Hi, all! Keeping our promise of bringing you the second and final part of the part of the command and control (C&C) series, we're back. Last time, we shed light on the following key topics:
In case you want a quick brush up these, or missed it, you can find the blog here.
In the second and final part of this series, we'll delineate on the indicators of compromise (IoCs), discuss some of the best practices against them, and learn how an effective SIEM solution can help in their detection.
Let's get started folks!
Here are some of the common IoCs which organizations can watch out for in their network:
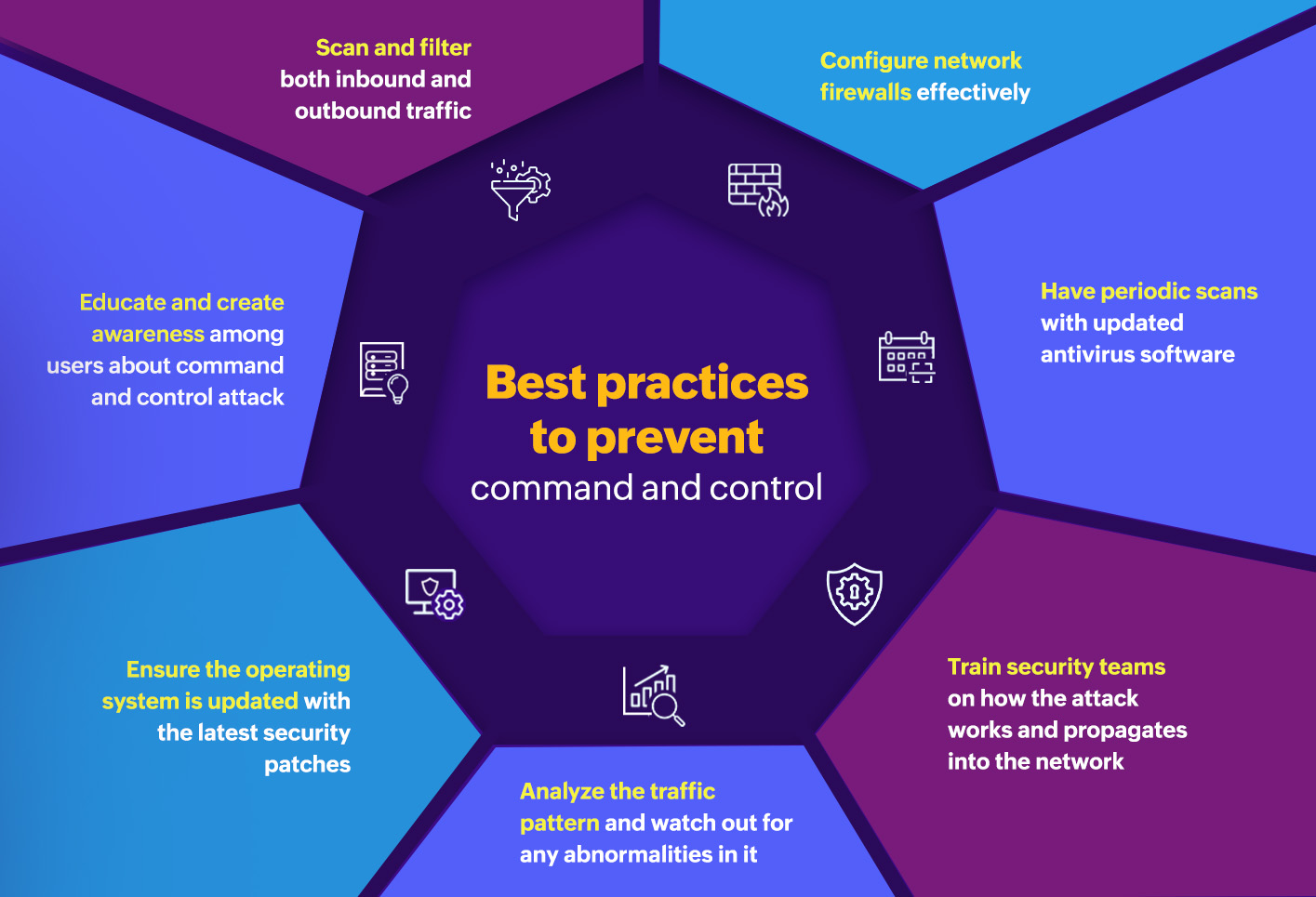
A SIEM solution like ManageEngine Log360 can help organizations detect and respond to the IoCs of a C&C effectively with its various comprehensive modules. Here are a few of the ways this is achieved:
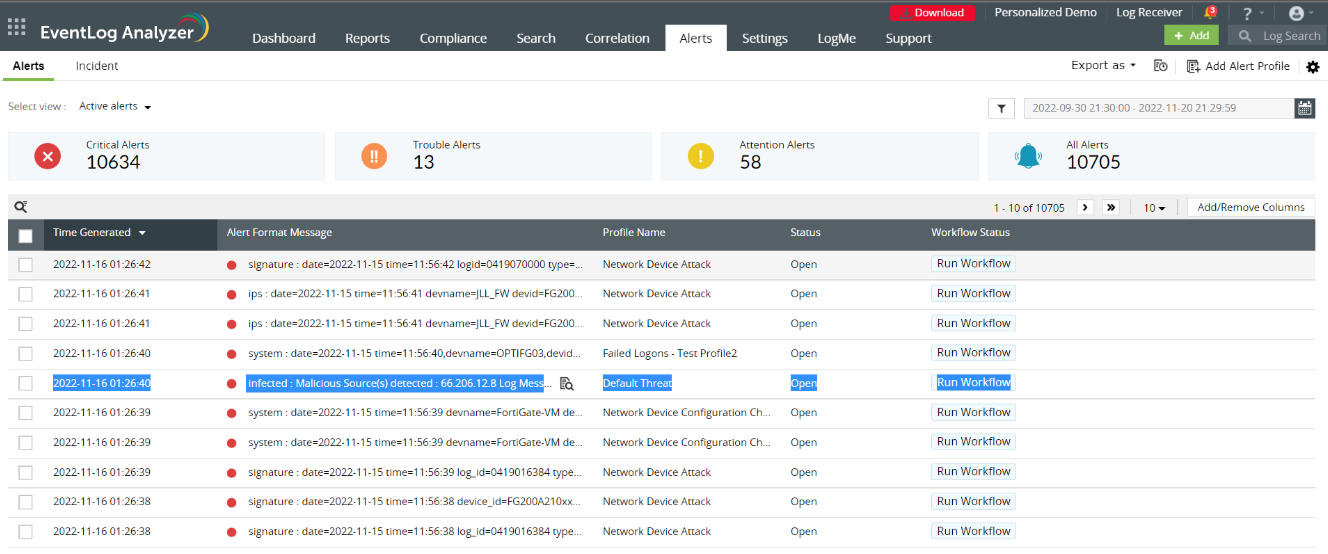
Figure 1 shows alerts on detected malicious sources.
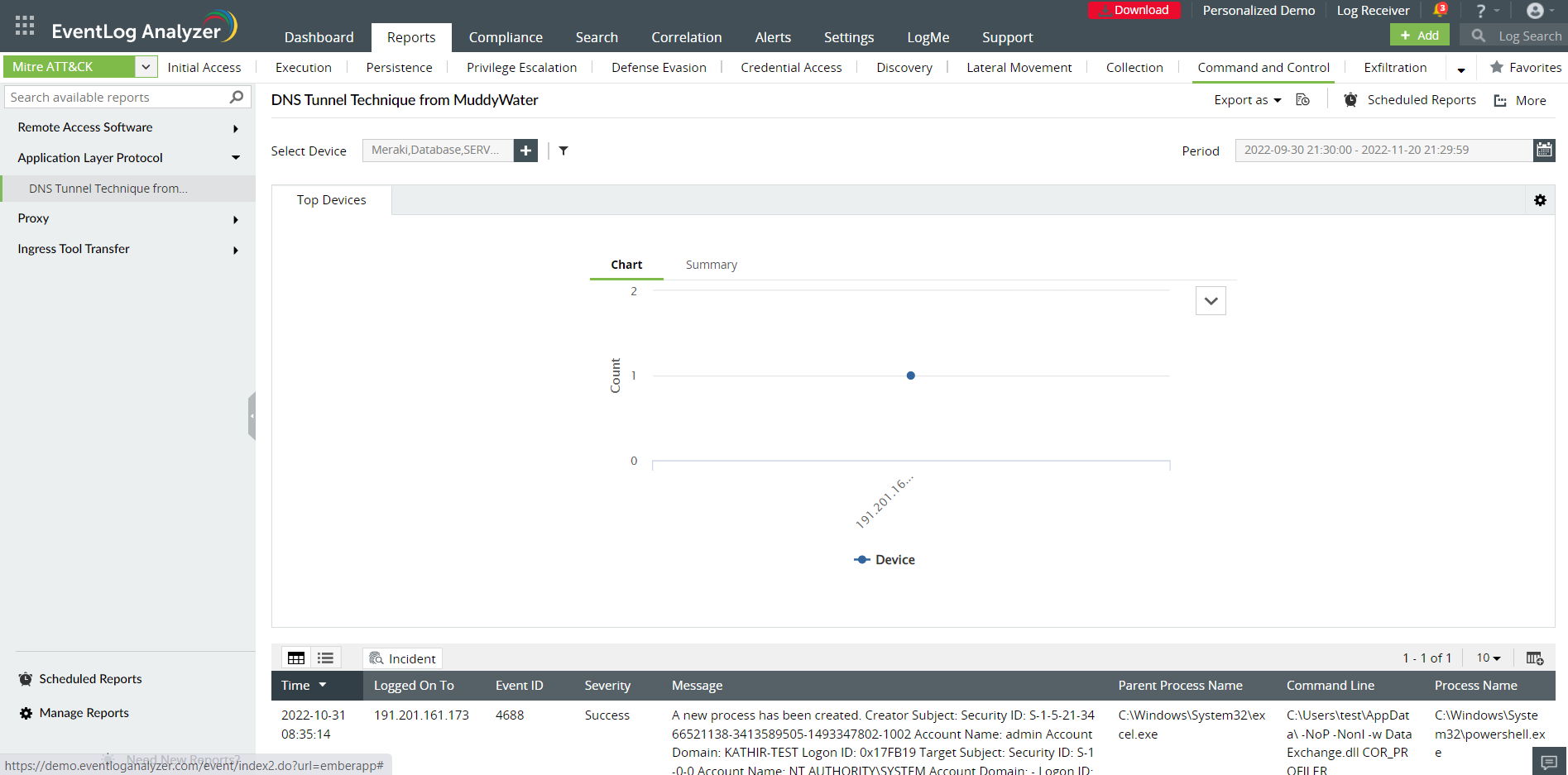
Figure 2 shows DNS Tunnel report.
To prevent your network from becoming a victim of an attack like C&C, it is crucial for your organization to have a SIEM solution in place to correlate activities across the network and take preemptive measures to mitigate attacks.
Try a free, 30-day trial or schedule a personalized demo to fully evaluate how a SIEM solution like Log360 can bolster your organization to defend against various cyberattacks, including command and control.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.