When shifting to the cloud, organizations need to ensure that cloud applications can be accessed only by authorized users. As your network perimeter changes, you need to implement security policies that adapt to the ever-evolving threat landscape. This article will explain what a cloud access security broker (CASB) is, the benefits of implementing one, and some security use cases for each mode of deployment.
What is a CASB?
A CASB is a security solution that sits between an organization's on-premises or remote infrastructure and its cloud applications, acting as an intermediary to monitor the traffic between them. These solutions are deployed using either proxies or APIs to identify if a connection to a cloud service is authorized or not. They provide an additional layer of security, enabling control over information shared across public and enterprise cloud apps.
Why should organizations use CASBs?
With organizations moving to the cloud and allowing employees to work from anywhere, the network perimeter is no more. Therefore, security teams need to adopt new ways of thinking about cybersecurity to secure their cloud infrastructure. CASBs can fill the security holes in the cloud, allowing security professionals to plan strategies, oversee threats, and gain complete visibility into sanctioned, unsanctioned, and shadow application use. A CASB-integrated SIEM solution like ManageEngine Log360 can help you identify the gaps in your cloud security, including shadow IT and data exfiltration threats. To learn more, read the article, Shedding light on shadow IT and data exfiltration with CASB.
Benefits of a CASB in an organization
- Secures data from unauthorized access and cyberthreats
- Monitors user behavior and responds immediately to any threats
- Detects the presence and use of unmanaged devices and unauthorized applications in the network
- Allows organizations to monitor user activity and reports if any anomalous activity is detected
- Generates reports for compliance auditing purposes
CASB deployment modes and use cases
Organizations looking to implement a CASB solution in their networks should know that CASBs can have two deployment modes: proxy-based and API-based. Each deployment mode has its advantages and disadvantages. Therefore, companies need to understand the important use cases associated with each and make decisions based on their specific needs.
Proxy-based CASBs
The first generation of CASBs uses proxies to monitor access between known users and cloud applications. Traffic is rerouted through a proxy, allowing IT teams to add encryption security controls and monitor access attempts, logins, and usage. Proxy-based CASBs act as intermediaries between user devices and the cloud applications that the devices are attempting to access. Proxy-based CASBs are further divided into forward and reverse proxy modes.
Forward proxy use cases
Implementing granular access and activity controls
The CASB forward proxy can be integrated with the network firewall to monitor and enforce controls at the user activity level. For example, you can define a CASB policy to prevent users from accessing a specific application or uploading documents to certain websites. You can configure DLP policies in the cloud using Log360 for specific applications, storage services, mail services, messaging services, streaming services, social sites, and more, as shown in Figure 1.
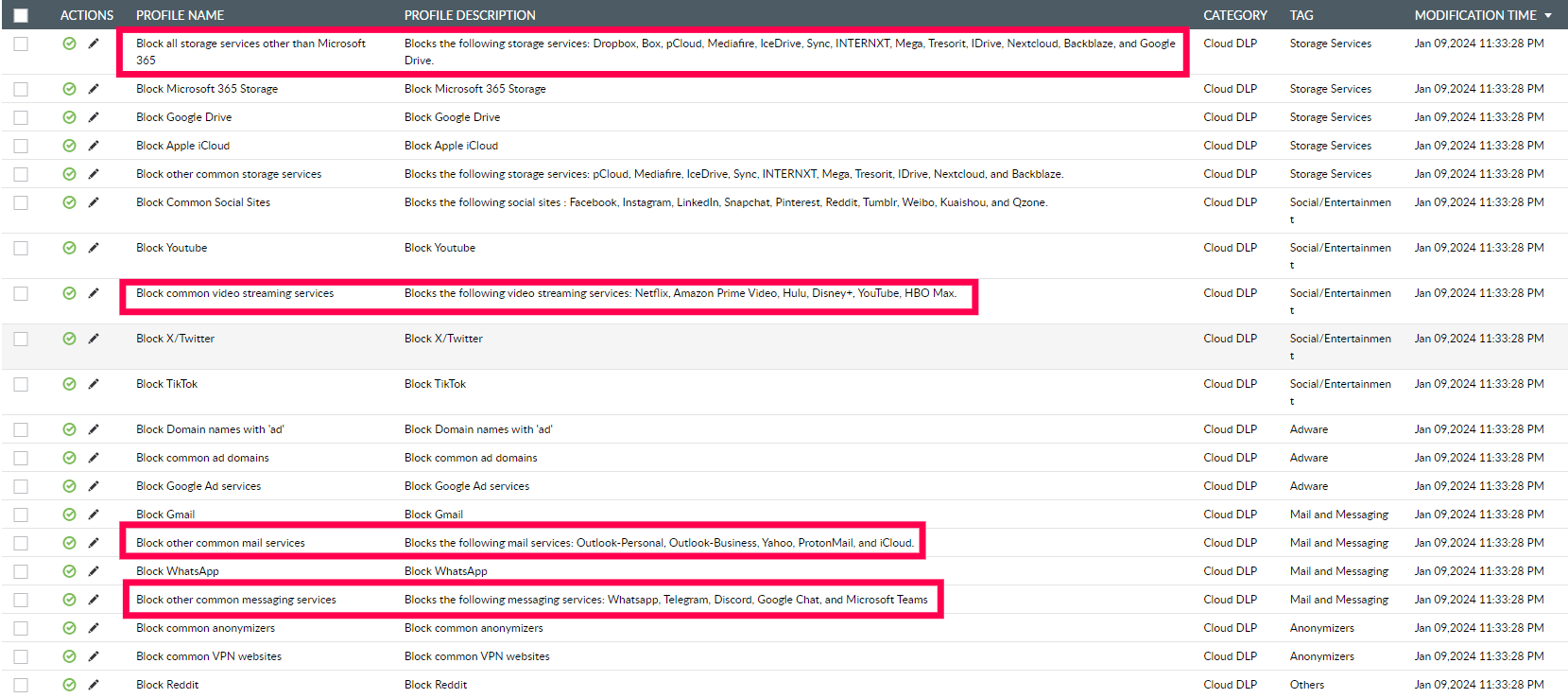
Figure 1: Configuring cloud DLP policy profiles in Log360 to control app usage
Detecting shadow IT in your network
Every access request is sent through the CASB forward proxy, providing real-time information on what is happening to the data in transit. Therefore, forward proxies can detect whether a user is trying to access a sanctioned application or an unsanctioned shadow application by using the web traffic logs. Log360 provides forward proxy capabilities for identifying the cloud apps used and the users accessing them, as shown in Figure 2.
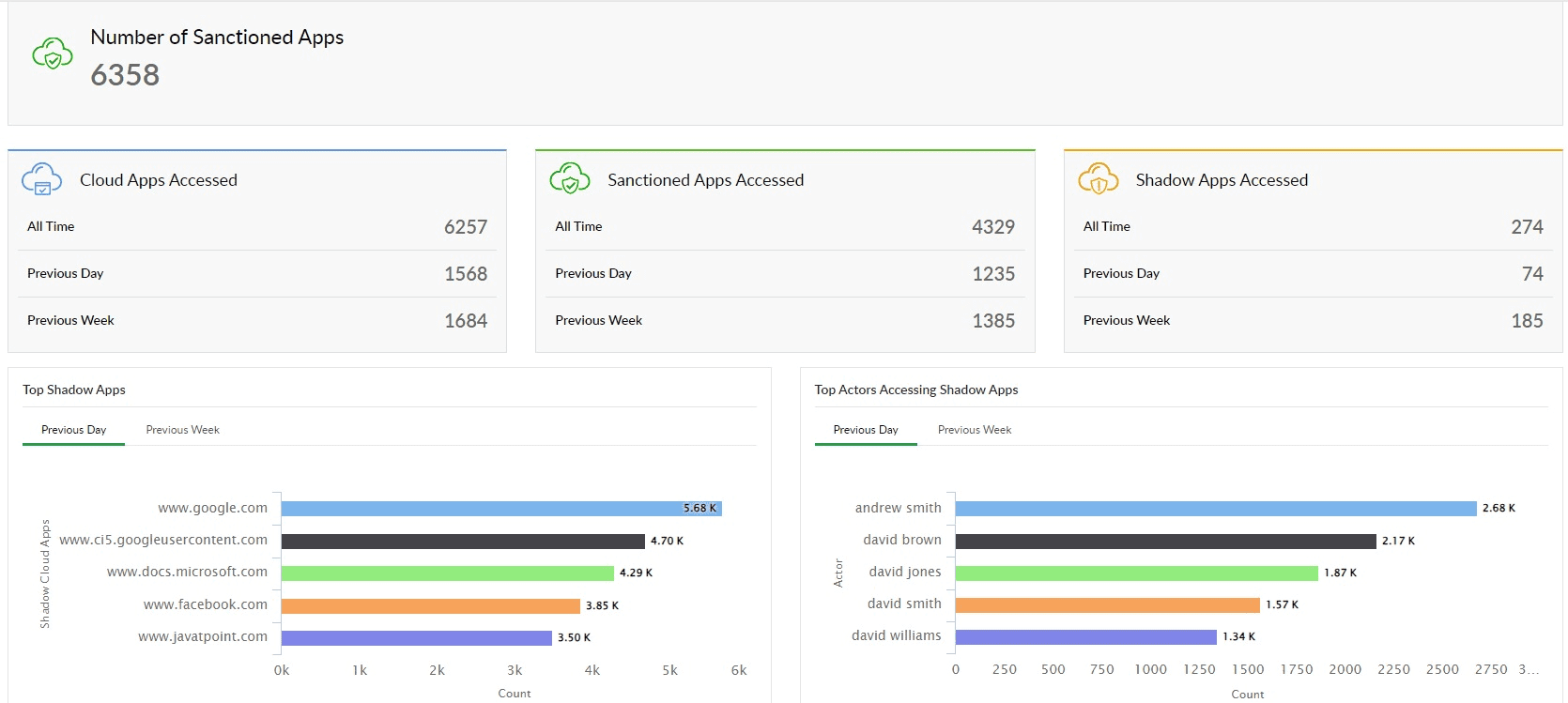
Figure 2: Forward proxy in Log360 offering insights into sanctioned and shadow apps
Reverse proxy use cases
Enforcing access controls based on user behavior
CASBs can monitor user and entity behavior details, such as role, location, and time, to determine access levels and alert admins if anything malicious is detected. The CASB reverse proxy can be integrated with identity management applications to permit or restrict access to specific applications, files, and functions.
Preventing data loss from specific applications
Malicious insiders or external attackers can sometimes access sensitive data uploaded to internal applications. You can integrate a CASB with a DLP solution to apply granular access policies and prevent data exfiltration. Log360 alerts security analysts of malicious data exfiltration attempts with the help of its intuitive dashboards and comprehensive reports, as shown below.
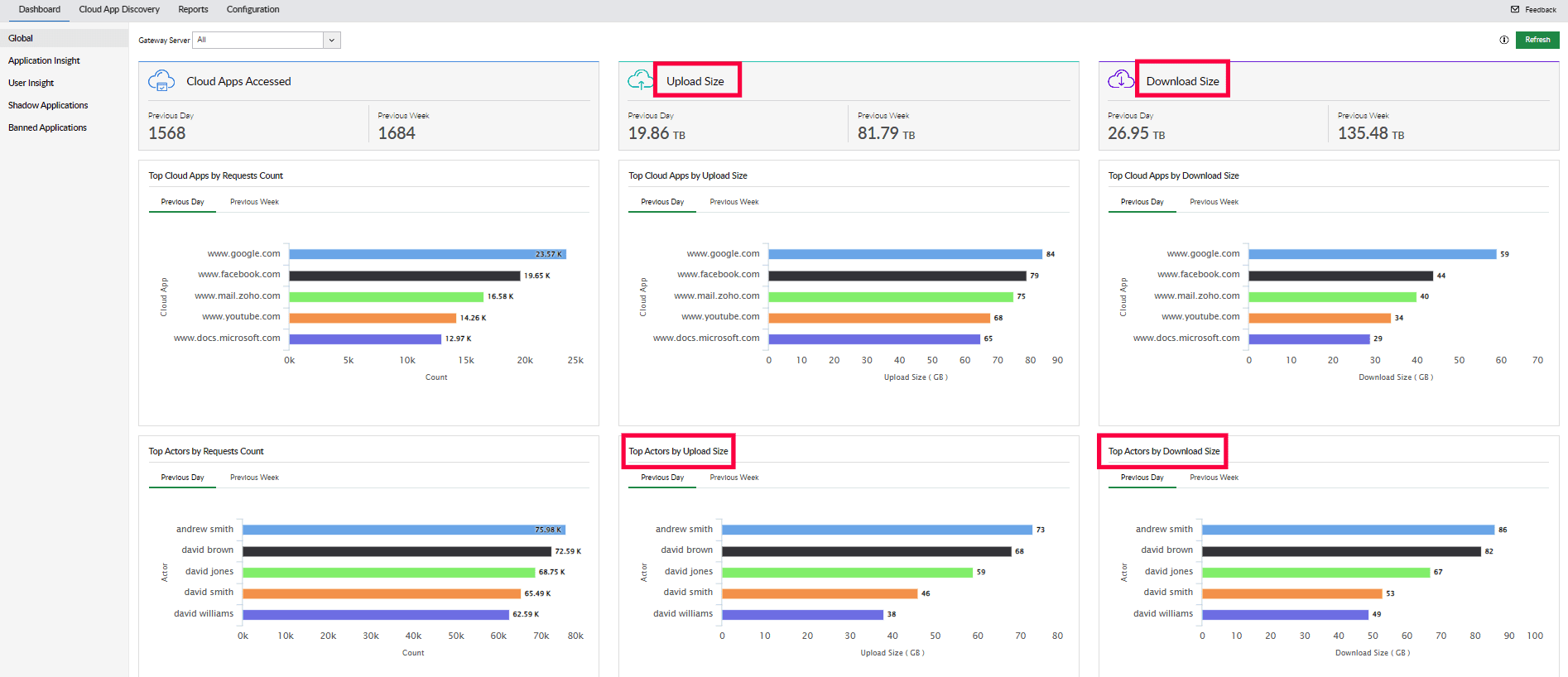
Figure 3: Log360 dashboard showing details about file uploads and downloads
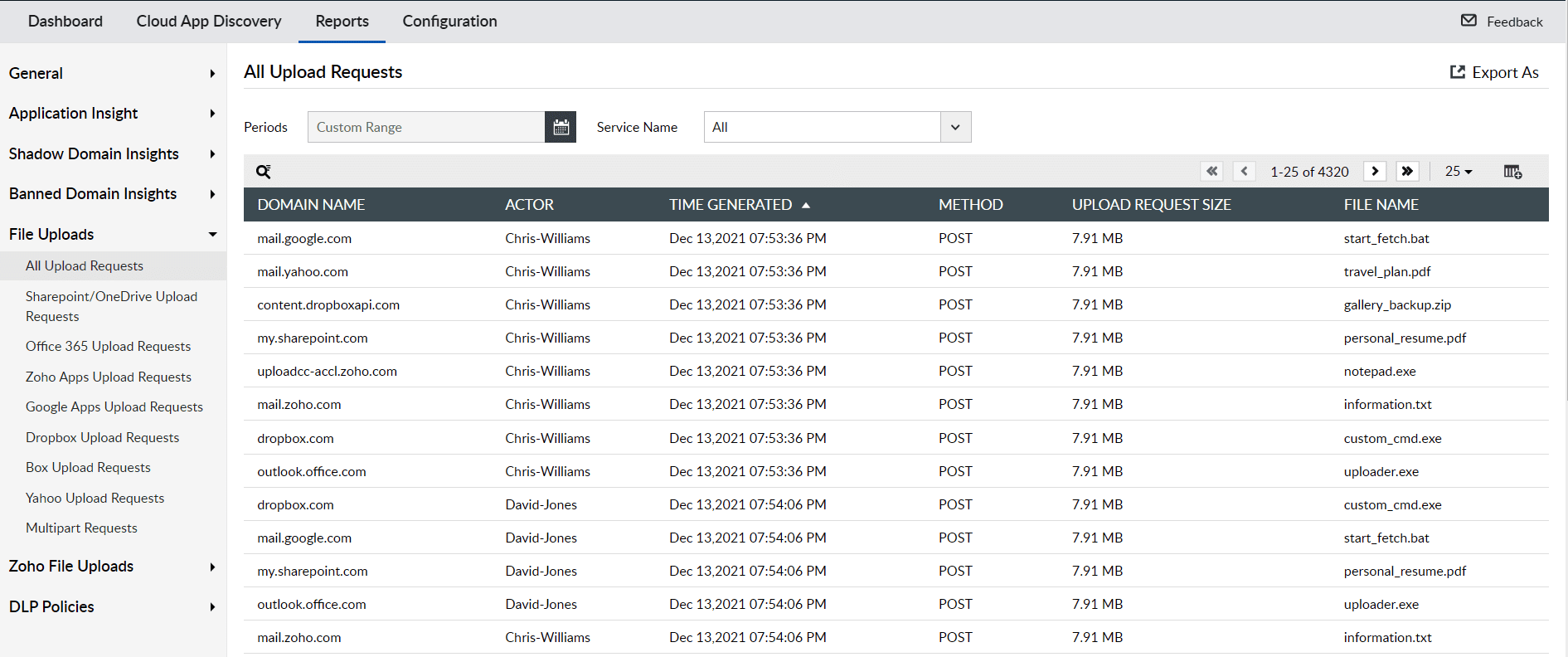
Figure 4: Reports in Log360 detailing all upload requests
Encrypting corporate data residing in the cloud
CASBs can be integrated with key management services to encrypt certain types of data transferred to cloud services, such as email addresses and credit card numbers.
Controlling access to downloaded data
CASBs can be used to prevent the unauthorized export of critical data from cloud applications to unmanaged devices. This is done by integrating CASBs with endpoint agents and identity management solutions to detect if a download request is from a managed or unmanaged device and to restrict access to the data.
Auditing user activity in cloud applications
Placed closer to the cloud applications, the CASB reverse proxy integrates with identity providers to track user and admin activity inside cloud services. This lets security teams investigate the logs generated by the CASB tool and view the security incidents originating from the cloud services.
API-based CASBs
Alternatively, CASBs can use APIs to access and monitor data stored in the cloud. Because they use the cloud service provider's built-in APIs, they allow IT professionals to customize access rules, automate incident responses, and gain deeper insights into activities performed in the cloud.
API use cases
Detecting malware in cloud services
API-based CASBs provide granular visibility into files stored in cloud services. This enables IT admins to detect and remove malware residing deep within. They can also integrate with malware detection solutions to strengthen malware diagnoses.
Enforcing data transfer policies across multiple cloud services
Employees may sometimes share sensitive corporate data with their personal email address or use two or more cloud apps to make their work easier. This comes with its own set of hazards. API-based CASBs can detect all the files shared with unapproved domains or anyone on the internet, then revoke permissions and shared links.
Auditing user access provisioning
API-based CASBs can detect whether the accounts that were granted permissions are still active or dormant. They can also detect the type of permission that was granted, such as admin or viewer.
Extending on-premises DLP policies to cover cloud data
API-based CASBs can be integrated with on-premises DLP solutions to audit files stored in cloud applications and perform necessary actions, such as deleting or encrypting files that were stored against DLP policies.
What capabilities do you need in your SIEM solution?
Today, the cybersecurity landscape is as complex as it gets, with varied categories of tools solving different security problems. Can a DLP tool become a CASB tool if it can encrypt data in the cloud? If a SIEM solution can collect endpoint logs, why do you need an EDR solution? The questions are endless. But it's safe to say that all these security solutions provide better visibility into and control over the incidents happening in your network when they integrate effectively with each other.
So, where does a CASB fit in your security posture?
As organizations continue to shift their operations to the cloud, their visibility into the data residing in their cloud apps tends to decrease. CASBs are here to fill in the gaps. CASBs can understand the context of data in transit or at rest, which a log collected from a SIEM solution or firewall lacks. They also allow existing security policies to extend to the cloud by integrating with and collecting log data from various on-premises tools:
- DLP tools
- Firewalls
- Secure web gateways
- Identity management tools
- SIEM solutions
A unified SIEM solution with integrated CASB and DLP capabilities like ManageEngine Log360 collects logs from over 700 different log sources such as your network firewall logs, security device logs, servers, Windows, and Linux logs, web proxy logs, endpoint security logs, application logs, database logs, web server and web application logs, and more. Additionally, it provides anomaly detection and threat analytics capabilities that help organizations prevent and thwart insider and external attacks. To learn more, sign up for a personalized demo.



