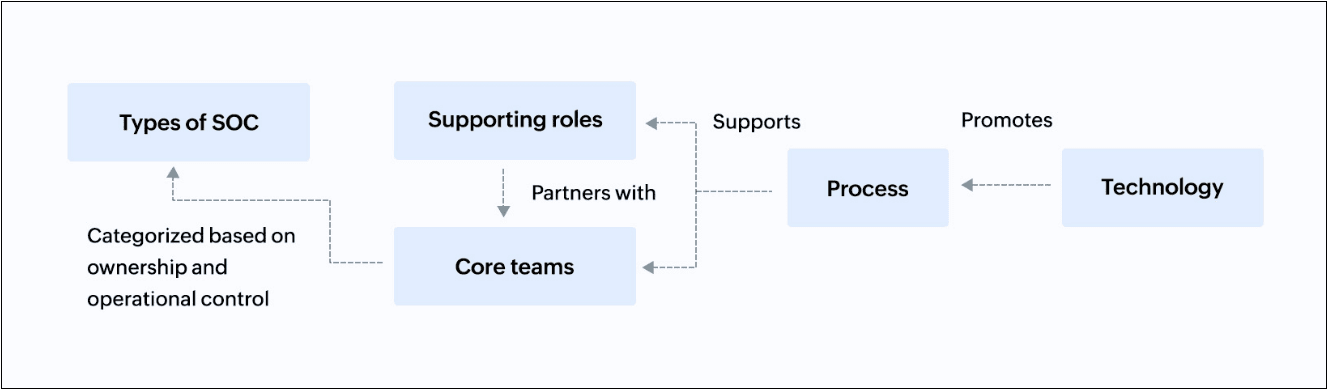
Figure 1: SOC structure
1. Core teams
To ensure thorough cybersecurity SOC monitoring, threat identification, and incident response, a SOC framework/team is made up of people with a variety of functions and skill sets. The SOC team members are as follows:
- SOC analysts:
- Tier 1: Monitor alerts, prioritize incidents, and escalate as needed.
- Tier 2: Investigate incidents, perform in-depth analysis, and coordinate responses.
- Tier 3: Address complex and sophisticated attacks through advanced analysis and threat hunting.
- Incident responders: Specialists who handle containment, mitigation, and recovery during security incidents.
- SOC manager: Oversees SOC operations, ensures efficiency, and acts as a liaison between teams and stakeholders.
- Threat hunters: Focuses on proactively identifying hidden threats using advanced techniques and tools.
To learn more in depth about the different SOC roles and their key responsibilities, visit this page.
2. Supporting roles
- Threat intelligence team: Gathers and analyzes data on emerging threats to strengthen defenses.
- Forensic experts: Examines breaches to identify attack routes and reduce potential risks.
- Compliance and audit specialists: Ensures adherence to cybersecurity standards and prepares for regulatory audits.
3. Processes and workflow
- Alert management: Security tools generate alerts that analysts review and triage.
- Incident response plan: Definite procedures for identifying, responding, and recovering from incidents.
- Knowledge sharing: Keeping a reference database of threat intelligence and incident learnings.
4. Technology stack
- SIEM: Aggregate and analyze logs for threats.
- EDR: Protect endpoints from attacks.
- Firewall and IDS/IPS: Block unauthorized access and detect intrusions.
- Threat intelligence platforms: Provide data on emerging threats and vulnerabilities.
5. Types of SOC
- In-house SOC: Fully staffed and managed by the organization.
- Outsourced SOC (managed security service providers, or MSSPs): Third-party management for organizations lacking resources.
- Hybrid SOC: Combines in-house efforts with outsourced support for flexibility and scalability.
This methodical approach assures that the SOC is prepared to effectively handle threats in accordance with the organization's security plan.
Exploring various SOC models
An organization's framework or method to structure, operate, and manage its SOC is known as a SOC model. It outlines how the SOC team uses technology to defend against cybersecurity threats and connects with organizational procedures. There are various SOC models to suit different organizational objectives, resources, and needs.
The choice of SOC model depends on factors such as:
- Size and complexity of the organization.
- Budget and resources available.
- Regulatory and compliance requirements.
- Level of control and customization needed.
Each SOC model has unique strengths and trade-offs, and organizations often adapt or combine elements to meet their specific cybersecurity needs. The table below represents various SOC models and how they function:
| SOC model | What is it? | What are the advantages? | What are the disadvantages? |
|---|---|---|---|
| In-house SOC | A SOC that is entirely built, managed, and operated by an organization's internal team is known as an in-house SOC. This paradigm ensures greater alignment with business objectives and regulatory standards while providing complete control over security operations. For in-house SOCs to be effective, a large investment in knowledgeable staff, cutting-edge equipment, and frequent updates is necessary. Despite requiring a lot of resources, it is perfect for businesses handling extremely sensitive data or those with complicated security requirements. | Full control, tailored security measures, close integration with organizational processes | High cost, requires skilled personnel and continuous maintenance |
| Outsourced SOC | Often known as an MSSP, an outsourced SOC is a SOC run by a third-party supplier. With the help of this approach, businesses can hire outside professionals to handle cybersecurity tasks like threat detection, incident response, and monitoring. It is an affordable option for businesses without the resources or expertise to manage an in-house SOC. | Scalability, access to cutting-edge technologies, and around-the-clock monitoring without heavy investment in personnel or infrastructure | Limited customization, less control, and potential delays in response |
| Hybrid SOC | A hybrid SOC combines both in-house and outsourced resources to manage cybersecurity operations. According to this strategy, a company uses external MSSPs for additional expertise or scalability while keeping its own internal security team for strategic oversight and important duties. This approach offers a balance between control and cost efficiency, allowing organizations to benefit from external resources while retaining some autonomy. Organizations with limited internal resources or differing security requirements are best suited for hybrid SOCs. It offers versatility in handling security events and speeding up reaction times. | Flexibility, shared responsibilities, access to external expertise while retaining some control | Requires careful coordination between internal and external teams |
| Virtual SOC | A virtual SOC operates without a physical location, leveraging remote teams and cloud-based tools to manage cybersecurity functions. Without a centralized office, it allows organizations to monitor, identify, and react to risks from any location.Businesses with a dispersed staff or no physical infrastructure are best suited for this strategy. | Cost-efficient as it reduces overhead costs, is easy to scale, and is accessible from anywhere | Relies heavily on reliable cloud services and requires strong coordination between remote team members |
| Co-managed SOC | A co-managed SOC is a collaborative model where an organization’s internal security team works alongside a third-party MSSP to manage security operations. By pooling the resources and experience of both internal and external teams, this model enables shared accountability for threat detection, incident response, and monitoring. While keeping some degree of control and supervision, it provides organizations with better security coverage. This approach is ideal for organizations that require external expertise but also want to keep some operations in-house. | Offers flexibility, scalability, faster response, shared expertise, and cost-effectiveness while balancing control and outsourcing | Requires clear communication and role definitions |
| Command SOC | A command SOC is a centralized SOC that oversees and manages multiple regional or local SOCs within an organization. It coordinates global cybersecurity efforts, ensuring consistency in security policies, monitoring, and response strategies across various locations. Multinational corporations usually utilize this model to offer a consistent method for incident management and threat detection. The command SOC provides centralized visibility into the whole threat landscape and ensures that regional teams are in line with global security objectives. | Uniform policies, global threat visibility, and improved efficiency | Complex coordination and management, which results in higher costs |
Key benefits of a SOC
Here are a few benefits of investing in a SOC team for your organization:
- Provides 24/7 monitoring, ensuring continuous surveillance and rapid detection of cybersecurity threats.
- Minimizes damage and downtime by improving the organization's capacity to respond swiftly to security events in order to mitigate potential security incidents.
- Consolidates security data from various systems, improving threat detection and enabling more effective analysis of security events.
- Helps in maintaining compliance with industry regulations and standards by generating reports and maintaining security logs for audits.
- Enhances the organization's overall security posture by using proactive threat hunting to identify vulnerabilities before they are exploited.
- Allows an organization to focus on its core business operations while the cybersecurity professionals handle security concerns.
SOC tools and technology stack
- SIEM: SIEM, being a comprehensive approach to cybersecurity, involves collecting, correlating, and analyzing security data from various sources across an organization's IT infrastructure. It aggregates log data from network devices, servers, and applications, providing a centralized platform for real-time monitoring and threat detection. By correlating events and identifying patterns indicative of potential security incidents, SIEM enables rapid response to threats, facilitates compliance with regulatory requirements, and enhances overall security posture through proactive threat management and incident response. Additionally, SIEM solutions often incorporate features such as user and entity behavior analytics and automation to streamline security operations and improve efficiency.
- SOAR: SOAR is a solution that converges three primary security functions—management of threats, incident response, and automation of security operations—into a single holistic security solution. SOAR aims to alleviate the strain on IT security teams that manage an overwhelming number of network alerts; overlooked alerts will negatively impact security. SOAR ensures that threats are identified and a response strategy is implemented. The system is then automated to the maximum extent possible to run more efficiently. A novel feature of SOAR is the use of playbooks, which automate and coordinate workflows; these may include any number of disparate security tools as well as human actions.
- XDR: Extended detection and response (XDR) aims to solve the issue of siloed detections and responses across multiple security layers, like the cloud, endpoints, point solutions, and other network components. It is designed to provide rich threat intelligence. XDR solutions also offer automated analysis of different data, correlating data points across the different layers to give more accurate threat detection results.
- EDR: EDR functions as a subset of XDR. EDR solutions offer exclusive protection of endpoints by monitoring malicious activity happening on them. EDRs collect data, such as user logins and process executions, and can perform behavioral analysis to spot anomalous events.
- IDS/IPS: An IDS analyzes packets and records to find possible risks, including malware infections, illegal access attempts, or odd patterns. It also monitors network traffic for suspicious behaviors or security incidents. Rather than actively blocking or preventing assaults, an IDS only monitors network traffic and sends out notifications when it spots unusual activity. However, an IPS works in a proactive manner, actively thwarting or minimizing identified threats in real-time by using preestablished rules or signatures to stop malicious activity before it has a chance to harm the network. IDSs and IPSs are complimentary tools for network security; the IDS offers insight into possible attacks, while the IPS offers proactive defenses to counter them. Together, these tools improve the network's overall security posture.
Key challenges faced by the SOC
Challenges are not new for SOC teams. Being one of the most critical teams in every organization and the first line of defense, there are new challenges that develop daily. Here are a few common challenges that every SOC experiences.
- Analyst burnout: Averaging over a thousand alerts daily, analysts are exhausted trying to deduce alert integrity. Analysts rely on solutions such as SIEM solutions with integrated SOAR and threat intelligence capabilities that minimize false positives and reduce the mean time to detect (MTTD). Future developments, such as the autonomous SOC, can also help with this issue.
- Skill shortage: The global cybersecurity skill gap has reached a record high of four million. The supply is not meeting demand due to increased cyberattack frequency and sophistication. This is one of the main reasons that analysts face burnouts. This skill shortage is often attributed to lack of proficiency with advanced security tools, and scripting languages and high level of specialization. The specializations include security architecture; cloud security engineering; governance, risk and compliance digital forensics; network security; incident response; and application security.
Explore certifications for SOC analysts:
Read our article, Can technology help bridge the gap in cybersecurity skills?, to learn how automation and advanced SIEM capabilities play a key role in today's threat landscape.
- Staying updated with the attack landscape: In order to minimize detection and response time and conduct attack simulations within the internal network, analysts need to break down and understand how each attack propagates within the network. By analyzing the various tactics, techniques, and procedures, analysts can stay ahead of attackers to a large extent. This process, although beneficial, can be extremely tedious.
- Collaboration of distributed workforces: With the emergence of COVID-19, the era of remote work was boosted significantly. Managing security when your organization's workforce is scattered worldwide can be a difficult task. Components like unknown networks, personal devices, and potential insider threats are factors that require attention.
Suggested read: A SOC manager's dilemma: How to manage a distributed workforce
- Budget constraints: Communicating the intricacies and challenges of security to CISOs can be a strenuous process. With the attack landscape changing on a daily basis, SOCs require a budget to invest in technology, resources, and talent to become a worthy contender.
Suggested read: How to communicate your SOC's ROI and justify your security team's value
- Visibility gaps: "A new survey of 530 U.S. cybersecurity professionals at organizations with over 1,000 employees reveals enterprises lack visibility into their own data, creating significant security risks that are compounding as organizations and their employees increase artificial intelligence (AI) adoption." Understanding the gaps within the infrastructure and monitoring them at all times can be tiring.
Essential best practices for an effective SOC
The process of building an effective SOC requires constant, incremental efforts. Let's take a look at a few points that should be considered.
- Set clear goals and KPIs: Understanding the objectives of the team is crucial. Terms such as MTTD, MTTR, false positive rates, and business downtime should be second nature for any SOC analyst. Once the goals and KPIs are clear, it becomes easier for the analysts to pave their journey effectively.
- Formulate an effective incident response strategy: When an incident takes place, the environment is in complete shambles, and it can cause havoc. This is when having a preplanned incident response plan comes in handy. Each stage of the incident response process needs to be modified based on the context of the attack. Therefore, having a standardized plan that can be morphed for various attack contexts is essential.
- Inculcate a proactive approach: Destruction and wreckage can be avoided by instilling a proactive approach in your team. Practices such as table-top exercises, pen testing, and threat hunting can save your team from preventable attacks.
- Practice collaboration and information sharing: This method can phenomenally help in the progress of KPI improvement. Factors such as MTTD, MTTR, and downtime can all be minimized with effective collaboration and documentation. Documentation will etch all the efforts taken during an incident so that similar future incident efforts can be streamlined and redundancy is minimized.
Suggested read: How to choose the right SIEM solution for your SOC needs
How can a SIEM solution help a SOC?
SIEM solutions have been the backbone of security teams for decades now. Despite the rise of competing technologies that boast of being better than SIEM, SIEM solutions have remained fairly unbeatable when it comes to enterprise security. With a unified solution that brings in valuable threat intelligence, provides real-time monitoring, offers built-in detection for well-known attacks, and automates workflows to deal with threats immediately, organizations can defend themselves against most threats.
| Centralized data collection and correlation | A SIEM solution collects logs and security data from various sources (e.g., firewalls, endpoints, servers, and the cloud). This centralized view allows SOC analysts to correlate events and detect complex attack patterns that might otherwise go unnoticed. |
| Real-time threat detection | SIEM solutions offer real-time monitoring and alerting, allowing analysts to swiftly detect and respond to security issues. By automating anomaly detection, SIEM allows analysts to focus on significant risks. |
| Incident response automation | Many SIEM solutions provide playbooks and automated workflows for responding to incidents. This eliminates manual effort, improves response times, and ensures that incidents are handled consistently. |
| Enhanced threat intelligence | SIEM solutions integrate threat intelligence feeds, giving SOC analysts up-to-date information on known threats, including IoCs. This allows them to detect and manage threats proactively. |
| Comprehensive reporting and compliance | SIEM tools generate extensive compliance reports for mandates including the GDPR, HIPAA, and the PCI DSS. These reports provide insight into security posture, allowing SOC analysts to demonstrate compliance and improve organizational security policy. |
Discover how Log360, a unified SIEM solution, can supercharge your SOC.
Role of the SOC in healthcare
Critical responsibilities: Protect patient data (e.g., medical records, Social Security information, insurance information, healthcare resources like electronic health records, IoT devices, and hospital infrastructure like administrative systems).
Threats to watch out for: Ransomware attacks that deny access to patient data, unauthorized access attempts to or tampering of electronic health records (EHRs), data breaches exposing patient information, malware infections in systems that delay healthcare delivery.
SOC activities:
- Analyze security logs to identify potential external threats.
- Keep track of suspicious insider behavior, especially users with administrative privileges.
- Implement security measures and patch vulnerabilities.
- Educate hospital staff on safe system and web usage, phishing awareness, etc.
- Ensure adherence to compliance regulations, such as HIPAA and the GDPR, to protect patient data.
Role of the SOC in BFSI
Critical responsibilities: Protect financial data of clients and critical infrastructure like online banking and trading platforms.
Threats to watch out for: Unauthorized access to client accounts, DDoS attacks disrupting banking services, tampering with financial data.
SOC activities:
- Monitor network activity for the various branches spread across geographical locations for suspicious behavior.
- Keep track of suspicious insider behavior, especially users with elevated admin privileges.
- Implement security measures and patch vulnerabilities on the banking applications and employee laptops and endpoints.
- Educate employees on safe system and web usage, phishing awareness, etc.
- Ensure adherence to compliance regulations, such as FISMA, SOX and the GDPR, to protect patient data.
Role of the SOC in the education sector
Critical responsibilities: Protect student data like exam results, scholarship declarations, educational material like important research data, and institutional systems like administrative systems and student portals.
Threats to watch out for: Phishing attacks targeting administrative staff, malware infections on school systems, tampering with student records, and denial-of-service attacks disrupting online learning systems.
SOC activities:
- To improve the distribution of educational content, SOCs assist in the development and implementation of digital learning platforms.
- They monitor internet safety and ensure that teachers' and students' data is protected.
- SOCs assist educational establishments in preventing cyberthreats and assaults that interfere with classroom settings.
- They offer staff and students cybersecurity best practices training and awareness initiatives.
Role of the SOC in larger enterprises
Critical responsibilities: To monitor, detect, investigate, and respond to cybersecurity threats in real time to protect organizational assets and ensure business continuity.
Threats to watch out for: A SOC in an enterprise must watch for threats such as phishing, ransomware, malware, insider threats, DDoS attacks, data breaches, advanced persistent threats (APTs), and zero-day vulnerabilities.
SOC activities:
- SOC teams can develop clear security objectives that align with your business goals and assign clear roles and responsibilities within SOC teams regarding who handles various aspects of security.
- Implement effective access controls through MFA, follow the principles of least privilege, and perform periodic threat hunting exercises.
- Evaluate and invest in solutions that monitor behavioral activity, protect data across its life cycle, and provide response automation features.
Empower your SOC analysts
Our cutting-edge security technology can help your SOC team reach its full potential! Are you ready to improve your threat detection and response capabilities? Sign up for a personalized demo of ManageEngine Log360, a comprehensive SIEM solution that can help you detect, prioritize, investigate, and respond to security threats.
FAQ
- How does a SOC integrate with other security functions within an organization?
-
By centralizing threat monitoring, detection, and response throughout the organization, a SOC facilitates integration with other security operations. It collaborates with IT, risk management, and compliance teams to share intelligence, enforce policies, and address vulnerabilities. The SOC escalates issues to specialized teams, such as threat hunters or forensic analysts, and offers real-time insights. This cooperation ensures a unified strategy for protecting the company's resources and information.
- How does a SOC collaborate with other teams within an organization, such as network operations, IT, and compliance?
-
By exchanging threat intelligence, organizing incident responses, and making sure security rules complement corporate objectives, a SOC works in tandem with the network operations, IT, and compliance teams. It works with network operations to monitor and secure infrastructure, with IT to patch vulnerabilities and manage endpoints, and with compliance to meet regulatory requirements. Cross-functional workflows and regular communication facilitate the organization's security initiatives.
- Is compliance a function of a SOC?
- What is the typical procedure for incident escalation within a SOC?
- Monitoring tools are used to identify incidents, which are then categorized according to their impact, severity, and breadth.
- The SOC analyst performs triage, investigates the incident, and determines whether it requires escalation.
- Incidents are forwarded to specialized teams like threat hunters or forensic specialists, or to higher-tier analysts (such as Tier 2 or Tier 3) based on their level of complexity.
- Depending on the circumstances, critical incidents are forwarded to the appropriate stakeholders, including management, network teams, or IT.
- To ensure a coordinated response and resolution, the SOC keeps track of all findings and actions and provides timely updates.
- After resolution, incidents are reviewed to improve processes and prevent recurrence.
- What are the different levels of maturity for a SOC, and how can organizations assess their SOC maturity level?
- Initial or ad hoc: The SOC relies on manual efforts and irregular procedures, and it functions reactively with few processes.
- Repeatable: Although basic procedures are established, they lack standardization and adequate documentation. Partially automated detection and reaction are used.
- Defined: Processes are standardized, documented, and consistently followed. The SOC uses advanced tools and begins proactive activities like threat hunting.
- Managed: The SOC uses performance measurements, maintains continual improvement, and is well integrated with other organizational functions.
- Optimized: To keep ahead of risks and drive innovation, the SOC uses automation, artificial intelligence, and predictive analytics to operate at an advanced level.
- Conducting self-assessments or using frameworks like NIST CSF or MITRE ATT&CK.
- Evaluating key areas, including processes, technology, staffing, threat intelligence, and incident response capabilities.
- Reviewing operational metrics, such as MTTD and mean time to respond (MTTR).
- Engaging third-party auditors or performing gap analyses to identify areas for improvement.
- What are the key elements of a SOC's incident response plan?
- How does automation and machine learning impact SOC operations?
No, although a SOC assists compliance efforts, compliance is not usually a direct function of a SOC. While compliance is handled by a different team that is in charge of making sure that rules, regulations, and policies are followed, a SOC concentrates on threat detection, monitoring, and incident response. The SOC aids compliance by providing logs, reports, and evidence of security controls to demonstrate adherence during audits.
Incident escalation within a SOC typically follows these key steps:
A SOC's maturity levels are normally evaluated in five stages using a progression model, like the Capability Maturity Model Integration (CMMI):
Organizations can assess their SOC maturity level by:
Identifying potential security incidents, identifying and evaluating threats, containing compromised systems to stop their spread, eliminating malicious components, recovering systems to normal operation, and learning from incidents through post-event reviews to enhance subsequent responses are all part of a SOC's incident response plan.
SOC activities are greatly improved by automation and machine learning (ML), which increase accuracy and efficiency. Automating repetitive processes like log analysis, alert triage, and threat detection frees up analysts to concentrate on intricate investigations. ML models enable the early detection of complex threats by more quickly and reliably identifying patterns and abnormalities in huge datasets than manual approaches. By connecting events and offering useful insights instantly, they also improve incident response. Automation reduces human error, expedites remediation efforts, and ensures consistent execution of security policies. Overall, these technologies empower SOCs to manage increasing volumes of data and evolving threats more effectively.



